
Lessons Learned From Israel-Hamas Conflict: A Cybersecurity Perspective
The Israel-Hamas conflict, which started with the surprise attack of Hamas militants on Israeli territory on October 7, escalated in a very short time with Israel’s declaration of war and is continuing. This tragic event, which is still ongoing, naturally attracted the attention of the world.
Cyberspace, which is now a new frontier of wars, has begun to escalate in parallel with the physical world. We tried to monitor the conflict by following this environment throughout the last month and covering the events in our live blog. In addition to monitoring more than a hundred hacktivist groups and threat actors, observing the direction of events and providing insights to our readers, we also informed our platform users about news that concerns their organizations and sectors.
The article Reflections of the Israel-Palestine Conflict on the Cyber World, in which we tried to draw a framework with certain milestones, forms the basis of this text. Still, it is a difficult article to extract the important points. Therefore, let’s take a look at the situation once again by compiling the important facts and lessons to be learned in this article.
Cyber World: A New Frontline
The Israel-Hamas conflict has unequivocally shown that the digital realm is as much a battleground as any physical territory. As missiles soared through the skies and cities braced for airstrikes, the invisible world of the internet was equally charged with digital offensives. Both pro-Israel and pro-Palastine hacktivists and nation-sponsored actors harnessed the vast capabilities of the internet, launching cyberattacks in pair with the physical operations. This simultaneous warfare not only emphasizes the growing importance of cyber defense but also showcases the changing dynamics of modern conflicts. It clearly shows the need for cyber defense mechanisms, recognizing that future wars may be won or lost in the digital realm.
While we often perceive the cyber world as mirroring the physical realm, it’s worth noting that the significant number of rocket attacks conducted by Hamas on the first day of the conflict can be likened to a physical DDoS attack aimed at overwhelming Israel’s Iron Dome defense system. In this context, it’s more akin to two interconnected planes of action that cannot be analyzed in isolation from each other.
Resurgence of Hacktivism
The Israel-Hamas conflict witnessed a marked revival of hacktivism. Various groups, driven by the tragic events on the ground, took to the digital space to voice their opinions, support their side, or simply disrupt the opposition. This renewed vigor in hacktivism underscores its potency as a means for non-state entities to shape global perceptions and influence international events. The conflict served again as a testament to the fact that in today’s digital age, a keyboard can be as powerful as a missile in swaying global narratives.
Below is a mapping of the threat groups involved in the Israel-Palestine conflict. You can navigate around the mind map by dragging and dropping.
A similar resurgence took place on the Ukrainian-Russian war side, but it did not spread to such a global level. Another similar resurgence was also observed during the Arab Spring.
The Global Reach of Cyber Conflicts
The digital ripples of the Israel-Hamas conflict were felt far and wide, transcending the geographical confines of the Middle East. Cyberattacks stemming from this conflict were reported in various corners of the globe, highlighting the boundless nature of cyber warfare. This global reach of cyber conflicts serves as a stark reminder that in the digital age, regional disputes can escalate into global cyber crises, affecting nations and organizations far removed from the epicenter of the conflict.
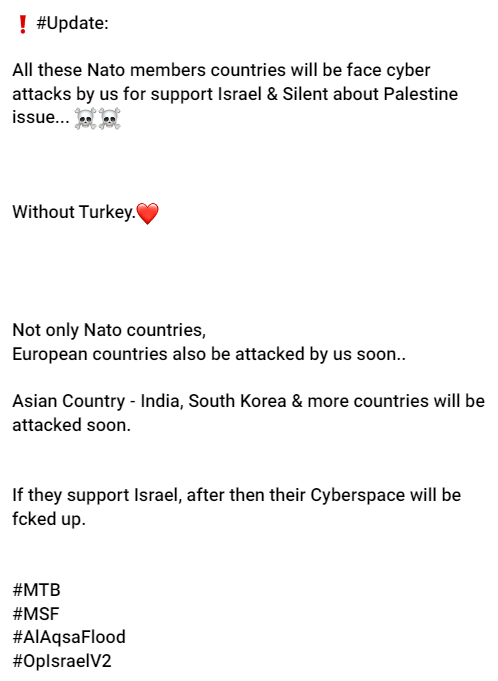
Indeed, numerous regions around the globe, including NATO members, Japan, Singapore, Indonesia, Pakistan, Bangladesh, Malaysia, India, Arab countries, Iran, and Russia, were either attacked or became origins of assaults in this cyber conflict. Surprisingly, there were days when India faced more cyberattacks than even Israel.
Every Organization May be a Target
The indiscriminate nature of cyber warfare during the Israel-Hamas conflict underscored a chilling reality – no organization was safe. From pivotal government institutions to small private enterprises, the digital onslaught was relentless and widespread. Civil infrastructure, Healthcare, and Education continued to be important targets for hacktivists. This universal vulnerability reiterates the pressing need for organizations, irrespective of their size or domain, to prioritize cybersecurity.
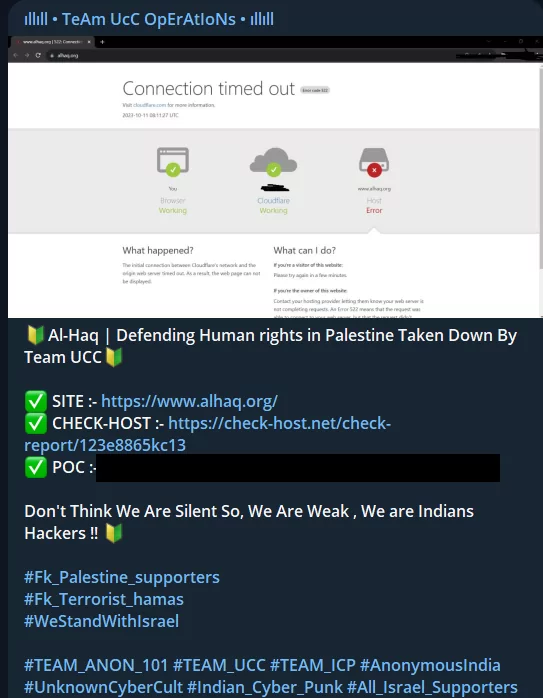
Although human rights organizations, foundations and associations were targeted for showing support in some sense, many organizations were also targeted solely because of the political stances of the countries they were based in.
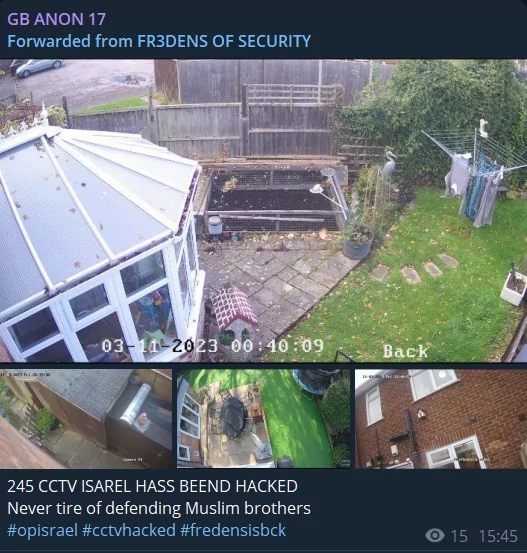
The Evolving Tactics of Hacktivists
The Israel-Hamas conflict showed the speed at which hacktivists change and introduce new techniques. They employed various strategies, such as utilizing botnets and setting up automated attacks, to boost their impact. Moreover, to amplify their efforts, hacktivist groups distributed tools and scripts to their supporters. They set specific objectives, fostered collaboration among different groups, and even encouraged individuals without technical expertise to participate in activities like email spamming and spreading false information. This indicates that our cybersecurity methods should also adapt quickly.
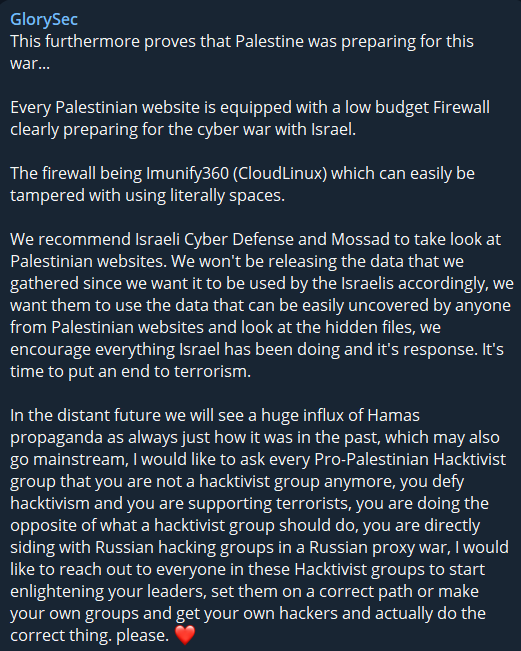
One example was the attack methods and vulnerabilities that the pro-Palestinian GlorySec hacktivist group shared with Israeli authorities and other pro-Israeli hacktivists. Pro-Palestinian hackers are also working to increase their efficiency and numbers by sharing their tools and TTPs with their followers.
Expansion of the Hacktivist Arsenal
As mentioned earlier, not only have the methods used by hacktivists advanced and diversified, but their toolkit has also broadened. Throughout the conflict, hacktivists utilized various strategies, from Distributed Denial-of-Service (DDoS) attacks to data breaches. This might be attributed to the widespread availability of such tools, with numerous free or paid botnet services, scripts, stealers, and even ransomwares being shared on Telegram channels and hacker forums. The wide range of tools they have access to suggests that hacktivists are growing in sophistication, presenting a considerable challenge for those in cybersecurity.
Involvement of Ransomware Groups
Ransomware, typically used for financial gain, may have found a new purpose during the conflict. Ransomware attacks during the conflict served not solely for monetary benefits but as a means of disruption and making political statements. This shift in ransomware usage underscores its versatility as a tool and the need for organizations to be prepared against such threats, regardless of their perceived value to attackers. Moreover, while cheaper and modular ransomware is emerging, even ransomware groups can choose a side in the cyber war.
Hacktivism’s Echo in Asia
As mentioned, while the conflict was centered in the Middle East, its ripple effects were felt in the world, with several hacktivist groups from the region getting involved. These groups launched attacks, either in solidarity with one side or the other, showcasing the global reach once again and influence of hacktivism.
The special case is that while activities and groups that can be seen as “hacktivist,” such as the Anonymous group and the Wikileaks incident, come from the Western hemisphere, after the 2010s, with the Arab Spring, the heart of hacktivism began to beat in Asia. In this cyber war, most of the groups involved, especially South Asian hacktivists, are eastern hemisphere-based collectives.
While this highlights the interconnectedness of global events and the role of hacktivism in shaping international narratives it also showcases the greater hacktivist stance in the eastern hemisphere of the world.
Involvement of APT Groups
While hacktivist movements are prominent, they can sometimes overshadow other more covert operations, serving as distractions.
The gravest cyber threats often emanate from Advanced Persistent Threat (APT) groups. Their involvement underscores the strategic importance of the cyber domain in modern warfare. This evolving dynamic is evident in the Israel-Hamas conflict. For instance, the pro-Hamas hacktivist group utilized the BiBi-Linux Wiper malware against Israeli targets, potentially named after the Israeli Prime Minister’s nickname.
However, beyond hacktivist groups, APT entities like Moses Staff, a pro-Iranian group, have been active. They’ve resumed their operations, continuing their campaigns with data breaches and disruptive attacks. The presence and activities of such APT groups highlight the intricate and multi-faceted nature of cyber warfare in the context of broader geopolitical conflicts.
DDoS is Still by Far the Most Common Attack
During the conflict, many hacktivists continued to prefer Distributed Denial-of-Service (DDoS) attacks. Even with more advanced attack techniques available, the straightforwardness and efficiency of DDoS attacks make them a primary choice for disruption.
This preference for DDoS was also evident in the Ukraine-Russia war. It appears that hacktivist groups have brought this reflex to the current conflict, swiftly shifting their long-standing practices to new targets. Israeli defense mechanisms faced significant challenges, and various organizations and nations became the recipients of these digital onslaughts for different reasons.
It underscores the importance for entities to focus on bolstering defenses against such prevalent and potent cyber threats.
Track Dark Web Activity with SOCRadar
SOCRadar’s Cyber Threat Intelligence and Digital Risk Protection tools, you can easily monitor threat actor activities across all web surfaces, including Telegram channels.
The Digital Risk Protection tool by SOCRadar streamlines the process of tracking threat actor movements. The Dark Web Monitoring feature instantly offers relevant details about products and technologies linked to your digital assets. Meanwhile, Dark Web News provides key updates from deep and dark web forums, social media, and communication channels like Telegram, accompanied by screenshots and text.
Find out if your data is vulnerable to threat actors and act to safeguard your digital assets. SOCRadar regularly scans the internet to spot new Telegram groups that might contain your company’s exposed data. Plus, it quickly notifies you about any data related to your organization.



































