
Phishing in 2024: 4,151% Increase Since Launch of ChatGPT; AI Mitigation Methods
Phishing remains a major threat in cybersecurity, with attacks growing more frequent and sophisticated each year. In 2024, we have seen an alarming 856% increase in malicious emails, illustrating the scale and severity of the problem.

Phishing in 2024 – an illustration by DALL-E
The dramatic rise in phishing in 2024 is fueled by technological advancements, with cybercriminals using tools like generative AI to create convincing phishing emails and malicious code. These tools allow attackers to automate and refine their tactics, making it easier to deceive their targets. As a result, phishing has become a more formidable challenge for both individuals and organizations.
This blog post explores the trends of phishing in 2024, emphasizing the dual role of AI in both enabling and combating these threats. Importantly, we will explore how organizations can leverage AI-driven solutions to identify and block phishing attempts effectively.
Understanding the landscape of phishing in 2024 is essential for developing effective defense strategies. By examining the latest tactics used by cybercriminals and the advanced tools available for detection and prevention, we aim to provide valuable insights for enhancing your cybersecurity posture against phishing threats.
Modern Phishing Attacks and the Latest Tactics
Phishing in 2024 has become more advanced, with new techniques and tools making these attacks increasingly sophisticated and difficult to detect. Understanding the mindset behind phishing campaigns is important for developing effective defenses.
Phishing campaigns exploit human psychology to trick individuals into revealing sensitive information. Cybercriminals use tactics like urgency, fear, curiosity, and trust to manipulate their targets. For example, an email pretending to be from a bank might warn of unauthorized account access, prompting the recipient to click on a malicious link out of fear of losing money.
The motivations behind phishing campaigns range from financial gain to corporate espionage and political manipulation. By understanding these psychological tactics, organizations can better train their employees to recognize and resist phishing attempts.
For more information in this context, check out our blog post: “The Mindset Behind Phishing Campaigns.”
As mentioned earlier, there has been an 856% increase in malicious email threats over the past year. This surge highlights the growing frequency and impact of phishing in 2024. Data from “The State of Phishing in 2024” report shows that phishing remains a significant threat to both individuals and organizations, causing substantial financial and reputational damage.
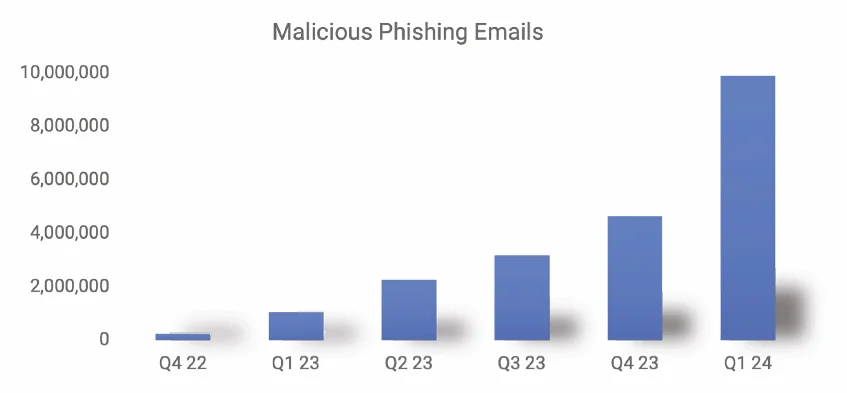
Increase in phishing emails through Q4 ‘22 – Q1 ‘24 (SlashNext)
Among the latest tactics used in campaigns involving phishing in 2024 are generative AI, phishing kits, CAPTCHA-based attacks, exploiting trusted services, and QR code-based attacks. Let’s explore these:
Generative AI
Generative AI tools and services have greatly contributed to the rise in phishing attacks. These tools enable cybercriminals to quickly create convincing phishing emails and malicious code.
An attacker-favorite platform is ChatGPT; since OpenAI launched ChatGPT in late 2022, researchers report a staggering 4,151% increase in malicious emails.
ChatGPT has been popular among both attackers and defenders since its launch in November 2022. (OpenAI)
Nevertheless, while attackers use AI to enhance their phishing campaigns, defenders can leverage AI to detect and mitigate these threats. AI-driven security solutions can analyze patterns and detect anomalies in real time, providing a strong defense against phishing attempts. In a later section, we will explore how AI can be used to combat phishing.
Phishing Kits
Phishing kits, available on dark web forums and other hacker channels, amplify the threat of phishing.
These kits provide cybercriminals with pre-packaged tools and templates to launch phishing campaigns, making it easier for less skilled attackers to carry out sophisticated attacks.
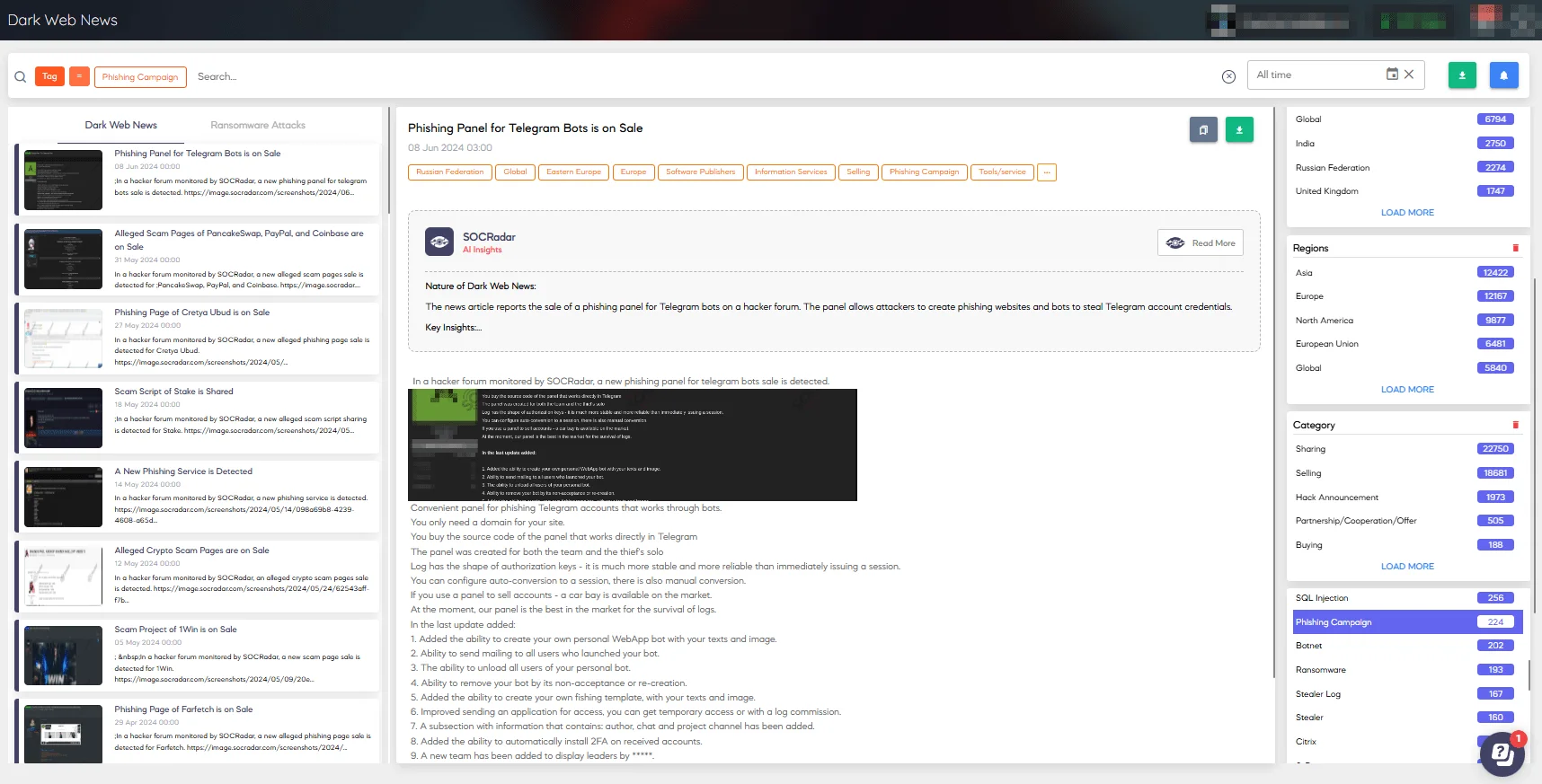
You can effortlessly monitor potential threats with SOCRadar. Use the Dark Web News module to filter and search for phishing kits and campaigns.
For more information on this threat, read our article: “What is a Phishing Kit?”
Exploiting Trusted Services
Attackers often leverage trusted services to hide phishing and malware, increasing the success rate of phishing campaigns.
Platforms such as Microsoft SharePoint, Amazon Web Services (AWS), and Salesforce are widely trusted, which helps cybercriminals bypass traditional security measures and reach their targets more effectively.
CAPTCHA-Based Attacks
Another notable trend in 2024 is the increased use of CAPTCHA-based attacks.
Cybercriminals exploit CloudFlare’s CAPTCHAs to hide credential harvesting forms, making it more challenging for users to detect malicious activities.
These attacks add a layer of complexity, making them harder to identify and block.
We previously discussed an interesting incident on the SOCRadar blog, in which threat actors were impersonating Cloudflare to spread trojans through CAPTCHA quizzes.
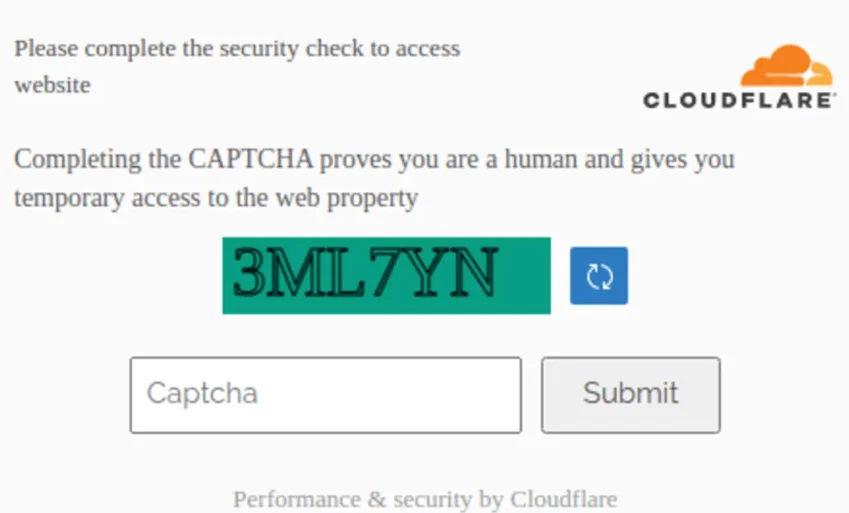
A fake Cloudflare CAPTCHA quiz
QR Code-Based Attacks
QR code-based attacks account for 11% of all malicious emails, according to The State of Phishing in 2024 report.
Cybercriminals use QR codes to direct victims to malicious websites or prompt them to download malware, exploiting the increasing use of QR codes in everyday transactions.

For an example of how QRs could be used in such attacks, check out a SOCRadar blog post about EvilQR – a threat that intercepts legitimate QR codes to gain unauthorized access and harvest credentials.
Rising Tide of Phishing in 2024 with Critical Statistics
Phishing attacks have surged in 2024, driven by the evolving complexity and diversity of tactics used by cybercriminals. The rising tide of phishing in 2024 reflects the relentless efforts of cybercriminals to exploit technological advancements and human vulnerabilities.
Researchers reported this alarming trend with several critical statistics:
- Over the last year, there has been an astounding 856% rise in malicious email threats. This dramatic increase underscores the growing sophistication and volume of phishing campaigns targeting individuals and organizations alike.
You can use the free Email Threat Analyzer feature on SOCRadar LABS to analyze EML files for traces of malicious content and protect against phishing scams.
Email Threat Analyzer on SOCRadar LABS
- In a period of six months alone, credential harvesting phishing attacks have surged by 217%. Cybercriminals are increasingly focusing on stealing user credentials, which can be used to gain unauthorized access to sensitive information and systems.
- Since January 2024, Business Email Compromise attacks have risen by 29%.Business Email Compromise (BEC) attacks are particularly damaging as they often involve social engineering tactics to deceive employees into transferring money or divulging confidential information.
- During a six-month period, an average of 59,000 credential phishing threats were hosted daily on trusted domains. This statistic highlights the widespread and persistent nature of these attacks, exploiting the reputation of legitimate services to deceive users.
You can track phishing domains and stolen credentials using the Digital Risk Protection module on the SOCRadar platform. The module features services such as Brand Protection, and VIP Protection, among others.
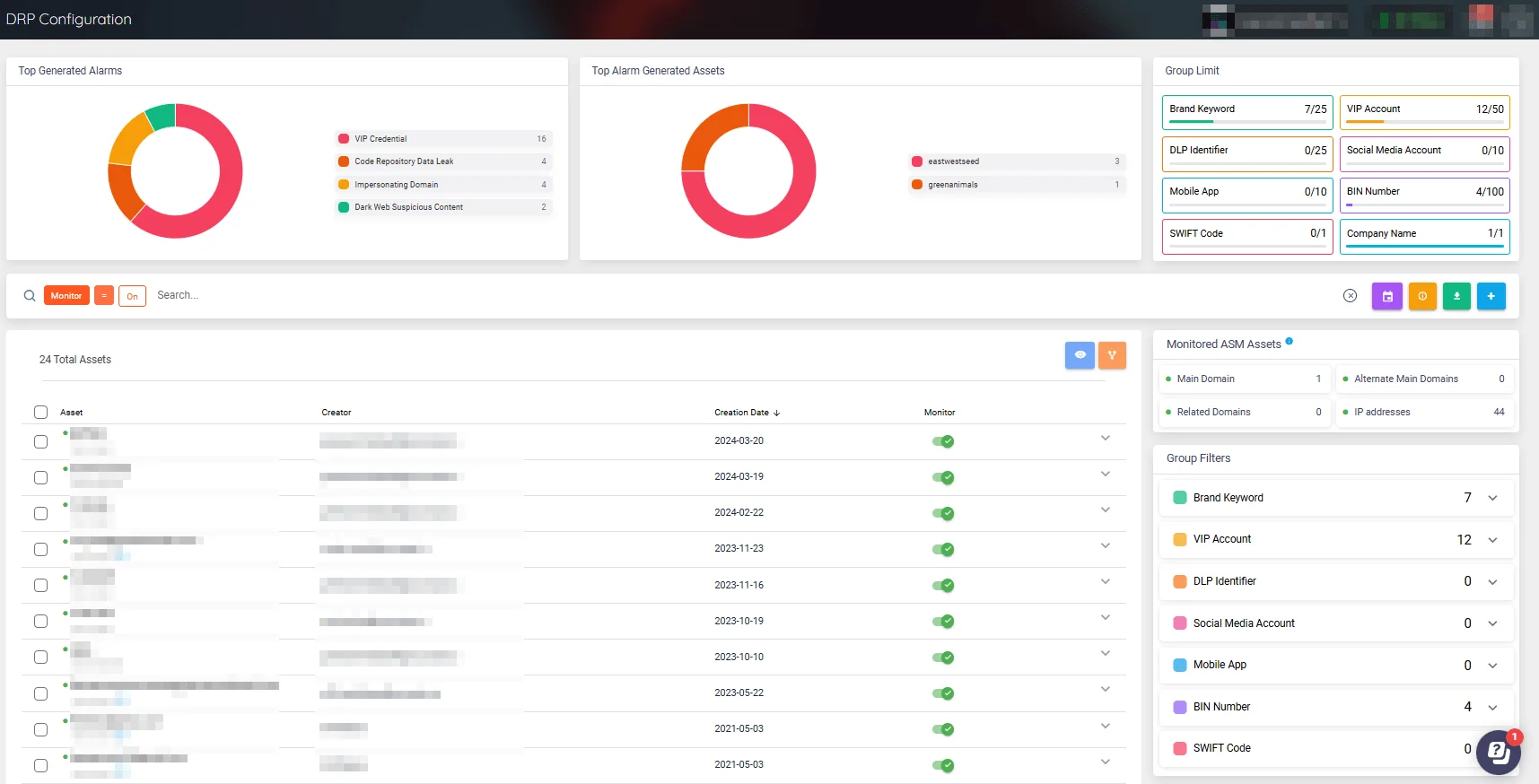
Digital Risk Protection Configuration page on the SOCRadar platform
These statistics paint a clear picture of the growing threats and help further understand the specific tactics employed by modern phishing attacks, but, what are the common signs to avoid phishing campaigns? And most importantly, how can we utilize AI to protect against phishing in 2024?
Red Flags in Your Inbox, the Top 10 Signs of Phishing Attempts
Phishing heavily relies on social engineering tactics to trick victims into revealing sensitive information. Recognizing phishing attempts involves spotting several common red flags.
Here are the top 10 signs of a phishing attempt:
- Urgent Messages: Emails that require immediate action, such as alerts about compromised accounts or suspended services.
- Unknown Sender: Emails from unfamiliar or unexpected senders, often using spoofed email addresses.
- Suspicious Links: Links that direct you to unfamiliar or fake websites. Hovering over the link often reveals a different URL than expected.
- Attachments: Unexpected attachments, especially with file extensions like .exe, .zip, or .doc, can contain malware.
- Inconsistent Formatting: Emails with unusual fonts, colors, or layouts that do not match a known sender’s usual style.
- Too Good to Be True Offers: Promises of rewards, prizes, or significant discounts that seem too good to be true.
- Requests for Personal Information: Emails asking for sensitive information like passwords, Social Security numbers, or credit card details.
- Generic Greetings: Lack of personalization, such as using “Dear Customer” instead of your actual name.
- Inconsistent URLs: URLs that look similar to legitimate sites but with slight variations, like misspellings or additional characters.
- Unusual Requests: Requests that seem out of the ordinary, such as transferring money or sharing confidential information.
You can utilize the free SOCRadar LABS services to quickly check for phishing threats. In addition to the Email Threat Analyzer service featured earlier, LABS also offers IP Reputation and Phishing Radar services as part of its SOC Tools.
Free SOC Tools featured on SOCRadar LABS
For more detailed guidance on identifying phishing attempts, see our blog post, “How to Detect Phishing Attacks?”
Key AI Capabilities in Combating Phishing
In a previous section, we mentioned how generative AI can be utilized by both attackers and defenders in the topic of phishing.
Cybercriminals leverage LLMs to swiftly craft convincing phishing emails. However, AI also plays a role in combating these threats. AI’s ability to analyze the context and behavior of emails makes it a powerful tool in phishing detection and prevention. AI systems can identify unusual communication patterns and detect changes in typical user behavior, helping to prevent sophisticated scams.
AI-based systems look for anomalies and warning signals within emails, from metadata to message content. For instance, AI can detect forged senders, typosquatted domains, and urgent language that may signify a phishing attempt.
By understanding the context of messages, AI systems can distinguish between spam and genuine threats, providing a defense against phishing.
For instance, if a cybercriminal attempts to impersonate a C-level executive of a company, AI can detect inconsistencies in the communication style and help block the attack before it causes harm.
Here are the key capabilities of AI in preventing phishing:
- Anomaly Detection: AI systems can identify deviations from normal behavior, such as unusual login locations or times, which may indicate a phishing attempt.
- Content Analysis: By analyzing the context and content of emails, AI can detect phishing attempts that traditional security measures might miss.
- User Behavior Monitoring: AI can learn and monitor typical user behavior, making it easier to spot irregular activities that could signal an attack.
Enhancing Brand Protection, and Domain Takedown Strategies Against Phishing
By integrating AI with traditional security measures, organizations can enhance their ability to detect and prevent phishing attacks, safeguarding their data and reputation.
In the fight against phishing in 2024, SOCRadar safeguards organizations with its many modules; with the Dark Web Monitoring module, it continuously scans various sources on the internet, including social media platforms, dark web forums, black markets, and IM services used by threat actors. This enables identification and alerting when information related to your organization, employees, or potential customers is detected in any of these sources.
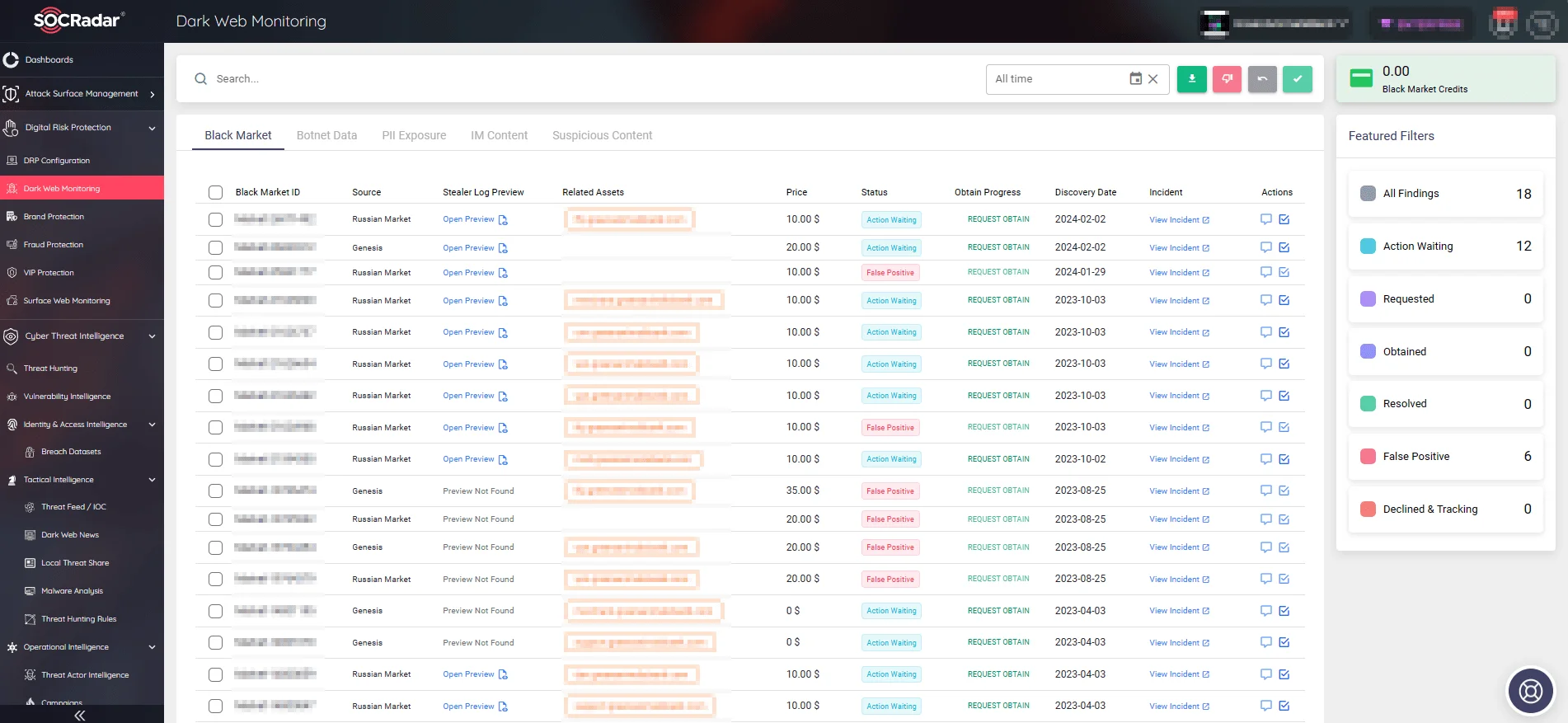
SOCRadar monitors various sources to detect data exposures (Dark Web Monitoring)
SOCRadar’s Brand Protection service also offers extensive capabilities, such as suspicious activities related to your digital assets, identifying compromised credentials, and facilitating the takedown of fraudulent sites. It helps organizations ensure that potential threats are mitigated before they can cause significant damage.
Additionally, SOCRadar’s Integrated Takedown service effectively combats digital threats like counterfeit websites and impersonating domains. This service works strategically to neutralize these dangers, ensuring your digital landscape accurately and authentically represents your organization’s true values and identity.
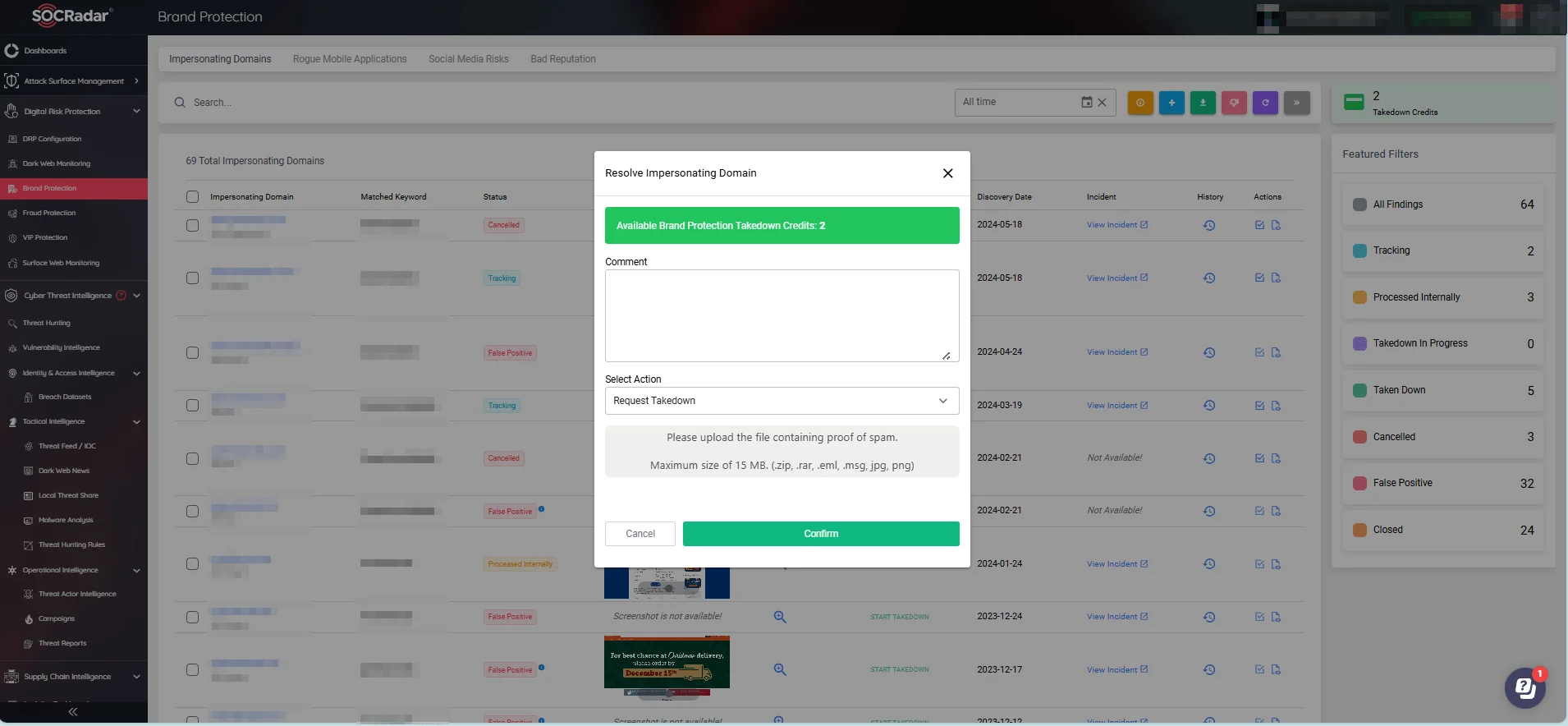
Quickly initiate takedowns on impersonating domains with SOCRadar’s Brand Protection
By quickly identifying and removing fraudulent sites, the Integrated Takedown service helps maintain your brand’s integrity and protects your customers from phishing attacks.
Conclusion
Threat actors continue to escalate phishing in 2024, driven by technological advancements and increasingly sophisticated tactics. With a staggering 856% rise in malicious emails – and a 4,151% increase since ChatGPT’s launch – organizations should be on high alert.
AI has several capabilities that can help combat these threats, and when used together with other security solutions, it can significantly enhance organizations’ ability to detect and block phishing attempts, safeguarding both data and reputation.
For comprehensive protection and an all-in-one service against cyber threats, explore SOCRadar’s solutions.

SOCRadar’s modules
SOCRadar’s Brand Protection and Integrated Takedown services provide proactive measures to combat phishing, ensuring your organization remains secure in the ever-evolving digital landscape.

































