
Increasing Cyberattacks Targeting the Gaming Industry in 2022
By SOCRadar Research
The gaming industry has recently emerged as a preferred target for cyberattacks. The industry is constantly growing, with new platforms and products appearing daily. Changes in the social structure and globally unexpected circumstances like the COVID-19 pandemic have contributed to the gaming industry’s recent growth. According to Newzoo’s Global Games Market Report, nearly 3.09 billion people spent $203.1 billion on games in 2022.
The transition to cloud systems has impacted the growth of the gaming industry. Many gaming companies implemented cloud-based game infrastructures. Based on the Brandessence market research, the Cloud Gaming market size reached $609.67 million in 2021 and is likely to grow to $7.382 billion by the end of 2028. With cloud systems, users can play virtually anywhere without device limitations or needing the latest hardware. Additionally, as mobile gaming has expanded rapidly, the flexibility and mobility of users have increased, resulting in more games being played on more devices.
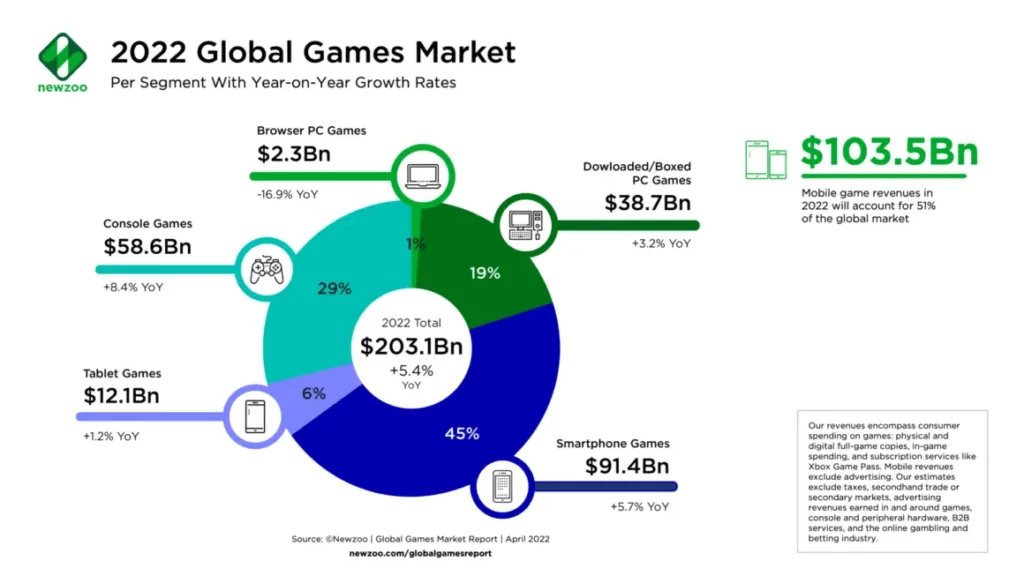
More devices and users mean a larger attack surface. The gaming industry has a huge user base, so many potential victims and sensitive data exist. When the financial dimension of the gaming industry is included, the scope of attacks and targets in the gaming sector has reached extraordinary levels.
Why Cybercriminals Targeting Gaming Industry
Two main targets for cyber attackers in the gaming industry are gamers and gaming corporations.
Gaming Corporations:
Threat actors choose game developers and supporting companies creating software and hardware as targets. Threat actors attempt to steal source codes, development kits, or sensitive personal data of users and staff data of gaming firms.
As a result of the attacks, interruptions in the games’ online services and network infrastructure cause both financial and reputational losses for the companies and weaken the users’ loyalty. The leak of personal data from their systems also subjects companies to the obligation of many legal regulations such as GDPR (General Data Protection Regulation) and financial penalties.
Gamers:
Threat actors target players for their data, account, and virtual money or goods. Data collected from players contains credentials, credit card information, profile data such as game success, rank in games, messages, contacts list, etc. For gamers, progressing in a game is time-consuming and challenging. Threat actors can steal a player’s account to obtain a gaming experience. The account can be renamed and sold.
In-game microtransactions are a significant financial item in the gaming industry. Players can generously purchase in-game tools, character skins, and character upgrades using virtual money and swap real money for virtual items. According to a report by Business Research Company, the online microtransaction market will be worth $106.02 billion by 2026, with a compound annual growth rate of 11.9%. Many players’ payment methods are linked to player accounts due to microtransactions, making the accounts a target for attackers seeking payment information.
What are the Attack Vectors?
DDoS (Distributed Denial of Service) assaults, which consume resources extremely, also pose a risk to players and gaming firms. DDOS attacks, intended to slow down or terminate services significantly, have the most significant effect on the gaming industry. According to Akamai’s ‘Gaming Respawned’ report, DDoS attacks targeting the gaming industry cover 37% of all DDoS attacks.
Malware is one method used to steal the information of gamers. Users who prefer third-party sellers over official vendors and download games from untrusted sites may download malware designed to steal their personal data. Attackers frequently use well-known games with fans or newly released games to spread malware. Players sometimes utilize cheat codes to obtain an advantage in the game. Cybercriminals can use such fake cheat software to distribute malware to steal players’ data.
Ransomware attacks can potentially disrupt the gaming industry as in all verticals. Ransomware attackers especially focus on demanding ransom by disrupting gaming systems and threatening to reveal users’ sensitive information and/or game source codes, using the double extortion method.
Phishing with social engineering techniques is another approach utilized by attackers. Threat actors may gain gamers’ trust by chatting with them through in-game conversations or other social networking platforms and convince participants to share sensitive data.
However, attackers can gain access to the credentials by phishing websites requesting players to submit user account details. For example, webpages that duplicate the user interfaces of well-known in-game retailers or websites that offer fake giveaways to win in-game currency or items.
Another weakness exploited by attackers for account takeover is the habit of most users logging in with the same passwords across several platforms and choosing predictable passwords. Thus, credential stuffing allows attackers to get access to user accounts.
Cyberattacks Targeting Gaming Industry in 2022
The following are some of the notable cyberattacks that hit the gaming industry in 2022:
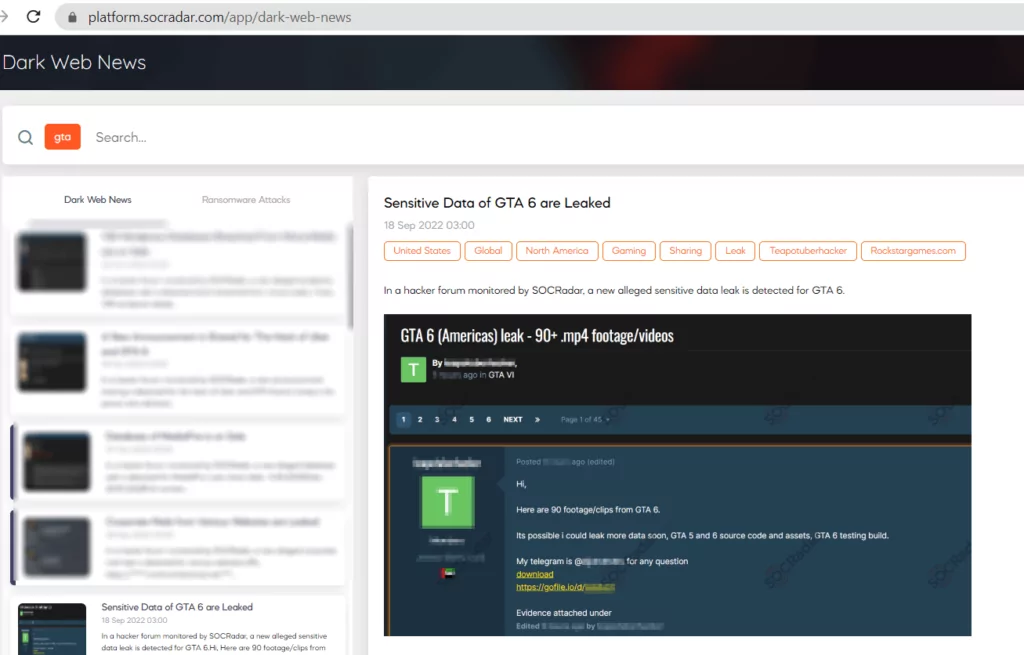
Rockstar Attack: On September 18, 3GB of video footage from the Rockstar Games company’s GTA6 edition of the ‘Grand Theft Auto series, which has yet to be released, was shared on the GTAForum by a user nicknamed ‘Teapoyuberhacher.’ The attackers claimed to have stolen the complete source code for GTA5 and the early GTA6 source code. The attackers claimed that the videos were from an attack on Rockstar employees’ slack channel. The leak was confirmed by Rockstar, stating that an unauthorized third party illegally accessed confidential data from their system.
2K Games Attack: 2K Games, which the same parent company owns as Rockstar Games, was attacked the same week as Rockstar. The attackers gained access to the company’s helpdesk platform and sent malware-infected emails to users. 2K Games has disabled its support portal. It has been verified that the attackers accessed their systems by acquiring unauthorized access to one of the vendors’ credentials.
Roblox Attack: With over 37 million players, Roblox is one of the world’s largest gaming platforms, allowing users to create their games in the company’s universe. In July, security researchers discovered that 4GB of Roblox company data had been exposed. Data obtained from a Roblox employee through social engineering contains emails, spreadsheets on several games, and personal information of other Roblox employees and content creators. Unidentified attackers posted some of this data on the dark web. Roblox confirmed that the stolen documents were taken illegally as part of an extortion attempt in which they declined to participate.
Bandai Namco Attack: Bandai Namco, the publisher of popular games such as Tekken and Elden Ring, announced in July that they had been attacked. The ransomware group ALPHV, also known as BlackCat, released Bandai Namco’s name on its dark web blog on July 11. Bandai Namco announced on July 13 that they were the victim of a cyberattack on July 3 that may have resulted in losing their customers’ personal information.
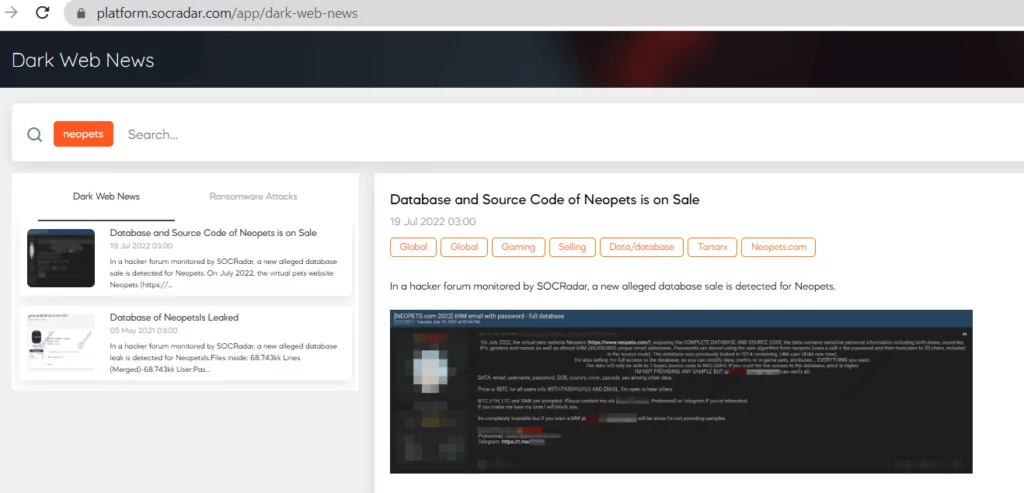
Neopets Attack: In July, 69 million Neopets member registrations and source codes were listed for sale for 4BTC. The Neopets company confirmed that IT systems were compromised from January 2021 to July 2022, exposing 69 million user accounts and source code. Users’ names, email addresses, usernames, birth dates, gender, IP addresses, Neopets PINs, and hashed passwords, as well as data generated during the game, were all compromised.
NVIDIA Attack: In 2022, the Lapsus$ group drew attention with a series of attacks against several technology giants, including the graphic card manufacturer NVIDIA. Lapsus$ claimed that they had stolen 1TB of data from NVIDIA systems. In response to the data, they asked NVIDIA to open-source GPU drivers entirely and remove all restrictions on cryptocurrency miners.
On February 23, NVIDIA confirmed that they had detected a cyberattack and that employee credentials and NDVIA confidential data had been stolen from their systems.
Considering the SOCRadar XTI platform database, 382 dark web posts related to the gaming industry have been reported by dark web analysts in 2022. The most active threat actor is ‘Flowercower.‘ According to the SOCRadar research team’s analysis, the distribution of cyberattacks in the gaming industry in 2022 by countries is as follows.
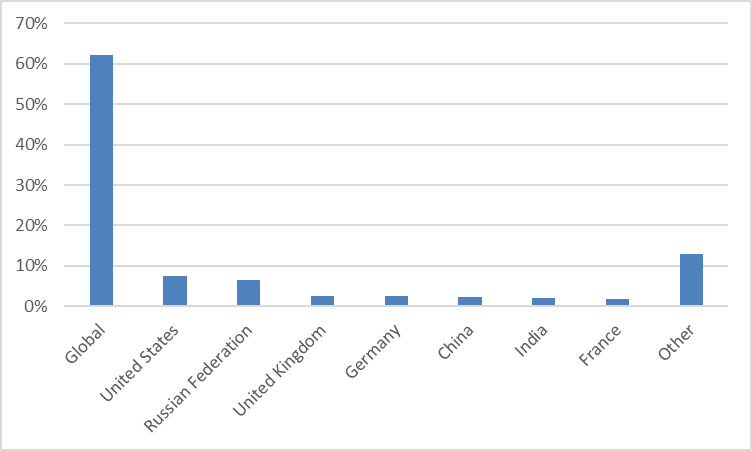
(Source: SOCRadar XTI Platform)
More than half of the attacks (62%) affect global users. Such an outcome is consistent with the geographically boundless nature of the gaming industry.
Conclusion
For a more secure gaming experience, the two main components of the gaming industry should take the necessary precautions. In this context, the players should;
- Be careful when interacting with other players via in-game chat or other applications.
- Avoid using game account usernames and passwords on other platforms. They should be suspicious of emails or websites that request their passwords.
- Avoid downloading games from untrusted sources.
- Avoid using weak or repetitive passwords.
- Use VPN (Virtual Private Network) for a more private connection.
On the other hand, game developers are responsible for the security of their systems and the gamers. Many users are young kids who still need to develop cybersecurity awareness. Also, many users who play games just to have fun, relax and experience the competition do not have severe security concerns. So, game developers must compensate for the customers’ lack of security awareness and invest in appropriate security solutions.
As seen in the cyberattacks in 2022, the starting point of many attacks is the capture of employee information through social engineering. As a result, organizations must train their employees on phishing and other cybersecurity threats effectively. Besides, firms need to be sensitive about employee credential leaks. Companies can benefit from cyber threat intelligence gathered from the surface web and dark web about leaked credentials and attackers targeting the industry by utilizing Extended Threat Intelligence (XTI) products and can take proactive actions.



































