
Cyber Threats Targeting U.S. Elections in 2024
[Last Update] November 5, 2025: “Deepfakes, Disinformation, and Alternative Facts: Voice-based scams” / “Voting Machine Hacking – Colorado’s voting systems leak” / “Phishing Threats: 4.6 million records from Illinois”
As the 2024 U.S. presidential election approaches, the political atmosphere is charged with significant issues that will undoubtedly shape the campaigns of the leading candidates. With a polarized electorate and pressing national concerns, both Kamala Harris and Donald Trump frame their narratives to resonate with voters.
Key themes at the forefront of this election include abortion, border security and immigration, climate change, the state of democracy, economic concerns, education, foreign policy (particularly regarding the Russia-Ukraine war and the Israel-Hamas conflict), healthcare, and LGBTQ+ rights.
Harris’s approach may resonate particularly well with younger voters and those concerned about social justice issues. Her emphasis on abortion rights, climate change, and LGBTQ+ rights aligns with the priorities of many constituents who feel that these issues are fundamental to personal freedom and equality.
Trump’s supporters are mainly motivated by issues such as border security and immigration, viewing them as essential to national sovereignty and safety. Trump’s stance will likely energize voters who prioritize strict immigration policies, making it a cornerstone of his campaign strategy.
As we approach November 5, 2024, these themes will undoubtedly influence voter sentiments across the nation. The contrasting visions presented by Kamala Harris and Donald Trump reflect deeper societal divisions but also highlight opportunities for dialogue on crucial issues facing America today.
Voter engagement will be essential in determining not only who wins the presidency but also how these pivotal issues are addressed in the years to come.

Generated by ImageFX
A distinct pattern emerges when examining potential threats to elections. The primary danger does not stem from financially motivated actors; instead, it predominantly arises from those driven by political motives. While this may look evident, identifying the threats can be complex.
In recent years, the integrity of U.S. elections has become increasingly vulnerable to various cybersecurity threats. As we approach the 2024 presidential elections, the stakes are higher than ever due to a surge in sophisticated cyberattacks, misinformation campaigns, and foreign interference. These threats jeopardize the electoral process and undermine public trust in democratic institutions.
This article aims to explore the multifaceted cybersecurity threats targeting U.S. elections, analyze their implications for democratic processes, and propose strategies for enhancing resilience against such attacks.
Deepfakes, Disinformation, and Alternative Facts
In the digital age, the proliferation of deepfakes and disinformation campaigns poses a significant threat to election integrity. These technologies can create realistic but fabricated content that misleads voters and undermines trust in the electoral process. As political narratives become increasingly manipulated, distinguishing between fact and fiction is crucial for maintaining a healthy democracy.
To learn more about deepfake scams, you can visit our CISO Guide to Deepfake Scams.
When it comes to disinformation, the threat landscape takes a different shape. Political parties, consultancies, and politically motivated threat actors share the spotlight. In January, a fake audio of U.S. President Joe Biden urged Democrats to stay home when New Hampshire voters prepared for the state’s first-in-the-nation primary. A rival state did not do this, but a political consultant. According to NBC News, Steve Kramer, a political consultant with a company specializing in the projects that help increase voter turnout in the elections, was behind the call.
The use of personal data in U.S. elections has long been intertwined, a reality underscored by the events of 2016. In light of this, former President Donald Trump has issued a stark warning to Meta CEO Mark Zuckerberg, suggesting that if he interferes in the 2024 elections, he could “spend the rest of his life in prison.”

The White House refuted Zuckerberg’s claims and said it “encouraged responsible actions” from Facebook to ensure public safety (AP)
Such platforms serve as fertile ground for disinformation, raising significant concerns about the responsibilities of the parties involved—namely, the companies behind artificial intelligence models and the social media networks that host the information.
One of the primary risks associated with AI is the alarming combination of the detailed personality of users and their interests with AI-generated content. This convergence creates a significant threat, as it can facilitate highly personalized disinformation campaigns that exploit individual vulnerabilities. The misuse of such data amplifies the impact of AI-generated misinformation. It makes it more persuasive and challenging to detect since people will be less likely to realize that the content is fake since it impacts them emotionally.
Voice-based scams are a significant concern, amplified by deepfake and AI-driven text-to-speech technologies. Researchers have highlighted potential abuse of OpenAI’s real-time voice API in ChatGPT-4o. Despite safeguards the platform’s capabilities could be exploited in financial scams.
In a recent study, University of Illinois Urbana-Champaign (UIUC) researchers Richard Fang, Dylan Bowman, and Daniel Kang demonstrated that unrestricted tech tools with limited protections may enable large-scale scams. These operations can be scaled to reach bigger audiences while requiring minimal human intervention.
Even though this research focuses on financial scams, the content of the message can be changed based on the goals of the threat actors.
While social media platforms have become more cautious in managing user data since the 2016 election, creating groups based on individuals’ political beliefs does not necessarily require access to personal data. Anyone with sufficient knowledge of various political factions and their sub-groups can establish such groups and leverage AI to disseminate misleading information tailored to each audience’s predispositions.
Since it is harder for the Federal Government to reach every individual, local governments and other smaller governmental entities have more responsibility when it comes to fighting disinformation and helping people access accurate information during the election process.
- Education Initiatives: Local governments should launch awareness campaigns and host informational events to educate residents about misinformation and how to identify it. By fostering media literacy, communities can become more adept at recognizing false or deceptive information, thereby reducing its impact.
- Promotion of Local Media: Supporting local news outlets is vital, as these sources often provide more trustworthy information than broader social media platforms. Local governments can share posts from these organizations or host press conferences to highlight their work and encourage community engagement with local journalism.
- Dedicated Fact-Checking Platforms: Establishing a website or app where residents can submit articles or social media posts for verification can empower citizens to fact-check their news sources. This initiative would provide a reliable resource for residents seeking to discern truth from misinformation.
These strategies help build trust within communities and empower residents to engage critically with the information they encounter.
Foreign countries are also after muddying the waters with fake news and disinformation. In a criminal case made public by the Justice Department, two employees of the Russian state media outlet RT are accused of secretly giving almost $10 million to a content production company based in Tennessee to post videos that promote the interests of the Russian government, including the conflict in Ukraine and apperantly, the videos posted by this company got more than 16 million views on YouTube alone.
In addition to using local sources for disinformation campaigns, officials announced that 32 domains used by Kremlin for propaganda purposes were seized. The websites were designed as real news sites but they were actually fake.
Another attempt from Russia was targeting Kamala Harris. Microsoft clarified that the video, which targeted Harris for a fake hit-and-run event, originated from Storm-1516, a Russian-affiliated influence network, aka CopyCop.
Another nation attempting to meddle in the US elections is China. According to several people familiar with the situation who spoke to the BBC’s US news partner, CBS News, US authorities believe that cybercriminals associated with China may have tried to access the phones or networks used by former President Donald Trump and his running mate, Senator JD Vance. The Trump-Vance campaign had been informed that Trump and Vance’s phones might have been among the targets of a larger cyberattack.
Additionally people connected to the Harris-Walz campaign were also targeted, a source informed BBC News. How much information, if any, may have been compromised is unknown.
The Tech Accord from the Munich Security Conference
Tech companies are also responsible for protecting the public from deepfakes. Therefore, various companies pledge to work together to detect and counter harmful AI content. The Tech Accord to Combat Deceptive Use of AI in 2024 Elections is a set of commitments to deploy technology countering harmful AI-generated content to deceive voters.

Tech Accord to Combat Deceptive Use of AI in 2024 Elections, Munich Security Conference
The companies in this Tech Accord pledge to collaborate on tools to detect and address the online distribution of such AI content and provide education.
The digital content addressed by the AI Content Accord encompasses AI-generated audio, video, and images that deceptively manipulate or fabricate the appearance, voice, or actions of political candidates, election officials, and other key stakeholders in democratic elections. This includes misleading information directed at voters regarding when, where, and how they can vote.
The current signatories of the AI Elections Accord are Adobe, Amazon, Anthropic, ARM, ElevenLabs, Gen, GitHub, Google, IBM, Inflection AI, LG AI Research, LinkedIn, McAfee, Meta, Microsoft, NetApp, Nota, OpenAI, Snap, Stability AI, TikTok, TrendMicro, TrueMedia, TruePic, and X.
Participating companies agreed to eight specific commitments:
- Developing and implementing technology to mitigate risks related to Deceptive AI Election content, including open-source tools where appropriate.
- Assessing models in the scope of this accord to understand the risks they may present regarding Deceptive AI Election Content.
- Seeking to detect the distribution of this content on their platforms.
- Seeking to appropriately address this content detected on their platforms.
- Fostering cross-industry resilience to Deceptive AI Election Content.
- Providing transparency to the public regarding how the company addresses it.
- Continuing to engage with a diverse set of global civil society organizations, academics.
- Supporting efforts to foster public awareness, media literacy, and all-of-society resilience.
As highlighted previously, the role of AI in elections and the potential for misuse is significant. Generative AI technologies can create highly realistic deep fakes that may mislead voters and undermine trust in the electoral process.
Voting Machine Hacking
The security of voting machines is paramount in safeguarding the democratic process. Voting machine hacking represents a critical vulnerability that can lead to unauthorized access, data manipulation, and potential election outcomes being compromised.
Even though the voting machines don’t connect to the internet directly, vendors can make mistakes or create workarounds to maintain the tool. A similar case occurred in 2018 when a vendor admitted that they installed remote access software on their systems over six years ago but claimed to have stopped the practice.
Besides remote access, these tools are also vulnerable to certain threats since the companies manufacturing them are open to threats. We analyzed our stealer logs data and checked several companies manufacturing voting machines. As a result of this analysis, we detected data from several companies in our stealer logs database. You can check this article’s Stealer Logs Analysis section for more information.
After the voting machines are manufactured ready to use, they become the responsibility of states. The importance of security training for public officials comes into play at this point. Colorado’s voting systems faced scrutiny after a spreadsheet containing one of two passwords required for access was found online. This two-password system, with credentials stored separately by different parties, is part of a layered security protocol, according to the Secretary of State’s office. Officials have since changed passwords, reviewed access logs, and assessed chain of custody records.
Even though the Secretary of State Jena Griswold emphasized that the incident does not pose a security threat, noting that not all exposed passwords were active and no breach has occurred, such incidents can be the ingredient for further disinformation operations.
Furthermore, machines can also be vulnerable to various physical threats. If a threat actor can physically access machines during transportation or while in a warehouse, they can try to exploit them.
Finally, disinformation efforts related to the voting machines are another threat to the elections. Threat actors can even utilize a discourse about a vulnerability for disinformation purposes.

Polling Place, Source – Politico
For example, when election officials in New Hampshire decided to replace the state’s aging voter registration database before the 2024 election, they decided to work with a small, Connecticut-based IT firm. However WSD Digital decided to offshore part of the work. After the officials decided to investigate the technology, the forensic firm hired found out that the software was misconfigured to connect to servers in Russia and that a Russian computer engineer oversaw the open-source code used.
Such discoveries raise immediate concerns about potential vulnerabilities and the integrity of the election system since the possibility of foreign access to sensitive voter data is a serious issue.
Other than voting machines, another physical threat to the elections might come from the volunteers. CISA already published a guide on how to mitigate this risk related to insider threats. These threats may involve attempts to damage ballots, grant unauthorized access to voting facilities, infiltrate computer networks, gather information from unauthorized or unrelated sources, and more.
Transform your cyber defense with SOCRadar’s Vulnerability Detection service. Experience unparalleled vigilance in safeguarding your digital assets.
SOCRadar Vulnerability Detection service
DDoS Attacks
Distributed Denial-of-Service (DDoS) attacks have emerged as a formidable threat against election infrastructure. By overwhelming systems with traffic, attackers can disrupt services essential for conducting elections, such as voter registration websites and result reporting platforms. This chapter will examine the mechanics of DDoS attacks, their potential impact on election operations, and the proactive steps organizations can take to mitigate these risks and ensure uninterrupted electoral processes.
With technological advancements, DDoS attacks are becoming less disruptive. However, this development also allows threat actors to increase the frequency of their DDoS attacks. We saw a similar pattern with the DDoS attacks and other low-level cyber threats targeting the United Kingdom after their military equipment started being used on Russian soil.
Back in the 2022 midterms, Google’s Project Shield DDoS protection tool detected a 4x increase in weekly attacks while defending websites against more than 25,000 attacks.
As the 2024 elections approach, the potential for large-scale DDoS attacks can be even greater. However, according to a joint alert from the Cybersecurity and Infrastructure Security Agency (CISA) and the FBI issued on July 31, these attacks are unlikely to prevent voters from casting their ballots.
If a DDoS attack or a similar disruptive event, such as a ransomware attack, were to occur on or near Election Day, it could significantly impede voting processes.
Recent intelligence from Microsoft reveals that the Iranian state-linked threat actor known as Cotton Sandstorm (associated with the Islamic Revolutionary Guard Corps) has intensified reconnaissance on U.S. election-related websites.
The targeting of election-related websites suggests an interest in disrupting the functionality or credibility of U.S. information channels ahead of critical voting periods. The focus on reconnaissance and scanning indicates likely pre-operational planning for influence activities or direct interference in U.S. democratic processes.
Enhance your DDoS defense with SOCRadar’s DoS Resilience Free Tool. Our Free DoS Resilience Service allows you to check your domain’s or subnet’s resilience against DoS attacks, such as slow loris attacks.
SOCRadar’s DoS Resilience Free Tool
Defacement Attempts
Defacement is a form of cyber vandalism where an attacker modifies the appearance or content of a website without authorization. However, in terms of elections, website defacement is not merely an act of vandalism; it is a tactic used to spread disinformation and create chaos during critical electoral periods. Attackers may alter official election websites to disseminate false information or undermine public confidence in the electoral process.
In 2020, a threat actor took control of then-President Trump’s campaign website, posted a message, and demanded payment to prevent the leak of alleged data.
Such events can occur, and even though they won’t impact the integrity of the elections, they may give rise to challenges related to communication breakdowns and the spread of disinformation.
Protect your online presence with SOCRadar’s integrated takedown services. You can initiate takedown requests for phishing sites and other content with a single click without incurring legal consequences.
SOCRadar Integrated Takedown service
Phishing Threats
Phishing remains one of the most prevalent cyber threats facing election officials and voters alike. By tricking individuals into divulging sensitive information through deceptive emails or websites, attackers can gain access to critical systems and data. This chapter will focus on the various forms of phishing attacks.
The leak that exposed 4.6 million records from Illinois which occurred back in August can be a good example of resources available for threat actors for their phishing operations. According to the research, individuals’ names, addresses, Social Security numbers, and other sensitive personally identifiable information, as well as ballot templates and other election records were leaked. While it is hard to impersonate these individuals and change the votes, such data can be easily used for disinformation or phishing operations.
New Phishing Template Targeting the U.S. Elections is on Sale
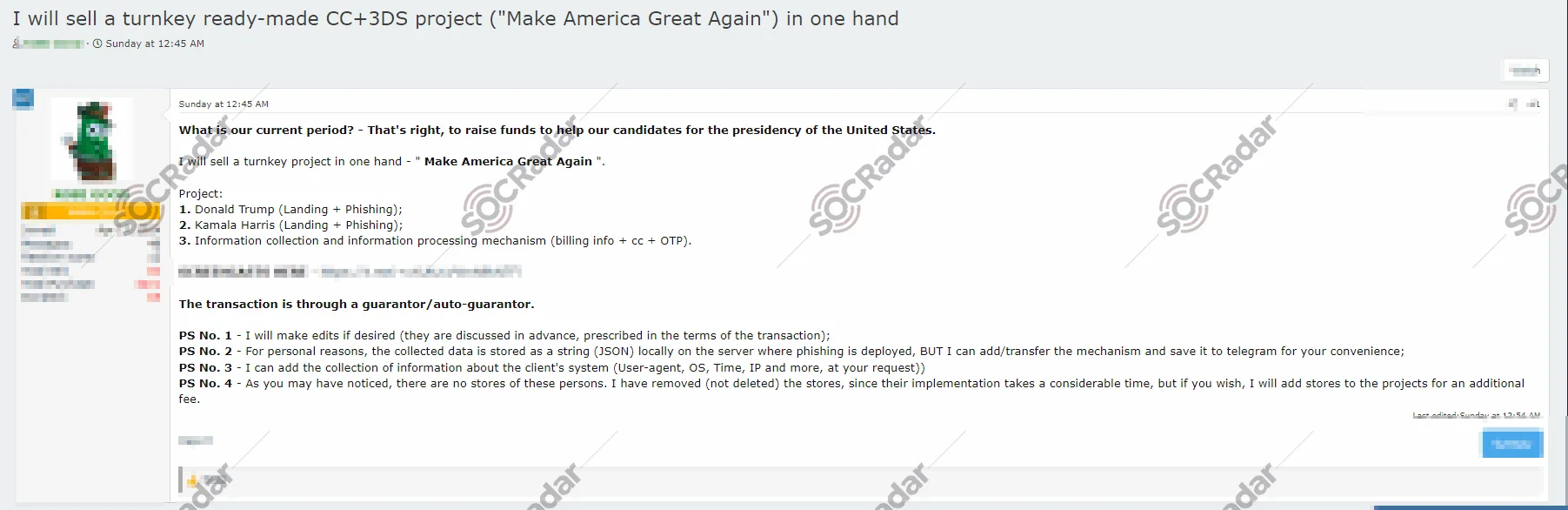
A threat actor selling phishing kit on a Dark Web forum monitored by SOCRadar
In a recent post on a Dark Web forum, an alleged threat actor has unveiled a phishing campaign project tied to the upcoming U.S. Presidential elections. The threat actor claims to sell turnkey phishing operations aimed at two high-profile political figures: Donald Trump and Kamala Harris.
The post outlines several critical components of the phishing campaigns, and in several additional notes, the threat actor offers customization options for buyers. The threat actor’s language suggests a potentially adaptable project ready for deployment.
While not yet verified, the post highlights the ongoing cyber risks surrounding the U.S. elections. The inclusion of high-profile political figures and the sophisticated nature of the phishing project underscores the need for heightened security measures in the lead-up to the election.
Phishing attempts targeting election officials and government workers represent a significant cybersecurity challenge, especially during critical election periods. These sophisticated attacks often aim to gain unauthorized access to voter databases, election systems, and internal communications. They create scenarios designed to pressure recipients into taking immediate action, often leveraging current events or real deadlines to make their fraudulent messages appear more credible.
To combat these threats, employing robust email filtering systems while providing thorough cybersecurity training for all staff and volunteers is crucial.
Dark Web Threats
The Dark Web is a breeding ground for discussions around malicious activities targeting elections. From selling stolen voter data to sharing tactics for disrupting electoral processes, this hidden part of the internet poses unique challenges for cybersecurity professionals. This chapter will explore how threats manifest in Dark Web forums, the implications for election security, and how monitoring these spaces can provide valuable insights into emerging risks.
Top Threat Categories Targeting the United States
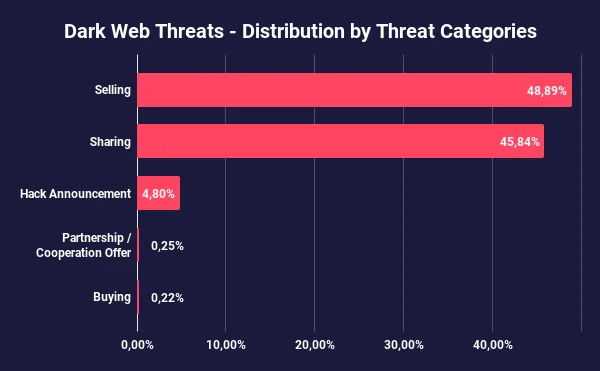
Distribution of dark web posts by threat category
Threat actors targeting the U.S. mostly sell content. Posts categorized as “Selling” account for 48.89% of all posts on Dark Web forums, making it the most prevalent category. “Sharing” ranks second, comprising 45.84% of forum activity, while “Hack Announcements” follow in third place, representing 4.80% of the posts.
Top Threat Types Targeting the United States
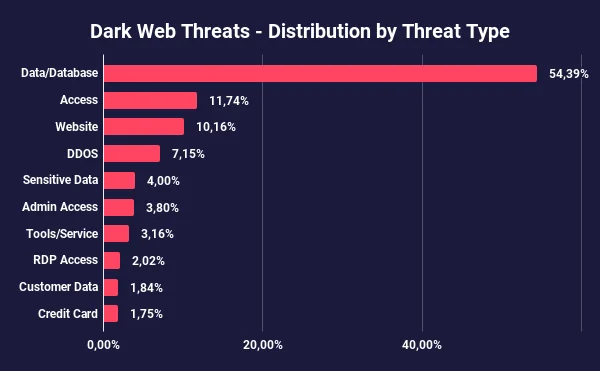
Distribution of dark web posts by threat type
When analyzing content shared on Dark Web forums, databases emerge as the predominant category, representing 54.39% of all posts. Access-related activities, including sales and exchanges, account for 11.74% of the shared content. Meanwhile, posts related to website attacks, such as defacements and DDoS incidents, constitute 10.16% of the total.
With SOCRadar Labs’s Dark Web Report, instantly discover if your data has been exposed on Dark Web forums, black market, leak sites, or Telegram channels. Request a Free Dark Web Report today to see what threat actors post about your company.
SOCRadar Labs Free Dark Web Report
Recent Developments From the Dark Web
The Alleged Data of The White House is Leaked
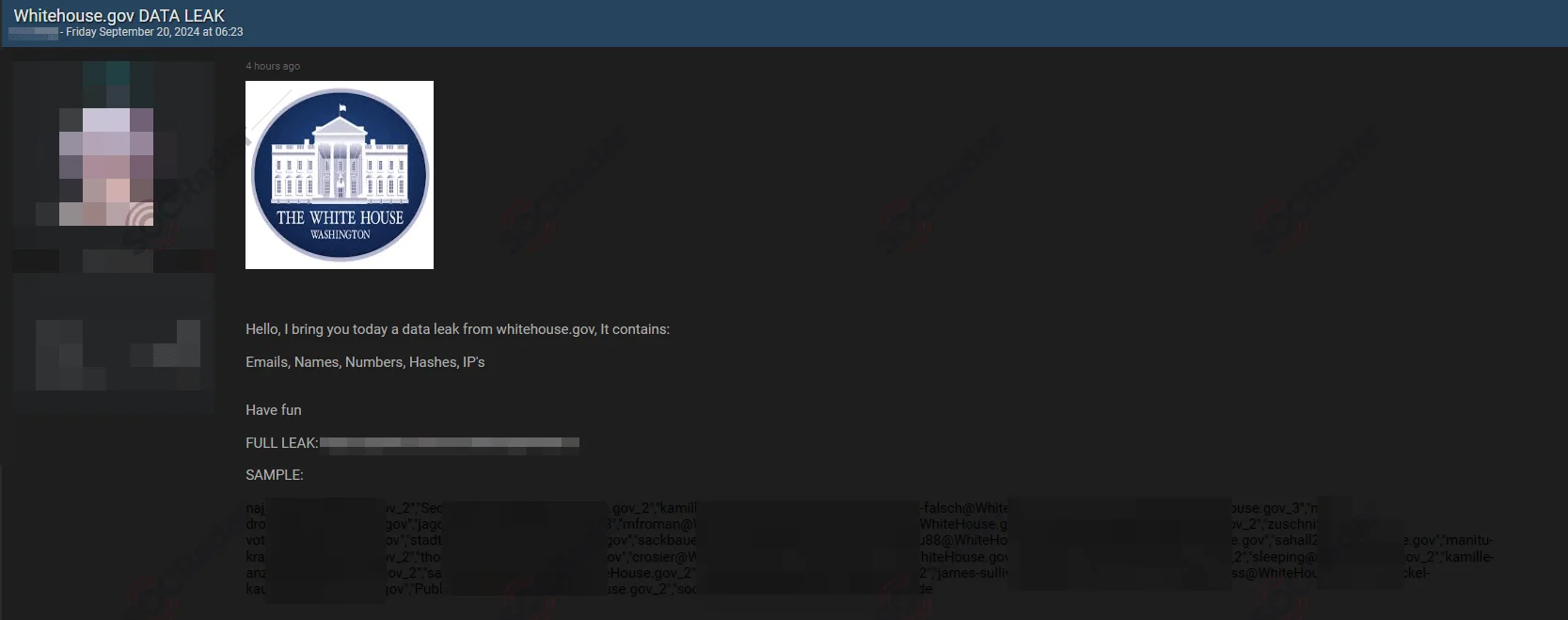
Alleged Data Leak from Whitehouse.gov Surfaces on Dark Web Forum
A threat actor has claimed responsibility for leaking sensitive information purportedly stolen from the White House’s official website. The alleged leak, posted on a Dark Web forum, reportedly contains a range of personal data, including emails, names, phone numbers, hashed passwords, and IP addresses.
In the post, the threat actor provided a link to the alleged dataset and a sample of the leaked information.
This incident is another example of the growing prevalence of attacks targeting high-profile institutions as threat actors continue to exploit security vulnerabilities for political leverage.
The Alleged Unauthorized Access Sales are Detected for Facebook, Instagram, and TikTok Law Enforcement Panels
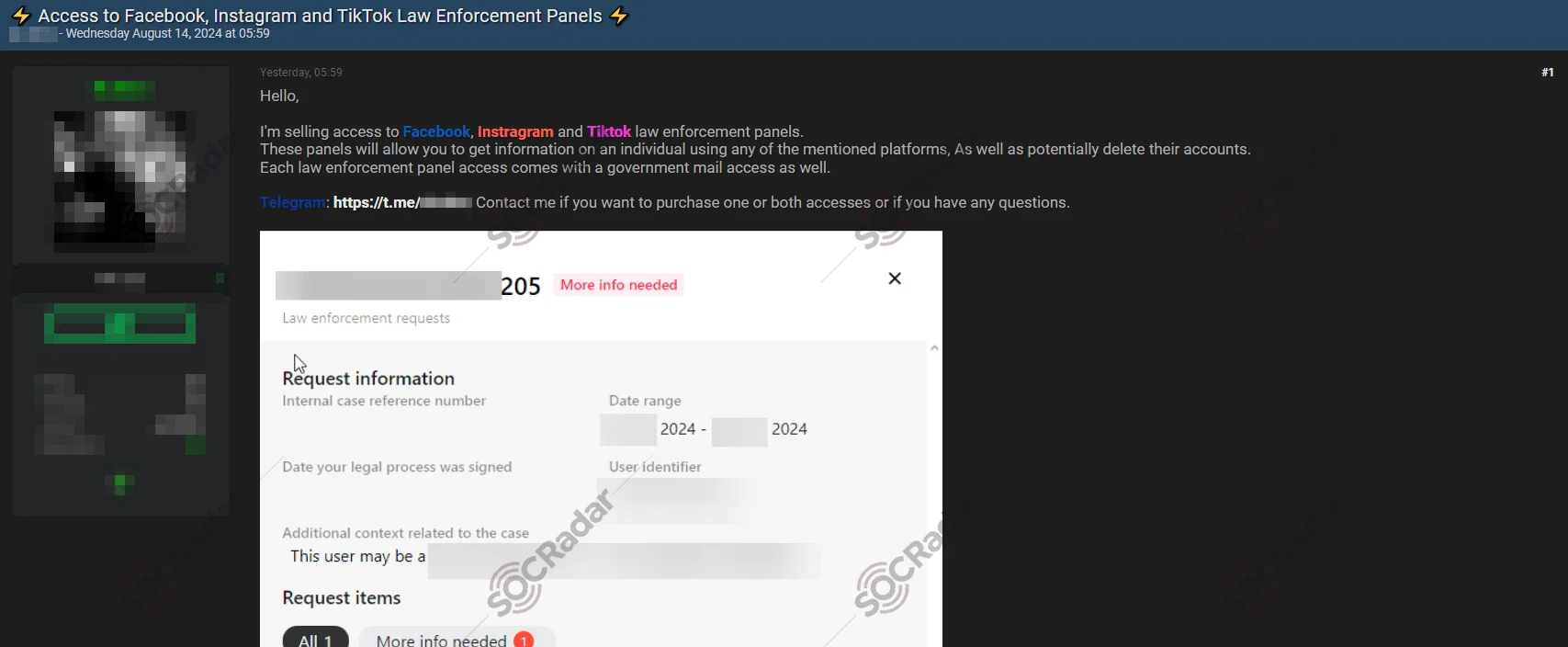
A threat actor claiming to sell access to law enforcement panels for major social media platforms
A threat actor in a Dark Web forum post allegedly offers access to law enforcement panels for major social media platforms, including Facebook, Instagram, and TikTok. The seller claims these panels can provide users with sensitive information about individuals using these platforms and even offer the potential to delete their accounts.
The post, addressed to prospective buyers, describes how each law enforcement panel comes bundled with access to a government email address, which would likely be required to access these tools. The implication is that with these credentials, unauthorized individuals could exploit the capabilities typically reserved for official investigations.
This type of unauthorized access, often offered on criminal forums, can result in significant risks, including phishing attacks or defacement attempts. Such accounts can also be used for disinformation purposes.
Database of National Public Data is Allegedly Leaked
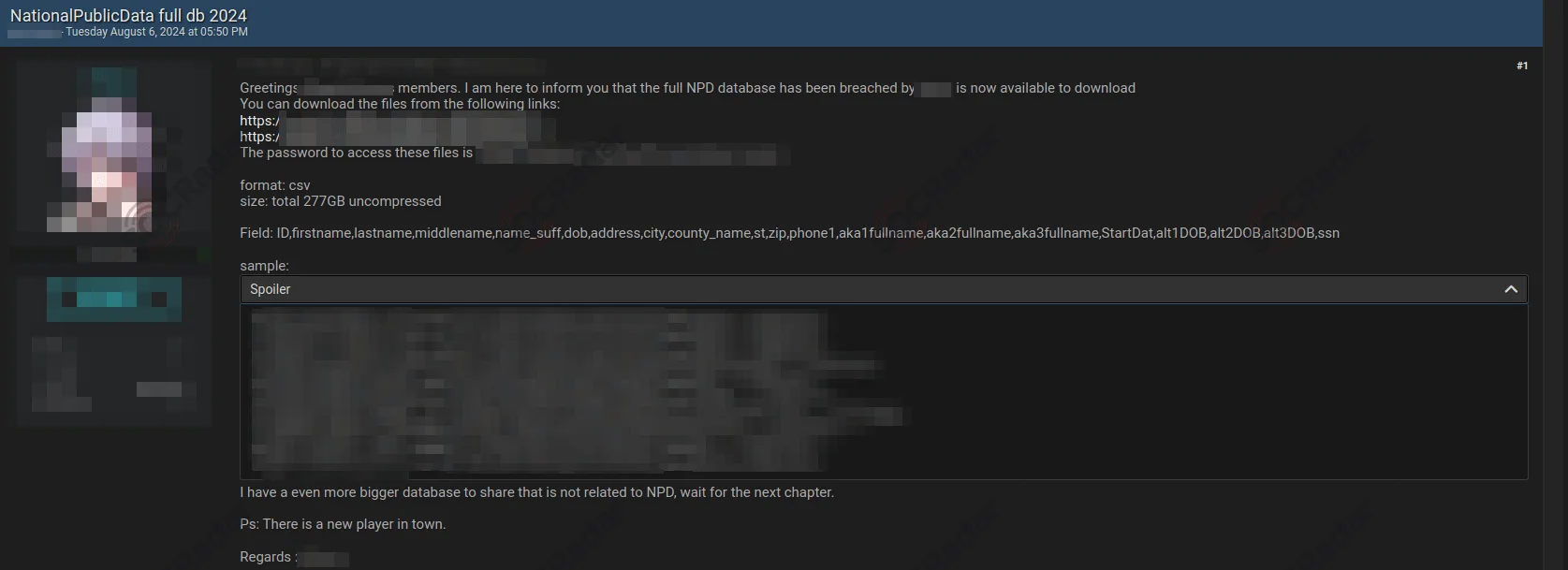
Alleged Data Breach of National Public Data Reported on Dark Web Forum
In a post on a Dark Web hacker forum, a threat actor has claimed responsibility for breaching the National Public Data (NPD) database, now allegedly offering the complete dataset for sale.
The dataset reportedly contains detailed personal information, including fields such as ID, full name, date of birth, addresses, city, county, state, zip codes, phone numbers, aliases, and even Social Security numbers. A sample of the dataset was made available for forum members to preview, potentially serving as a sales tactic.
The actor hinted at possessing an even larger database unrelated to the NPD breach, suggesting a continuing trend of data leaks in exchange for illicit financial gains.
According to Dark Reading, data aggregator National Public Data has confirmed the breach, which exposed personal identity records belonging to potentially hundreds of millions of people across the U.S., U.K., and Canada.
Such leaks enable threat actors to exploit individuals’ personal information for various purposes, including scams, disinformation campaigns, or other activities.
You can establish proactive monitoring capabilities to detect and mitigate potential data breaches, leaks, and illicit transactions involving sensitive information. Collaboration with threat intelligence providers can enhance visibility into Dark Web activities and enable timely threat response.
Learn about the latest Dark Web developments with SOCRadar’s Dark Web News module. SOCRadar’s Dark Web News page revolutionizes how you stay informed. It’s not just an information aggregator; it’s a sophisticated filter, meticulously separating the signal from the noise.
SOCRadar Dark Web News module
Stealer Log Analysis
Stealer logs are a significant concern in the realm of cybersecurity as they collect sensitive information from compromised systems. Analyzing these logs can reveal patterns of attack and help identify vulnerabilities within election infrastructure. This chapter will discuss the methodologies for stealer log analysis, its relevance in understanding cyber threats to elections, and how findings from such analyses can inform better security practices to protect electoral systems from exploitation.
Stealer Log Statistics: Top Domains Related to the Elections
| democrats.org | vote.gov |
| gop.com | fvap.gov |
| state.gov | verifiedvoting.org |
| nass.org | hartintercivic.com |
| bipartisanpolicy.org | microvote.com |
| unisynvoting.com | essvote.com |
| vote.org | clearballot.com |
| factcheck.org | dominionvoting.com |
| ifes.org | rockthevote.org |
| realclearpolitics.com | justfacts.votesmart.org |
| fec.gov | realclearpolling.com |
| tools.vote.org | vote411.org |
| opensecrets.org | ncsl.org |
In our analysis of potential threats related to the upcoming U.S. elections, we identified 26 domains associated with electoral activities and conducted a thorough examination for stealer logs. While not all domains released stealer logs, our investigation revealed a mix of outcomes: some domains were deemed safe, while others lacked a login system altogether. Nonetheless, our comprehensive scanning approach ensured that all identified domains were analyzed for potential risks.
Stealer Log Statistics
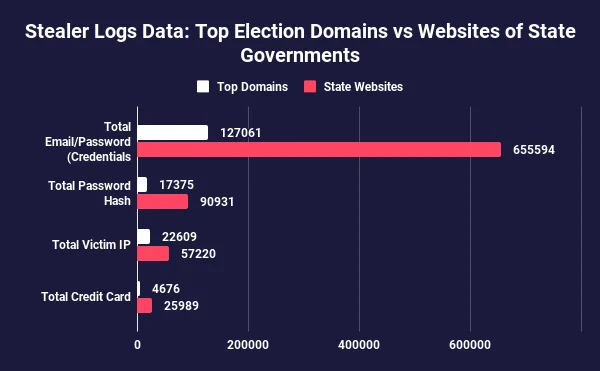
Comparison of the stealer logs from the top domains related to the elections and the official websites of the states
The graph highlights the distribution of stealer logs across key election-related domains and the official websites of all states, classified into four distinct categories. The total number of email and password combinations stands at 782,655, while the total number of password hashes amounts to 108,306. Additionally, the graph reveals a total of 79,829 victim IPs, along with 30,665 stolen credit card details, illustrating the extent of compromised data impacting these crucial domains.
Considering the fact that 13,112 credentials are exposed on average from each state government’s website, a valuable insight into the scale and nature of the cybersecurity risks surrounding election infrastructure can be gained.
Although not all exposed credentials may directly impact election infrastructure, threat actors can still attempt to exploit them to gain any form of advantage, including creating confusion or uncertainty.
The Alleged 2 Billion Lines of Stealer Logs are on Sale
A Dark Web forum post detected by SOCRadar
A post on a Dark Web forum claims access to a staggering 2 billion lines of sensitive data, with the threat actor boasting that the database is updated daily. The post offers potential buyers a customizable selection of information formats, including URLs, domains, keywords, emails, login details, and even full logs.
The post concludes by inviting interested parties to reach out via Telegram, a common communication method used in underground markets to facilitate illicit deals.
The example demonstrates that accessing desired data through criminal forums is relatively easy. Individuals seeking to influence elections or cause disruption can exploit these criminal services to gather information on their targets.
A scenario in which a threat actor collects data on an official and uses it for illicit purposes is entirely plausible.
Is knowing which key (identity) is stolen enough to secure your company building? Identity intelligence helps you determine which users’ keys have been stolen, but Access Intelligence is crucial for knowing when, how, and where those keys are stolen.
SOCRadar equips users with detailed access information, including on which date, in which info stealer malware, from which computer, and from which IP address the compromised credentials are exposed.
You can check whether your employee’s credentials are exposed on the Identity & Access Intelligence module.
SOCRadar Identity & Access Intelligence module
Resources
Ensuring the integrity and security of elections requires access to the right resources, tools, and information. In today’s digital landscape, where adversaries continuously evolve their tactics, it is essential for election officials, cybersecurity teams, and stakeholders to stay well-informed and equipped to counter potential threats. This chapter highlights key resources aimed at safeguarding election infrastructure against cyberattacks. By leveraging these resources, election authorities can enhance their resilience, mitigate risks, and preserve voter confidence.
- Election Infrastructure Cybersecurity Readiness and Resilience Checklist.
- Frequently Asked Questions page of the National Association of State Election Directors.
- Helpful Links and Resources by the National Association of State Election Directors.
- Electoral College U.S. Voting and Election Resources.
- U.S. Department of State 2024 Elections Resources.
- Open Secrets is a research group tracking money in U.S. politics and its effect on elections and public policy. You can follow their website for related matters.
- #Protect2024 is CISA’s support page for election officials and private sector election infrastructure partners where they address the physical, cyber, and operational security risks they face.
- Rumor vs Reality is a resource by CISA that addresses election security rumors by describing common and generally applicable protective processes, security measures, and legal requirements designed to deter, detect, and protect against significant security threats related to election infrastructure and processes.
- #TrustedInfo2024 is a public education effort by NASS to promote election officials as the trusted sources of election information during the 2024 election cycle and beyond.
- United States Elections Assistance Commission also provides resources about the 2024 elections at the Election Security Preparedness page.
Key Suggestions for U.S. Elections
This is our short guide outlining critical groups involved in the U.S. elections, along with specific cybersecurity and cyber hygiene practices they should adopt to ensure a more secure election period:
- Voters
- Understand how to verify information about candidates, measures, and polling locations.
- Be cautious of false information circulating on social media. Use official state election websites for accurate information.
- Keep software and apps updated, use strong passwords, and enable two-factor authentication.
- Avoid clicking on suspicious links in emails or texts claiming to be from election officials.
- Report fake news and other types of information.
- Use fact-checking services to reach out for accurate information.
- Campaign Officials
- Use secure channels for sensitive communications and ensure all staff members are trained on cybersecurity practices.
- Verify claims before sharing. Utilize fact-checking organizations to dispel false narratives.
- Actively track and address misinformation targeting the campaign, providing clear counter-messaging when necessary.
- Regularly back up campaign data and use secure file-sharing methods.
- Campaign Volunteers
- Only rely on verified campaign materials and communication channels for information and outreach.
- Notify campaign officials if they encounter phishing attempts or any suspicious communications.
- Use unique passwords for campaign-related accounts and enable two-factor authentication.
- Be cautious with suspicious emails or messages. Report if necessary.
- News Agency Employees
- Always check the credibility of sources before reporting or sharing information, especially concerning election-related news.
- Employ fact-checking teams to ensure accurate reporting, especially around contentious issues.
- Provide resources for the public to discern reliable news from disinformation, including tips for verifying information.
- Federal Government Employees
- Be aware of the potential for targeted phishing attacks and other cyber threats during election periods.
- Participate in cybersecurity awareness programs and training specific to election security.
- Work with state and local election officials to ensure they have the necessary resources and information to protect election integrity.
- Local Government Officials
- Work closely with state and federal election officials to share best practices and receive guidance on cybersecurity measures.
- Provide comprehensive cybersecurity training for all election workers, emphasizing the importance of recognizing phishing attempts and maintaining data security.
- Educate the community about how to report suspicious activities and misinformation related to elections, fostering a proactive approach to cybersecurity.
Conclusion and Recommendations
As we navigate the complexities of the digital age, the cybersecurity threats targeting U.S. elections present a formidable challenge that demands attention and swift action. The potential for cyberattacks to disrupt electoral processes, manipulate public opinion, and erode trust in democratic institutions cannot be overstated. This report has highlighted the diverse range of threats—from sophisticated foreign interference to domestic misinformation campaigns—and underscored the critical need for comprehensive strategies to mitigate these risks.
Human error remains a significant factor contributing to these vulnerabilities. As election officials navigate complex technologies and processes, the potential for mistakes increases, making systems susceptible to exploitation by malicious actors. By understanding these challenges, stakeholders can work towards safeguarding the integrity of future elections.
To safeguard the integrity of upcoming elections, stakeholders—including government agencies, election officials, technology providers, and the public—must collaborate to foster a culture of cybersecurity awareness and resilience. Implementing robust security measures, investing in education, and promoting transparency in electoral processes are vital to enhancing our defenses against cyber threats.
Moreover, ongoing education and training for election personnel and public outreach initiatives to inform voters about potential disinformation tactics will empower citizens to engage more critically with information sources. As we approach the 2024 elections, we must remain vigilant and proactive in addressing these cybersecurity challenges. By prioritizing election security, we can protect not only the integrity of our democratic processes but also the foundational principles of trust and accountability that underpin our society. A secure electoral environment is essential for ensuring that every voice is heard and every vote counts.







































