
A Review of 2023 – 26,447 CVEs, 44 Days to Exploit, and Ransomware Onslaught
As we reflect on the cybersecurity journey of 2023, we uncover valuable lessons that shape our understanding of the ever-changing landscape of threats and vulnerabilities. These insights form the bedrock of our efforts to fortify risk management strategies in the coming year. In this exploration of the 2023 CVEs, we take a closer look at specific instances that left an indelible mark on the threat landscape.
Notably, our attention is drawn to the looming shadow of ransomware, a persistent menace that gained prominence in the cybersecurity narrative. This review is rooted in Qualys’ meticulous research, providing a deeper understanding of the vulnerabilities that defined the intricate landscape of 2023.
Consider this article as a compass in navigating the complex cyber terrain. Through a discerning perspective, we guide you through the twists and turns of the cybersecurity landscape, shedding light on critical aspects that demand attention. By reflecting on the prevailing threats of the past year, our aim is to furnish you with proactive insights, empowering you to face the challenges that await in 2024 with confidence and readiness.
Vulnerability Landscape of 2023: A Deep Dive into the Numbers
The researchers initially report that the year 2023 witnessed a surge in disclosed vulnerabilities, with a staggering 26,447 CVEs brought to light. This marked an increase of over 1,500 from the previous year, continuing the trend of surpassing the vulnerability count annually.
Surprisingly, less than 1% of these vulnerabilities fell into the highest-risk category – vulnerabilities either exploited, actively targeted by threat actors, or with confirmed evidence of exploitation in the wild.
Addressing this challenge, the SOCRadar Vulnerability Intelligence module, designed to monitor vulnerability updates and trends, now incorporates EPSS scores into vulnerability intel cards. EPSS (Exploit Prediction Scoring System) simplifies the complex task of predicting the likelihood of a CVE being exploited in the wild within the next 30 days. You can combine EPSS and SVRS (SOCRadar Vulnerability Risk Score) for a more comprehensive understanding of the threat landscape.
As we proceed, let’s see which vulnerabilities are considered high-risk and demand special attention:
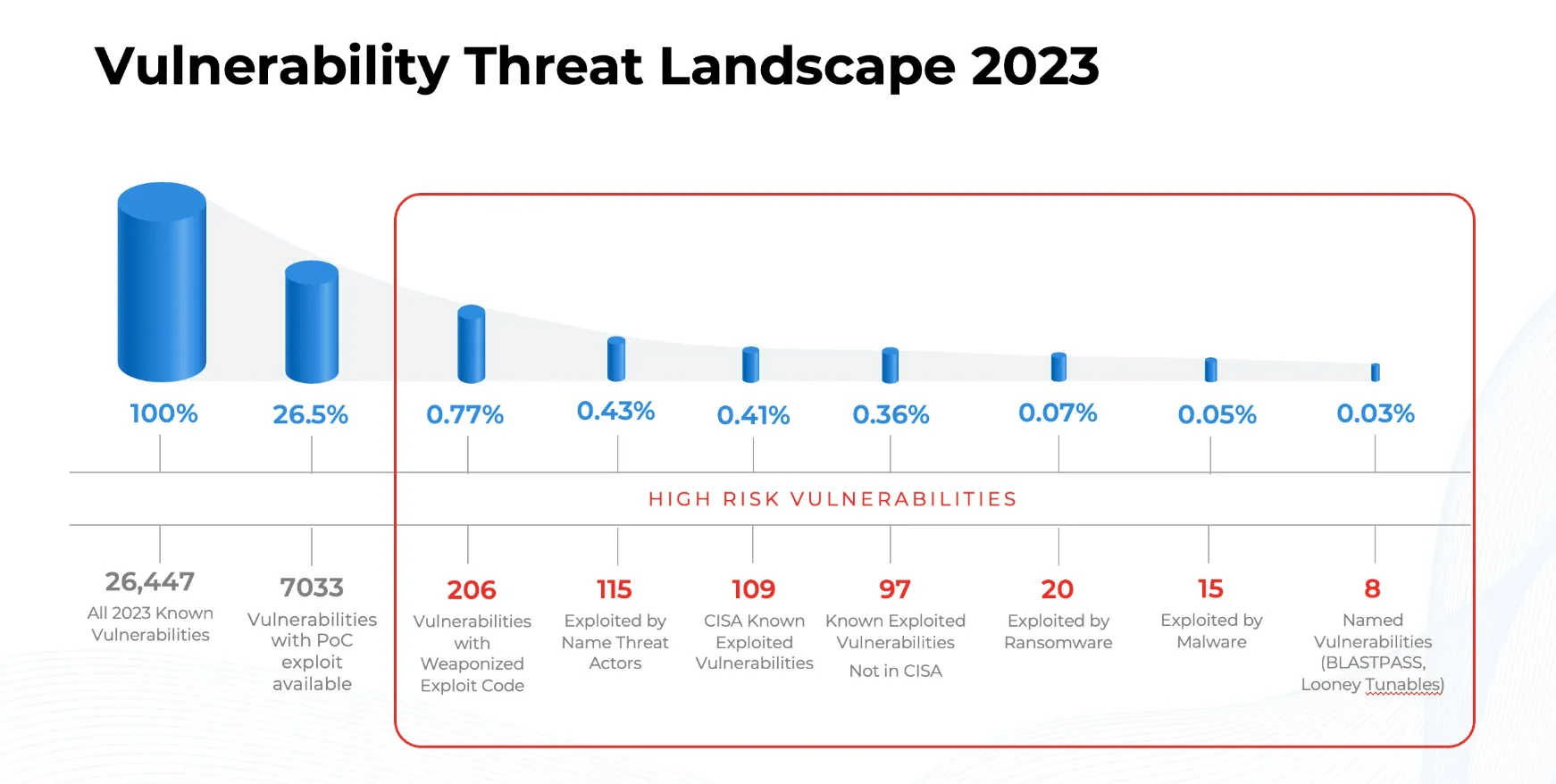
High-risk CVEs of 2023 (Qualys)
Within this critical segment:
- 206 vulnerabilities stood out, armed with weaponized exploit code, posing a significant threat due to their high likelihood of successful exploitation.
It is noteworthy that the timeline between public disclosure and exploit availability is approximately 14 days. While the figure of 206 may seem reassuring among the sea of over 26,000 CVEs surfacing in 2023, it remains a substantial number, presenting a potential avenue for threat actors to wreak havoc.
Beyond these high-risk vulnerabilities, an additional 7,000 vulnerabilities had Proof-of-Concept (PoC) exploit code. Although capable of exploitation, the lower quality of the exploit code may diminish the likelihood of a successful attack.
Leveraging SOCRadar’s Vulnerability Intelligence provides a window into detailed insights and updates about these vulnerabilities, letting organizations know if there are exploits available and enabling them to stay ahead of potential breaches.
Further categorization reveals that high-risk vulnerabilities comprised:
- 115 vulnerabilities subjected to routine exploitation by threat actors.
- 109 vulnerabilities listed in the CISA KEV, acknowledging their susceptibility to exploitation.
- 97 vulnerabilities exploited in the wild but not listed in the CISA KEV due to specific inclusion criteria.
This is because exploitation is not the only criteria for inclusion in the KEV Catalog; we have discussed this in detail in another blog post about the timeframe problems caused for organizations solely relying on the KEV Catalog for exploitation insights.
- Adding to the complexity, 20 vulnerabilities succumbed to exploitation by ransomware groups, while 15 vulnerabilities fell prey to the schemes of malware and botnet groups. In summary, despite being a subset of the vast vulnerability pool, more than 50% of the 206 high-risk vulnerabilities were exploited by threat actors, ransomware, or malware.
Top Vulnerability Types of 2023
A significant revelation emerges – over a third of the identified high-risk CVEs in 2023 have the potential for remote exploitation. The top five vulnerability types, constituting more than 70% of the total discoveries, are dominated by Remote Code Execution (RCE), followed by Security Feature Bypass and Buffer Manipulation.
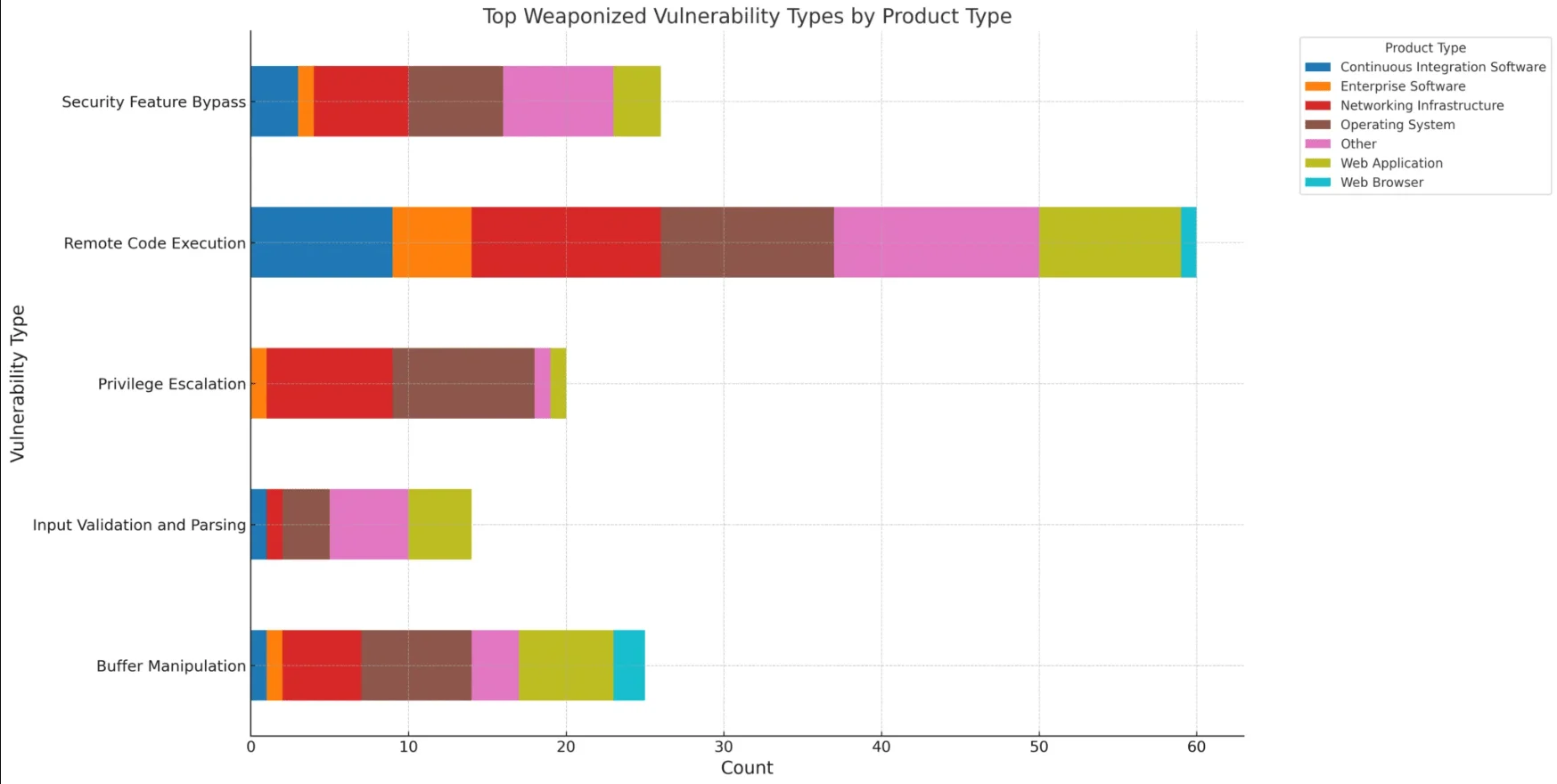
Top exploited vulnerability types and categorization by product (Qualys)
An interesting observation is that, in our 2023 CISA KEV Catalog Review, Privilege Escalation vulnerabilities were the most prevalent type exploited by threat actors and subsequently added to the Catalog. However, in Qualys’ research encompassing almost all the vulnerabilities identified throughout the year 2023, Privilege Escalation ranks fifth among the top five prevalent vulnerability types.
However, Privilege Escalation consistently maintains its prominence and does not drop from the top ranks in any context. Noteworthy findings from the research highlight three prominent MITRE ATT&CK tactics – exploitation of remote services, exploitation of public-facing applications, and exploitation for privilege escalation. These tactics collectively underscore the criticality of a comprehensive vulnerability management strategy, urging organizations to fortify their defenses against threats targeting network devices and web applications.
44 Days to Disaster: The Exploitation Timeline for High-Risk CVEs in 2023
Researchers reported that the mean time to exploit vulnerabilities stands at a mere 44 days, signifying a race against time for defenders to secure their digital landscapes.
Yet, beneath this average lies a more urgent narrative. In numerous instances, attackers wasted no time capitalizing on vulnerabilities. Zooming in on the crucial 0 to 25-day period, an astonishing 25% of security vulnerabilities became immediate targets, with exploits published on the same day as the public disclosure of the vulnerability. The data further unveils that 75% of vulnerabilities fell victim to exploitation within a mere 19 days of publication.
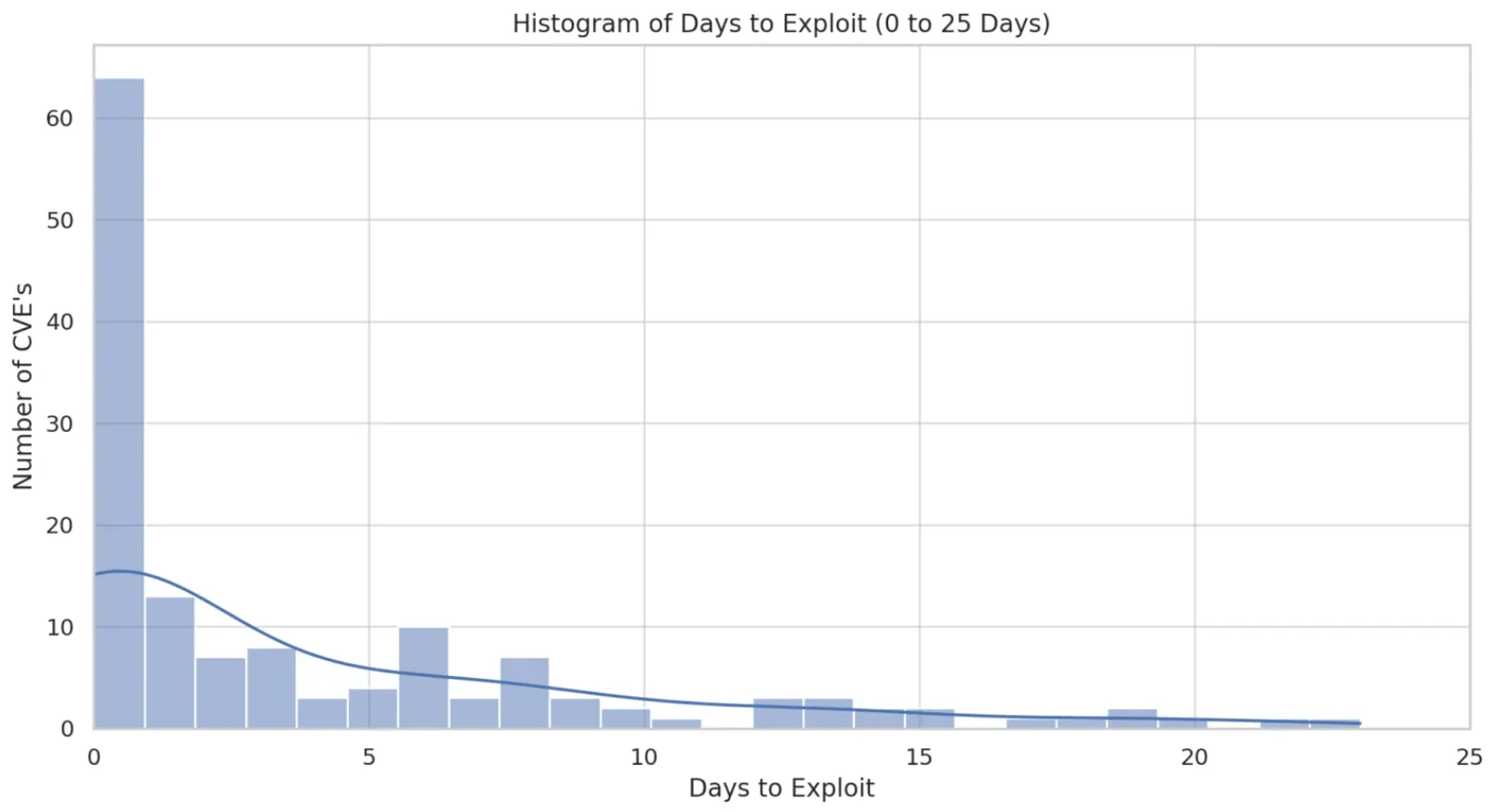
Vulnerabilities exploited during the first 25 days of their publication (Qualys)
This time-sensitive scenario underscores the importance for organizations to swiftly prioritize and address critical vulnerabilities, adopting a proactive stance toward patch management and threat intelligence.
Enter the SOCRadar XTI platform, where the Vulnerability Intelligence module diligently tracks identified vulnerabilities, providing timely updates. Complemented by the Attack Surface Management (ASM) module, the platform also ensures real-time monitoring of digital assets. SOCRadar’s alerts offer quick insights into emerging security issues, including vulnerabilities that could impact your organization.
By leveraging SOCRadar’s capabilities, organizations gain quick insights, facilitating a seamless response process. This empowers them to prioritize patches effectively, fortify defenses, and proactively prevent potential exploitation. With SOCRadar’s Vulnerability Intelligence, detailed insights and updates about vulnerabilities, along with the information on available exploits, are at your fingertips, enabling a proactive and vigilant cybersecurity posture.
Decoding the Most Exploited CVEs of 2023: A Ransomware Perspective
In the labyrinth of cyber threats that defined 2023, certain vulnerabilities emerged as prime targets for exploitation, paving the way for insidious ransomware campaigns.
Leading the notorious lineup is CVE-2023-34362, the MOVEit Transfer SQL Injection vulnerability. This vulnerability, leveraged in Cl0p Ransomware attacks, has left its mark on at least 60 million individuals. The Cl0p threat group’s utilization of MOVEit breaches underscores the impact of this exploit on a significant scale.
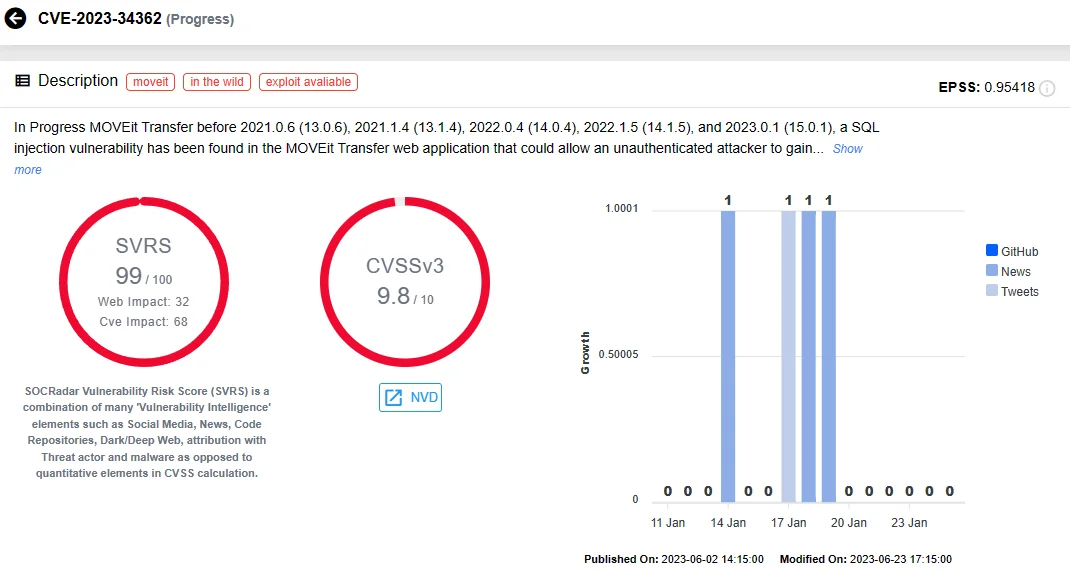
SOCRadar vulnerability card for CVE-2023-34362
Another player in the ransomware arena is CVE-2023-0669, an RCE vulnerability in Fortra GoAnywhere Managed File Transfer (MFT) service. Its emergence led to a staggering 91% increase in ransomware attacks. The vulnerability has been exploited by ransomware groups like ALPHV (BlackCat) and LockBit, alongside Cl0p.
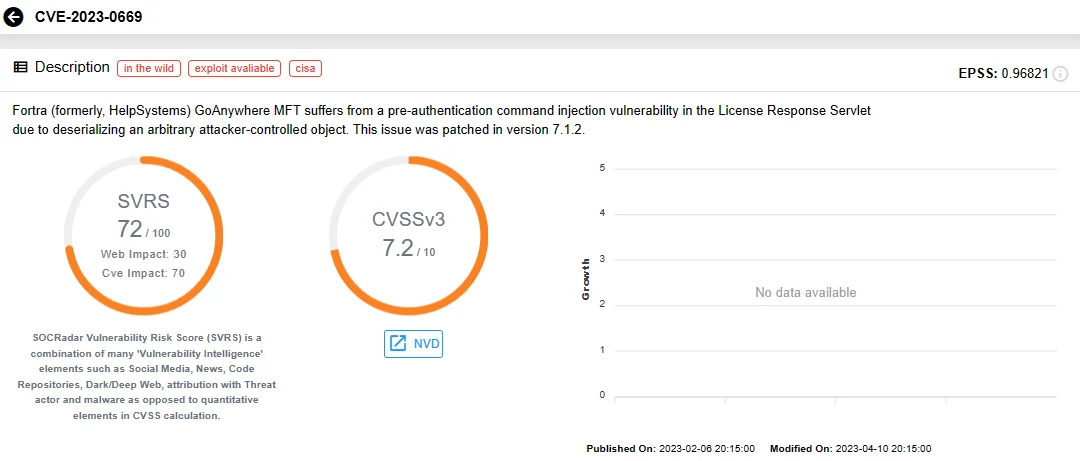
SOCRadar vulnerability card for CVE-2023-0669
CVE-2023-27350, an Improper Access Control vulnerability affecting PaperCut, marked its presence by becoming a conduit for ransomware spread, featuring Cl0p and Bl00dy Ransomware in its exploit narrative.
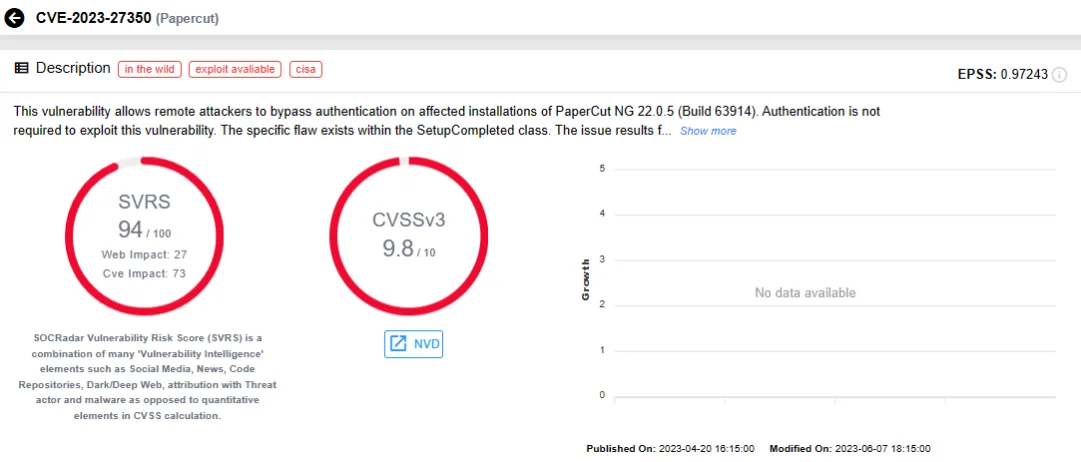
SOCRadar vulnerability card for CVE-2023-27350
CVE-2023-24880, a Windows SmartScreen Security Feature Bypass vulnerability, has emerged as a medium severity zero-day, and has been fixed in March 2023 Patch Tuesday. The vulnerability was under active exploitation as it was disclosed; the CISA KEV Catalog confirms that it has been exploited by ransomware actors.
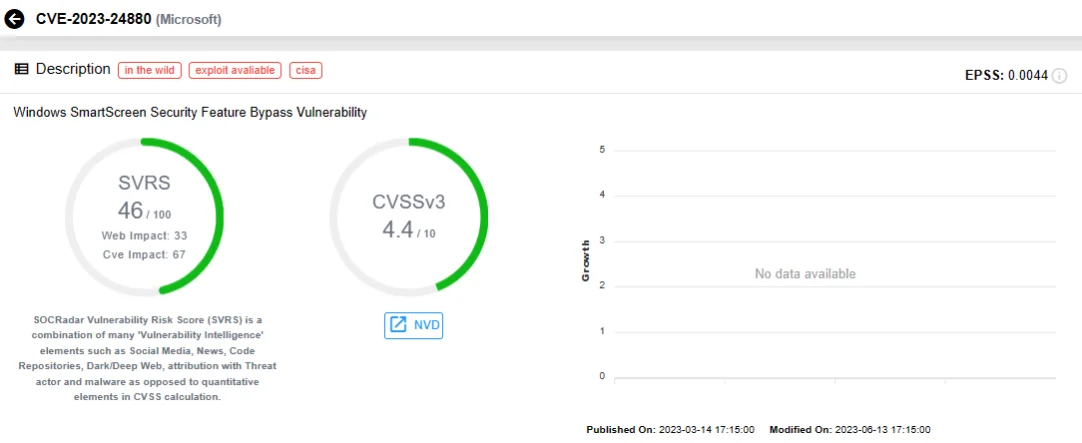
SOCRadar vulnerability card for CVE-2023-24880
CVE-2023-28252, another Windows zero-day vulnerability, impacting the Common Log File System (CLFS) Driver, fueled Privilege Escalation exploits. CISA added this vulnerability to its KEV list in April 2023, and it played a role in distributing the Nokoyawa Ransomware.
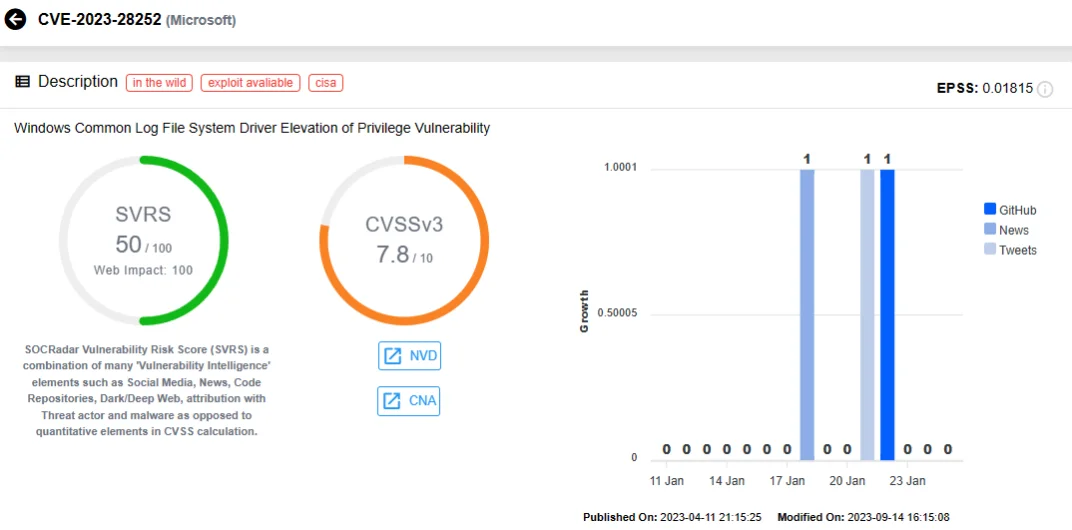
SOCRadar vulnerability card for CVE-2023-28252
Linked to a supply chain attack dubbed “SmoothOperator,” CVE-2023-29059 targeted the 3CX VoIP desktop client. Exploited for arbitrary code execution, it facilitated ransomware attacks through compromised software updates. It stands out as the only vulnerability in this list that is not included in the CISA KEV Catalog.
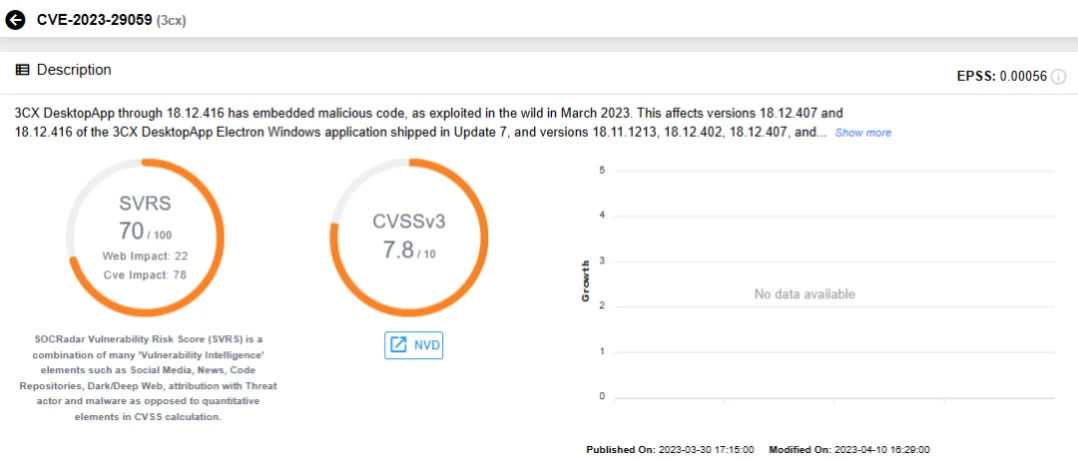
SOCRadar vulnerability card for CVE-2023-29059
Through SOCRadar’s ASM, you can access the CISA KEV Check and Ransomware Check features. These features can help verify whether a vulnerability has been cataloged by CISA in KEV or exploited in ransomware operations; you can subsequently access more information about these vulnerabilities, and if these vulnerabilities are currently affecting your organization, you can acquire actionable insights for a seamless remediation process.
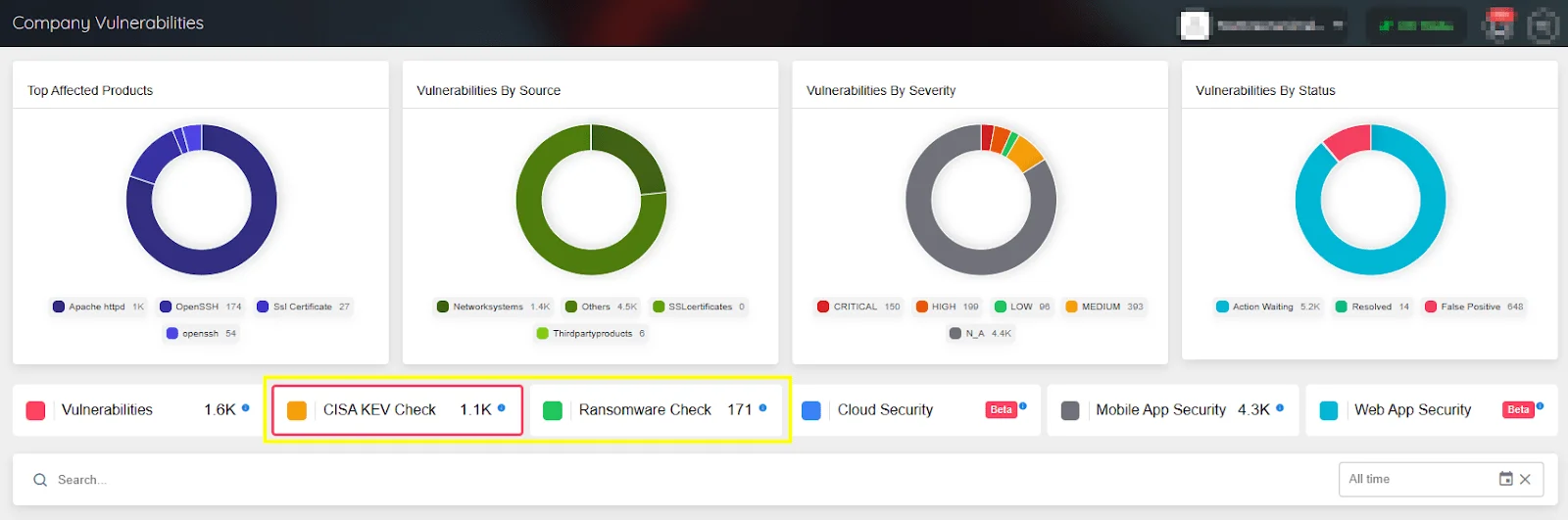
SOCRadar ASM – CISA KEV Check and Ransomware Check features
Additionally, several other vulnerabilities gained prevalence in their exploitation in 2023, although their involvement in ransomware campaigns remains unclear. Notable mentions include:
- CVE-2023-20887 (VMware Aria Operations for Networks Command Injection Vulnerability)
- CVE-2023-22952 (SugarCRM RCE Vulnerability)
- CVE-2023-23397 (Microsoft Office Outlook Privilege Escalation Vulnerability)
- CVE-2023-2868 (Barracuda Networks ESG Appliance Improper Input Validation Vulnerability)
Feel free to explore detailed blog posts related to these CVE by clicking on their identifiers. For swift insights, you can also leverage the AI insights feature on the SOCRadar platform by searching for these vulnerabilities:
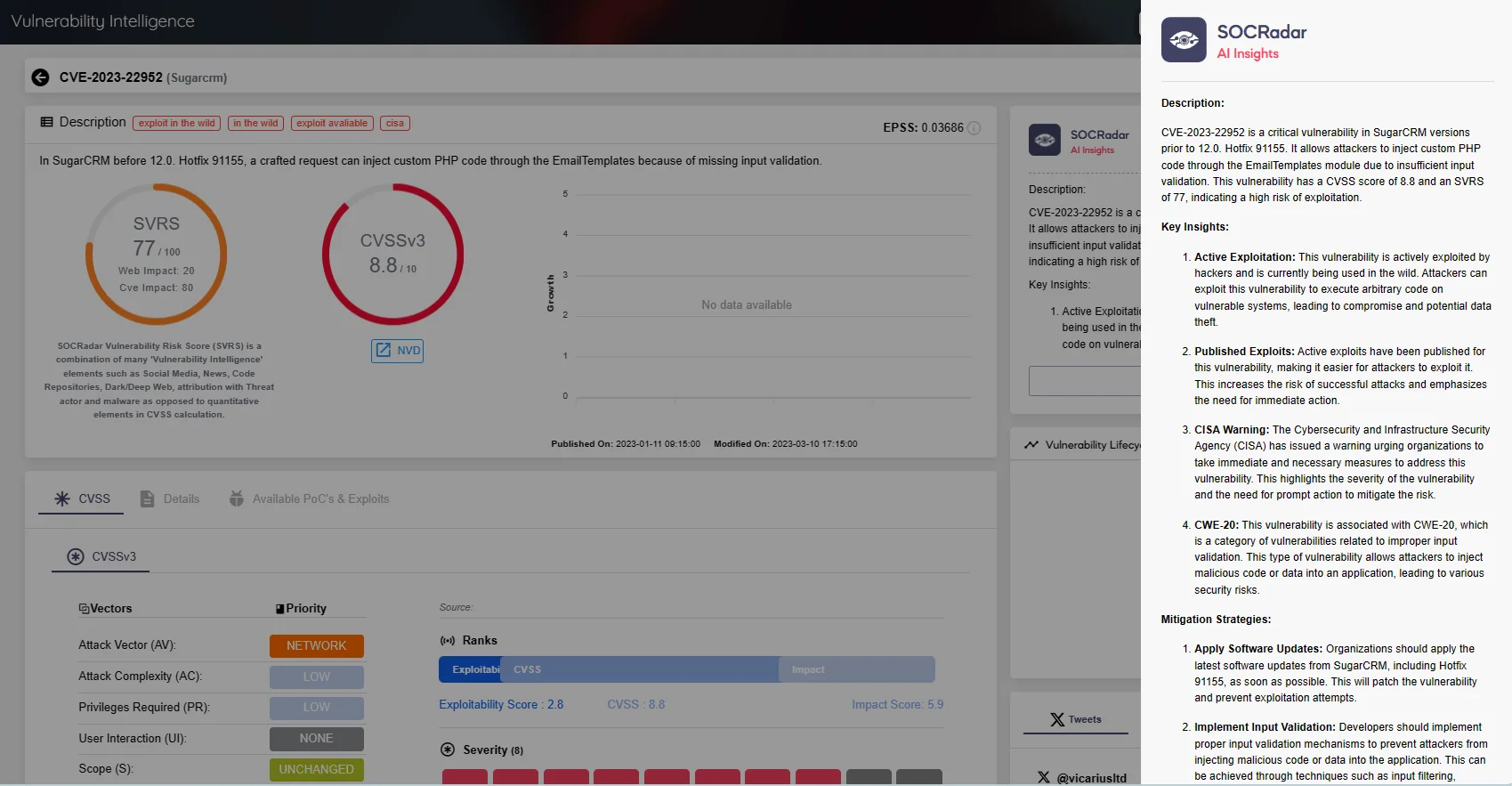
AI insights for CVE-2023-22952 (SOCRadar Vulnerability Intelligence)
A striking observation is that, more than half of the vulnerabilities labeled as ‘most exploited’ by researchers found their sinister purpose in ransomware attacks, underscoring the prevalent financial motivations behind these cyber threats.
As highlighted in our 2024 Cybersecurity Predictions blog post, that draws insights from Fortinet, the ransomware threat actors’ focus shifts from encryption to Denial-of-Service (DoS) and extortion. Due to this fact, the increased prevalence of vulnerabilities being exploited by ransomware groups, and the growing creativity in ransom threats, it is crucial to stay ahead of threats proliferating throughout your industry by taking a proactive stance.
You can check out SOCRadar Labs’ Industry Threat Landscape Report page to get a free report on a variety of industries. These reports include information about the prevalence of specific cyber threats targeting the industry, as well as details on ransomware groups focusing on the sector, along with the top target countries.
Industry Threat Landscape Report on SOCRadar Labs
Conclusion
As the number of disclosed vulnerabilities surpasses previous years, organizations face a daunting challenge in fortifying their digital perimeters.
Key insights unveil the prevalence of high-risk vulnerabilities, with 1% of overall CVE discoveries in 2023 posing threats due to active exploits. Furthermore, time proves to be of the essence, with the mean time to exploit vulnerabilities standing at a mere 44 days. The urgency is further magnified by instances where exploits materialize on the very day of disclosure, indicative of an evolving threat landscape demanding swift responses.
Unveiling the most exploited vulnerabilities of 2023, we observe a nexus with ransomware operations. Notable instances like CVE-2023-34362 (MOVEit SQLi vulnerability) and CVE-2023-0669 (GoAnywhere MFT RCE vulnerability) became gateways for widespread ransomware attacks, urging organizations to prioritize patch management and threat intelligence.
As we glance toward the future, the proactive adoption of a multifaceted vulnerability management approach becomes critical. In navigating these challenges, SOCRadar emerges as a beacon of defense. Through its Vulnerability Intelligence and Attack Surface Management modules, organizations can gain real-time insights, ensuring the safety of their digital perimeter.



































