
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog Cybersecurity is a constant back-and-forth between the defenders and the threat actors, all centered around finding vulnerabilitie...
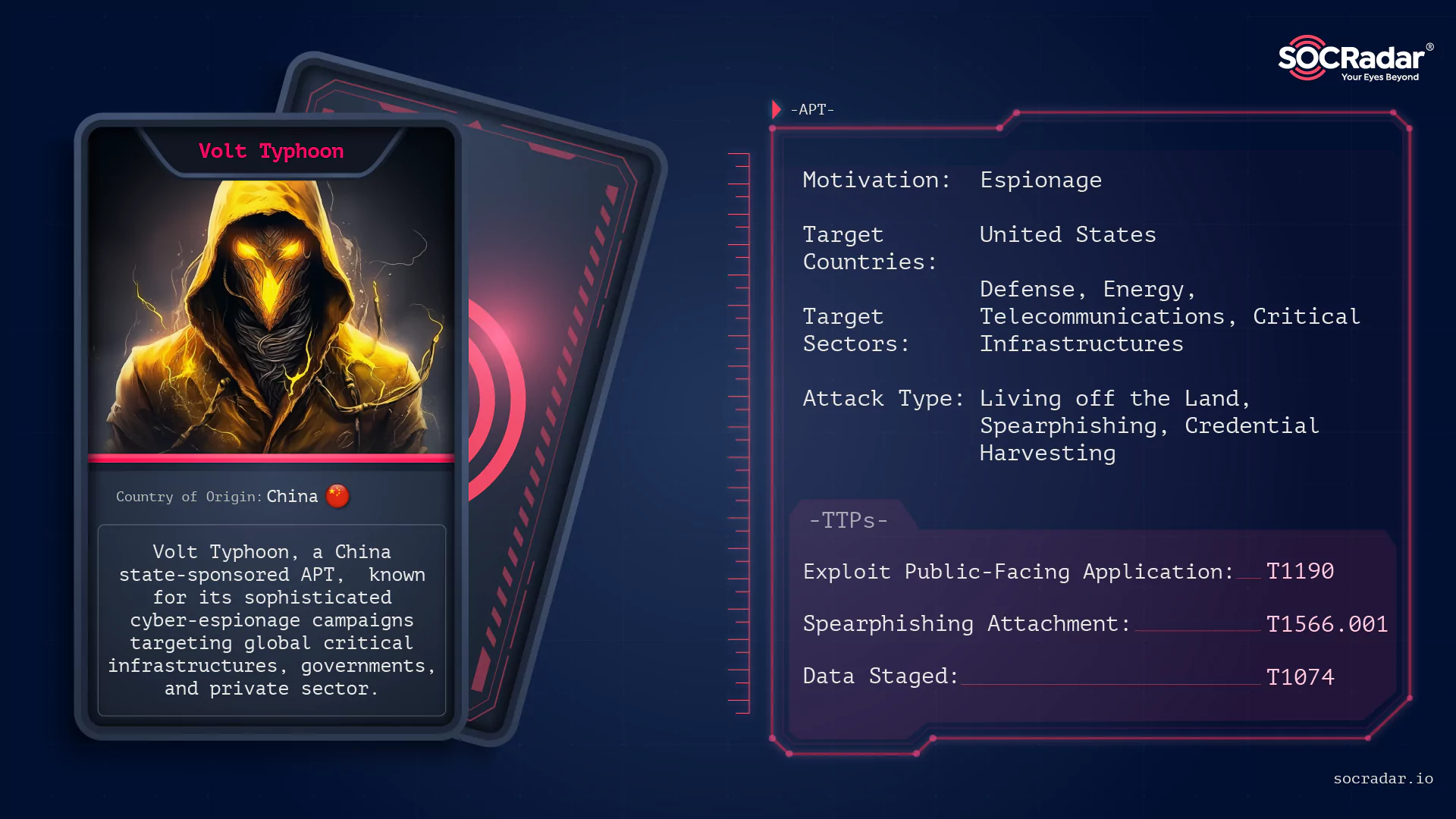
APT Profile: Volt Typhoon
APT Profile: Volt Typhoon [Update] February 01, 2024: U.S. Government Actions Against Volt Typhoon As cyber currents ebb and flow, a storm named Volt Typhoon surges from the digital depths. This isn’t...

CISA Alert: Serious Vulnerabilities in Adobe ColdFusion (CVE-2023-4435...
CISA Alert: Serious Vulnerabilities in Adobe ColdFusion (CVE-2023-44350, CVE-2023-44351, CVE-2023-44353 and More) CISA has issued an alert regarding multiple vulnerabilities impacting Adobe ColdFusion...

Surging Tide of E-Commerce Security Threats: Insights from SOCRadar's ...
Surging Tide of E-Commerce Security Threats: Insights from SOCRadar’s Report In recent years, the e-commerce industry has become a prime target for cybercriminals, making e-commerce security mor...

Atlassian Patches RCE Vulnerabilities in Bamboo & Crowd Data Cente...
Atlassian Patches RCE Vulnerabilities in Bamboo & Crowd Data Center and Server: CVE-2023-22516, CVE-2023-22521 Atlassian has urgently issued security advisories for two separate products: Bamboo D...

Dark Web Sales: E-Commerce and Crypto Wallets' Databases, Fortinet Acc...
Dark Web Sales: E-Commerce and Crypto Wallets’ Databases, Fortinet Access in US, UK Credit Cards Embarking on a relentless pursuit of the shadows, the SOCRadar Dark Web Team brings to light a se...

Fortinet Reveals Critical Vulnerability in FortiSIEM Report Server (CV...
Fortinet Reveals Critical Vulnerability in FortiSIEM Report Server (CVE-2023-36553): Patch Now Fortinet, a leading cybersecurity provider, has recently issued an advisory for a critical vulnerability ...

Predicting Vulnerability Exploitation for Proactive Cybersecurity: Wha...
Predicting Vulnerability Exploitation for Proactive Cybersecurity: What’s EPSS, and How Can SVRS Enhance It? Predicting outcomes closely before taking action is a fundamental aspect of effective decis...

Education Security: A Critical Analysis of the K-12 Threat Landscape
Education Security: A Critical Analysis of the K-12 Threat Landscape As digital transformation reshapes the education sector, education security in K-12 schools has emerged as a crucial concern. The c...

Citrix Hypervisor Security Update: Addressing CVE-2023-23583 and CVE-2...
Citrix Hypervisor Security Update: Addressing CVE-2023-23583 and CVE-2023-46835 Vulnerabilities In the dynamic field of cybersecurity, staying abreast of new vulnerabilities is crucial. The recent dis...

Cyber Extortion Meets Regulatory Pressure: ALPHV's SEC Complaint Again...
Cyber Extortion Meets Regulatory Pressure: ALPHV’s SEC Complaint Against MeridianLink The ALPHV/BlackCat ransomware group, known for their vicious ransomware attacks, has recently taken a surprising a...

Dark Peep #5: The Calm Before the Storm
Dark Peep #5: The Calm Before the Storm On the dark web, the weather has closed, the thunder is rumbling, and the wind is picking up. Chaos is coming, ahem, not that chaos, ChaosSec is coming(!) Let&#...

SAP November 2023 Security Patch Day: Critical Business One Vulnerabil...
SAP November 2023 Security Patch Day: Critical Business One Vulnerability Has Been Fixed (CVE-2023-31403) SAP, a prominent enterprise software company, has unveiled three new vulnerabilities in its No...

MGM Casino Hack and Realities of Social Engineering Attacks
MGM Casino Hack and Realities of Social Engineering Attacks In the complicated world of cybersecurity, the most unpredictable element remains the human factor. Social engineering attacks exploit this ...

Critical CVE-2023-34060 Vulnerability in VMware Cloud Director Applian...
Critical CVE-2023-34060 Vulnerability in VMware Cloud Director Appliance: CISA Advises Immediate Patching VMware recently issued an advisory (VMSA-2023-0026) regarding a critical authentication bypass...

Microsoft's November 2023 Patch Tuesday Tackles Exploited Zero-Day Vul...
Microsoft’s November 2023 Patch Tuesday Tackles Exploited Zero-Day Vulnerabilities, Now Listed in CISA KEV Microsoft recently rolled out its Patch Tuesday for November 2023, tackling a total of ...

SOCRadar Technical Whitepaper: 'A 100M+ USD Negotiator's Guide to Surv...
SOCRadar Technical Whitepaper: ‘A 100M+ USD Negotiator’s Guide to Surviving Ransomware’ In an era where digital threats constantly evolve, ransomware attacks have emerged as a formidable challenge, ho...

A Brief Look at SOCRadar's Saudi Arabia Threat Landscape Report
A Brief Look at SOCRadar’s Saudi Arabia Threat Landscape Report Saudi Arabia, a major player in Middle Eastern geopolitics and global economics, faces significant cybersecurity challenges. With ...

Exploring the Top Vulnerabilities Exploited by State-Sponsored Threat ...
Exploring the Top Vulnerabilities Exploited by State-Sponsored Threat Actors While cyberattacks are a common concern for individuals and organizations alike, the shadowy realm of state-sponsored threa...

LockBit Shares Boeing Data, Software Company and US Database Leaks, Du...
LockBit Shares Boeing Data, Software Company and US Database Leaks, Dutch RDP Sale The SOCRadar Dark Web Team has diligently documented a series of unsettling activities within the depths of the dark ...



































