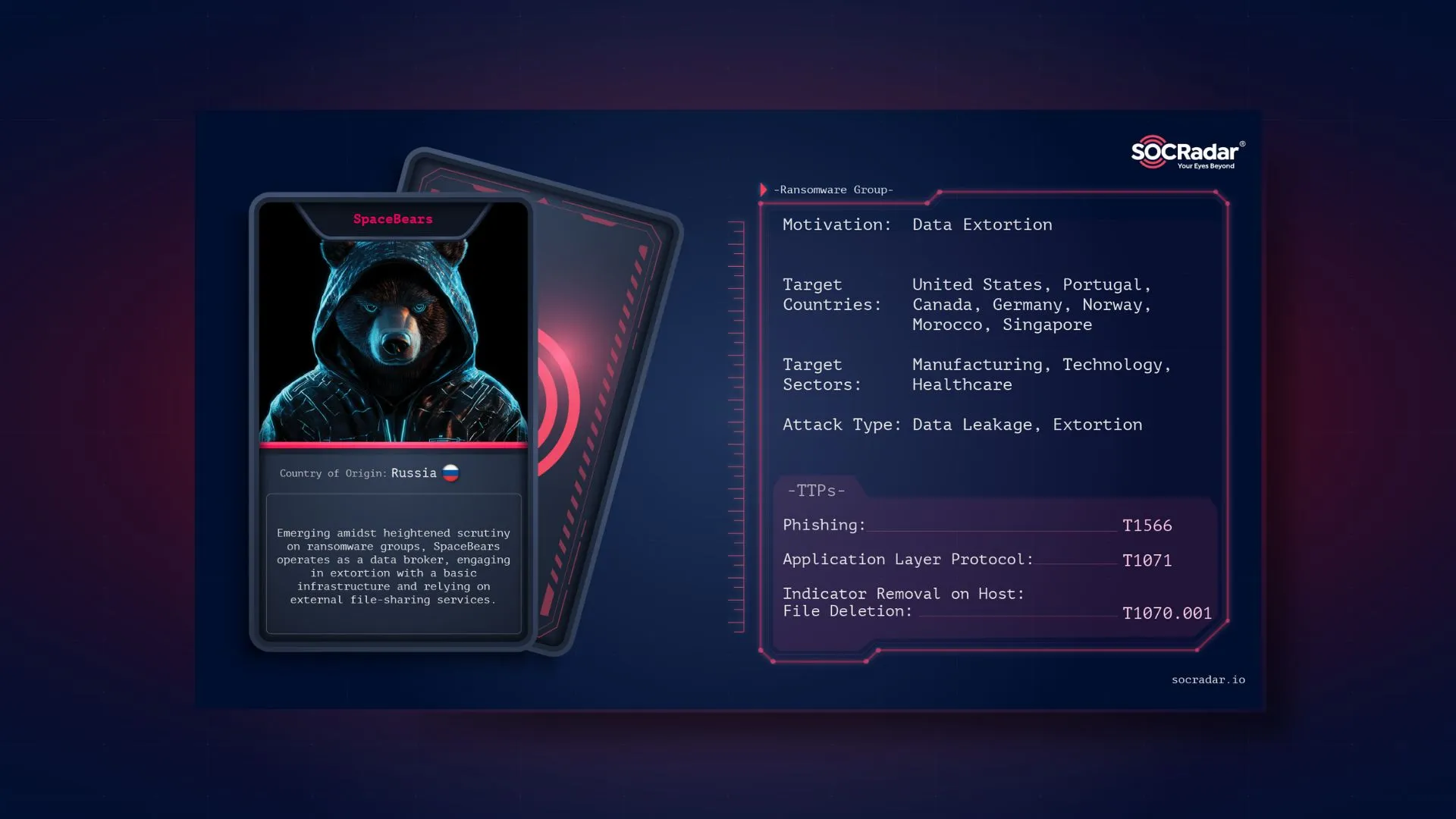
Dark Web Profile: SpaceBears
Dark Web Profile: SpaceBears Recent history could be termed the Age of Ransomware in the realm of cybercrime. However, threat actors have discovered a way to profit without the need for malware develo...

Shedding Light on the Netherlands Threat Landscape Report
Shedding Light on the Netherlands Threat Landscape Report In an era of dynamic change in digital threats, there is more need for knowledge of regional cybersecurity challenges than ever. Therefore, it...

Dark Web Profile: DragonForce Ransomware
Dark Web Profile: DragonForce Ransomware DragonForce Ransomware has emerged as an intriguing adversary. Known for its prominent targets and unusual ways of communication, it has quickly gained notorie...

Zero-Day Exploits for Windows, Atlassian, Mastodon Data Leak, DDoS Att...
Zero-Day Exploits for Windows, Atlassian, Mastodon Data Leak, DDoS Attack on FC Bayern Munich The SOCRadar Dark Web Team has recently uncovered several alarming posts on hacker forums and Telegram cha...

VMware vCenter Server Updates Address Critical RCE and Privilege Escal...
VMware vCenter Server Updates Address Critical RCE and Privilege Escalation Vulnerabilities (CVE-2024-37079, CVE-2024-37080, CVE-2024-37081) Broadcom has released a security update for its popular man...

Global DDoS Attack Landscape: Insights from Q1 2024
Global DDoS Attack Landscape: Insights from Q1 2024 Distributed Denial of Service (DDoS) attacks continue to escalate in frequency and complexity, posing significant threats across various sectors, pa...

Top 10 Cybersecurity Conferences
Top 10 Cybersecurity Conferences In the dynamic and ever-evolving world of cybersecurity, certain events stand as pillars of knowledge exchange and innovation. These gatherings, many of which have bee...

Phishing in 2024: 4,151% Increase Since Launch of ChatGPT; AI Mitigati...
Phishing in 2024: 4,151% Increase Since Launch of ChatGPT; AI Mitigation Methods Phishing remains a major threat in cybersecurity, with attacks growing more frequent and sophisticated each year. In 20...

Cyber Threats Targeting the Hajj Season
Cyber Threats Targeting the Hajj Season Hajj is a religious obligation for Muslims, which must be completed at least once in their lifetime by all adults who are physically and financially able to mak...

Microsoft’s June 2024 Patch Tuesday Highlights KeyTrap Zero-Day, Criti...
Microsoft’s June 2024 Patch Tuesday Highlights KeyTrap Zero-Day, Critical MSMQ Flaw; Windows LPE Exploit [Update] December 24, 2024: “CVE-2024-30085 PoC Exploit Released, Immediate Action Requir...
Libraries for Red Teaming Your GenAI Applications
Libraries for Red Teaming Your GenAI Applications It is critical to ensure the security and integrity of Generative AI (GenAI) applications. Red teaming these applications entails proactively identify...

Major Cyber Attacks in Review: May 2024
Major Cyber Attacks in Review: May 2024 May 2024 saw several major cyber attacks across diverse sectors, including cryptocurrency, cloud services, and online archives. Notable incidents include the $3...

Malvertising Campaign Targets Windows Administrators Using PuTTy and W...
Malvertising Campaign Targets Windows Administrators Using PuTTy and WinSCP An AI illustration of the malvertising campaign using PuTTy and WinSCP In the ever-evolving landscape of digital security...

CISO Guide to Deepfake Scams
CISO Guide to Deepfake Scams Initially perceived as a novelty, deepfakes have evolved into sophisticated fraud, misinformation, and manipulation tools. Utilizing artificial intelligence and machine le...

Dark Web Data Breaches: PT Nap Info Lintas Nusa, LocalPlace, Opensoft ...
Dark Web Data Breaches: PT Nap Info Lintas Nusa, LocalPlace, Opensoft Affected The SOCRadar Dark Web Team has detected multiple new posts on hacker forums, alleging significant data breaches across va...

Critical RCE Vulnerability (CVE-2024-4577) in PHP on Windows: Patch No...
Critical RCE Vulnerability (CVE-2024-4577) in PHP on Windows: Patch Now Available [Update] August 21, 2024: “CVE-2024-4577 Exploited to Deploy Msupedge Backdoor” [Update] June 13, 2024: “CISA Adds Cri...

Grandoreiro Malware Campaign: A Global Threat to Banking Security
Grandoreiro Malware Campaign: A Global Threat to Banking Security The Grandoreiro banking trojan was first observed in 2016. This threat is described as a highly sophisticated and adaptive Windows-bas...

Unleashing AI's Potential: Top 10 Tools for CISO for Productivity (Par...
Unleashing AI’s Potential: Top 10 Tools for CISO for Security (Part-2) Even in large organizations, persistent and ever-evolving cyber challenges have broken down perimeter security, and traditional m...

Exploring the Most Common Passwords in Singapore: Trends, Implications...
Exploring the Most Common Passwords in Singapore: Trends, Implications, and Security Tips Passwords are essential for protecting your online accounts, yet many people still use weak, easy-to-guess pas...

Impacts of Geopolitics to Cyberspace: Sweden Faces Intensifying Hackti...
Impacts of Geopolitics to Cyberspace: Sweden Faces Intensifying Hacktivist Attacks On June 28, Salwan Momika, an Iraqi immigrant to Sweden, burned a Qur’an outside a Stockholm mosque. This act, coinci...
































