An Analysis of Emerging Fortinet Vulnerabilities Trend
By SOCRadar Research
Fortinet is one of the major cybersecurity companies and offers 56 cybersecurity products. But, such a wide range of products and services means that the attack surface is vast, and being widely used products, we can also say that a vulnerability affects a large customer pool. Home to some of the most critical vulnerabilities of 2021 and 2022, Fortinet products have been observed as a popular target for threat actors.
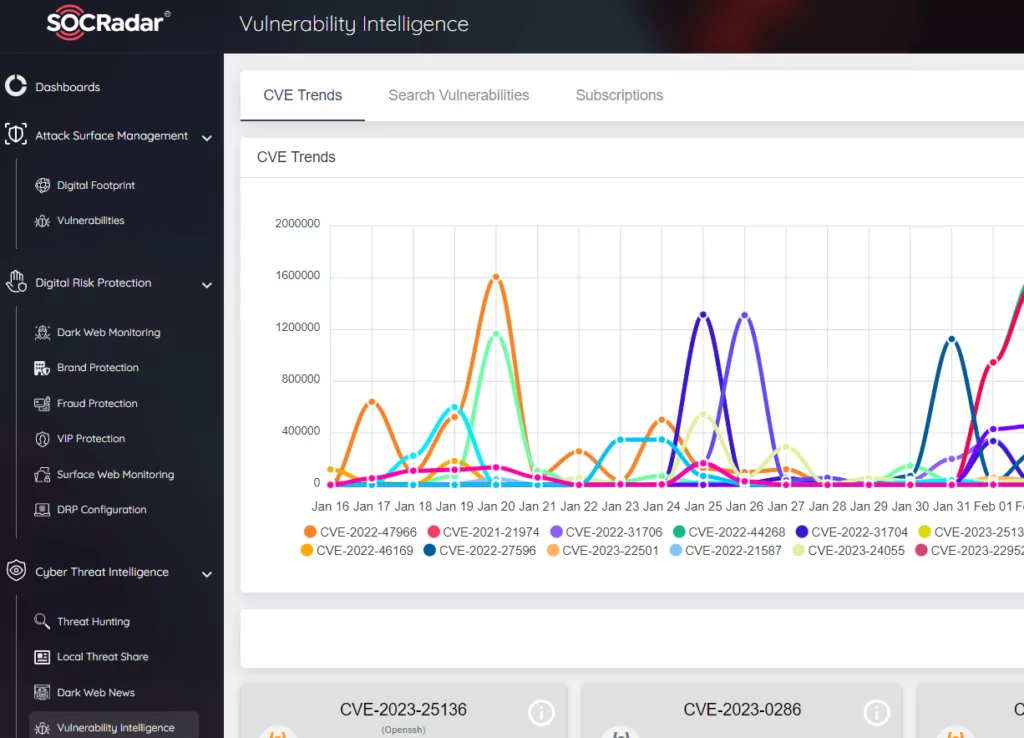
The SOCRadar Extended Threat Intelligence (XTI) platform has over 100 CVEs published or updated on Fortinet products in and after 2022 in the Vulnerability Intelligence section. CVE Details, on the other hand, registered 461 CVEs as Fortinet as Vendor in an all-time total, of which 30 were again designated as critical since 2005. As a result of these data, it is seen that the variety of Fortinet products and their extensive use also lead to the emergence of many weaknesses. Especially critical vulnerabilities, which peaked in 2022, attracted the attention of all cybersecurity researchers and threat actors last year.
Overview
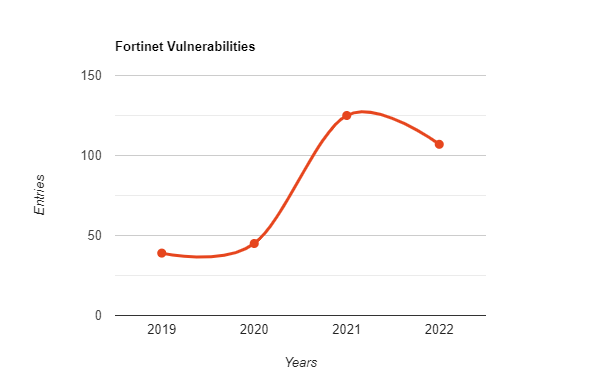
Threat actors are getting faster and faster at targeting vulnerable products or services. According to Gartner’s report, the average exploitation time of a new vulnerability has decreased from 45 days to 15 days in the decade. This situation can be explained with concepts such as the increase in the speed of spreading of information and the fact that it is more accessible, vulnerable services can be detected even with publicly available tools, and perhaps threat actors are also technically advanced.
Whatever the reason, many vulnerabilities remain undisclosed while hundreds of new CVE are registered yearly. As this situation is constantly encountered, even in the most reliable products, active update management and vulnerability intelligence have become necessary in today’s cyberspace. As mentioned above, Fortinet is the vendor of one of the most used products in the entire IT industry. Therefore, researchers spotted an upward increase in targeting this organization’s products in 2022.
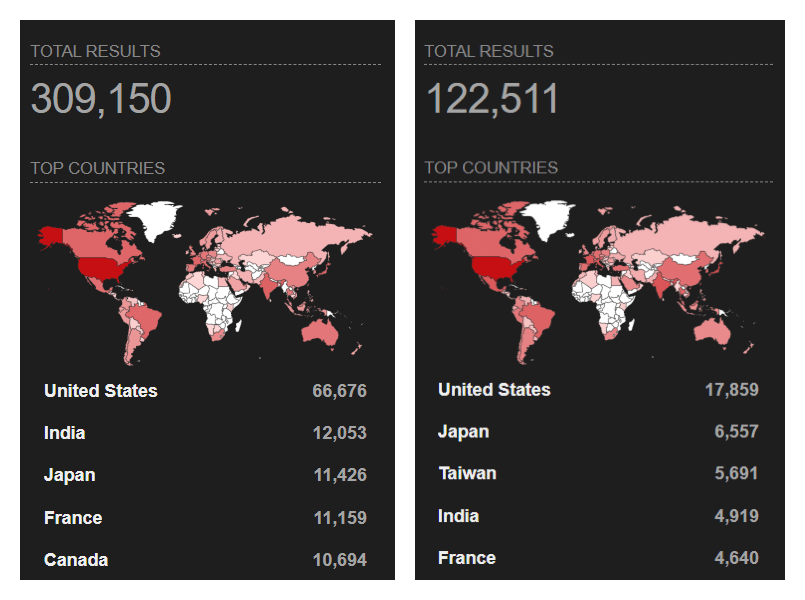
Top Exploited Fortinet Vulnerabilities
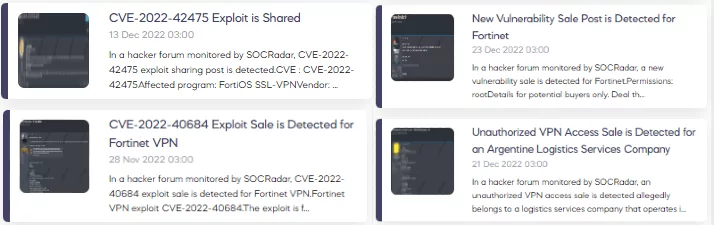
CVE-2022-42475
In 2022, one of the most critical vulnerabilities with Fortinet was a heap-based buffer overflow vulnerability CVE-2022-42475, with a CVSS score of 9.3, which affected the FortiOS product, allowing an attacker to execute arbitrary code remotely. Fortinet issued an emergency patch for this vulnerability in December and warned its customers.
In January 2023, Mandiant’s research revealed that this vulnerability, which was revealed as a zero-day, has been exploited by allegedly Chinese threat actors since October 2022, when a patch has not been released yet. Threat actors were exploiting CVE-2022-42475 with malware called BoldMove, created specifically for FortiGate firewalls. BoldMove was designed as a backdoor, written in C programming language, and has Windows and Linux versions.

CVE-2022-40684
According to SOCRadar XTI Platform data, the second most critical Fortinet vulnerability in recent years is the authentication bypass CVE-2022-40684. This vulnerability, which threat actors can use against several of Fortinet’s products, was exploited with specifically generated HTTP and HTTPS requests. Fortinet said it was observed to be exploited in the wild.
Researchers have stumbled upon this vulnerability being exploited multiple times in the wild. It has also been observed that the exploit techniques and tools of the vulnerability are offered for sale on dark web forums.

CVE-2022-39952
This critical CVE, with a score of 9.8, updated by Fortinet’s February 2023 advisory, soon became one of the vulnerabilities targeted by threat actors. According to the PoC published by Horizon3 researchers, it was possible to target internet-facing endpoints, obtain root authority with a reverse shell and use it as a backdoor. Having reached an audience of over 2 million on Twitter, CVE has become a known target already. Shadowserver researchers have reported attempts to exploit Fortinet FortiNAC honeypots.
Horizon3’s researchers also added that there are different ways to target this vulnerability, emphasizing the importance of making the necessary security update. We can think that the vulnerability exploitation trend in Fortinet products in the past years will continue in 2023 with this critical CVE that allows a backdoor to be created.
Fortinet Products as an Access
One of the prominent initial access methods in 2022 was registered in the SOCRadar Platform as SSL-VPN access credentials through Fortinet products. While many scripts, tools, or technical documents are sold to exploit Fortinet vulnerabilities in the dark web, it has been observed that some threat actors are trying to make a profit by selling the access they obtained using these tools.
The accesses obtained by exploiting the vulnerabilities in Fortinet products also significantly contributed to the initial access market, which increased by nearly 50% from 2021 to 2022. Again, the Fortinet advisory for February 2023 was an update for more than 40 vulnerabilities, two of which were critical. The CVE-2022-39952 mentioned above and CVE-2021-42756 vulnerabilities found on FortiNAC and FortiWeb can also be expected to be among the targets of initial access brokers in 2023.
Conclusion
From a broad perspective, the number of critical vulnerabilities that have increased in recent years affects many institutions directly or indirectly. The increase in initial access sales, access as service methods, and exploit tools also increase in parallel with this in the dark web. While such vulnerabilities can be exploited by threat actors and cause a breach, they can also be used by relatively less capable threat actors when a vulnerability is discovered. Threat actors who cannot go beyond the Cyber Kill Chain‘s further steps can also put your company in trouble by selling the initial access they have obtained in dark web markets. At this point, traditional security measures are the first solutions that come to mind.
Although products that are used frequently and whose performance is assured are seen as approved solutions, they are also the products that threat actors encounter most often. A vulnerability discovered by cybercriminals before cybersecurity researchers can turn into a crisis that can affect the entire industry at this point. A vulnerability detected in a specific company’s product can be found in a company within your supply chain, even if it is not in your organization’s inventory.
So, in today’s cyber world, security solutions that we rely on, such as regular security patches and raising employees’ awareness of cyber security and traditional security products, may be insufficient. With an understanding of cyber security powered by Dark Web Monitoring and CTI products, building a broader defense for your company and taking a proactive stance in the everchanging cyber world is necessary.
In this matter, the SOCRadar XTI platform can meet many of your needs. Active dark web scans are performed for your organizational data and employee credentials for a possible leak. You can also have information on the changing TTPs of threat actors, manage your attack surface and obtain Vulnerability intelligence to cover your cyber security needs.