
Dark Web Profile: CosmicBeetle (NoName) Ransomware
CosmicBeetle, also known as NoName, is a ransomware group that has targeted small to medium enterprises globally with its customized ransomware tools. Notably active since 2020 and gaining traction in 2023, the group has worked to establish a foothold in the cybercrime landscape by deploying unique encryption software like ScRansom. Known for attempting to mimic the infamous LockBit ransomware group, CosmicBeetle has adopted similar strategies, including a DLS (Data Leak Site) designed to pressure victims into paying ransoms.
Illustration of CosmicBeetle (Bing AI)
Who is CosmicBeetle(NoName)?
The ransomware group CosmicBeetle, tracked by cybersecurity firms as NoName, first appeared in 2020, but its activities have escalated significantly in 2023. While the group should not be mistaken for a pro-Russian hacktivist group with the same moniker as NoName057(16), it has established itself as a prominent cyber threat with a distinct operational profile. CosmicBeetle primarily targets small to medium-sized enterprises worldwide, often breaching networks using brute-force attacks and exploiting known vulnerabilities, such as EternalBlue (CVE-2017-0144) and Zerologon (CVE-2020-1472).

Threat actor card for CosmicBeetle(NoName)
CosmicBeetle has experimented with different malware families over the years, including Spacecolon, Scara, and ScRansom, an encryption tool based on Delphi. ScRansom is known for its partial encryption capability, offering operators multiple encryption speeds and an “ERASE” mode that permanently destroys file content, rendering it irretrievable. This ransomware can encrypt files across multiple storage media, including networked and removable drives, and can be configured to target specific file extensions, enhancing its versatility in attacks.
In their quest for notoriety, CosmicBeetle once mimicked LockBit’s data leak site (DLS), launching a site called “NONAME” that replicates LockBit‘s theme and ransom note style. While the group doesn’t exfiltrate data consistently, they employ this site to create a sense of urgency among victims, coercing them into compliance. Their attempts at replicating LockBit’s methods illustrate a strategy to leverage the reputation of established ransomware groups while bolstering their own visibility on the Dark Web and the media as well.
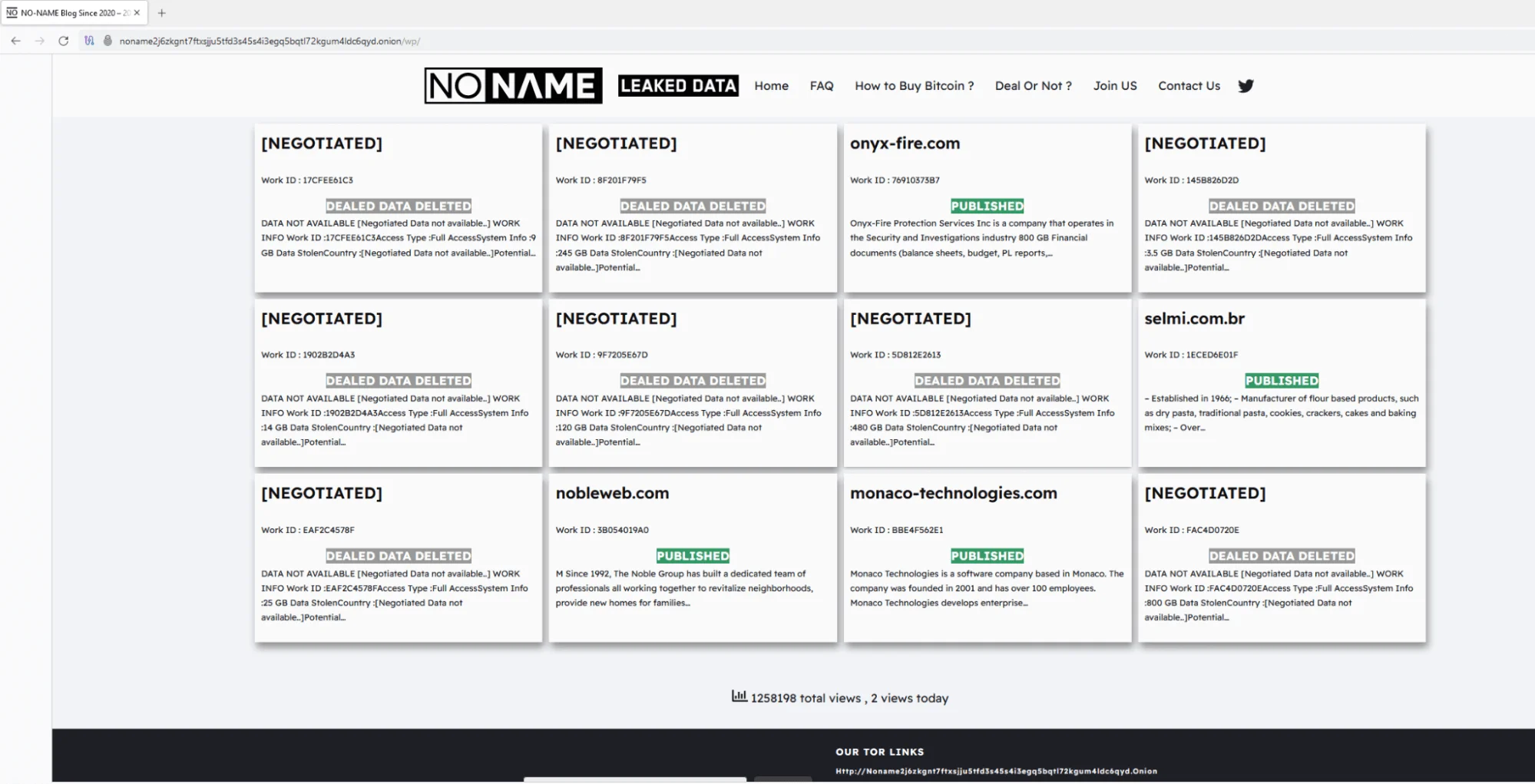
Overly similar DLS site design to LockBit’s DLS (ESET)
At the time of writing, all of CosmicBeetle’s DLS domains are inactive. However, with a rebrand, or even by adopting literally a no-name approach as an affiliate of RansomHub or another RaaS program, they are highly likely to remain active.
What Are Their Targets?
CosmicBeetle primarily targets small to medium-sized businesses (SMBs) in various sectors worldwide. According to ESET’s telemetry, this group has been highly active across different verticals, particularly focusing on regions in Europe and Asia. The most commonly affected industries include manufacturing, pharmaceuticals, healthcare, technology, legal, education, hospitality and leisure, financial services, and even regional government bodies. This broad array of targets reflects a strategic approach aimed at sectors where cybersecurity measures might be less mature or underfunded, making these businesses more susceptible to exploitation.
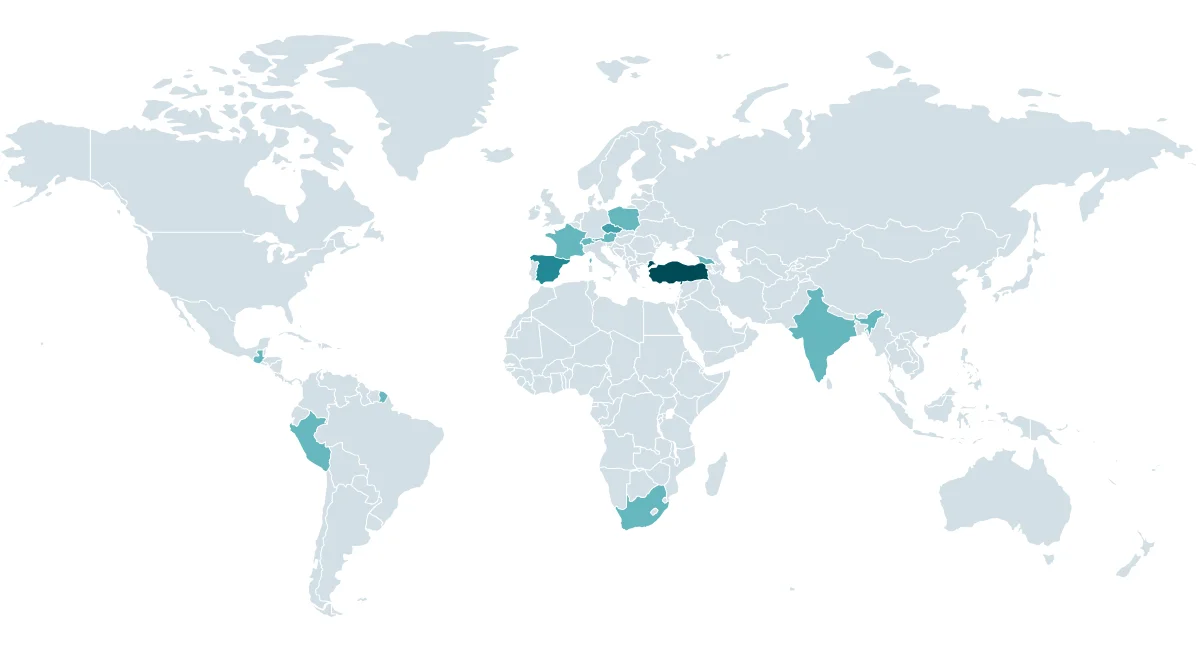
Heatmap of CosmicBeetle attacks since August 2023, according to ESET telemetry (ESET)
CosmicBeetle’s focus on SMBs is influenced by two key factors. Firstly, SMBs are often more likely to rely on vulnerable, outdated software and are less likely to have comprehensive patch management policies, which CosmicBeetle capitalizes on. Secondly, these organizations may not have the resources or expertise to counteract advanced threat actors, making them ideal targets for ransomware campaigns. CosmicBeetle’s consistent attack patterns reveal an intent to exploit vulnerabilities across a wide range of industries with a particular emphasis on sectors handling sensitive data or operationally critical infrastructure, where even temporary disruptions can lead to significant financial losses.
How Do They Operate?
CosmicBeetle’s operational tactics are notably aggressive and persistent, leveraging both brute-force attacks and exploiting well-known vulnerabilities in widely-used systems. The group primarily uses brute-force techniques to gain unauthorized access to target networks, but they also rely heavily on exploiting a set of critical vulnerabilities. According to ESET’s report, these include:
- CVE-2017-0144 (EternalBlue): A highly notorious vulnerability in Microsoft’s SMB protocol, frequently targeted by ransomware groups due to its widespread presence and significant damage potential.
- CVE-2023-27532: Found in Veeam Backup & Replication, this vulnerability allows attackers to exploit backup processes, which SMBs often rely on, and gain control over stored data.
- CVE-2021-42278 and CVE-2021-42287: These are Active Directory (AD) privilege escalation vulnerabilities, commonly known as “noPac,” which allow CosmicBeetle to move laterally within compromised networks, escalating their access privileges for further exploitation.
- CVE-2022-42475 (FortiOS SSL-VPN vulnerability): Used to compromise Virtual Private Networks (VPNs), this flaw lets the group intercept and manipulate network traffic, bypassing security controls that might be in place.
- CVE-2020-1472 (Zerologon): Another privilege escalation flaw that enables attackers to fully compromise Windows domain controllers, often leading to complete system control.
CosmicBeetle has evolved its toolkit over time, with its main ransomware, ScRansom, becoming the centerpiece of its attacks. Originally deploying Scarab ransomware, the group shifted to ScRansom in 2023, which they continually refine. Though ScRansom is not the most sophisticated malware, it has proven to be effective against poorly-secured systems, enabling the group to cause substantial disruption. ScRansom’s design often results in significant data loss; victims attempting to pay for decryption may experience issues due to the ransomware’s need for multiple decryption keys, sometimes leading to irrecoverable data loss. CosmicBeetle’s attempts to impersonate other prominent groups, like LockBit, further add to the confusion for their victims.

NoName Ransomware’s victim posting from 2021
The group also made use of the leaked LockBit Black builder to craft ransomware samples, adopting the visual style and ransom notes of LockBit in an attempt to capitalize on the fear associated with the LockBit name. This tactic included establishing their own LockBit-inspired dedicated leak site (DLS) on the Tor network, named “NONAME,” where they posted victim data. This site mirrored LockBit’s leak site design, down to the Work ID strings in ransom notes, all of which contributed to the perception that these attacks were associated with LockBit. Additionally, CosmicBeetle went as far as registering a domain, lockbitblog[.]info, which closely mimicked LockBit’s official site. This website featured LockBit’s logo and provided ransom notes in Turkish, strengthening the illusion of a connection to the infamous gang. These impersonation tactics highlight CosmicBeetle’s resourceful approach to enhancing the perceived legitimacy and threat level of their operations.
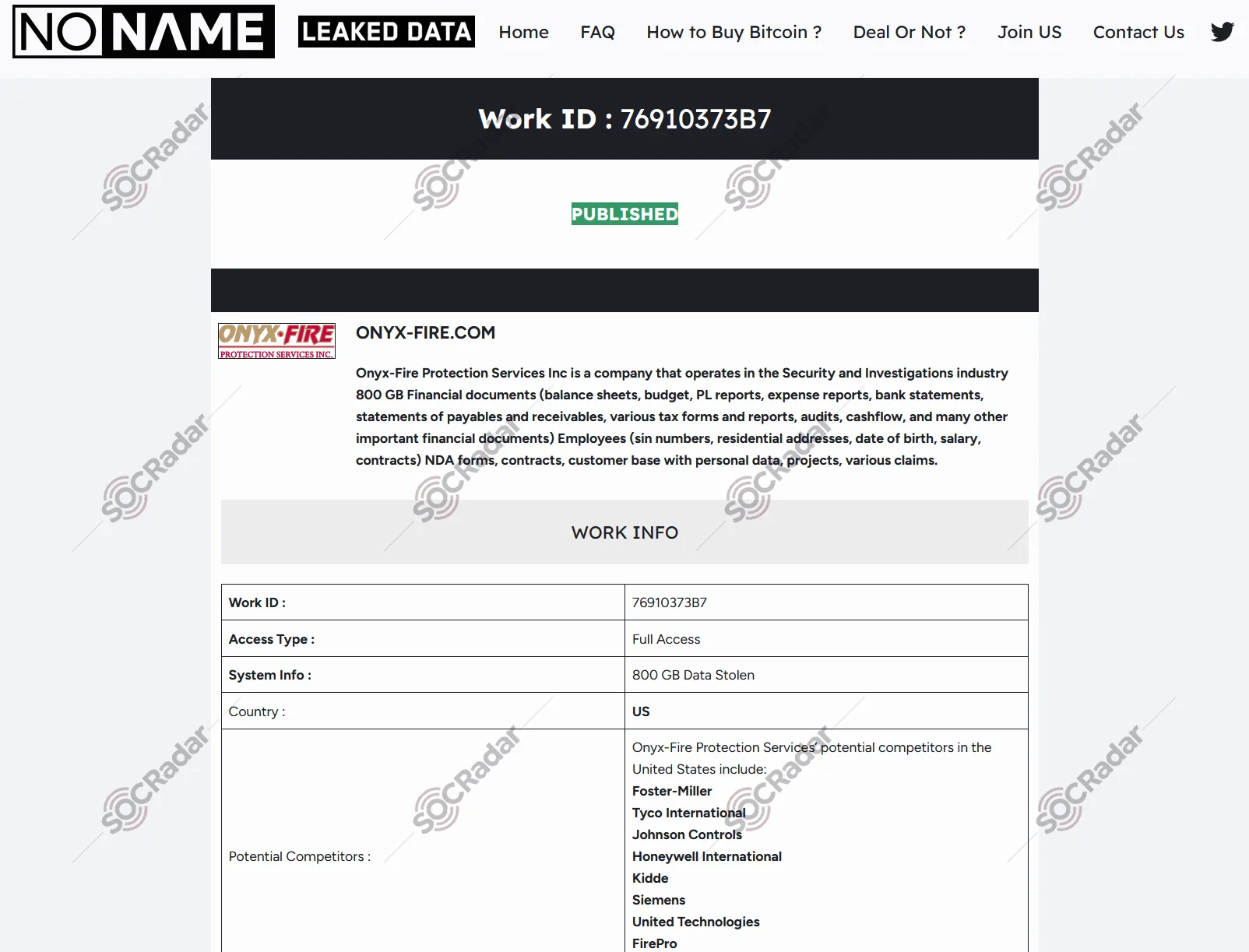
Before the inactivity, a victim’s data allegedly published
In their communications, CosmicBeetle relies on anonymous, peer-to-peer messaging applications, primarily qTox, which uses the encrypted Tox protocol. This protocol is popular among ransomware groups for its robust end-to-end encryption, ensuring secure communication with victims during ransom negotiations. Victims are often warned against seeking assistance from third parties, such as recovery firms, with threatening messages that claim recovery efforts will worsen the damage. This direct communication is designed to instill fear and coerce victims into paying ransom without exploring alternative recovery options.
CosmicBeetle has also recently taken a significant step in their operational structure by aligning themselves with RansomHub, a rapidly growing Ransomware-as-a-Service (RaaS) operation. As an affiliate, CosmicBeetle gains access to additional resources and operational support from RansomHub’s infrastructure. This move reflects their desire to solidify their position within the ransomware ecosystem and extend their reach further. This affiliation not only enhances CosmicBeetle’s operational capabilities but also aligns them with a larger, more experienced network of threat actors, providing additional opportunities to exploit victims on a wider scale.
The CosmicBeetle group, while still immature compared to other established actors, is continually adapting and refining its methods. Their technical shortcomings are often masked by their use of deception, branding, and psychological tactics to extract ransoms from victims. CosmicBeetle’s strategy of mimicking other ransomware groups and aligning with RansomHub suggests a group determined to grow and become a more formidable player in the ransomware space.
How Can You Defend Against CosmicBeetle and Similar Ransomware Attacks?
To defend against ransomware attacks like those executed by CosmicBeetle, organizations must adopt a multi-layered defense strategy that covers all attack stages, from initial access to impact. Below are critical measures to minimize exposure and reduce the risk of ransomware infections:
- Preventing Initial Access:
- Patch Vulnerabilities: Regularly update and patch software, particularly public-facing applications like SSL-VPNs, to close security gaps that attackers could exploit. Utilize automated patch management tools to ensure vulnerabilities are addressed promptly.
- Network Segmentation: Limit lateral movement by segmenting networks. Ransomware typically spreads once initial access is achieved. Isolating sensitive systems and restricting access to critical data can help contain the threat.
- Access Control: Restrict access to public-facing services. Use firewalls, intrusion prevention systems (IPS), and Virtual Private Networks (VPNs) to monitor and control remote access points, reducing the risk of exploitation.
- Credential Protection and Brute Force Prevention:
- Multi-Factor Authentication (MFA): Enforce MFA for all remote access, VPNs, and critical systems. This significantly reduces the effectiveness of brute-force attacks and unauthorized access attempts.
- Password Policies: Implement strong password policies that enforce complexity and regular changes. Use password managers and ensure that passwords are never reused across systems.
- Account Lockout and Monitoring: Set up account lockout mechanisms after a specified number of failed login attempts and implement continuous monitoring for suspicious login attempts, especially over RDP and SMB.
- Malware Execution Prevention:
- Endpoint Detection and Response (EDR): Deploy EDR tools that can detect suspicious behavior, such as the execution of unauthorized scripts (e.g., PowerShell, BAT), or the creation of new accounts. These tools can automatically alert security teams to take action before malware can spread.
- Application Whitelisting: Use application whitelisting to prevent unapproved software, including ransomware executables, from running on the network.
- Behavioral Analysis: Implement tools that analyze the behavior of running processes and identify anomalous activities that could indicate ransomware execution or malware propagation.
- Persistence and Lateral Movement Control:
- Regularly Review User Privileges: Conduct regular audits of user accounts, ensuring that only authorized users have administrative privileges. Enforce the Principle of Least Privilege (PoLP) to minimize potential attack surfaces.
- RDP and SMB Hardening: Disable RDP where not needed and restrict SMB access. For essential systems, require multi-factor authentication for remote access and implement strong password policies.
- Monitor for Unusual Network Traffic: Monitor for abnormal network activity indicative of lateral movement or malware communications. Use a combination of anomaly-based detection systems and network segmentation to block unauthorized connections.
- Mitigating the Impact of Ransomware:
- Data Backup and Recovery: Implement a robust backup strategy, ensuring that critical data is regularly backed up and stored offline. Regularly test backup restoration to ensure that data can be recovered quickly in the event of an attack.
- Network Isolation for Backup Systems: Ensure that backup systems are isolated from the main network to prevent ransomware from encrypting backup data. This helps guarantee the availability of clean backup copies.
- Incident Response Plan: Have an updated incident response (IR) plan specifically for ransomware attacks, detailing the steps to take when an infection occurs. This should include isolating affected systems, notifying stakeholders, and beginning the recovery process.
- Post-Incident Recovery and Forensics:
- Ransomware Decryption Tools: If attacked, immediately check for any available ransomware decryption tools provided by trusted sources such as No More Ransom. Utilize these tools when applicable to restore encrypted files.
- Security Incident Logging: Maintain detailed logs of security incidents for forensic analysis. These logs can provide valuable insights into how the attack occurred, which systems were affected, and how to strengthen defenses going forward.
- Collaborate with Authorities: Report ransomware attacks to relevant authorities and cooperate with law enforcement to track the threat actor. This collaboration can provide insights into ongoing campaigns and help prevent future incidents.
How SOCRadar Can Help in Defending Against Ransomware
SOCRadar’s advanced cybersecurity tools provide critical capabilities to detect, mitigate, and defend against ransomware attacks like CosmicBeetle. Here’s how SOCRadar helps organizations strengthen their defenses:
- Proactive Threat Intelligence:
- SOCRadar’s Threat Intelligence platform offers detailed insights into the latest ransomware Tactics, Techniques, and Procedures (TTPs) used by groups like CosmicBeetle. By continuously tracking threat actor activities, you can stay ahead of emerging threats and adjust your defenses accordingly.
- Dark Web Monitoring and Credential Exposure:
- SOCRadar’s Advanced Dark Web Monitoring tracks the leak of sensitive information, including stolen credentials, malware, and exploits. If CosmicBeetle or similar ransomware groups leak or sell exploit tools or ransomware payloads on the Dark Web, SOCRadar will alert your organization, enabling swift action before an attack can occur.
- Vulnerability Intelligence and Exploit Tracking:
- SOCRadar’s Vulnerability Intelligence service provides real-time updates on newly discovered vulnerabilities, including those used by ransomware groups. This helps you patch and secure your systems before they can be exploited, especially with the fast-moving tactics of groups like CosmicBeetle.
- Ransomware Tracking and Tool Identification:
- SOCRadar’s Ransomware Intelligence module can help identify ransomware variants and their corresponding tools, including any public ransomware builder leaks. This can provide early warnings about ongoing campaigns and help security teams prepare defenses against new strains like CosmicBeetle.
- Real-time Alerts and Reporting:
- Through SOCRadar’s Threat Detection capabilities, organizations receive timely alerts and comprehensive reports on ransomware attacks, including Indicators of Compromise (IoCs), attack paths, and recommended remediation steps.
In Summary
CosmicBeetle is an evolving ransomware group that has established itself in the cybercrime ecosystem. While their methods and techniques are still developing, the group’s growing capabilities—especially their use of Ransomware-as-a-Service (RaaS) through affiliations with networks like RansomHub—suggest that they will continue to expand their operations. They tend to focus on SMBs that are more vulnerable to ransomware attacks, using a combination of exploits, brute-force methods, and psychological tactics to extort victims.
Their shift towards more complex, multi-stage attacks that combine encryption with data theft indicates that they are aware of the value in both quick payouts and long-term reputational damage. The group’s success in mimicking more established ransomware actors like LockBit highlights their desire to appear as a high-level threat, despite still being a relatively lesser-known player.
CosmicBeetle’s future actions will likely depend on how quickly they can refine their tactics and grow their capabilities. With continued exploitation of vulnerabilities and evolving ransom tactics, CosmicBeetle may well become a significant threat to businesses worldwide. By understanding their patterns and TTPs, organizations can better prepare for and defend against the potential impact of this and other similar threat actors.
What Are Their MITRE ATT&CK Techniques?
MITRE ATT&CK techniques by ESET:
| Tactic | ID | Name | Description |
| Reconnaissance | T1595.002 | Active Scanning: Vulnerability Scanning | CosmicBeetle scans its targets for a list of vulnerabilities it can exploit. |
| T1590.005 | Gather Victim Network Information: IP Addresses | CosmicBeetle scans the internet for IP addresses vulnerable to the vulnerabilities it can exploit. | |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains | CosmicBeetle registered its own leak site domain. |
| T1587.001 | Develop Capabilities: Malware | CosmicBeetle develops its custom toolset, Spacecolon. | |
| T1588.002 | Obtain Capabilities: Tool | CosmicBeetle utilizes a large variety of third-party tools and scripts. | |
| T1588.005 | Obtain Capabilities: Exploits | CosmicBeetle utilizes publicly available PoCs for known exploits. | |
| T1588.001 | Obtain Capabilities: Malware | CosmicBeetle probably obtained ransomware from RansomHub and the leaked LockBit 3.0 builder. | |
| Initial Access | T1190 | Exploit Public-Facing Application | CosmicBeetle gains initial access by exploiting vulnerabilities in FortiOS SSL-VPN and other public-facing applications. |
| Execution | T1204 | User Execution | CosmicBeetle relies on user execution for some of its tools, though this is usually done by the threat actor via RDP. |
| T1059.003 | Command and Scripting Interpreter: Windows Command Shell | CosmicBeetle executes various BAT scripts and commands. | |
| T1059.001 | Command and Scripting Interpreter: PowerShell | CosmicBeetle executes various PowerShell scripts and commands. | |
| Persistence | T1136.001 | Create Account: Local Account | CosmicBeetle often creates an attacker-controlled administrator account. |
| Defense Evasion | T1078 | Valid Accounts | CosmicBeetle abuses valid accounts whose credentials it successfully obtains. |
| T1140 | Deobfuscate/Decode Files or Information | ScRansom samples protect public RSA keys by encryption. | |
| Credential Access | T1110.001 | Brute Force: Password Guessing | CosmicBeetle utilizes RDP and SMB brute-force attacks. |
| T1212 | Exploitation for Credential Access | CosmicBeetle exploits known vulnerabilities to obtain credentials. | |
| Impact | T1485 | Data Destruction | CosmicBeetle renders some encrypted files unrecoverable. |
| T1486 | Data Encrypted for Impact | CosmicBeetle encrypts sensitive files on compromised machines. |
For the latest IoCs, remember to visit SOCRadar platform.





































