
High-Severity Vulnerabilities in CODESYS V3 SDK and Python’s URLlib.pa...
High-Severity Vulnerabilities in CODESYS V3 SDK and Python’s URLlib.parse Library The widely-used industrial software development kit, CODESYS, has been found to harbor multiple security vulnerabiliti...

What is EMOTET Malware and How to Protect Yourself
What is EMOTET Malware and How to Protect Yourself According to Arne Schoenbohm, who leads the German Federal Office of Information Security (BSI), EMOTET is the king of malware. EMOTET actively attac...

New Malware “Statc Stealer” Targets Windows Devices to Steal Browser D...
New Malware “Statc Stealer” Targets Windows Devices to Steal Browser Data, Cryptowallets, and More Researchers have identified a new information-stealing malware named “Statc Stealer.” Thi...

New Global Phishing Scam Exposed: Facebook and Instagram Users Targete...
New Global Phishing Scam Exposed: Facebook and Instagram Users Targeted by Fake Crypto Platform The thrill of curiosity! It is the spark that drives innovation, leads us to explore new horizons, and s...
The "Downfall" Effect: Intel CPUs May Leak Sensitive Information
The “Downfall” Effect: Intel CPUs May Leak Sensitive Information On August 9, Intel and the discoverer of the vulnerability, Daniel Moghimi, unveiled a fresh exploit named Downfall. This n...

EvilProxy Account Takeover Campaign Targets Key Executives
EvilProxy Account Takeover Campaign Targets Key Executives An escalating threat, named EvilProxy, combines advanced Adversary-in-the-Middle (AitM) phishing with sophisticated Account Takeover (AT...

SOCRadar Unveils 'Treemium': Report a Bug, Plant a Future with SOCRada...
SOCRadar Unveils ‘Treemium’: Report a Bug, Plant a Future with SOCRadar We are overjoyed to pull back the curtain on a new initiative from SOCRadar – Treemium! This new initiative, rooted ...

Microsoft’s August 2023 Patch Tuesday Fixes Six Critical Vulnerabiliti...
Microsoft’s August 2023 Patch Tuesday Fixes Six Critical Vulnerabilities and Two Exploited Zero-Days Microsoft’s August 2023 Patch Tuesday has just arrived. The update addresses a total of 74 vulnerab...

Complex RCE Vulnerability (CVE-2023-39143) in PaperCut Application Ser...
Complex RCE Vulnerability (CVE-2023-39143) in PaperCut Application Servers PaperCut NG and PaperCut MF are extensively utilized software solutions for print management servers. CVE-2023-39143 refers t...
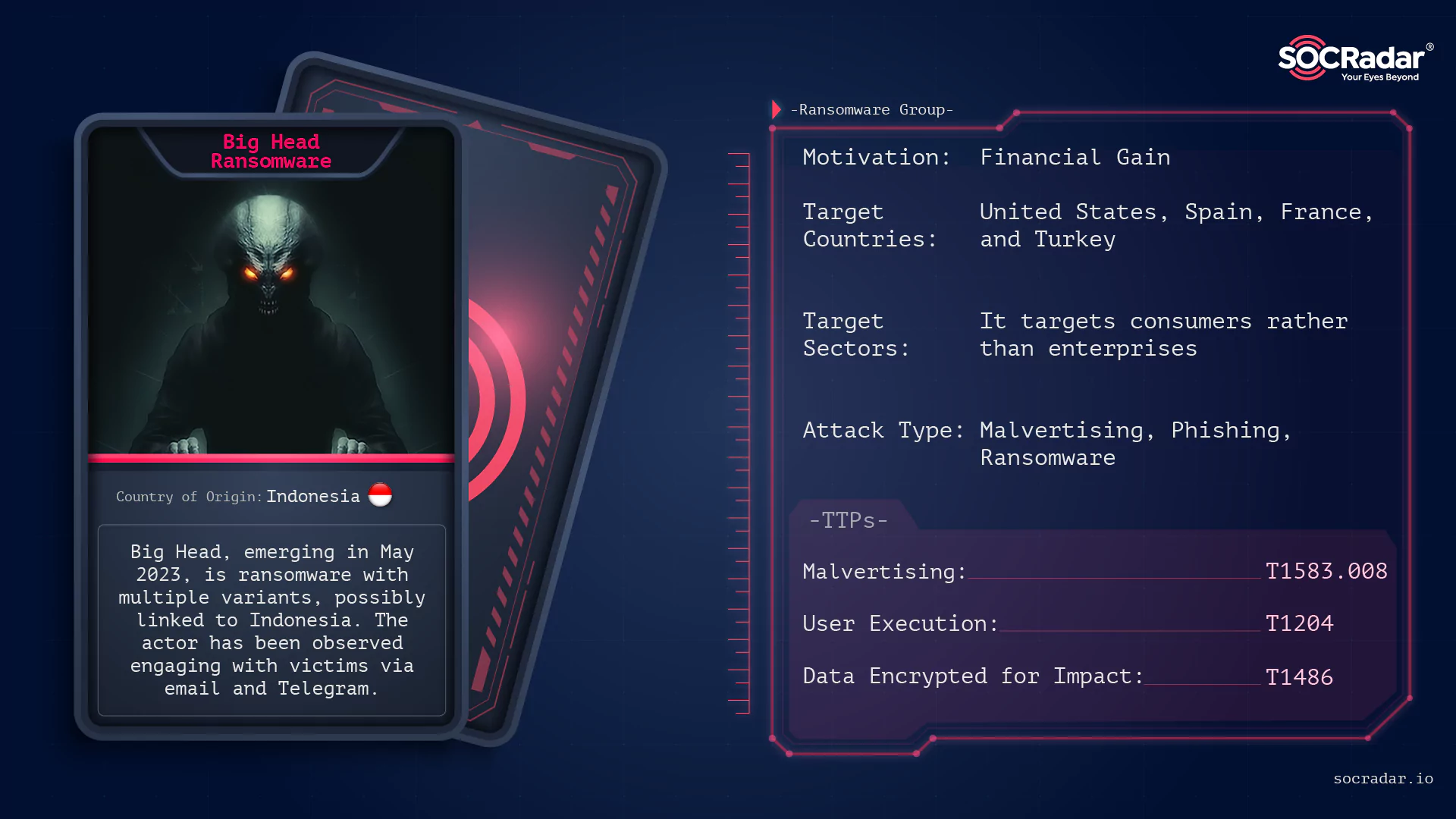
Dark Web Profile: Big Head Ransomware
Dark Web Profile: Big Head Ransomware While ransomware groups such as ALPHV and Lockbit 3.0 continue to hit big companies and make headlines with the large-sized files they steal, there are also actor...

Dark Web Sales: Unauthorized Citrix Access, Credit Cards, and Student ...
Dark Web Sales: Unauthorized Citrix Access, Credit Cards, and Student Documents The SOCRadar Dark Web Team has been tirelessly monitoring the deep corners of the internet, and their efforts have unear...

Critical Microsoft Power Platform Vulnerability: Proactive Security Me...
Critical Microsoft Power Platform Vulnerability: Proactive Security Methods to Prevent Exploitation Microsoft fixed a critical vulnerability in its Power Platform after facing criticism for the delaye...

Threat-Informed Defense (TID): A Threat Intelligence Perspective
Threat-Informed Defense (TID): A Threat Intelligence Perspective Cyberattacks are increasing in frequency worldwide, posing significant challenges for organizations as they strive to protect their cyb...

Threat Actors Employ New Phishing Tactic Using Google AMP
Threat Actors Employ New Phishing Tactic Using Google AMP Researchers have uncovered a highly effective phishing tactic, which utilizes Google AMP (Accelerated Mobile Pages). Google AMP is an open-sou...

Living Off the Land (LOTL): The Invisible Cyber Threat Lurking in Your...
Living Off the Land (LOTL): The Invisible Cyber Threat Lurking in Your System [Update] January 10, 2024: “Countering Living Off the Land (LOTL) Attack Methods with AI and ML” ...

Threat Profile: Rhysida Ransomware
Threat Profile: Rhysida Ransomware [Update] November 16, 2023: See the subheading: “Collaborative Advisory by CISA, FBI, and MS-ISAC on Rhysida Ransomware.” [Update] February 13, 2024: “A Free D...

Major Cyberattacks in Review: July 2023
Major Cyberattacks in Review: July 2023 The major cyberattacks of July 2023 included waves of data breaches, affecting both private and public sector entities, including healthcare organizations, fina...

Top 10 Ransomware Demands
Top 10 Ransomware Demands In cyberspace, few threats rival ransomware attacks’ pervasive and destructive nature. As our interconnected world grows, these digital extortionists demonstrate unpara...

Zero-Day RCE Sale, Pizza Hut Access Sale & More
Zero-Day RCE Sale, Pizza Hut Access Sale & More Welcome to the twisted world of the Dark Web, where the illicit trade of cyber weapons and stolen data thrives under the cover of anonymity. In thi...

P2Pinfect: A Worm-Like Botnet Malware Targeting Redis Deployments
P2Pinfect: A Worm-Like Botnet Malware Targeting Redis Deployments Researchers have identified an unknown group of hackers employing a novel strain of malware named “P2Pinfect” to target pu...



































