
Increasing Cyberattacks Targeting the Gaming Industry in 2022
Increasing Cyberattacks Targeting the Gaming Industry in 2022 By SOCRadar Research The gaming industry has recently emerged as a preferred target for cyberattacks. The industry is constantly...

Top 10 Cyber Incidents in 2022
Top 10 Cyber Incidents in 2022 2022 was a year in which everyone worked to overcome the COVID-19 pandemic and a year in which threat actors simply tried to profit more from it. Threat actors...
An Analysis of Central Banks Hackings: Who is Next?
An Analysis of Central Banks Hackings: Who is Next? By SOCRadar Research Critical infrastructures are the basis for the functioning of the countries’ system, and they are essential to continue t...

Reports of ProxyNotShell Vulnerabilities Being Actively Exploited (CVE...
Reports of ProxyNotShell Vulnerabilities Being Actively Exploited (CVE-2022-41040 and CVE-2022-41082) According to reports, the zero-day vulnerabilities CVE-2022-41040 and CVE-2022-4108...

Top 10 Data Leaks in 2022
Top 10 Data Leaks in 2022 Threat actors need sensitive information to carry out most of their malicious activity. They typically obtain the information by conducting various cyberattacks or simply gat...

The Week in Dark Web – 19 December 2022 – Access Sales and Leaks
The Week in Dark Web – 19 December 2022 – Access Sales and Leaks Powered by DarkMirror™ Threat actors always search for something profitable for their malicious activities, whether a government instit...

Veeam Fixes Critical Vulnerabilities in Backup & Replication Software ...
Veeam Fixes Critical Vulnerabilities in Backup & Replication Software (CVE-2022-26500 & CVE-2022-26501) Veeam has recently fixed two security vulnerabilities (CVE-2022-26500 and CV...

Dark Web Profile: Killnet - Russian Hacktivist Group
Dark Web Profile: Killnet – Russian Hacktivist Group By SOCRadar Research The ongoing conflict between Ukraine and Russia has attracted the attention of various cybercriminal groups and pushed t...

Dark Web Profile: Black Basta Ransomware
Dark Web Profile: Black Basta Ransomware By SOCRadar Research [Update] January 3, 2024: Read the subheading “Turning the Tables on Black Basta” One of the perpetrators of the ransomware attacks, whic...

Microsoft Reevaluates SPNEGO NEGOEX Vulnerability CVE-2022-37958 as Cr...
Microsoft Reevaluates SPNEGO NEGOEX Vulnerability CVE-2022-37958 as Critical Microsoft reassessed the severity score of a vulnerability fixed in September 2022 Patch Tuesday. The vulnerabi...

Top 5 Vulnerabilities Routinely Exploited by Threat Actors in 2022
Top 5 Vulnerabilities Routinely Exploited by Threat Actors in 2022 By SOCRadar Research Day by day, it becomes harder to maintain a good security posture. Threat actors are at every corner, searching ...

Gartner Recognized SOCRadar as a DRPS Vendor in 2 Reports
Gartner Recognized SOCRadar as a DRPS Vendor in 2 Reports The digitalization process has become a norm in any business. Now, organizations’ assets are highly increased, and there are many things...

The Week in Dark Web – 14 December 2022 – Access Sales and Leaks
The Week in Dark Web – 14 December 2022 – Access Sales and Leaks Powered by DarkMirror™ Just a few weeks remain to close 2022. We are all in the mood for the holiday season, but it seems threat actors...

APT5 Exploits Zero-Day Vulnerability on Citrix ADC and Gateway Devices
APT5 Exploits Zero-Day Vulnerability on Citrix ADC and Gateway Devices Citrix has just released a patch to address a critical zero-day vulnerability affecting its products. The vulnerability...

Fortinet Released Patch for FortiOS SSL-VPN RCE Vulnerability CVE-2022...
Fortinet Released Patch for FortiOS SSL-VPN RCE Vulnerability CVE-2022-42475 Fortinet has released a patch for a critical zero-day security vulnerability affecting its FortiOS SSL-VPN product. The vul...

Dark Web Profile: APT42 - Iranian Cyber Espionage Group
Dark Web Profile: APT42 – Iranian Cyber Espionage Group By SOCRadar Research After the Stuxnet occurred in 2010 on Iran’s nuclear program, Iran started to invest in and improve its cy...

Major Cyber Attacks in Review: November 2022
Major Cyber Attacks in Review: November 2022 Although the industry was relatively quiet last month, information is always valuable to both threat actors and us; in fact, it is vital. Helping you to pr...

All You Need To Know About the MegaRAC BMC Vulnerabilities
All You Need To Know About the MegaRAC BMC Vulnerabilities ...
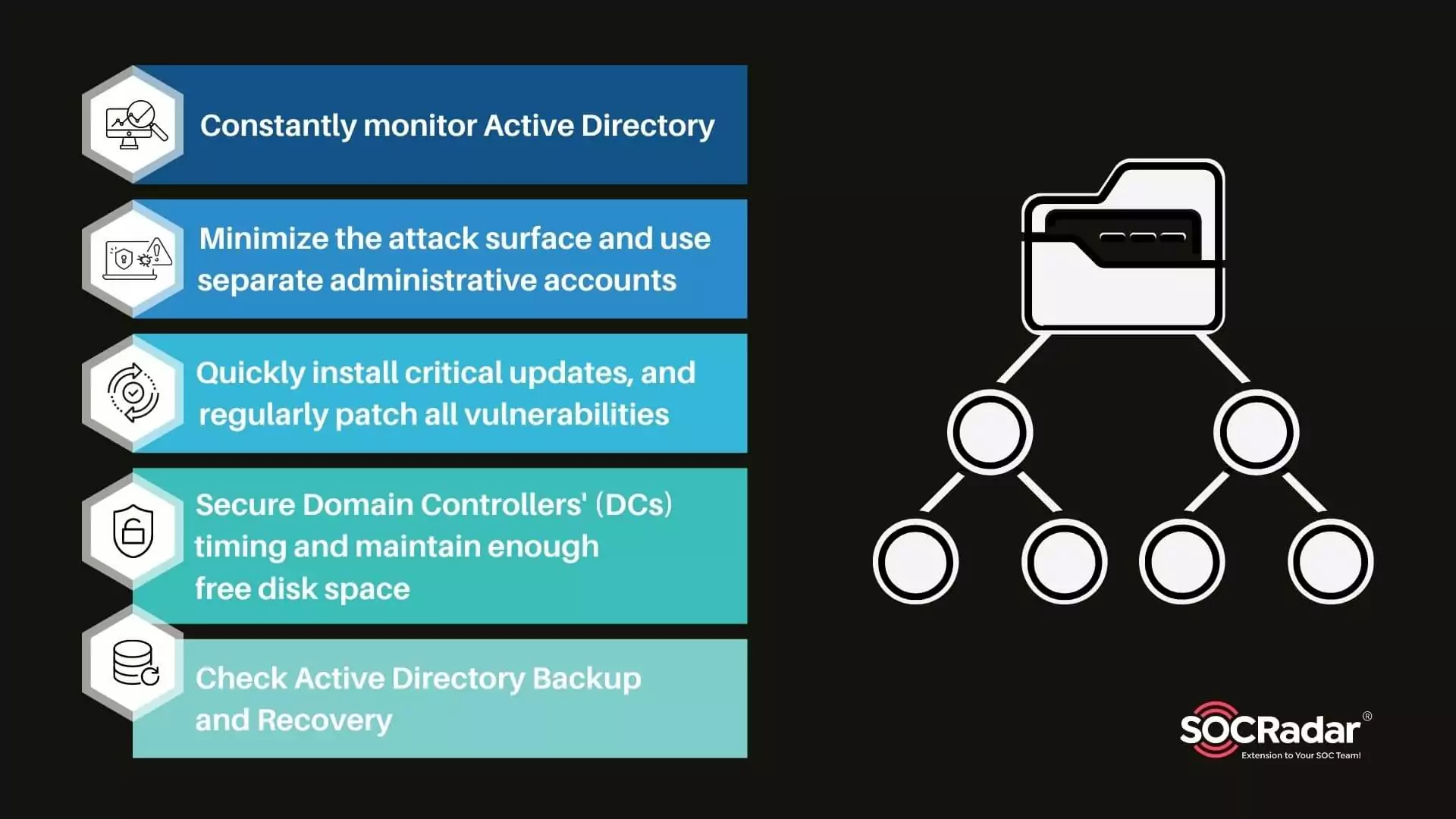
Security for Active Directory in 5 Steps
Security for Active Directory in 5 Steps Microsoft Windows directory service Active Directory (AD) enables IT administrators to manage permissions and restrict access to network resources. With this ...

Danger Lurking in GitHub Repositories
Danger Lurking in GitHub Repositories By SOCRadar Research GitHub is a system that has become the world’s largest source code repository, used by %90 of Fortune 100 companies and 94 million...



































