Dark Web Profile: Evil Corp
Evil Corp, also known as Indrik Spider, is a pro-Russian hacktivist group that is involved in large-scale financial cyberattacks. Since 2007, Evil Corp has constantly evolved its tactics, ranging from banking fraud to advanced ransomware attacks.
Evil Corp uses many malware and has caused hundreds of millions of dollars in worldwide damage. Maksim Yakubets, the group’s leader, has received widespread attention for his links to cybercrime and Russian intelligence services. Their activities have made it one of the most sought-after cybercrime syndicates, with U.S. authorities sanctioning key members and offering a reward for his arrest.
Who is Evil Corp?
Evil Corp is an international cybercrime organization best known for its involvement in banking fraud and ransomware attacks. It is widely regarded as one of the world’s most dangerous hacking groups.
Evil Corp was founded and led by Maksim Yakubets, who established a well-organized cybercriminal operation with ties to Russian financial crime. Yakubets, known for making critical decisions and exerting tight control over the group, later brought in Aleksandr Ryzhenkov, a trusted associate. They worked together on several of Evil Corp’s most significant ransomware strains, including Dridex and WastedLocker.

ImageFX illustration of Evil Corp
According to the NCA report, Evil Corp may have ties to the Russian government and is using its resources for cyber-espionage. According to the findings, the group has shifted to using third-party Ransomware-as-a-Service, such as LockBit, to avoid international sanctions and keep their operations hidden.
Because of its extensive criminal operations, Evil Corp has attracted the attention of international law enforcement. In 2019, the US Treasury Department imposed sanctions on Evil Corp members, focusing on its leader, Maksim Yakubets, who has close ties to Russian intelligence. Yakubets is one of the world’s most wanted cybercriminals, with the US government offering a $5 million bounty for his capture.
How Evil Corp Operates
Evil Corp primarily targets large businesses and financial institutions. They use a combination of spear-phishing campaigns and malware to gain access to internal systems, steal sensitive information, and encrypt data with ransomware.
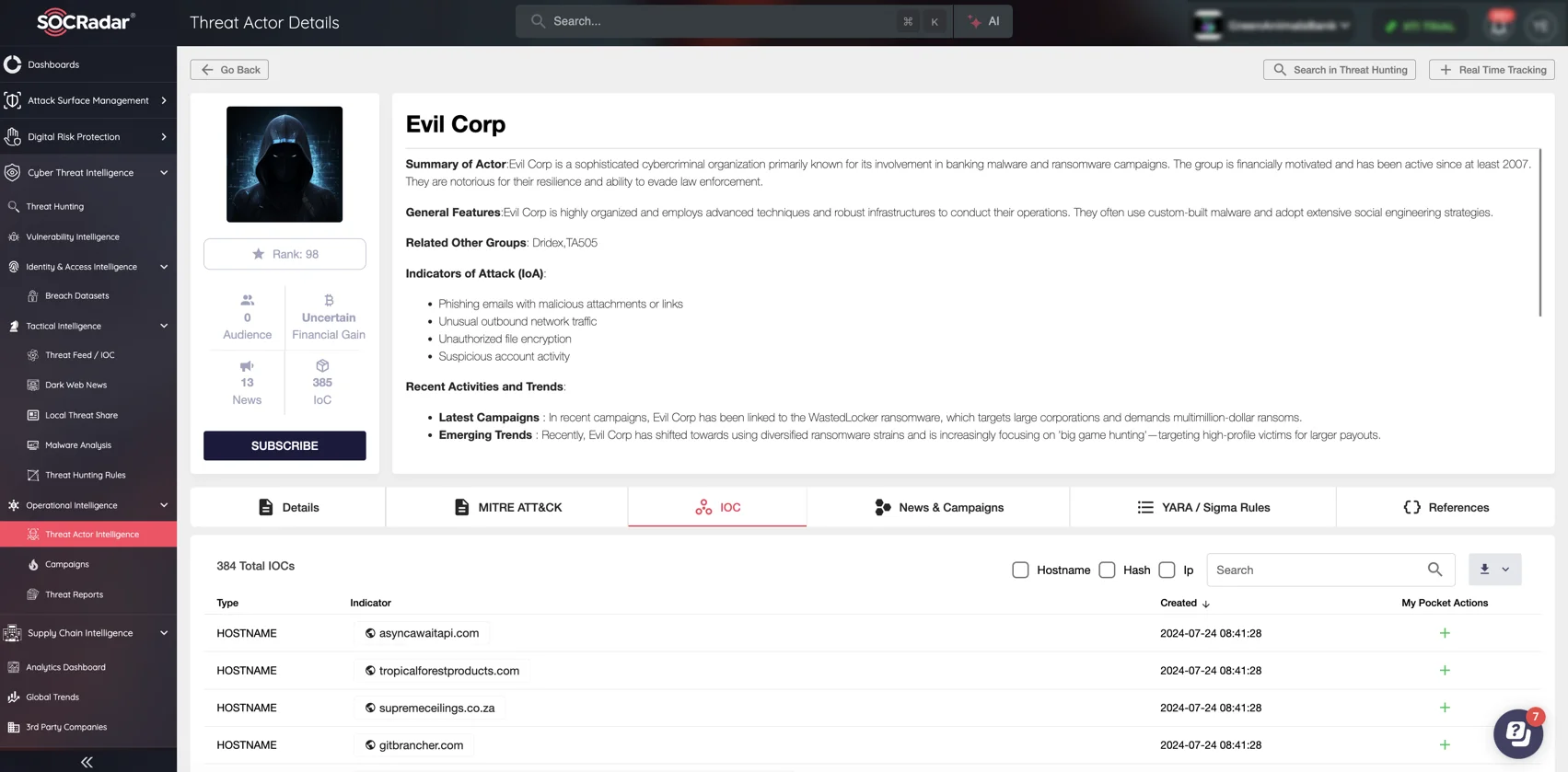
SOCRadar’s Threat Actor Intelligence monitoring threat actors and associated malware
Evil Corp targets international financial institutions and businesses, stealing more than $100 million through a variety of schemes. One of their primary methods is the use of advanced malware, which is distributed via phishing campaigns to steal banking credentials and automate financial theft.
Evil Corp is known for its adaptability and evasion techniques. After being sanctioned by the US government, the group frequently changed its ransomware signatures and exploited new vulnerabilities to get around security measures. Their use of malware like Truebot to exploit vulnerabilities in widely used software like Netwrix Auditor has enabled them to create botnets and gain unauthorized access to systems all over the world.
Associated Malware
Evil Corp is infamous for creating some of the most notorious malware in the cybercriminal landscape. Below are the key tools used by the group:
- Dridex: A highly adaptable banking trojan that was the foundation of Evil Corp’s financial fraud campaigns. Dridex infected banks worldwide, allowing the group to siphon off millions of dollars.
- BitPaymer: This ransomware was used in Evil Corp’s pivot to extortion-focused attacks, targeting large enterprises and demanding hefty ransoms.
- WastedLocker: A ransomware strain that targets high-value organizations, encrypting their files and demanding millions in exchange for decryption keys.
- Truebot: Originally linked to the Silence Group, Truebot is now associated with Evil Corp due to its connection with Grace malware (also known as FlawedGrace). Truebot infections surged in 2022, exploiting the remote code execution vulnerability in Netwrix auditor systems and leveraging Raspberry Robin to create a botnet of over 1,000 compromised systems, learn more aboutTruebot Malware Variants.
Following the United States’ 2019 sanctions, Evil Corp was forced to adapt. The group shifted tactics, abandoning direct ransomware attacks in favor of Ransomware-as-a-Service (RaaS) models such as LockBit. They also started using tools like SocGholish for initial access, which further complicated their operations.
Despite increased scrutiny and pressure from international law enforcement, Evil Corp managed to stay under the radar by constantly changing malware signatures and exploiting new vulnerabilities. Their ability to innovate and diversify their activities has enabled them to remain active on the dark web, recruit insiders, and profit from illegal activities.
The group’s close ties to Russian intelligence services such as the FSB and GRU strengthen their capabilities. These connections not only protect Evil Corp from law enforcement, but also allow it to engage in espionage activities that align with Russian geopolitical interests. Despite sanctions and international pressure, Evil Corp continues to adapt and is one of the most prominent cybercrime organizations operating today.
U.K. Exposes Family Ties in Evil Corp Sanctions
In October 2024, new details in the ongoing investigation into the Russian cybercrime group Evil Corp was revealed. The UK’s National Crime Agency (NCA) disclosed that Maksim Yakubets, the notorious leader of Evil Corp, has been supported by his father, Viktor Yakubets, and his brother, Artem. This information was part of a multinational effort involving the UK, US, and Australia, which led to sanctions against 16 individuals connected to Evil Corp.
His father, Viktor Yakubets, played a key role in laundering money, and his brother, Artem, was also involved, making Evil Corp a tightly-knit family affair. This structure, combined with their sophisticated laundering networks and technical capabilities, enabled them to conduct large-scale financial crimes. Their relationship with the Russian state further solidified their power. Evil Corp’s ties to Russian Intelligence Services, particularly the FSB and GRU, went beyond protection. They conducted cyber-espionage activities on behalf of the Russian government, targeting NATO allies and leveraging state resources to evade law enforcement.
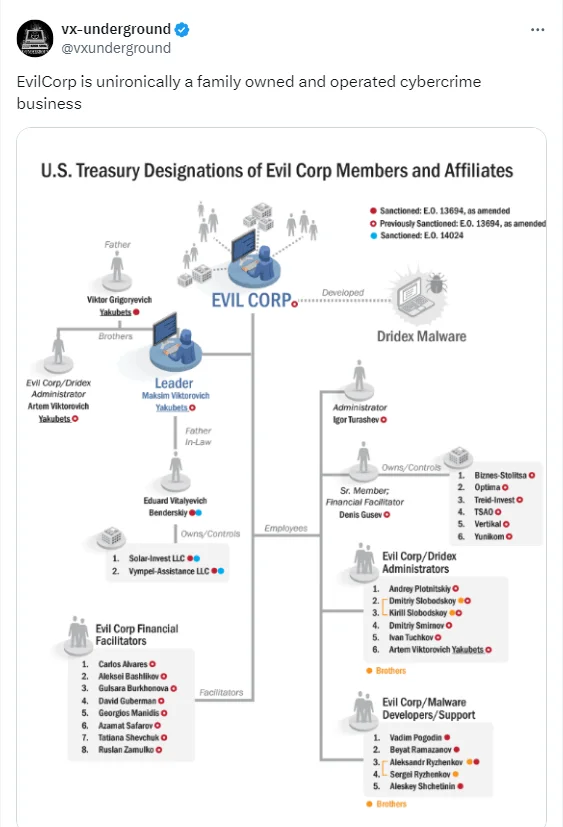
Family ties in Evil Corp (Source: X)
Maksim Yakubets, under scrutiny since 2019, had previously denied his father’s involvement, but the NCA now accuses Viktor of helping to launder stolen funds. The investigation uncovered new ties between Evil Corp and the LockBit ransomware group. These revelations highlight the growing complexity of the cybercrime landscape as law enforcement continues its efforts to bring down Evil Corp, which has stolen hundreds of millions of dollars through global cyber-attacks over the last decade.
SOCRadar’s Dark Web Monitoring for Evil Corp Threats
Evil Corp has established a presence on dark web forums and marketplaces, where they sell stolen credentials, banking information, and ransomware tools. Their participation in the dark web ecosystem enables them to remain anonymous while profiting from illegal activity. Recent investigations have revealed Evil Corp’s recruitment efforts on dark web forums, which target insiders within organizations for information or direct access into internal systems.
Given the group’s sophisticated operations, organizations must remain vigilant against both internal and external threats. SOCRadar’s Advanced Dark Web Monitoring enables organizations to detect and respond to threats originating from groups such as Evil Corp. SOCRadar scans dark web marketplaces, forums, and stealer logs in real time to identify potential data breaches and compromised credentials associated with Evil Corp’s malware campaigns.
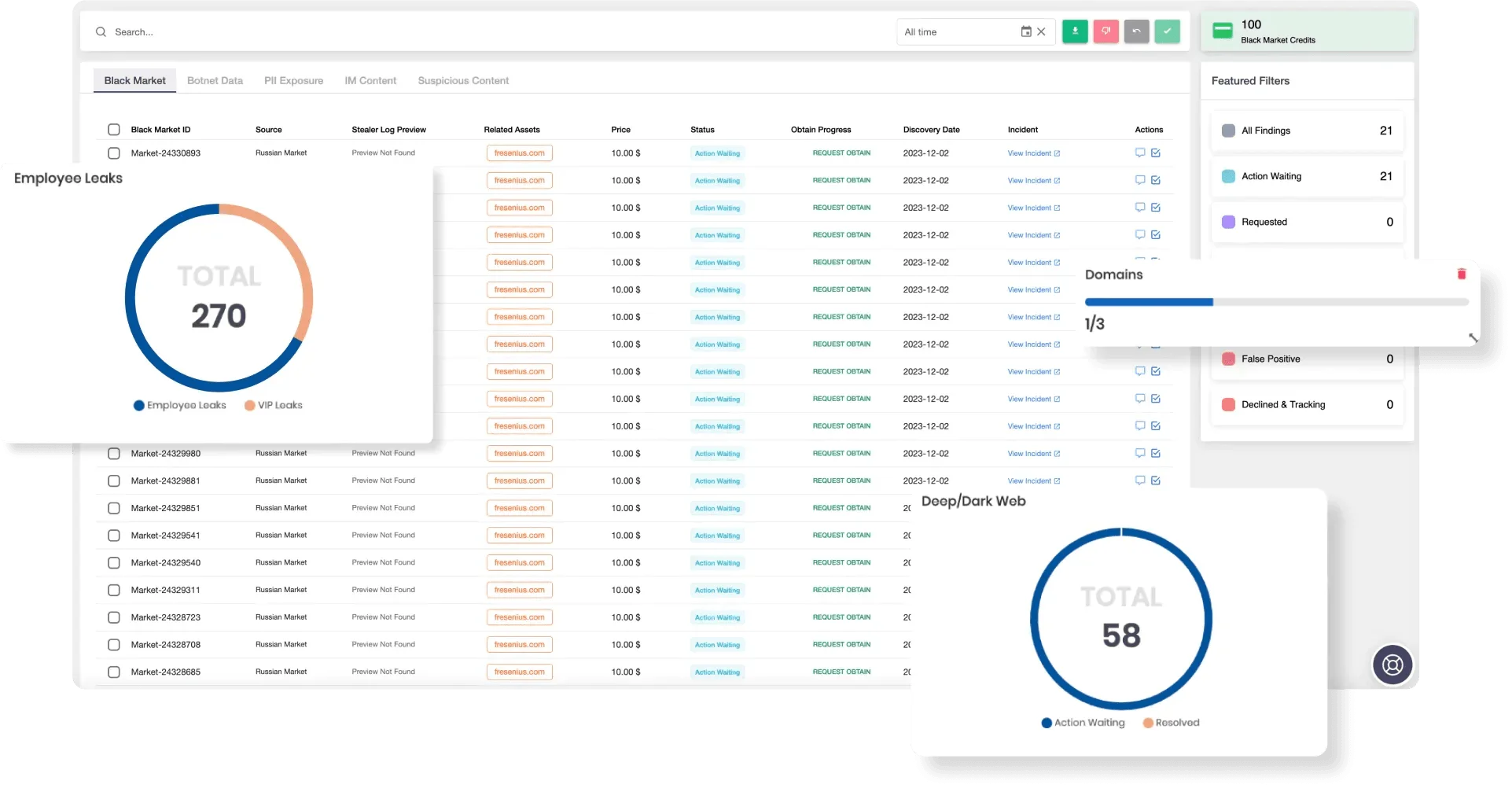
SOCRadar’s Advanced Dark Web Monitoring
SOCRadar continuously monitors the dark web for any mention of your company’s data or intellectual property being sold, ensuring that threats are identified and mitigated before they become full-fledged attacks.
What Are Their TTPs?
| Tactic | MITRE ID – Technique | Description |
| Initial Access | T1566.001 – Phishing: Spearphishing Attachment | Evil Corp uses spear-phishing emails to deliver malicious attachments or links, allowing them to infect systems with malware such as Dridex or BitPaymer. |
| T1190 – Exploit Public-Facing Application | The group exploits vulnerabilities in software like Netwrix Auditor, allowing them to escalate privileges within the compromised network and gain administrative control over systems. | |
| T1189 – Drive-by Compromise | Evil Corp uses drive-by compromises, leveraging tools like SocGholish to infect users’ systems through fake software updates or compromised websites, gaining initial access. | |
| Execution | T1204.002 – User Execution: Malicious File | The group uses malware like Dridex, Truebot, and WastedLocker to steal credentials, move laterally, or execute ransomware attacks once they gain initial access to a network. |
| T1059.001 – Command and Scripting Interpreter: PowerShell | Evil Corp uses PowerShell scripts to execute malware payloads and gain control over compromised systems. | |
| Defense Evasion | T1027 – Obfuscated Files or Information | To avoid detection by security software, Evil Corp frequently changes the signatures of their ransomware strains, making it harder for anti-virus tools to recognize and block them. |
| T1036.005 – Masquerading: Match Legitimate Name or Location | Evil Corp frequently changes the names or signatures of their malware strains to evade detection by security tools and avoid attribution. | |
| Credential Access | T1555.003 – Credentials from Password Stores: Credentials from Web Browsers | The group extracts credentials stored in web browsers, such as passwords and session cookies, to access more resources or escalate privileges. |
| T1552.001 – Unsecured Credentials: Credentials In Files | Evil Corp searches for unsecured credentials stored in files on local machines to gain access to additional systems or sensitive information. | |
| Resource Development | T1584.005 – Compromise Infrastructure: Botnet | Using malware like Truebot, Evil Corp builds botnets by exploiting vulnerabilities, such as the Netwrix auditor vulnerability, to maintain persistent access to compromised systems. |
| Lateral Movement | T1210 – Exploitation of Remote Services | Once inside a system, the group uses malware like Dridex or Truebot to move laterally through the network, gaining access to more systems and increasing their control. |
| Collection | T1005 – Data from Local System | Banking credentials, sensitive documents, and financial information are harvested from infected systems, enabling Evil Corp to steal millions through fraudulent transactions. |
| T1115 – Clipboard Data | Evil Corp’s malware collects sensitive information from the clipboard, such as copied credentials, to further compromise user accounts. | |
| Command and Control | T1219 – Remote Access Software | Evil Corp uses remote access tools in combination with Truebot and Raspberry Robin malware to control compromised devices and execute commands remotely. |
| Impact | T1486 – Data Encrypted for Impact | Ransomware like WastedLocker and BitPaymer encrypts files on compromised networks, rendering them unusable until a ransom is paid for decryption keys. |
| T1529 – System Shutdown/Reboot | Evil Corp has used system shutdowns or reboots to disrupt operations as part of their ransomware attacks, pressuring victims into paying ransoms. | |
| T1486 – Data Encrypted for Impact | Evil Corp uses WastedLocker ransomware to encrypt files on targeted systems, rendering them inaccessible and demanding millions in ransom for the decryption keys, often crippling business operations. |
Mitigation Strategies for Evil Corp Attacks
To defend against Evil Corp’s wide-ranging tactics, it’s essential to employ a layered defense strategy. Here’s how organizations can mitigate the impact of their attacks:
-
Phishing Defense
- Recommended Defense: To combat Evil Corp’s use of spear-phishing emails to distribute malware like Dridex, organizations should implement advanced email filtering solutions. Phishing awareness training for employees is critical, along with enforcing Multi-Factor Authentication (MFA) to protect against compromised credentials.
- How SOCRadar Helps: SOCRadar’s Phishing Domain Detection provides early warnings of phishing campaigns targeting your organization, while its Identity & Access Intelligence monitors dark web forums for stolen credentials linked to phishing attacks, enabling proactive defense.
-
Ransomware Mitigation
- Recommended Defense: Implement robust Endpoint Detection and Response (EDR) solutions to identify and isolate malicious activities such as WastedLocker or BitPaymer ransomware. Network segmentation and frequent backups can help limit the damage caused by ransomware attacks.
- How SOCRadar Helps: SOCRadar’s Threat Intelligence provides real-time alerts on ransomware activities, including Indicators of Compromise (IOCs) tied to Evil Corp. SOCRadar’s Dark Web Monitoring tracks ransomware tools and techniques shared in underground forums, allowing your team to stay ahead of emerging threats.
-
Vulnerability Management
- Recommended Defense: Evil Corp exploits vulnerabilities in public-facing applications, such as Netwrix Auditor, to infiltrate systems. Conduct regular vulnerability scans and apply patches promptly, particularly for critical infrastructure and internet-facing systems.
- How SOCRadar Helps: SOCRadar’s Vulnerability Intelligence continuously identifies vulnerabilities across your digital footprint. With real-time vulnerability intelligence, you can prioritize patching critical systems before Evil Corp can exploit them.
-
Credential Protection
- Recommended Defense: Enforce strong password policies and implement MFA across all critical systems. Use password managers to prevent the use of weak or reused credentials. Regularly monitor for brute-force attacks and compromised credentials.
- How SOCRadar Helps: SOCRadar’s Credentials & Data Leak Detection monitors the surface, deep, and dark web for compromised PII, including email addresses and credit card information. It provides real-time alerts on data leaks, helping organizations take swift action to prevent fraud. The platform prioritizes critical incidents, ensuring focused responses to the most significant threats.
-
Botnet Prevention
- Recommended Defense: Evil Corp has been known to use malware like Truebot to create botnets for persistent access to compromised systems. Implement network traffic monitoring and Intrusion Prevention Systems (IPS) to detect suspicious traffic associated with botnet activities.
- How SOCRadar Helps: SOCRadar’s Dark Web Monitoring offers a dedicated Botnet Data feature that continuously scans the dark web for botnet-related activities linked to Evil Corp’s malware, such as Truebot. This feature provides real-time alerts, allowing security teams to detect and respond to botnet threats early, preventing extensive damage before they escalate.
SOCRadar’s Botnet Data showing recent alarms
Conclusion
Evil Corp remains one of the world’s most dangerous and resilient cybercrime groups. Their ability to innovate and adapt their attack methods, combined with their extensive use of ransomware and malware, makes them a constant threat to organizations around the world. While law enforcement agencies have attempted to limit their activities, Evil Corp’s continued presence on the dark web and recruitment of insiders keep them at the forefront of cybercrime.
To defend against the group’s sophisticated tactics, organizations must implement proactive security measures such as advanced threat intelligence, dark web monitoring, and robust ransomware defenses. SOCRadar is dedicated to providing the tools necessary to detect and mitigate the evolving threats posed by organizations such as Evil Corp.