
NIST Cybersecurity Framework 2.0: What You Need to Know
In a previous SOCRadar blog post, we delved into the importance of cybersecurity frameworks for today’s organizations. In this installment, we pivot our focus toward the much-anticipated NIST Cybersecurity Framework 2.0.
As cyber threats evolve, so must our strategies to counter them. The introduction of NIST Cybersecurity Framework 2.0 marks a milestone in this evolution, offering organizations an enhanced, comprehensive approach to managing and mitigating risks.

The NIST Cybersecurity Framework 2.0 presents a revamped approach to cybersecurity, addressing modern complexities while encouraging community participation for its ongoing development. SOCRadar’s dynamic solutions offer seamless alignment with the principles outlined in this updated framework, making it an essential partner in upgrading your cybersecurity strategy.
Overview of the NIST Cybersecurity Framework (CSF)
The NIST CSF is a voluntary framework primarily intended for critical infrastructure sectors to manage and mitigate cybersecurity risk based on existing standards, guidelines, and practices. The Framework consists of three primary components: the Framework Core, Tiers, and Profiles. For a detailed understanding of these components, you can refer to our previous SOCRadar blog.
Why Version 2.0 of NIST Cybersecurity Framework is Needed
Why fix something that is not broken? Simply put, the digital landscape is in a constant state of flux, riddled with new challenges and complexities. The original CSF was a robust starting point, but it could not foresee every future development. Issues such as zero-trust architecture, artificial intelligence, and IoT security have grown in importance and complexity, necessitating a revision in the framework.
Main Differences Between Version 1.1 and 2.0
The second iteration of the CSF is not merely an update; it is an evolution. It introduces new best practices and methodologies adapted for the modern digital ecosystem. While preserving the original components, CSF 2.0 extends its reach to include guidelines on artificial intelligence risk management, zero-trust architecture, and more, thus making the framework even more versatile and comprehensive than before.
The “Govern” Function: A Significant Addendum
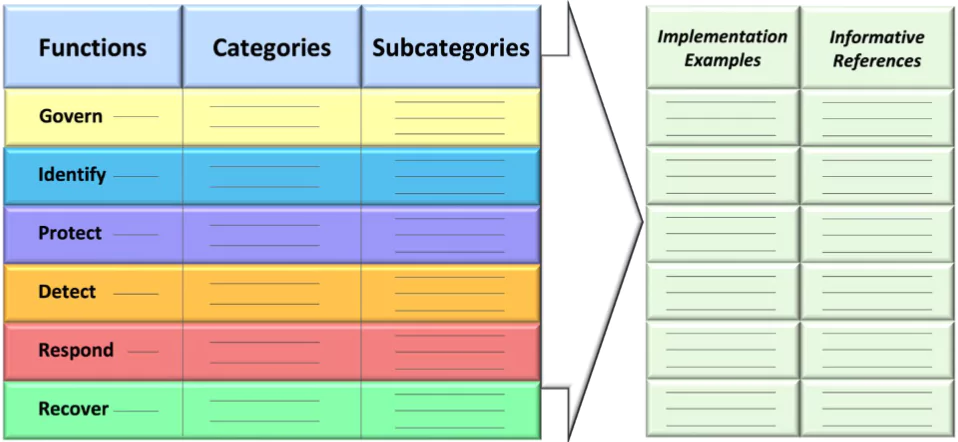
A notable addition to the NIST CSF 2.0 is the introduction of a sixth function named “Govern.” This extra layer augments the previous five – Identify, Protect, Detect, Respond, and Recover – by emphasizing the importance of governance in cybersecurity. Governance is not just a top-down approach from management; it encapsulates a range of strategies that involve both internal and external stakeholders.
By including “Govern,” the Framework encourages organizations to adopt a more holistic view of cybersecurity that goes beyond technical measures.
Expansion of Supply Chain Risk Management
One of the most significant updates is the expanded focus on supply chain risk management. While version 1.1 did touch upon supply chain risks, version 2.0 goes further to elaborate on best practices and provides more comprehensive guidelines for managing these risks effectively.
Alignment with Other Frameworks and Standards
While CSF 1.1 was compatible with other frameworks, the 2.0 version makes a concerted effort to provide more explicit guidance on how it can be used in conjunction with other cybersecurity frameworks and sector-specific frameworks.
By addressing these critical areas, NIST CSF 2.0 takes a holistic approach, aiming to cover every base, ensuring that organizations have a multi-faceted, robust mechanism to secure their digital landscapes.
Emphasis on Global Applicability
The CSF is not just a U.S.-centric initiative anymore. Its guidelines have been translated and adapted globally, and this trend is likely to continue with the 2.0 version. The international community’s involvement is crucial for crafting a framework that addresses the diverse challenges faced by organizations worldwide.
Version 2.0 represents a move toward a more internationally applicable framework, broadening its scope to include organizations around the globe for greater adaptability across different regions and industries.
Enhanced Metrics and Measures
The new version introduces an improved way to measure cybersecurity postures effectively. It enables organizations to develop specific metrics tied to desired outcomes, making it easier to track cybersecurity performance over time.
Strategic Objectives and Tactical Milestones
The update introduces a new “Implementation Guidance,” which includes strategic objectives and tactical milestones that organizations can follow. This guidance makes it easier for organizations to understand the process for achieving specific cybersecurity goals, thus making the framework more actionable.
How NIST Cybersecurity Framework 2.0’s “Govern” Function Aligns with ISO 27001 Principles
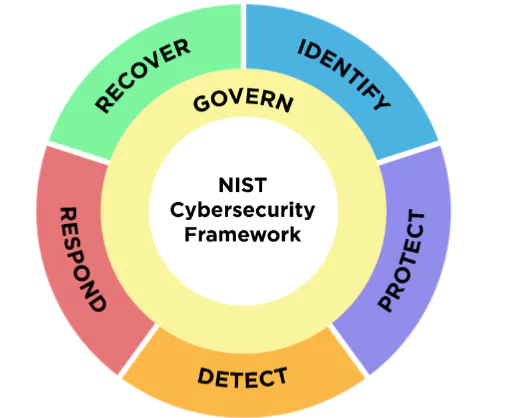
The introduction of the “Govern” function in the NIST Cybersecurity Framework (CSF) 2.0 marks a significant step towards incorporating more exhaustive governance mechanisms into cybersecurity management. Interestingly, this new addition aligns the NIST framework more closely with ISO 27001, a globally recognized standard for Information Security Management Systems (ISMS).
Key Points of Convergence:
- Risk Management Strategy: Both ISO 27001 and the new “Govern” function in NIST CSF 2.0 stress the necessity for a well-defined risk management strategy. ISO 27001 mandates a methodical approach to securing sensitive company information, aimed at guaranteeing its confidentiality, integrity, and availability. Similarly, the “Govern” function lays emphasis on understanding the organizational context, outlining the risk management strategy, and clearly defining roles and responsibilities. This shared focus on risk management brings CSF 2.0 into closer alignment with the governance stipulations of ISO 27001.
- Roles, Responsibilities, and Authorities: The need for clearly demarcated roles and responsibilities is a governance principle common to both ISO 27001 and CSF 2.0’s “Govern” function. In the context of ISO 27001, it’s a prerequisite for establishing and maintaining an effective ISMS. With its new “Govern” function, NIST CSF 2.0 is similarly designed to ensure that everyone in the organization understands their cybersecurity roles, responsibilities, and authorities.
- Policy, Processes, and Procedures: Both frameworks advocate for the establishment of robust policies, processes, and procedures. ISO 27001 necessitates the formulation of an ISMS policy, objectives, and accompanying processes and procedures. NIST CSF 2.0 complements this by delving into the policies, processes, and procedures that organizations should have in place for effective cybersecurity risk management.
- Oversight and Monitoring: ISO 27001 is stringent about the ongoing evaluation of the ISMS, requiring regular internal audits and management reviews. The “Govern” function in CSF 2.0 resonates with this ethos by accentuating the need for oversight in the governance process.
- Supply Chain Risk Management: Another area of compatibility between the two frameworks is the emphasis on managing supply chain risks. ISO 27001’s Supplier Relationship clauses and the “Govern” function’s focus on cybersecurity supply chain risk management both advocate for a strategic approach to managing risks related to vendors and third-party services.
- Continuous Improvement: Last but not least, both ISO 27001 and NIST CSF 2.0 prioritize the principle of continual improvement. Whether it is through internal audits and management reviews as per ISO 27001 or the “Govern” function’s emphasis on continual advancement, the core philosophy remains the same: never stop refining your cybersecurity posture.
In a nutshell, the “Govern” function in NIST CSF 2.0 augments the framework’s governance capabilities, making it more synergistic with the tenets of ISO 27001. Organizations adhering to ISO 27001 will likely find the transition to the updated NIST CSF 2.0 to be more seamless, and vice versa. This enhanced compatibility benefits organizations by providing a more holistic approach to cybersecurity governance.
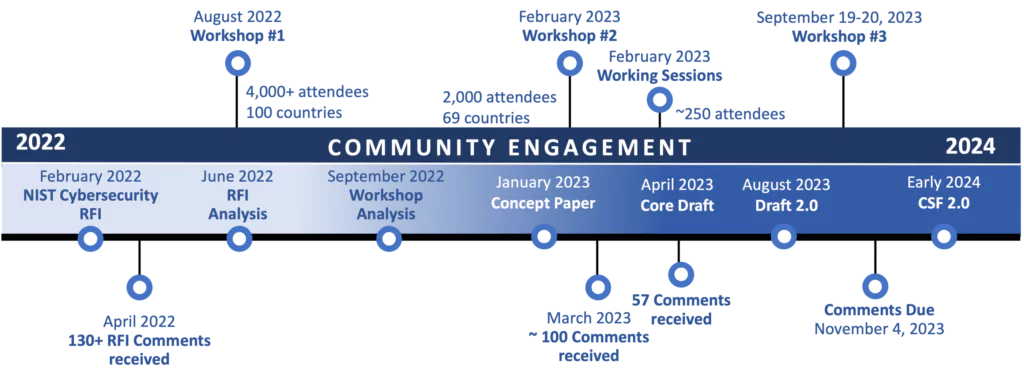
Engaging with the NIST Cybersecurity Framework 2.0 Update Process
The Cybersecurity Framework 2.0 is being designed with substantial input from stakeholders. NIST has rolled out multiple avenues for stakeholders to be part of this evolutionary process. Whether it is submitting comments, participating in workshops, or even joining international efforts, there are various ways for organizations and experts to contribute their insights and feedback.
You could:
- Visit the NIST CSF 2.0 update page for the latest updates and events.
- Participate in upcoming workshops to discuss proposed updates.
- Provide comments through Request for Information or on the public draft.
- Your input is invaluable in making CSF 2.0 a success.
How SOCRadar Can Complement Your CSF Strategy
As we move towards a more intricate cybersecurity landscape, it is crucial for organizations to align themselves with the evolving best practices outlined in CSF 2.0. This is where SOCRadar comes in. Our platform offers a plethora of tools, from attack surface management to vulnerability management, and threat intelligence designed to aid in your compliance with the NIST framework. Our real-time analytics and comprehensive risk assessments are perfectly aligned with the objectives of the updated CSF, making SOCRadar an ideal partner in your cybersecurity journey.
Conclusion
In a rapidly changing digital environment, complacency is not an option. The NIST Cybersecurity Framework 2.0 provides organizations with a more dynamic, comprehensive approach to cybersecurity risk management. Community involvement and international collaboration enrich this tool further, making it adaptable and relevant for the challenges that lie ahead.
The NIST Cybersecurity Framework 2.0 also offers an updated and comprehensive approach to managing cybersecurity risks. It brings new perspectives and methodologies tailored for today’s complex digital world. It is not just an American standard but a global one, enriched through international collaboration and widespread community engagement. As your organization considers the transition to this updated framework, remember that SOCRadar is here to facilitate each step, helping you establish a robust and adaptable cybersecurity posture for the modern age.



































