
Ransomware Gangs Leak Large Amounts of Data in Recent Attacks: Hive an...
Ransomware Gangs Leak Large Amounts of Data in Recent Attacks: Hive and Vice Society Ransomware gangs are known to release stolen data in retaliation if the ransom is not paid after successful encrypt...

Dark Web Profile: Royal Ransomware
Dark Web Profile: Royal Ransomware By SOCRadar Research [Update] November 14, 2023: See the subheading: “CSA Update from CISA and FBI: Royal Ransomware’s Possible Rebranding to ‘Blacksuit’” Ran...

The Week in Dark Web – 9 January 2023 – Access Sales and Data Leakes...
The Week in Dark Web – 9 January 2023 – Access Sales and Data Leakes Powered by DarkMirror™ Threat actors continue to target popular social networking platforms. Twitter was awash with two significant...

Major Cyber Attacks in Review: December 2022
Major Cyber Attacks in Review: December 2022 In the last month, we have seen many cyber incidents, ranging from data breaches at retailers to various cyberattacks on cryptocurrency exch...

200M+ Twitter Users' Email Addresses and 250M+ Deezer Users' Informati...
200M+ Twitter Users’ Email Addresses and 250M+ Deezer Users’ Information Leaked Online On a well-known hacker forum, a data leak containing the email addresses of 235 million Twitter users was made pu...

The Week in Dark Web – 4 January 2023 – Access Sales, Data, and Malwar...
The Week in Dark Web – 4 January 2023 – Access Sales, Data, and Malware Leakes Powered by DarkMirror™ Entering the first week of the year, the most sensational incident on the dark web was the sale of...

Synology Fixes a Max Severity RCE Vulnerability in VPN Server Products
Synology Fixes a Max Severity RCE Vulnerability in VPN Server Products Taiwanese NAS device manufacturer Synology has released a security update to address a critical vulnerability with a&nb...

How Easy Is It to Guess Fortune 500 Executives' Passwords?
How Easy Is It to Guess Fortune 500 Executives’ Passwords? Recently, many cyberattacks on large corporations have begun with acquiring credentials via multiple methods, particularly social ...

Secure Your Cloud Environment: 5 Best Practices
Secure Your Cloud Environment: 5 Best Practices With the increasing adoption of cloud computing, cloud security has become a major concern for businesses that rely on cloud-based services to...

10 Questions to ChatGPT: How It Can Change Cybersecurity
10 Questions to ChatGPT: How It Can Change Cybersecurity This blog is written with the help of OpenAI’s ChatGPT. In November 2022, OpenAI -an Artificial Intelligence research and depl...

Dark Web Profile: MuddyWater APT Group
Dark Web Profile: MuddyWater APT Group [Update] April 19, 2023: Added subheading: “MuddyWater Uses SimpleHelp Tool for Persistence on Victim Devices” Security concerns grow day by day with the rise of...

4 Lessons Learned from Supply Chain Attacks in 2022
4 Lessons Learned from Supply Chain Attacks in 2022 At the BlackBerry Security Summit in 2022, four-fifths of IT decision-makers said they had been notified of an attack or vulnerability in ...

RCE Vulnerability (CVE-2022-45359) in Yith WooCommerce Gift Cards Plug...
RCE Vulnerability (CVE-2022-45359) in Yith WooCommerce Gift Cards Plugin Exploited in Attacks In late November, security researchers found a critical vulnerability in Yith’s WooCommerce Gif...

Gartner Recognizes SOCRadar as an EASM Vendor in Hype Cycle for Endpoi...
Gartner Recognizes SOCRadar as an EASM Vendor in Hype Cycle for Endpoint Security Report Gartner’s report with comprehensive analysis and insights for endpoint security has been published. ...

CVE-2022-47633 Vulnerability Allows Attackers to Bypass Kyverno Signat...
CVE-2022-47633 Vulnerability Allows Attackers to Bypass Kyverno Signature Verification The Kyverno admission controller for container images has been found to have a high-severity security v...

The Week in Dark Web – 26 December 2022 – Data Leaks and Access Sales...
The Week in Dark Web – 26 December 2022 – Data Leaks and Access Sales Powered by DarkMirror™ We’re in the last week of the year. Most of us have already gone to visit our loved ones for a holida...

All You Need to Know About the Linux Kernel ksmbd Remote Code Executio...
All You Need to Know About the Linux Kernel ksmbd Remote Code Execution (ZDI-22-1690) Vulnerability Five new vulnerabilities, one of which has a severity rating of 10 according to the Common Vulnerabi...

400 Million Twitter Users Data Allegedly Breached for Extortion
400 Million Twitter Users Data Allegedly Breached for Extortion On December 23, 2022, a threat actor shared a post on a dark web forum monitored by SOCRadar, claiming to possess 400 million Twitter u...
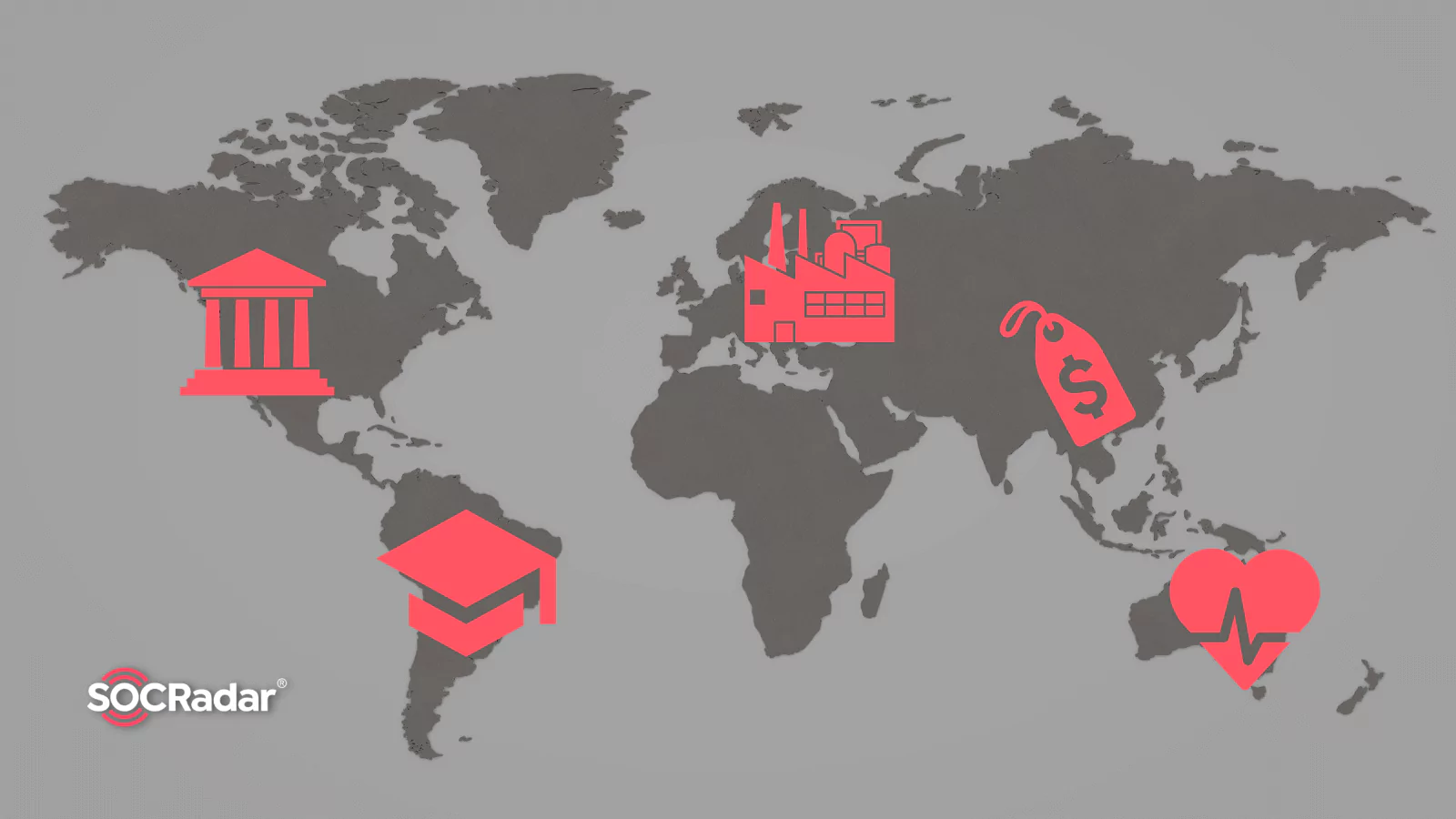
Top 10 Targeted Industries and Countries in 2022
Top 10 Targeted Industries and Countries in 2022 No matter the industry, cyberattacks can cause various problems, ranging from minor disruptions to significant losses or, even worse, lawsuits against ...

AWS Elastic IP Transfer Feature Could Be Exploited in Attacks
AWS Elastic IP Transfer Feature Could Be Exploited in Attacks Researchers have discovered a new security risk to a recently added feature in Amazon Web Services (AWS). Elastic IP transfer, ...



































