
Dark Web Profile: Lapsus$ Extortion Group
[Update] August 11, 2023: The Cyber Safety Review Board (CSRB) published a review of the Lapsus$ extortion group’s attacks. Read more under: “A Review of Lapsus$ by CSRB.”
The Lapsus$ group, which started its activities a short time ago, managed to attract the whole world’s attention. With their high-profile target and unconventional tactics and methods, are we just facing a “new player in the game” or “a game-changer”?
Who is Lapsus$
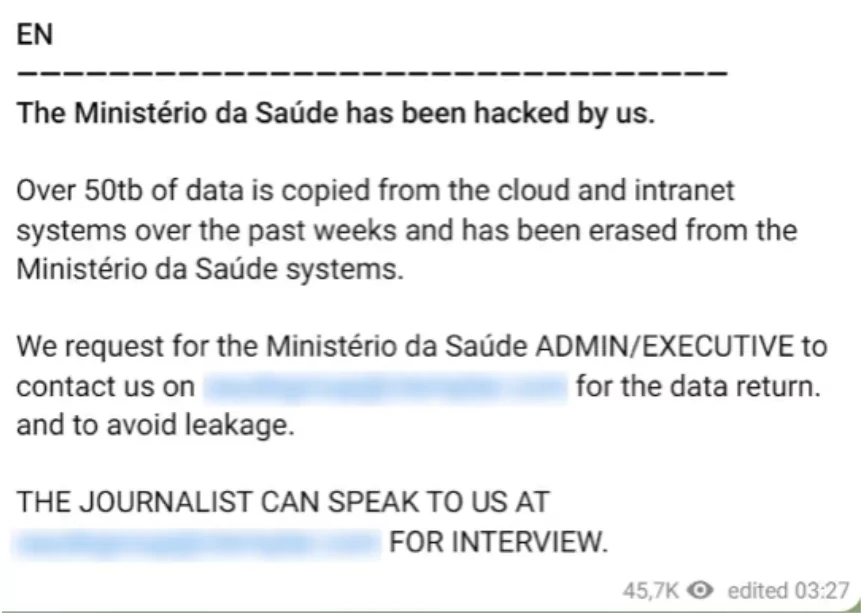
They announced they had attacked the Brazilian Ministry of Health and deleted 50 terabytes of data from the Ministry’s systems after copying it with a message they published on their Telegram channel in December 2021. The group later turned to CORREIOS, which operates Brazil’s national postal services, and Claro, a Brazilian-based Mexican Telecommunications company.
In early 2022, they advertised that they had attacked Impresa, a major media company in Portugal. Finally, they launched successive attacks against the giant companies, which turned all eyes on them. The attacks started with NVIDIA and were followed by Samsung, Ubisoft, Microsoft, and lastly, Okta in a few weeks.
They announced that they hacked NVIDIA by publishing 20 GB of data on torrent. In response to the data they obtained, they requested NVIDIA to remove the LHR (Lite Hash Rate) feature, limiting the use of graphics cards in mining. The LHR feature was a restriction added by NVIDIA to solve the stock problem that arose in graphics cards with the popularity of Crypto mining.
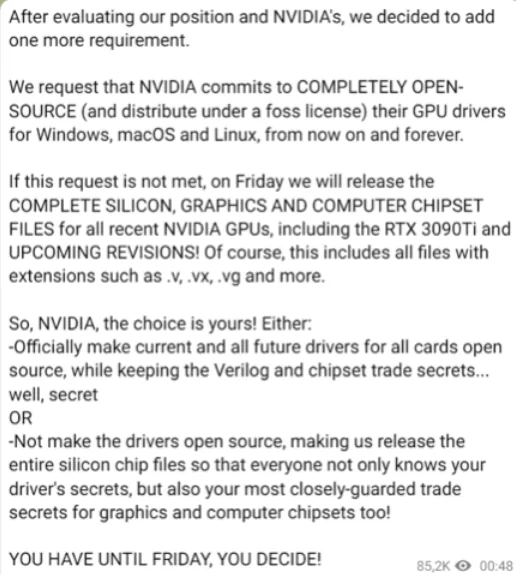
Not content with that, Lapsus$ demanded that NVIDIA commit to fully open-source its Graphics Processing Unit (GPU) drivers for Windows, Mac, and Linux operating systems, or they threatened to release trade secrets for all NVIDIA GPUs.
On March 1, NVIDIA confirmed that they had been hacked, resulting in the theft of 1 terabyte of data. These attacks caused NVIDIA’s services to stop for two days.
At the same time as the NVIDIA case, Samsung was also the target of this group. The group shared the company’s critical data (190GB), such as the biometric unlock technique and the company’s other proprietary and confidential codes. The leaked data includes even the source codes of Qualcomm, one of Samsung’s suppliers.
Samsung confirmed the incident on March 7, stating that their customers‘ data was not compromised and the company’s operations would not be interrupted.
Meanwhile, to gain access to the business network, Lapsus$ has announced that they are trying to hire insiders from their targets, such as telecommunications, software, gaming industries, and technology companies.
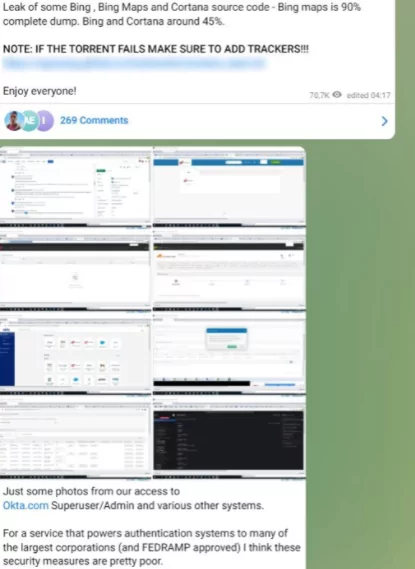
Later, the Lapsus$ group announced Microsoft was their next victim. On Monday night, March 21, source codes of Microsoft’s search engine (Bing), Bing Map, and Cortana Virtual Assistant services were posted on Lapsus$’s Telegram channel.
The Key to Major Companies: Okta
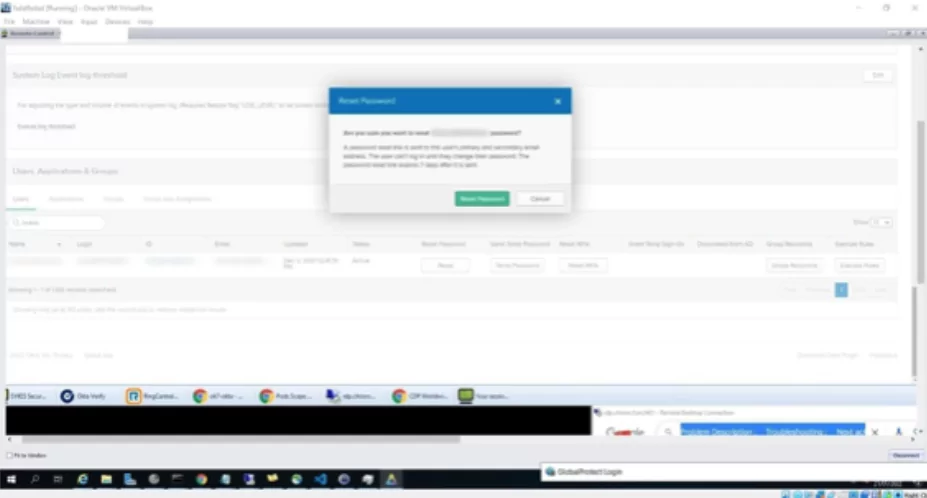
On March 21, The Lapsus$ Group has also announced they had breached Okta, an Identity and Access Management company with more than 15.000 customers worldwide. Lapsus$ has shared screenshots of Okta’s internal software, revealing that they have gained full control over administrator accounts of the company. Inside Okta’s internal network, the group could perform actions requiring admin privilege, such as password reset.
From the screenshots, we have seen that the dates go back as early as January 21, 2022. We can say Lapsus$ has been lurking inside Okta’s network for quite some time.
The group has announced the Okta breach on their Telegram channel just after they have shared Microsoft Bing’s and Cortana’s source code on the same channel. SOCRadar’s analysts think the Microsoft hack may be related to the Okta breach.
Below, you can see two posts (Microsoft leaks and Okta hack announcement) taken from the group’s Telegram channel. Lapsus$ states that they have gained access to management systems and superuser accounts of Okta. They also state that Okta’s security measures were really poor.
A day after the announcement of the hack, Okta confirmed the breach and stated only a small portion of their customers, approximately %2.5, were affected. This might seem like a small percentage, but when we calculate the numbers, the number of affected companies is 366.
The fact that 366 major companies (possibly including Microsoft) have suffered a data exfiltration attack we do not know the scale of is big news and could potentially lead to more leaks and cyberattacks by The Lapsus$ Group.
Lapsus$’s Response to Okta
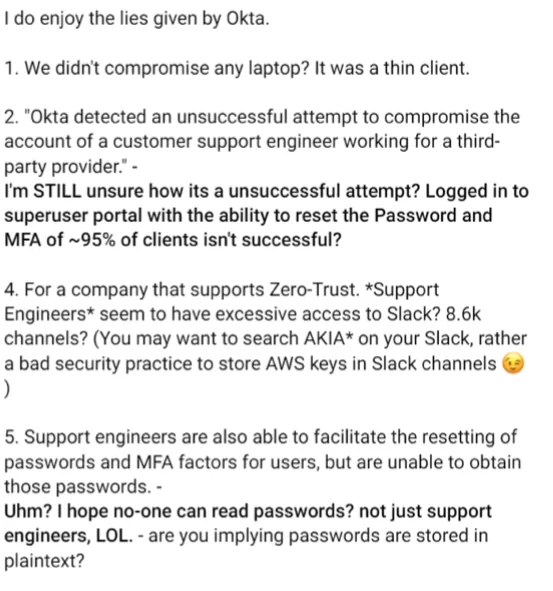
The Lapsus$ Group was not happy with Okta’s statement confirming the breach. On the same day after Okta’s statement, the group posted a lengthy message on their Telegram channel titled “I do enjoy the lies given by Okta.” The message mainly pointed out several poor security practices carried out by Okta in the message.
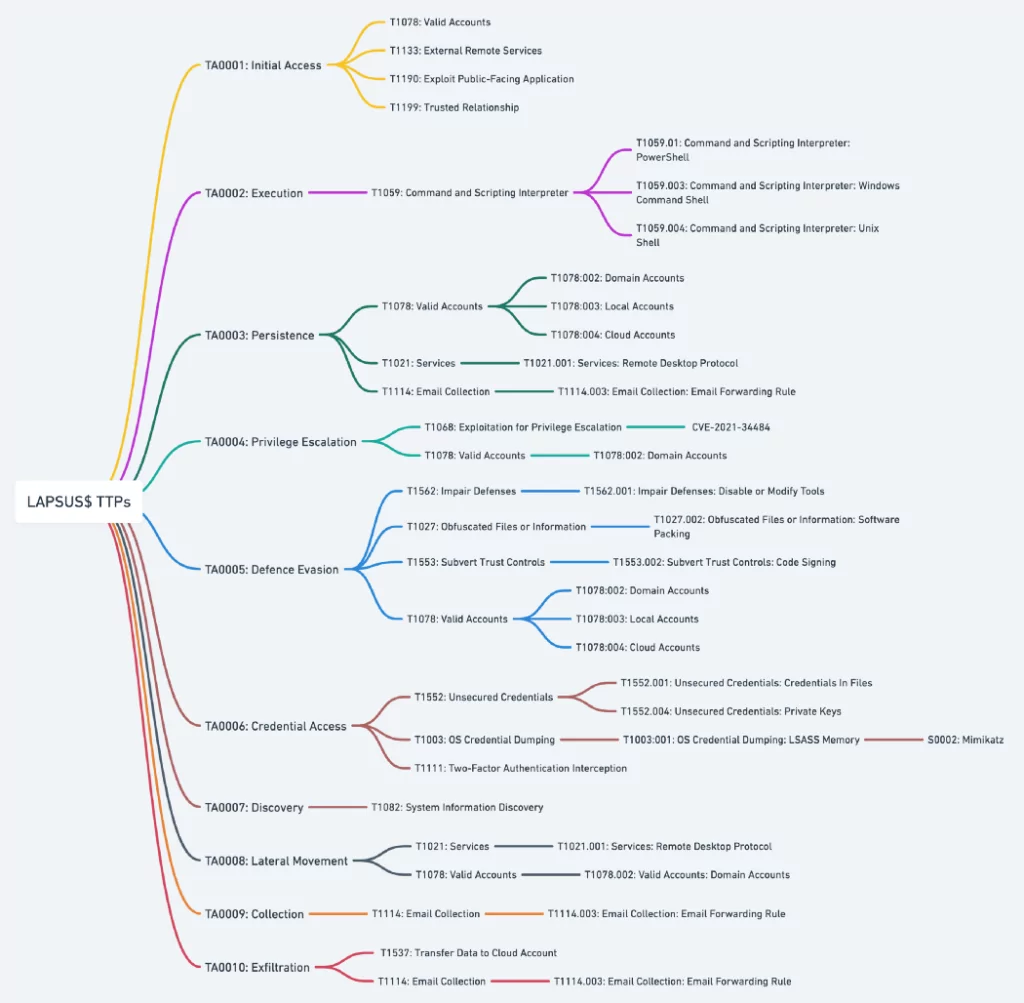
TTPs of Lapsus$
According to Microsoft’s detailed analysis, the Lapsus$ group (named DEV-0537 by Microsoft) used the following tactics to gain first access to the system:
- Phone-based social engineering
- SIM swapping
- Access personal e-mails of employees in target organizations
- Access to credentials
- Paying employees or business partners of target organizations for multi-factor authentication (MFA) approval
- Breaking into ongoing crisis communication calls
The real motivation of Lapsus$ is not known. However, Microsoft mentions that the Lapsus$ is a cybercrime group that aims to theft and destruction.
Although they may seem like a ransomware group when they started their activities, it is difficult to call whether they are a ransomware group. There is no indication that the victim system has been encrypted by ransomware. They threaten to share the stolen data online if their demands are not met.
One of the most critical questions in the upcoming period will be which measures to take against a cybercrime organization that does not try to cover its tracks, announces its attacks on social media, conducts surveys to determine its next leak, and publishes advertisements to buy initial access brokers.
A Review of Lapsus$ by CSRB
The Cyber Safety Review Board (CSRB) released a report in late July 2023, presenting a comprehensive review of the Lapsus$ extortion group’s attacks. Collaborating with over 30 entities, including companies, cybersecurity firms, law enforcement, researchers, and academics, the report delves into the cyberattacks that transpired between late 2021 and late 2022.
Lapsus$, along with related threat groups, targeted global entities using basic yet effective methods, exploiting vulnerabilities in the digital landscape. All of the vulnerabilities observed in use by threat actors were known and patched, and did not include zero-day vulnerabilities.
According to the report, successful tactics used by the group were initial access brokers and info-stealer malware. Considering these tactics, the report underscores the need for improved security measures and highlights the insufficiency of traditional multi-factor authentication (MFA). Traditional MFA requires authentication via a password and a one-time code obtained from another service such as SMS or email. Nonetheless, certain cyber attacks frequently bypass this type of MFA.
Additionally, the report emphasizes the importance of considering third-party risks and commends organizations with strong defenses, token-based MFA, and robust incident response protocols. It also sheds light on the challenges faced by law enforcement due to funding shortages and underreporting of cyber threats.
To access the full insights and findings, refer to the report.
Detect Threats with SOCRadar Before They Happen
Don’t miss the ever-evolving and changing TTPs of threat actors and APT groups with SOCRadar’s Extended Threat Intelligence. Regularly monitor for suspicious activity on the surface, deep and dark web to stay one step ahead.
Be aware of all your internet-facing assets with the automatic inventory extraction function and create a strong protective shield for your cyber security with in-depth and contextual intelligence.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.


































