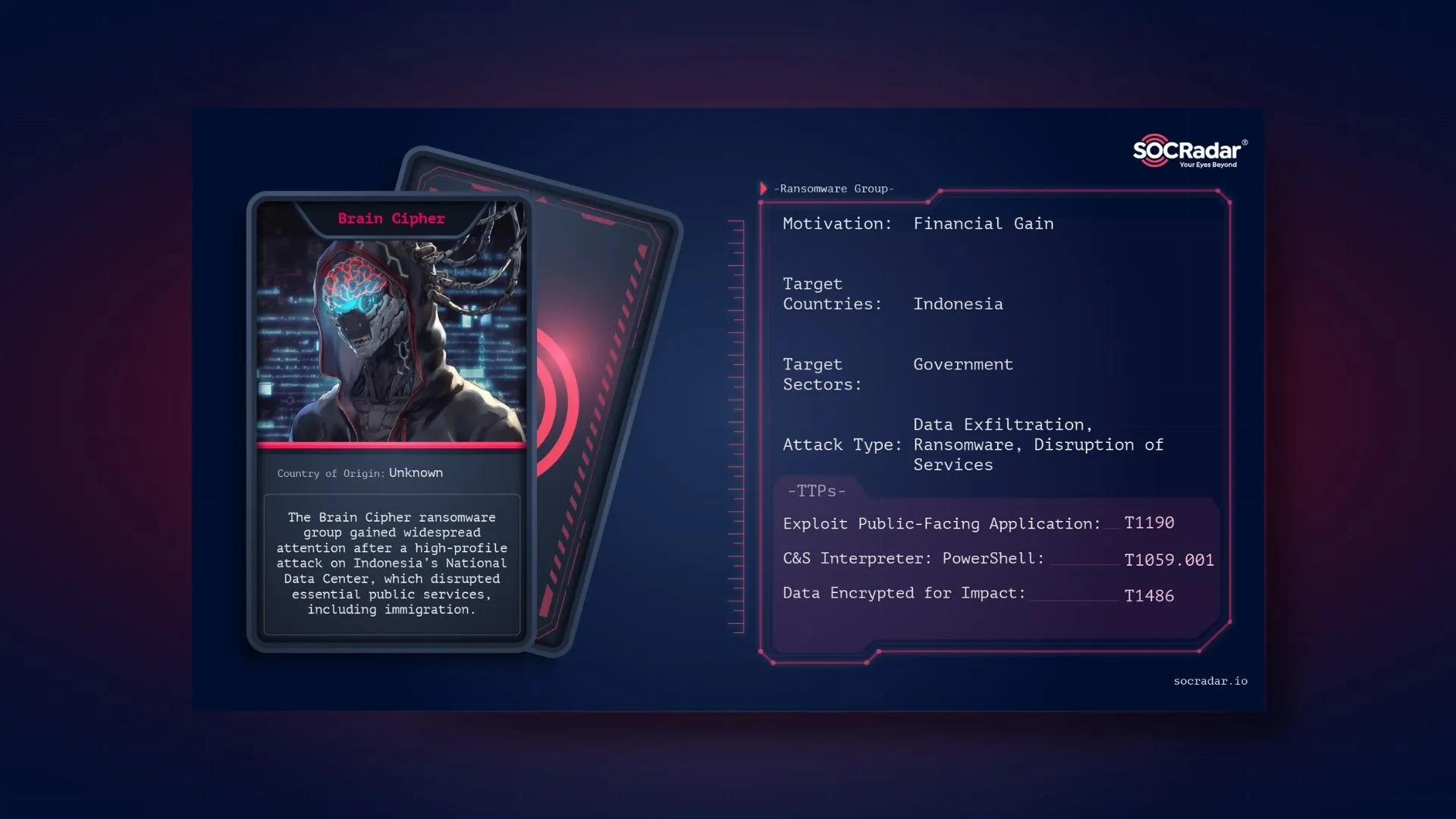
Dark Web Profile: Brain Cipher
Dark Web Profile: Brain Cipher The Brain Cipher ransomware group gained widespread attention after a high-profile attack on Indonesia’s National Data Center (Pusat Data Nasional – PDN), which disrupte...

Critical HTTP File Server Vulnerability (CVE-2024-23692) Actively Expl...
Critical HTTP File Server Vulnerability (CVE-2024-23692) Actively Exploited to Deploy Cryptomining Malware, RATs, Stealers Researchers have identified active exploitation targeting a critical vulnerab...

Everything You Need to Know About Dark Web and Deep Web
Everything You Need to Know About Dark Web and Deep Web The Internet encompasses an extensive and intricate network that goes well beyond the familiar surface websites we frequently visit. Two terms t...

Velvet Ant's Strategic Targeting: A Long-Term Cyber Espionage Campaign...
Velvet Ant’s Strategic Targeting: A Long-Term Cyber Espionage Campaign Against F5 BIG-IP Systems In the constantly evolving landscape of cybersecurity, the Velvet Ant Advanced Persistent Threat (APT) ...

Top 10 Deepfake Scams Impacting Industries Worldwide
Top 10 Deepfake Scams Impacting Industries Worldwide Deepfake technology has emerged as an effective tool for both creative and malicious purposes. This technology employs AI to generate highly realis...

New Security Vulnerability "regreSSHion" Exposes Millions of Linux Ope...
New Security Vulnerability “regreSSHion” Exposes Millions of Linux OpenSSH Servers to RCE Attacks (CVE-2024-6387) [Update] July 2, 2024: “PoC Exploit for regreSSHion Vulnerability (CVE-2024-6387) Surf...

Alleged Data Leaks of Truist Bank, Twilio Authy, Genesis Market, and S...
Alleged Data Leaks of Truist Bank, Twilio Authy, Genesis Market, and Skull OTP BOT The SOCRadar Dark Web Team has identified several critical cyber incidents involving major financial institutions and...

CISO Guide for Quantum Computing: Risks and Opportunities (Part II)
CISO Guide for Quantum Computing: Risks and Opportunities (Part II) While the specter of quantum computing as a new source of threats usually dominates the discussion, it is imperative to note that wh...

Top 10 Phishing Simulation Tools
Top 10 Phishing Simulation Tools Phishing attacks continue to pose a significant threat, affecting both individuals and organizations. To combat these threats, a variety of phishing simulation tools h...

Dark Web Profile: IntelBroker
Dark Web Profile: IntelBroker IntelBroker, a notorious figure known for orchestrating high-profile cyberattacks, operates within BreachForums. Specializing in identifying and selling access to comprom...

GitLab Issues Critical Patches for CE/EE Alongside Fortra & MOVEit (CV...
GitLab Issues Critical Patches for CE/EE Alongside Fortra & MOVEit (CVE-2024-5655, CVE-2024-5276, CVE-2024-5805, CVE-2024-5806) GitLab has rolled out new security updates for both its Community Ed...

Polyfill Fuels Supply Chain Concerns with Malicious Redirects: +100,00...
Polyfill Fuels Supply Chain Concerns with Malicious Redirects: +100,000 Websites Affected Latest Update: “Polyfill Issue Affects +380,000 Hosts and Major Companies, With Ongoing New Domain Regis...

Julian Assange Released, But the Leak and Extortion Era Began Long Ago
Julian Assange Released, But the Leak and Extortion Era Began Long Ago WikiLeaks founder Julian Assange has been freed in the UK after serving over five years in Belmarsh prison for what the U.S. gove...

Cyber Threats for the Upcoming 2024 Paris Olympics
Cyber Threats for the Upcoming 2024 Paris Olympics The world is eagerly waiting for the Paris Olympics to come. The event is not only going to be a scene for the best athletes in the world to compete ...

An Overview of Intelligence Requirements in CTI
An Overview of Intelligence Requirements in CTI Security, in general, is a complex domain where you need to keep in mind a variety of factors. In a complex field like this, the role of intelligence ca...
Tracking Down Notorious Ransomware Actors with CTI 2.0
Tracking Down Notorious Ransomware Actors with CTI 2.0 Alex was talking to his security team when his boss called him into his office one day. News about ransomware attacks across the industry has bee...

IntelBroker Claims Apple, AMD Data Breaches; NSA Data Allegedly Leaked
IntelBroker Claims Apple, AMD Data Breaches; NSA Data Allegedly Leaked The SOCRadar Dark Web Team has uncovered several alarming posts on hacker forums, revealing significant breaches and data sales i...

CISO Guide for Quantum Computing: Risks and Opportunities (Part I)
CISO Guide for Quantum Computing: Risks and Opportunities (Part I) For Chief Information Security Officers (CISOs) in charge of cybersecurity, quantum computing brings its paradox. It is both an oppor...

Top 10 VPN Vulnerabilities (2022 – H1 2024)
Top 10 VPN Vulnerabilities (2022 – H1 2024) In the landscape of cybersecurity, VPN security has become a critical concern for organizations worldwide. Compared to 2022, there was a staggering 47% incr...

Dark Web Profile: dAn0n Hacker Group
Dark Web Profile: dAn0n Hacker Group Global law enforcement agencies have ramped up their efforts against ransomware, leading to the weakening of groups and even dethroned the long ruled LockBit. Howe...
































