
Journey into the Top 10 Vulnerabilities Used by Ransomware Groups
Once upon a time, in cyberspace, a menacing threat emerged. It would forever change the landscape of digital security. This threat was ransomware. It is a wicked force capable of wreaking havoc on individuals, organizations, and even entire nations. Its power lies in the ability to encrypt valuable data. Imagine someone sneaking into your digital kingdom. They lock away your valuable information and demand a hefty ransom to set it free. It is a nightmare that comes to life.
In recent years, these ransomware attacks have become more common and dangerous. Like an unstoppable force, these sneaky attacks swept across the digital realm. It left a trail of destruction in their wake, from hospitals struggling with life-or-death situations to critical infrastructure systems. They all brought to their knees. The consequences were dire, and the financial gains for the attackers were significant. The attackers knew how to exploit weaknesses in our computer systems. They preyed on weaknesses in our software. It was no wonder that ransomware attacks became an alluring prospect for malicious actors worldwide.
But how did these cyber criminals manage to penetrate the defenses of their targets? The answer lay in exploiting vulnerabilities that plagued various systems and software. With precision, these nefarious individuals scoured the digital landscape. They searched for weaknesses to exploit. Their success hinged on the negligence of individuals and organizations in implementing timely security patches or updates. It left the doors wide open for the ransomware onslaught.
In our tale, we journey deep into the heart of the ransomware realm. We shine a light on the top 10 vulnerabilities that these malicious groups often exploit alongside the statistics behind their use of vulnerabilities. Each vulnerability, like a crack in the armor of a mighty fortress, offered an entry point for the ransomware invaders. We uncover the impact of these vulnerabilities. We peer into the preferred techniques employed by the ransomware groups.
But fear not, for our quest is not despair but empowerment. Armed with knowledge, we seek to equip individuals and organizations with the necessary means, which they need to fortify their digital defenses against the looming threat of ransomware attacks. Whether you’re an IT professional or a business owner, understanding these vulnerabilities will be your first line of defense.
As we navigate this dangerous path, SOCRadar Extended Threat Intelligence platform guides us. It provides us with invaluable information. Like a wise and vigilant companion, this platform keeps us informed about the vulnerability and threat actor data. With SOCRadar by our side, we gain deeper insights into the tactics and techniques of the ransomware groups. It gives us a better chance to outsmart them.
So, join us on this epic adventure as we uncover the dark secrets behind ransomware attacks and discover effective ways to fight back. With the guidance of SOCRadar Extended Threat Intelligence platform, we’ll navigate the dangers of outdated software and misconfigured systems. We will learn how to protect ourselves against the ever-present threat of ransomware. In a world where cyber threats are constantly evolving, knowledge and preparedness, along with the support of trusted allies like SOCRadar, are our greatest weapons. The battle against ransomware begins now.
Statistics Behind the Vulnerabilities Used By Ransomware Groups
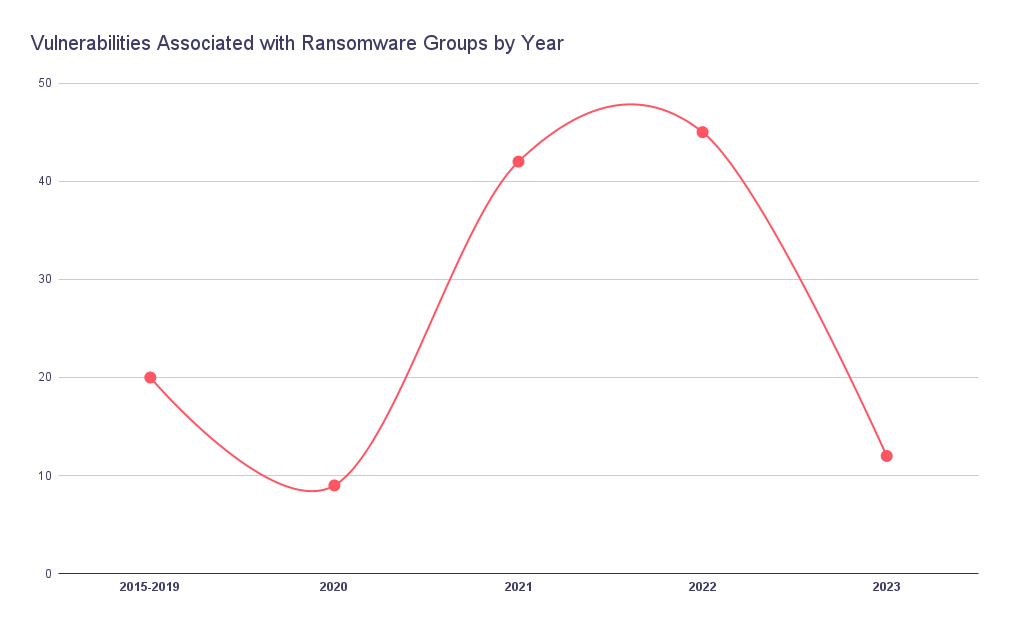
Certain years stand out as pivotal moments in the annals of cyber warfare. Among these, the years 2021 and 2022 shine brightly. They provided the lion’s share of the arsenal wielded by these nefarious adversaries.
In 2021, the battlefield witnessed a dramatic surge in ransomware attacks. The ransomware groups, fueled by a staggering array of 42 newly discovered Common Vulnerabilities and Exposures (CVEs), seized the opportunity to exploit weaknesses in systems and software. Among these was one of the most infamous vulnerabilities, the Log4Shell. With each successful breach, their audacity grew. It was a year that gave birth to unprecedented challenges for defenders. They have found themselves in a relentless struggle to patch vulnerabilities. They had to stay one step ahead of the ever-evolving threat landscape.
But the ransomware groups were not content with a single year’s worth of ammunition. As 2022 dawned, armed with 45 new CVEs, they struck with increased sophistication and precision. Their tactics had evolved. They are honed by experience and a deep understanding of their targets. No system was safe, and no organization was impervious to their malevolent intent. The defenders were stretched to their limits. They scrambled to fortify their defenses and stem the tide of ransomware attacks.
Now, as we stand on the precipice of 2023, the battle against ransomware groups continues. Though the number of CVEs at their disposal has only risen by 12, the impact of their attacks remains potent. The defenders know all too well that the ransomware groups are stubborn. They are utilizing the vulnerabilities from previous years continuously. The lessons learned from the torrential storms of 2021 and 2022 remain etched in their collective memory. It reminds defenders of the importance of constant vigilance and robust cybersecurity measures.
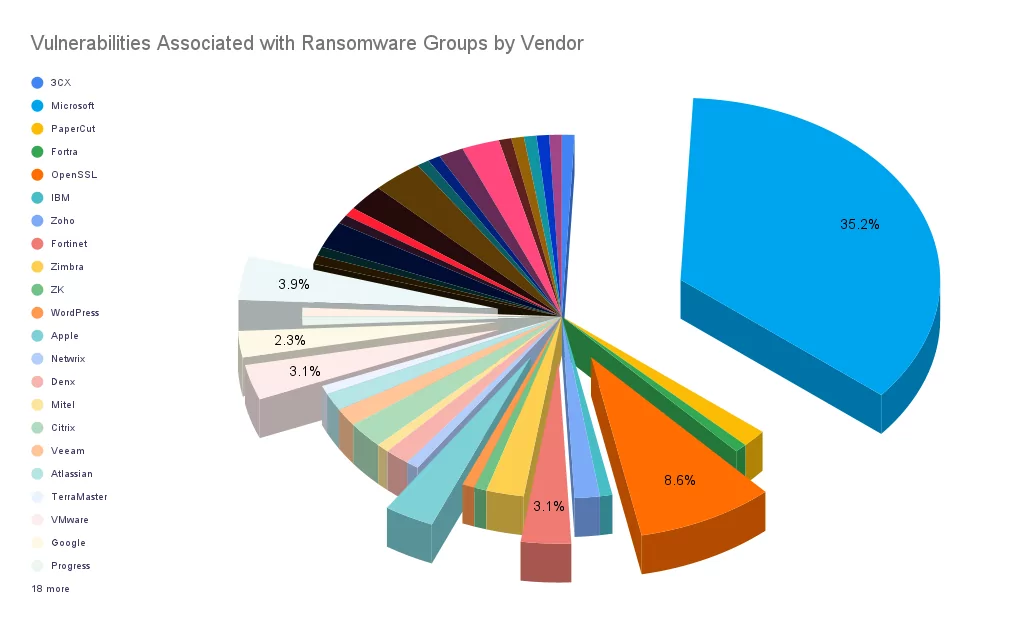
Microsoft held a commanding 35.4% share of the vulnerabilities exploited by ransomware groups because of its ubiquitous presence and a range of products relied upon by countless organizations. Microsoft’s prominence in the corporate landscape made it an enticing target for these digital criminals. Their products, such as Windows and Exchange Server, form the backbone of countless businesses. They house invaluable data and communications.
However, other vendors also garnered the attention of the ransomware underworld. Apache, OpenSSL, VMware, Fortinet, Apple, and Google garnered the attention of these malicious actors. It offered them additional avenues to infiltrate systems and wreak havoc. Each of these vendors plays a relevant role in the corporate ecosystem.
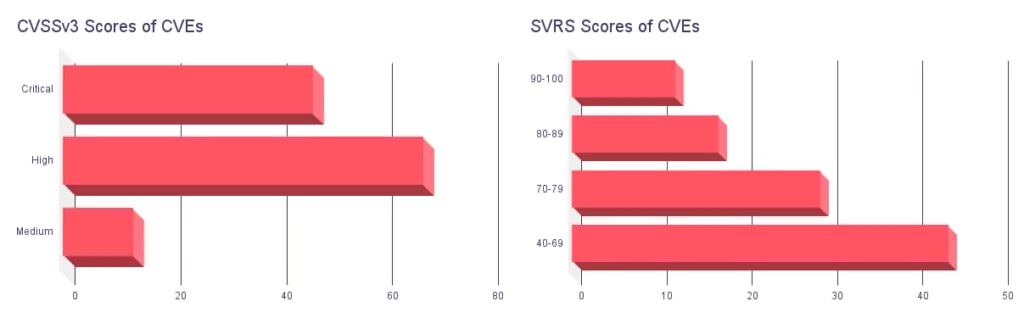
Traditional scoring systems like CVSSv3 have long been relied upon to assess the criticality of vulnerabilities. Looking at the data, we can see that there were 47 Critical CVEs, 68 High CVEs, and 13 Medium CVEs identified. CVSSv3 scores provide valuable information in determining the urgency of a vulnerability. However, they may not capture the full context and depth of the threat landscape. This is where the SOCRadar Vulnerability Risk Score (SVRS) steps in to offer a more comprehensive understanding. The SVRS takes into account a range of qualitative elements. It ranges from social media, news, code repositories, and dark/deep web sources to the attribution of threat actors and malware.
Digging into the SVRS scores, we find that there are 12 CVEs with SVRS scores ranging from 90 to 100, indicating a critical level of risk and severity. Additionally, 17 CVEs fall within the SVRS range of 80 to 89, and 29 CVEs are within the range of 70 to 79. It’s worth noting that 44 CVEs have SVRS scores between 40 and 69, signifying a moderate level of risk as of now.
These numbers highlight the value of SVRS in providing a more nuanced understanding of vulnerabilities. By incorporating qualitative elements, SVRS paints a richer picture of the potential impact and urgency of a vulnerability. It enables organizations to make more informed decisions regarding their security measures.
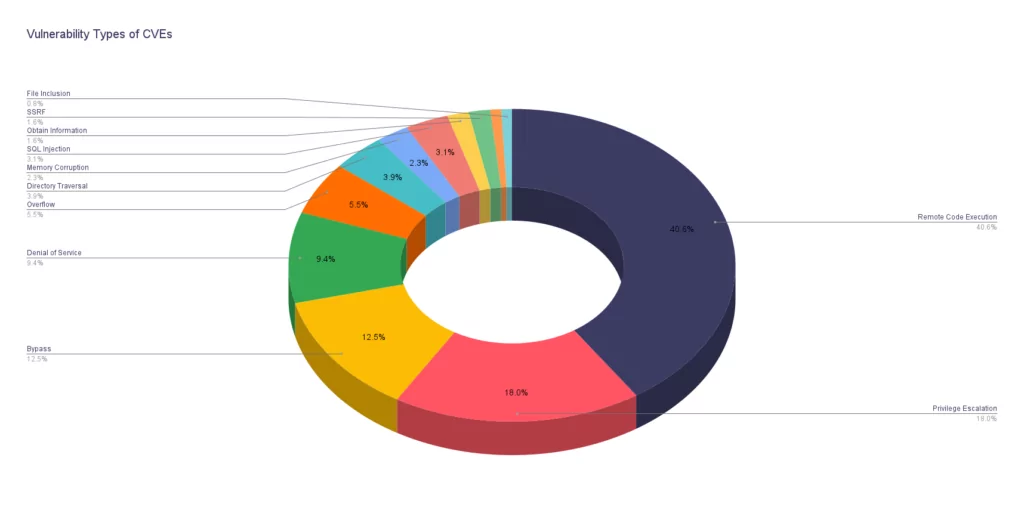
Examining the data on vulnerability types leveraged by ransomware groups, we discover a landscape dominated by one particularly menacing vulnerability: Remote Code Execution (RCE).
With a staggering 40.6% share, RCE vulnerabilities stand as the favored weapon in the arsenal of these malicious actors. This vulnerability type allows attackers to execute arbitrary code on targeted systems. Its magnitude cannot be underestimated. The consequences of successful RCE exploitation can be devastating.
However, RCE is not the sole vulnerability type embraced by ransomware groups. Privilege Escalation comes in second at 18%. It enables attackers to elevate their access privileges within a system and move laterally. In return, compromising additional resources. Bypass vulnerabilities account for 12.5%. It provides cybercriminals with methods to evade or circumvent security controls, while Denial of Service vulnerabilities stands at 9.4%. It allows attackers to disrupt or disable critical services, causing operational chaos.
Further down the list, we find Overflow vulnerabilities at 5.5%, Directory Traversal, and Memory Corruption, both at 3.9% each. It highlights the diverse techniques employed by ransomware groups.
Amidst this landscape, it is clear that RCE vulnerabilities reign supreme. It is the gateway for ransomware attacks. Their ability to execute arbitrary code grants cybercriminals unrestricted access to systems. It allows them to deploy ransomware, encrypt valuable data, and hold it hostage for monetary gain.
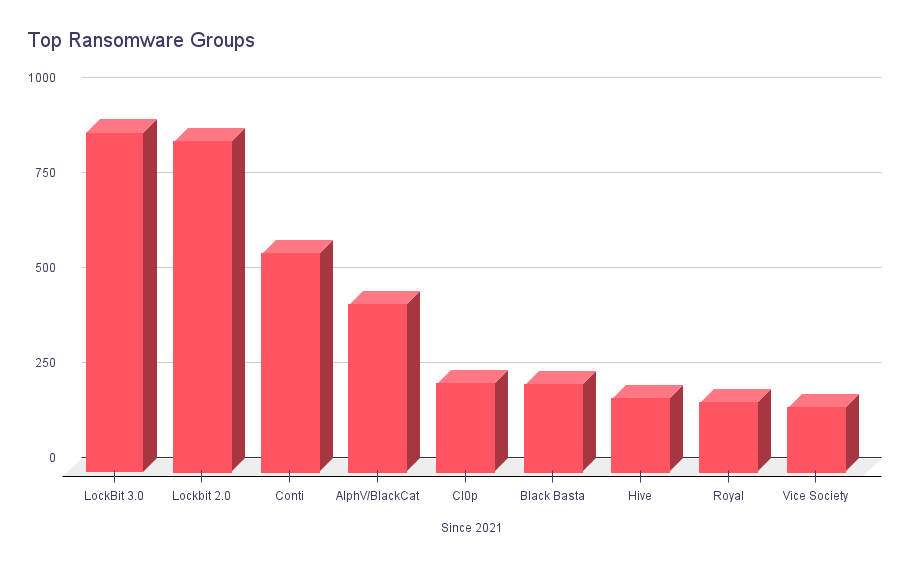
Two names stand out among the top ransomware groups since the beginning of 2021: LockBit and Conti. Let’s delve into their exploits and the impact they have had since 2021.
Lockbit, represented by its two versions, LockBit 3.0 and LockBit2.0, has been a formidable force. They launched, with their two versions, a staggering 892 and 869 attacks, respectively. With their sophisticated techniques and advanced encryption algorithms, LockBit has become synonymous with high-profile breaches, targeting organizations across industries.
Another notorious group, Conti, has etched its name in infamy with 574 documented attacks. However, a significant development unfolded in 2022, as Conti collapsed due to an implosion. Still, their impact continues to reverberate within the cybersecurity community. There are new groups formed from the remains of Conti.
Alongside these prominent groups, others have left their mark on the ransomware landscape. AlphV/BlackCat has carried out 440 attacks, while Black Basta has inflicted its own brand of digital mayhem with 228 incidents. Hive, Royal, and Vice Society round out the list, each leaving a trail of ransomware attacks in their wake.
However, one group skyrocketed in 2023, the Cl0p Ransomware. They leveraged zero-day vulnerabilities in MOVEit and GoAnywhere MFT software and launched torrents of attacks on big targets. As you can see on the graphic below, they currently sit in third place for the year 2023.
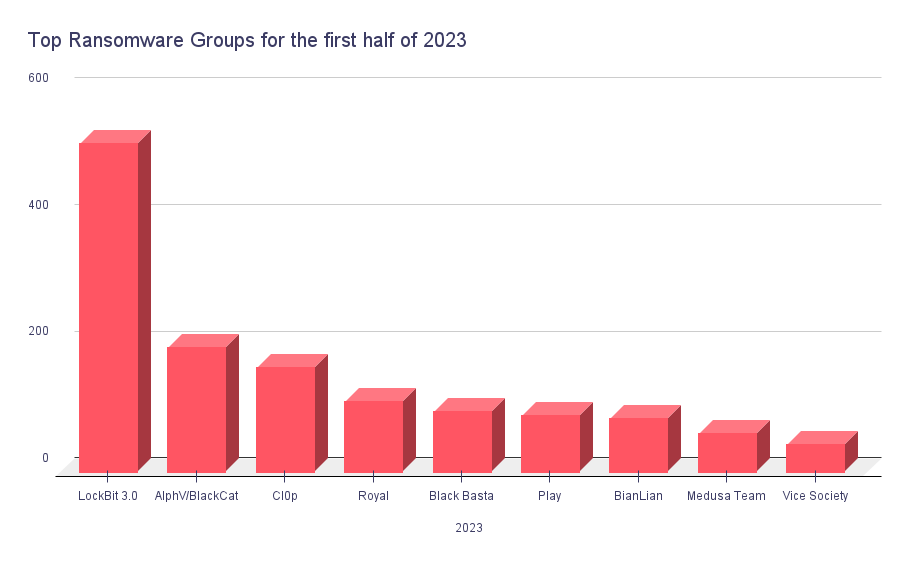
Top groups did not see a huge change in the first half of 2023. LockBit still stays way above any other group. In addition to the rise of Cl0p’s terror, we can see another group, Medusa Team, etching itself as one of the top threats.
These numbers paint a grim picture of the pervasive threat posed by ransomware groups. The sheer volume of attacks signifies the scale of their operations.
Top 10 Vulnerabilities Leveraged by Ransomware Groups
ProxyShell Vulnerabilities
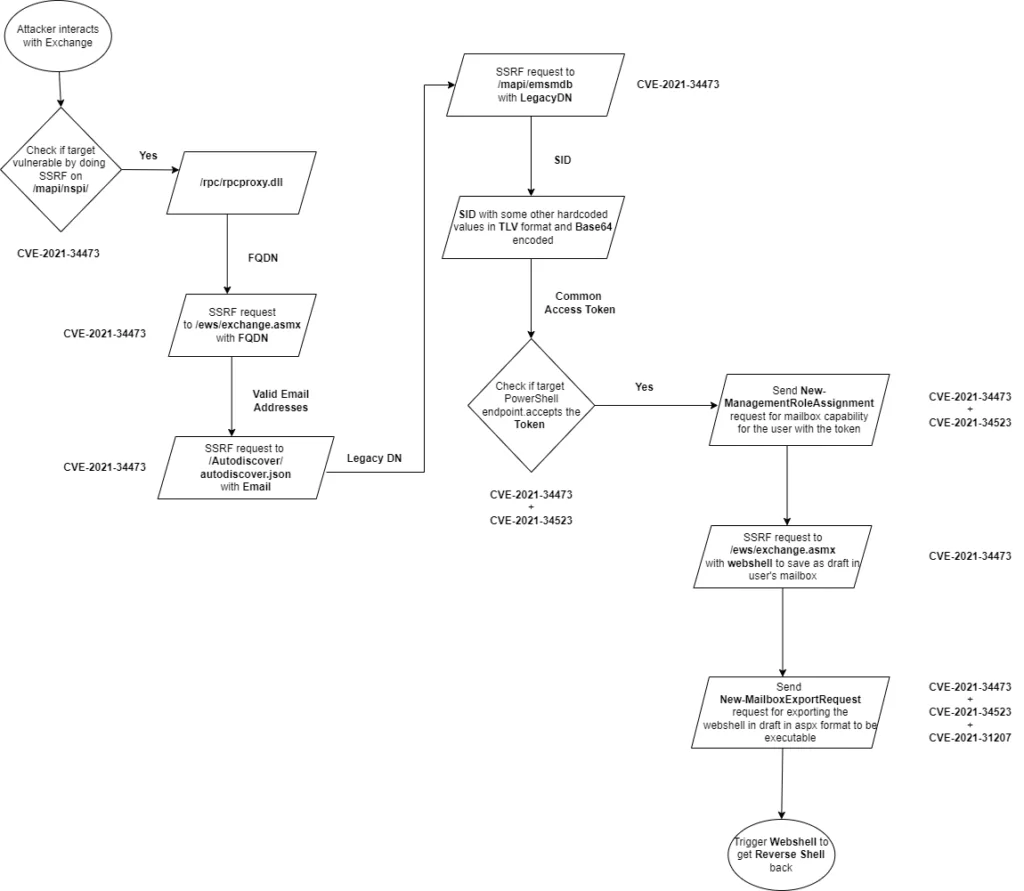
In August 2021, the cybersecurity community was alerted to the emergence of ProxyShell. It is a dangerous chain of vulnerabilities targeting on-premises Microsoft Exchange Servers. ProxyShell is comprised of three critical vulnerabilities: CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207. These vulnerabilities affect versions of Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019. Exploiting these vulnerabilities, ransomware groups can achieve pre-authenticated remote code execution (RCE), gaining unauthorized access and disrupting organizations’ digital infrastructures. Since then, sectors such as Education, Government, Business Services, and Telecommunications have already fallen victim to ransomware attacks leveraging ProxyShell vulnerabilities.
The ProxyShell exploit chain begins with the creation of an email item within a mailbox. It leverages the Autodiscover service and the Messaging Application Programming Interface (MAPI). These techniques allow attackers to obtain the necessary credentials and access tokens to interact with Exchange Web Services (EWS) as legitimate users.
CVE-2021-34473, the first vulnerability in the ProxyShell chain, involves pre-auth path confusion. It enables attackers to bypass access control lists (ACL) and gain arbitrary access to backend URLs as NT AUTHORITY/SYSTEM. This initial breach sets the stage for the subsequent vulnerabilities to be exploited.
CVE-2021-34523, the second vulnerability, exploits the Exchange PowerShell backend. By downgrading from the NT AUTHORITY/SYSTEM account to the target user, who must possess local administrative privileges, attackers can execute arbitrary Exchange PowerShell commands.
CVE-2021-31207, the final vulnerability in the ProxyShell chain, allows attackers to write files, specifically web shells, through the New-MailboxExportRequest cmdlet. These web shells, encoded in emails, are exported to a specific path, where they become decoded and operational. It potentially provides attackers with complete control over the compromised system.
The LV Ransomware group has been found leveraging the ProxyShell vulnerability chain. The emergence of LV Ransomware’s usage of ProxyShell underscores the evolving tactics and capabilities of ransomware groups. It highlights the critical importance of proactive vulnerability management against such threats.
ProxyLogon Vulnerabilities
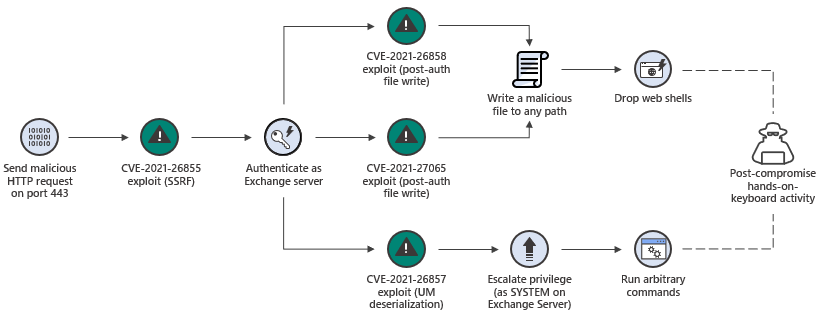
The ProxyLogon vulnerabilities have garnered significant attention due to their impact on Microsoft Exchange Server. These vulnerabilities, which include CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065, allowed threat actors to exploit weaknesses in the Exchange Server’s authentication and remote code execution mechanisms.
CVE-2021-26855 represents a server-side request forgery (SSRF) vulnerability that enabled unauthenticated attackers to send arbitrary HTTP requests and authenticate as the Exchange Server. This allowed them to gain unauthorized access and potentially exfiltrate sensitive information.
CVE-2021-26857 involved an insecure deserialization vulnerability, enabling remote code execution. By sending a specially crafted request, attackers could execute arbitrary code in the context of the Exchange Server, compromising the entire system.
CVE-2021-26858 represented a post-authentication arbitrary file write vulnerability. Exploiting this flaw allowed attackers with limited access to write arbitrary files. In return, it could be leveraged for further exploitation or to maintain persistence within the compromised environment.
CVE-2021-27065, the final vulnerability, pertained to a post-authentication arbitrary file written in the Exchange Control Panel (ECP). Attackers could utilize this vulnerability to write files and execute arbitrary code on the server.
The ProxyLogon vulnerabilities collectively provided a pathway for threat actors to gain unauthorized access, execute arbitrary code, and perform malicious activities within Exchange Server environments. The exploitation of these vulnerabilities enabled attackers to carry out the deployment of ransomware in addition to other types of attacks.
DoejoCrypt was observed exploiting the ProxyLogon vulnerabilities to gain initial access to vulnerable Exchange Servers. Once inside the compromised network, they deployed their ransomware payload, encrypting files across affected systems and demanding a ransom for their decryption. The use of ProxyLogon vulnerabilities provided DoejoCrypt with a way to bypass authentication mechanisms and establish a foothold within the targeted organization’s infrastructure.
Similarly, Pydomer capitalized on the ProxyLogon vulnerabilities to infiltrate vulnerable Exchange Servers. By exploiting the weaknesses, Pydomer gained unauthorized access and proceeded to deploy its ransomware, encrypting files and paralyzing critical systems. Pydomer then demanded a ransom from the victimized organizations in exchange for the decryption keys needed to restore the encrypted files.
Log4Shell
Log4Shell is a significant vulnerability that emerged in December 2021. It caused a major impact on the cybersecurity landscape. It is a zero-day vulnerability discovered in the Apache Log4j logging library, widely used by Java applications. The vulnerability is identified as CVE-2021-44228 and carries a critical CVSS score of 10.0.
The Log4Shell vulnerability allows attackers to execute arbitrary code on targeted systems. It potentially leads to system compromise and unauthorized access to sensitive information. Given the extensive adoption of the Apache Log4j library, the severity of this vulnerability is heightened. Many organizations, including tech giants like Apple, Google, Amazon, and Tesla, utilize this library in their environments.
Research conducted after the disclosure of the vulnerability revealed that Log4j was one of the most downloaded libraries, indicating its prevalence. Numerous projects were identified as vulnerable, with over 100 million instances of software and technology affected. In a pool of 105,497 services assessed for the Log4Shell vulnerability, a staggering 102,060 were found to be vulnerable.
Despite the high potential for exploitation, the public impact of Log4Shell has been somewhat less catastrophic than initially anticipated. However, it remains actively exploited by threat actors. The severity of the vulnerability led the Cyber Safety Review Board (CSRB) to classify it as an “endemic vulnerability.” It means that it is expected to persist in systems for many years, presenting a significant long-term risk.
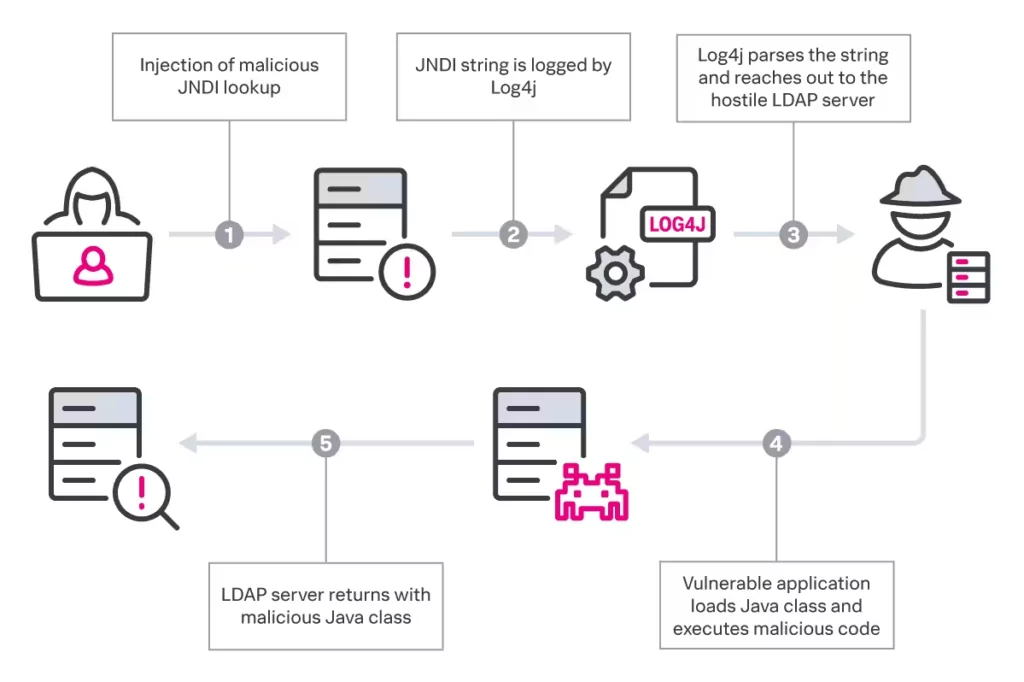
Multiple ransomware groups have leveraged the Log4Shell vulnerability to carry out attacks. LockBit, Conti (disbanded), and Alphv/BlackCat were responsible for the majority of Log4Shell incident response cases, with the average cost of a Log4Shell compromise exceeding $90,000.
PrintNightmare
The PrintNightmare vulnerability refers to a critical security flaw discovered in the Windows Print Spooler service, which is responsible for managing print jobs on Windows operating systems. This vulnerability was disclosed in June 2021 and is tracked as CVE-2021-34527.
The PrintNightmare vulnerability allows an attacker to remotely execute arbitrary code with system-level privileges on a target system. This means that an attacker who successfully exploits the vulnerability can take control of the affected system. After that, install programs, view, change, or delete data, and create new user accounts with full administrative rights.
The vulnerability gained significant attention because of its severity and the potential for widespread impact. It affects multiple versions of the Windows operating system, including Windows 7, Windows Server 2008 R2, Windows 8.1, Windows Server 2012, Windows 10, and Windows Server versions 2016, 2019, and 2022.
Black Basta, a ransomware group known for its malicious activities, has expanded its arsenal by leveraging the PrintNightmare vulnerability. According to research conducted by Trend Micro, the operators of Black Basta have incorporated the PrintNightmare vulnerability into their attack techniques. By exploiting this vulnerability, Black Basta is able to spread laterally across networks and encrypt critical files, demanding ransom payments for the encrypted data.
ZeroLogon
ZeroLogon is a critical vulnerability that affects the Windows Netlogon Remote Protocol (MS-NRPC) used by Microsoft Active Directory (AD). It was assigned the identifier CVE-2020-1472. This vulnerability allows an attacker to gain unauthorized access to the domain controller. Subsequently, take control of the entire Windows domain network. By exploiting ZeroLogon, an attacker can impersonate a domain controller, bypassing authentication measures and gaining administrative privileges.
This vulnerability is particularly significant because it allows attackers to achieve domain administrator access without requiring any user credentials. It makes it highly dangerous and appealing to malicious actors. With full control over the domain controller, an attacker can exploit the compromised network, steal sensitive information, deploy ransomware, or carry out other malicious activities.
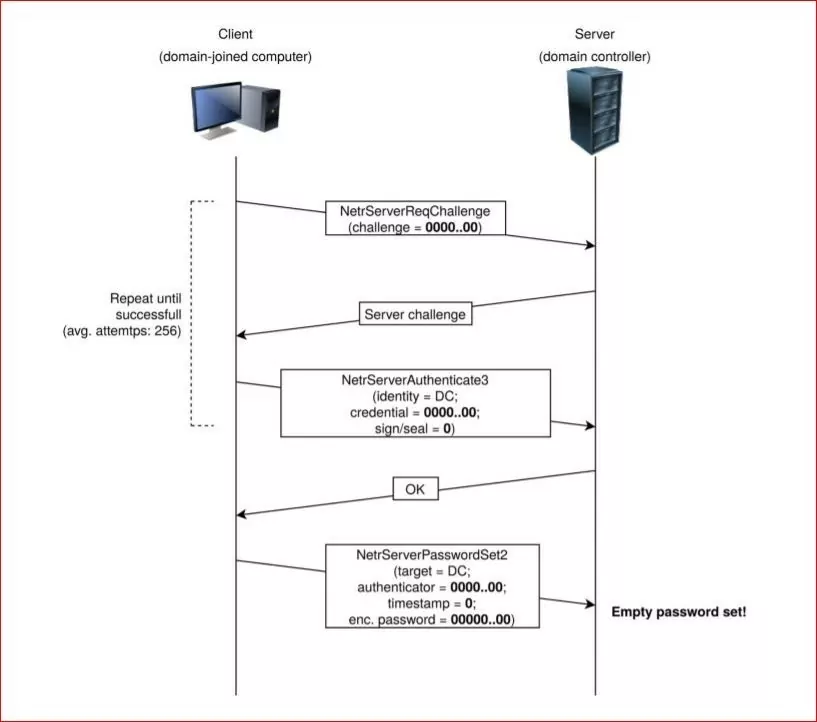
BianLian Ransomware is a threat actor group that has been identified as potentially exploiting the ZeroLogon vulnerability. According to a joint cybersecurity advisory by U.S. and Australian agencies, the group has demonstrated the capability to exploit this critical vulnerability in their ransomware operations. By leveraging ZeroLogon, BianLian Ransomware can gain unauthorized access to Windows domains, compromising the network infrastructure and potentially deploying ransomware to encrypt valuable data.
On the Rise Vulnerabilities
MOVEit Transfer Vulnerability (CVE-2023-34362)
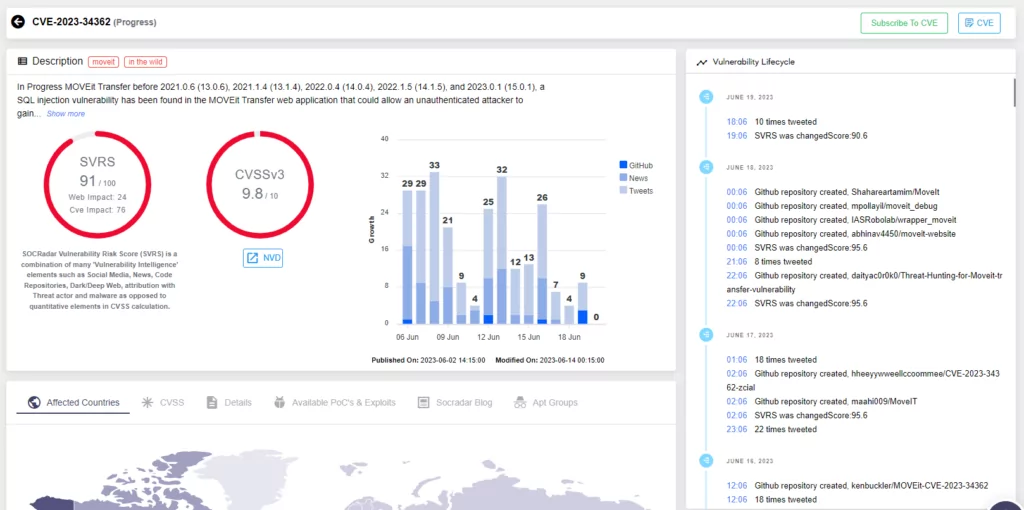
Cybercriminals are currently targeting the MOVEit Transfer software by exploiting a critical zero-day vulnerability known as CVE-2023-34362. This vulnerability allows attackers to execute remote code and extract data from organizations by leveraging SQL injection (SQLi) techniques. MOVEit Transfer is a managed file transfer (MFT) software developed by Ipswitch, a subsidiary of Progress Software Corporation.
On May 31, 2023, Progress Software issued an advisory to inform their customers about this critical vulnerability in MOVEit Transfer. Shortly after, on June 2, the vulnerability was assigned the CVE identifier CVE-2023-34362.
According to researchers, there have been observations of Cl0p Ransomware group actively seeking partners to collaborate on SQL injection attacks. And it bore fruit in the recent news CL0P announced a huge number of victims of their ransomware attacks.
To keep updated on the subject, you can check this blog post by SOCRadar.
Fortra GoAnywhere MFT Vulnerability (CVE-2023-0669)
Fortra GoAnywhere MFT vulnerability, identified as CVE-2023-0669, allows an attacker to execute arbitrary code remotely, potentially gaining unauthorized access and control over the affected system.
The CVE-2023-0669 has led to an increase in ransomware attacks since its disclosure. Malicious actors, including the Cl0p Ransomware group and the BlackCat (ALPHV) ransomware group, have attempted to exploit this zero-day remote code execution (RCE) vulnerability. In March, there were 459 recorded attacks related to the GoAnywhere MFT vulnerability, marking a significant 91% increase compared to the previous month. The healthcare industry has been particularly targeted, with 129 organizations being affected. These attacks highlight the severity and real-world impact of the CVE-2023-0669 vulnerability in terms of facilitating ransomware campaigns.
3CX VOIP Desktop Client (CVE-2023-29059)
The CVE-2023-29059 vulnerability is associated with a supply chain attack known as “SmoothOperator” that targets the 3CX VoIP desktop client. This attack involves the exploitation of a vulnerability within the 3CX VoIP desktop client software, which allows an attacker to execute arbitrary code on the targeted system.
The SmoothOperator attack campaign aims to compromise the software’s update mechanism, injecting malicious code into legitimate updates. When users download and install these compromised updates, the attacker gains unauthorized access to their systems.
Cybercriminals may exploit CVE-2023-29059 as a means to launch ransomware attacks on unsuspecting targets. By compromising the update mechanism of the 3CX VoIP desktop client, attackers can inject malicious code into legitimate software updates. Users who download and install these compromised updates may unknowingly grant unauthorized access to their systems, providing an opportunity for ransomware to be deployed.
Conclusion
And so, our journey into the realm of vulnerabilities ransomware groups use comes to a close. We have dived deep into the dark secrets behind ransomware attacks. We explored the top 10 vulnerabilities that these malicious groups exploited in recent years.
The statistics have painted an unpleasant picture of the threat landscape. We have witnessed the criticality of the vulnerabilities that came out in 2021 and 2022. It revealed the vulnerabilities most commonly leveraged by ransomware groups. Microsoft, with its widespread usage and products like Windows and Exchange Server, has been a prime target. RCE vulnerabilities have emerged as the favored weapon of these nefarious actors. The picture painted with these statistics emphasizes the average cost of a successful ransomware attack, with estimates ranging between $570,000 to $812,360.
We have also encountered some of the top ransomware groups, such as LockBit. They have plundered with their sophisticated techniques and advanced encryption algorithms. The impact of their attacks has been substantial. It left organizations grappling with compromised data, financial losses, and reputational damage.
But amidst the darkness, we have found a glimmer of hope. Armed with knowledge and empowered by SOCRadar Extended Threat Intelligence platform. With it, we can fortify our digital defenses and fight back against ransomware attacks. SOCRadar’s advanced threat intelligence capabilities provide real-time insights into emerging threats, vulnerabilities, and malicious activities. It enables organizations to detect and respond to potential ransomware attacks before they cause significant harm.
By leveraging SOCRadar’s comprehensive External Attack Surface Management (EASM) solution, businesses can gain a holistic view of their external attack surface. They can identify potential entry points for ransomware attacks. With continuous monitoring and threat intelligence integration, organizations can proactively detect vulnerabilities and prioritize their remediation efforts. In return, they can mitigate the risk of ransomware incidents.
Moreover, SOCRadar EASM offers automated asset inventory, vulnerability assessment, and threat intelligence integration. It simplifies risk management processes and enhances incident response capabilities. By utilizing SOCRadar’s comprehensive suite of security tools, organizations can significantly reduce their exposure to ransomware threats and strengthen their overall security posture.
As we bid farewell to this epic adventure, let us remember that the battle against ransomware is ongoing. The threat landscape is constantly evolving. New vulnerabilities and techniques will continue to emerge. But with constant vigilance, proactive security measures, and trusted allies like SOCRadar Extended Threat Intelligence, we can navigate the dangers and safeguard our digital kingdoms.
The battle against ransomware may be daunting, but we are not alone. Together, with the knowledge and preparedness provided by SOCRadar EASM, we shall emerge victorious. We will be fortified against ransomware attacks and resilient in the face of evolving cyber threats. The time to fortify our defenses and protect what is ours is now. The battle against ransomware continues, and with SOCRadar EASM as our shield, we shall prevail.



































