
Real-Life Examples of Successful Threat Intelligence Operations
Threat intelligence can improve organizations’ overall security posture and reduce the risk of cyber attacks by developing proactive strategies to prevent and mitigate potential threats.
Threat intelligence can use in the following ways to combat attacks:
-Early detection: Threat intelligence can help identify potential attacks by detecting suspicious activities and IoCs. This information can be used to alert security teams to take necessary actions to prevent or mitigate the impact of an attack.
-Vulnerability management: Threat intelligence can help identify system vulnerabilities that attackers may exploit. Organizations can reduce the risk of successful attacks by prioritizing patching and other mitigation measures based on intelligence.
-Malware analysis: Threat intelligence can help identify malware. This information can be used to update anti-virus software, firewalls, and other security tools to prevent or mitigate the impact of an attack.
-Tracking attackers’ activity: Threat intelligence can help track attackers’ activity and identify the infrastructure used to control the attackers. This information can be used to prevent further attacks.
-Incident response: Threat intelligence can assist in incident response by providing context on the attacker’s tactics, techniques, and procedures (TTPs) and helping to identify the type of attacks used. This information can guide remediation efforts and recovery strategies.
-Prevention: Threat intelligence can help organizations create effective security policies and procedures that reduce the risk of several types of attacks. By understanding the tactics and techniques of attackers, organizations can develop effective defenses that reduce the likelihood of successful attacks.
-Takedown operations: Threat intelligence can help identify the infrastructure used by attackers, such as command-and-control servers, phishing websites, or payment processors. This information can be used to disrupt their operations and prevent them from carrying out attacks.
Consequently, threat intelligence is an essential component of any comprehensive cybersecurity strategy, helping organizations stay one step ahead of cyber attackers.
Real-Life Examples of Successful Threat Intelligence Operations
Botnet Attacks
Threat intelligence can be life-saving in identifying and responding to botnet attacks. Botnets are computer networks compromised and controlled by a single attacking party. The attacker usually has the purpose of conducting cyber attacks such as DDoS or stealing sensitive information. Threat intelligence also can be used to identify and block traffic associated with known botnets, preventing the botnet from carrying out attacks.
In 2017, cybersecurity company CheckPoint and China’s Qihoo 360 Netlab security firm discovered a botnet called “Reaper,” which had involved over a million internet-connected devices, including routers and IP cameras. The incident was estimated to utilize over 100,000 malicious endpoints to crash servers. The botnet was designed to carry out DDoS attacks and steal data. They were able to track the IP addresses and domain names which were used by the command and control (C&C) servers by using honeypots to identify IoCs and monitor the botnet’s activity. It was also observed that only one of the C&C servers was controlling over 10,000 bots. The largest number of devices infected by Reaper has been traced to China, Italy, and Singapore.
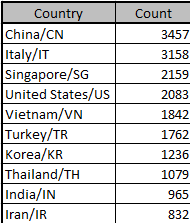
Netlab has confirmed that Reaper is currently using an exploit package that contains 9 vulnerabilities, namely: D-Link 1, D-Link 2, Netgear 1, Netgear 2, Linksys, GoAhead, JAWS, Vacron, and AVTECH. CheckPoint has also discovered the botnet attacking MicroTik and TP-Link routers, Synology NAS devices, and Linux servers. This was a threat intelligence method to identify the C&C infrastructure used by the botnet. With this information, they were able to take down the C&C servers, which effectively crippled the botnet. The company also shared its findings with law enforcement agencies and other security researchers to help prevent similar attacks in the future. This is just one example of the effective usage of threat intelligence in combat botnet attacks.
Ransomware
Threat intelligence also can be extremely useful in preventing, detecting, and responding to ransomware attacks. Organizations that prioritize threat intelligence in their security strategy can improve their ability to protect their systems and data from these increasingly sophisticated threats.
In May 2021, the Federal Bureau of Investigation (FBI) and the Russian Federal Security Service (FSB) collaborated with several private sector partners to dismantle the infrastructure of the notorious ransomware gang known as REvil, also known as Sodinokibi. REvil had been responsible for several high-profile attacks, including the ransomware attack on the meatpacking company JBS USA. JBS paid an $11 million ransom in Bitcoin to REvil.
Since launching in 2019, REvil has conducted numerous attacks against well-known companies, including JBS, Coop, Travelex, and Grupo Fleury. Finally, in a massive July 2nd attack using a Kaseya zero-day vulnerability, the ransomware gang encrypted sixty managed service providers and over 1,500 businesses worldwide. On July 23, 2021, Kaseya announced it had received the decryption key for the files encrypted on July 2.
Kaseya VSA ransomware attack from an unnamed “trusted third party,” later discovered to be the FBI who had withheld the key for three weeks and was helping victims restore their files. The key was withheld to avoid tipping off REvil of an FBI effort to take down their servers, which ultimately proved unnecessary after the hackers went offline without intervention.
The successful operation was based on extensive cyber threat intelligence gathering by the FBI, AFP, and their partners. VMWare’s head of cybersecurity strategy said, “The FBI, in conjunction with Cyber Command, the Secret Service, and like-minded countries, has truly engaged in significant disruptive actions against these groups.” Through this intelligence gathering, law enforcement identified the infrastructure and key individuals behind the REvil ransomware attacks.
In September 2021, Romanian cybersecurity firm Bitdefender published a free universal decryptor utility to help victims of the REvil/Sodinokibi ransomware recover their encrypted files if they were encrypted before July 13, 2021.
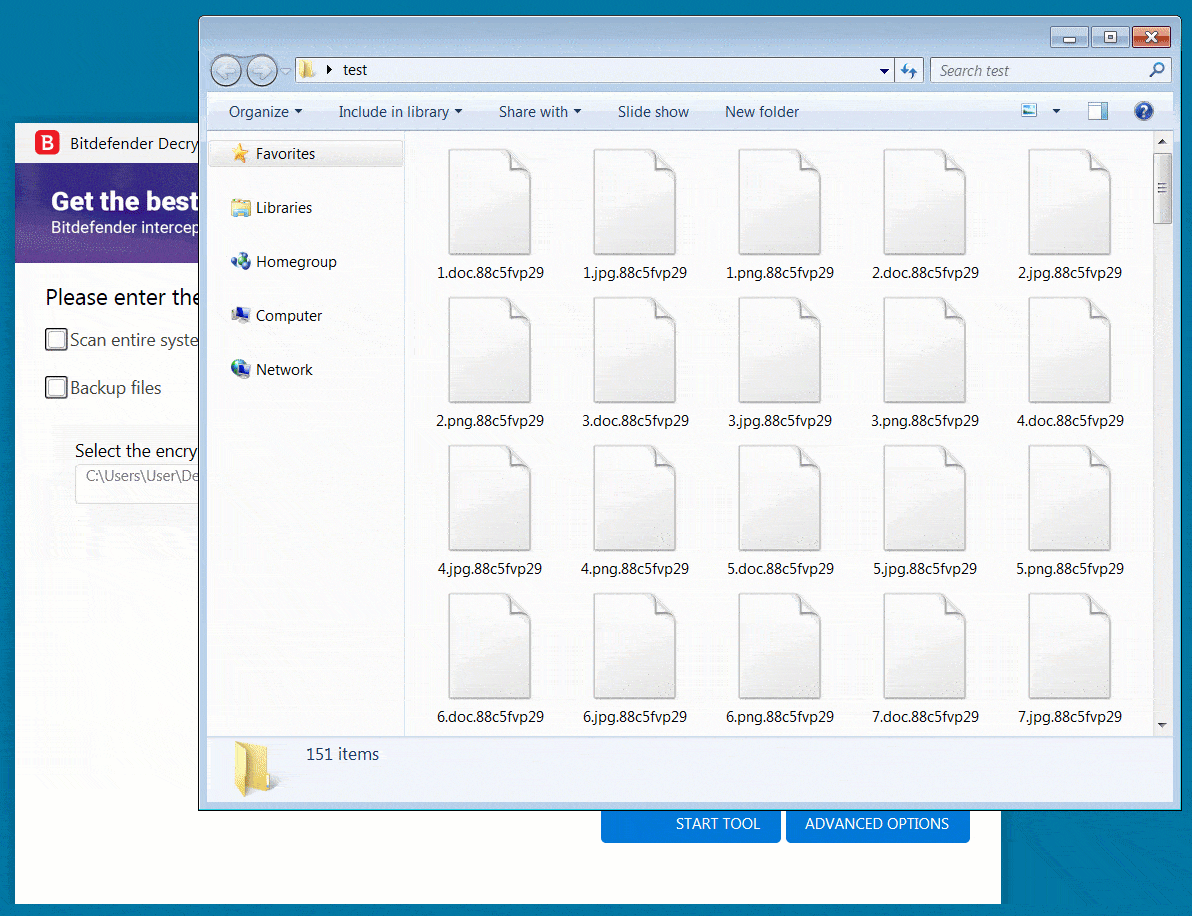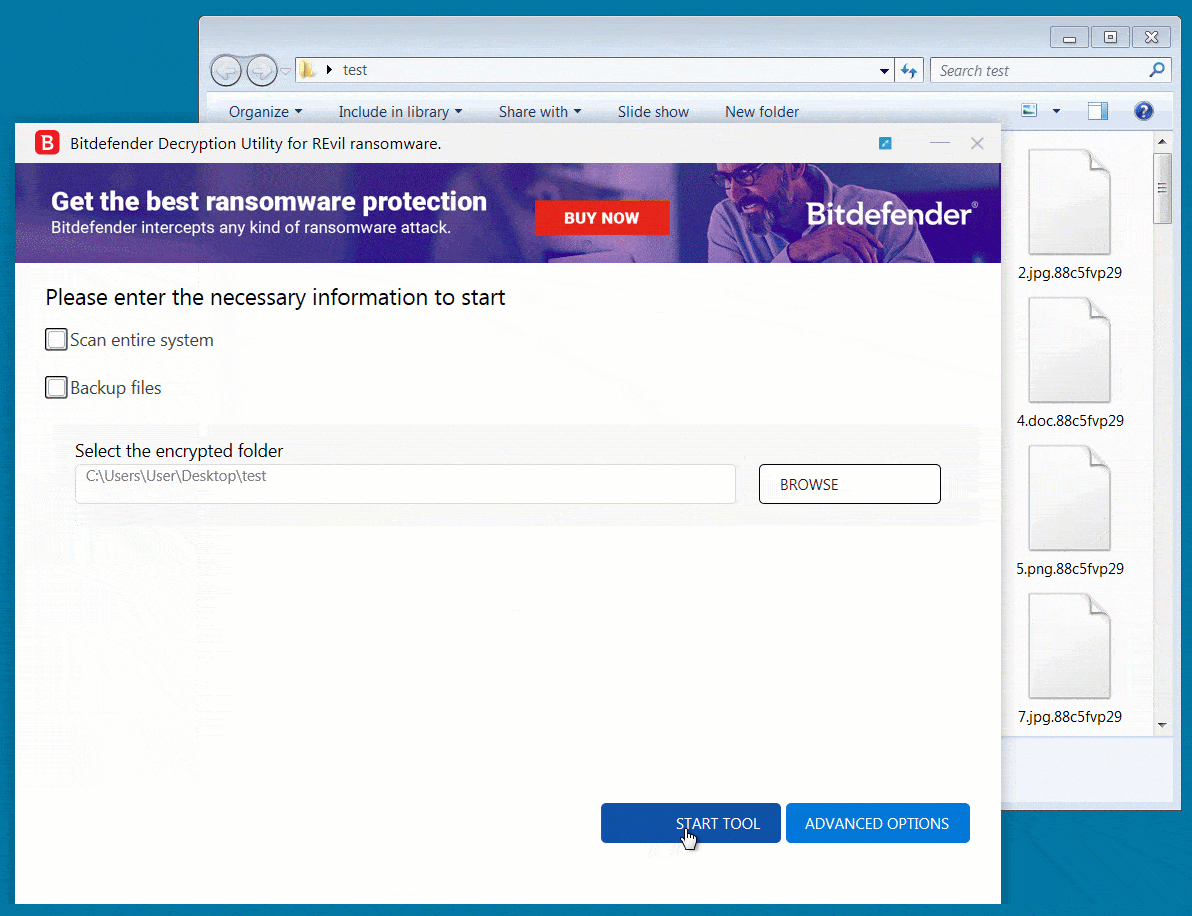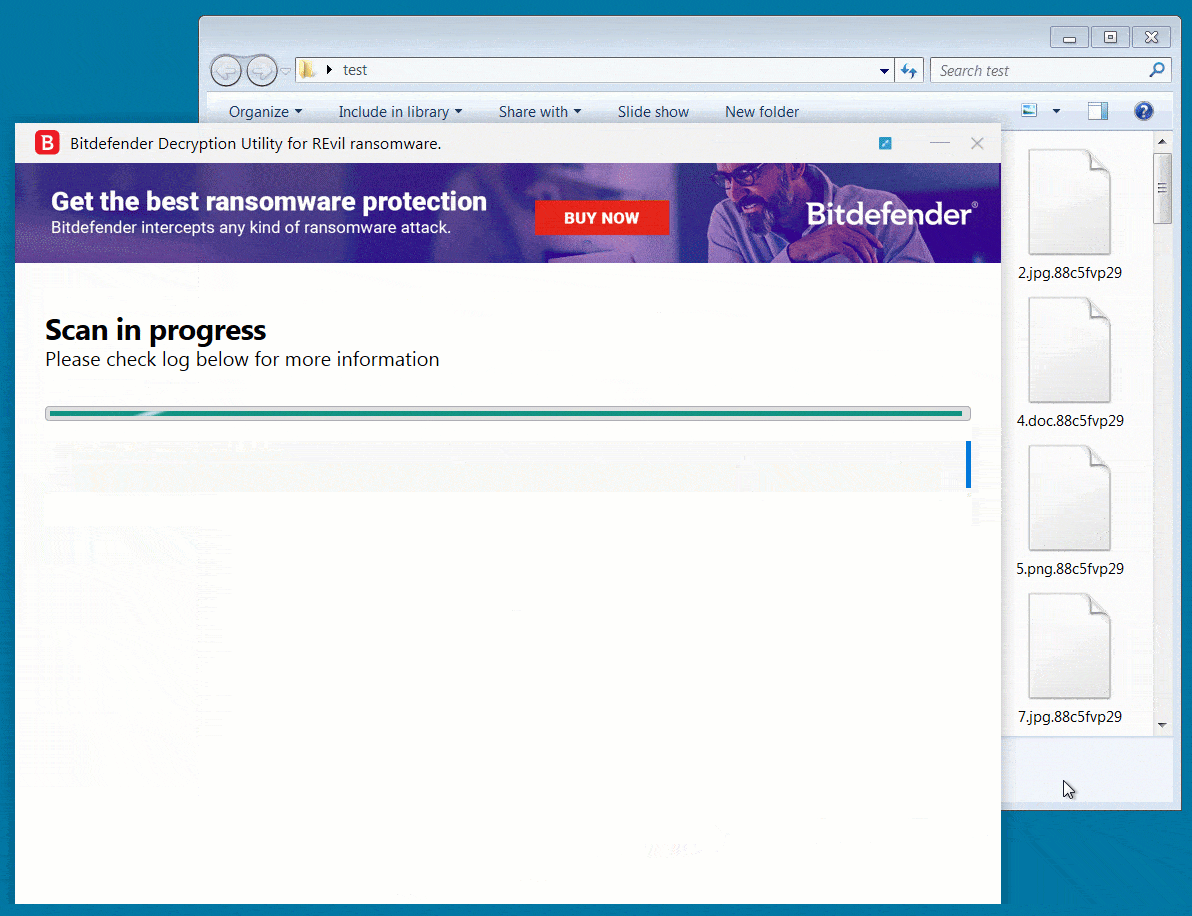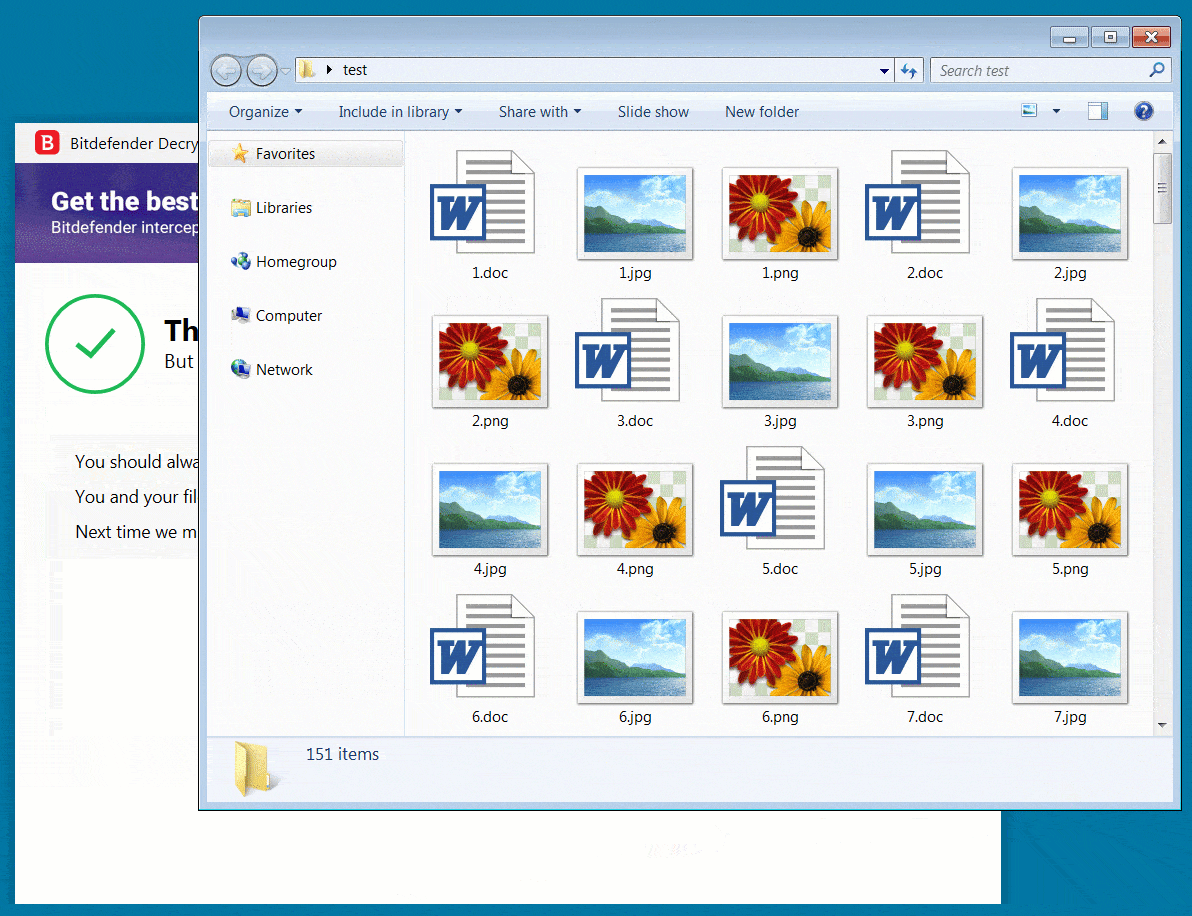
The operation also involved coordinated efforts to disrupt the gang’s communications, seize their servers, and arrest individuals associated with the group. As a result of this successful operation, REvil’s ransomware operations were disrupted, and several individuals associated with the group were arrested. This is a summarized example of how cyber threat intelligence can be used to identify and disrupt the operations of ransomware groups.
Advanced Persistent Threat (APT) Groups and Phishing Scams
Threat intelligence can be particularly valuable in preventing and responding to Advanced Persistent Threat (APT) attacks, which are typically carried out and highly skilled groups that are difficult to detect and deter. You can check out SOCRadar’s blog on the subject. Here’s an example of a successful application of threat intelligence to combat APT attacks:
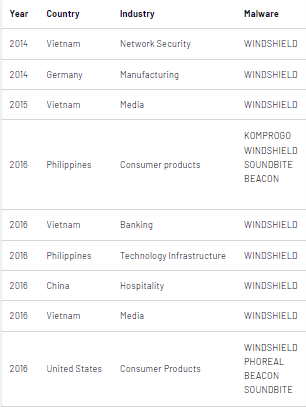
In 2017, the cybersecurity company FireEye discovered an APT group called “APT32,” also known as OceanLotus, targeting organizations in Southeast Asia. The group was using sophisticated techniques to prevent detection and gain access to sensitive data. FireEye used threat intelligence to track the group’s activity and identify its infrastructure to combat the threat. They discovered that the group was using a combination of custom-built malware and off-the-shelf tools to carry out their attacks.
The group used a website that masqueraded as a site for Vietnamese students studying abroad. When visitors to the site attempted to register for an account, they were redirected to a malicious website that served malware. This malware allowed OceanLotus to gain control of the victim’s computer.
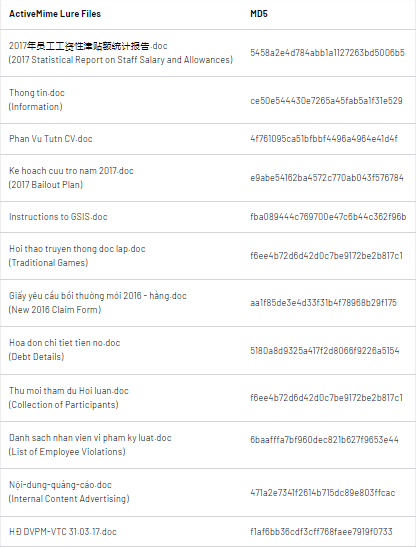
Also, APT32 actors designed multilingual lure documents which were tailored to specific victims. Although the files had “.doc” file extensions, the recovered phishing lures were ActiveMime “.mht” web page archives that contained text and images. These files were likely created by exporting Word documents into single file web pages. APT32 actors deliver malicious attachments via spear phishing emails. Evidence has shown that some may have been sent via Gmail.
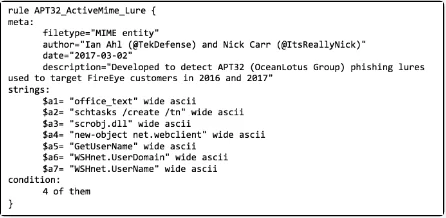
Using this information, FireEye developed a set of indicators of compromise (IoCs) that could be used to detect the group’s activity. Associated malware are SOUNDBITE, WINDSHIELD, PHOREAL, BEACON, and KOMPROGO. By identifying these IoCs, FireEye can create signatures and rules that can be used to detect and block APT32’s malware and command-and-control infrastructure. These IoCs can also be shared with other organizations and law enforcement, enabling them to detect and block APT32’s activity within their own networks.
By using threat intelligence to track the APT group’s activity and develop IoCs, FireEye was able to effectively detect and mitigate the threat. This is just one example of how threat intelligence can use to combat APT attacks.
BlueBleed
SOCRadar, continuously monitors the surface, deep, and dark web for vulnerabilities and data leaks. BlueBleed Part I is discovered as the result of such monitoring.
In 2022, SOCRadar’s built-in Cloud Security Module detected a misconfigured Azure Blob Storage maintained by Microsoft containing sensitive data from a high-profile cloud provider. As a result of investigations on the misconfigured server, SQLServer databases, and other files, SOCRadar researchers discovered publicly available 2.4 TB of data containing sensitive information belonging to Microsoft. The exposed data include files dated from 2017 to August 2022.
According to analysis, the leak, dubbed BlueBleed Part I, consists of critical data belonging to more than 65,000 companies from 111 countries. According to SOCRadar’s statement, SOCRadar researchers have discovered more than 335,000 emails, 133,000 projects, and 548,000 exposed users within the leaks.
Upon receiving the alert, Microsoft’s security team immediately investigated the issue and confirmed that the S3 bucket contained files related to its Bing search engine, including logs and configuration files. Microsoft then secured the bucket to prevent unauthorized access and thoroughly reviewed its cloud storage configurations to prevent similar incidents from occurring in the future.
This incident highlights the importance of proper security configuration and access control for cloud storage services and the value of cyber threat intelligence in detecting potential security risks. With the help of SOCRadar’s platform, Microsoft was able to identify and address a security issue before threat actors could exploit it.
In conclusion, as exemplified by the instances discussed in this blog, cyber threat intelligence has played a critical role in identifying and mitigating various cyber threats, including phishing attacks, ransomware, data breaches, etc.
Threat intelligence platforms like SOCRadar can identify potential threats across a wide range of attack surfaces using advanced technologies and techniques and provide organizations with actionable intelligence to protect themselves against these threats.
SOCRadar’s extended cyber threat intelligence modules are a precious platform for organizations looking to stay ahead of the constantly evolving threat landscape. SOCRadar empowers organizations to make more informed security decisions and respond quickly and effectively to potential threats by providing real-time, comprehensive threat intelligence. Additionally, the platform’s integration with various security tools helps organizations incorporate cyber threat intelligence into their existing security workflows and processes more efficiently.
As a result, this blog emphasizes the crucial significance of Cyber Threat Intelligence Sharing in the battle against cyber threats, underscoring the imperative for organizations to remain vigilant and proactive. By employing appropriate tools and technologies, organizations can gain an edge against potential threats and safeguard themselves against the ever-evolving tactics employed by cybercriminals and threat actors.
The real-life examples presented in this blog serve as a reminder that organizations require dependable solutions such as SOCRadar as a cyber threat intelligence provider to effectively navigate the intricate and constantly changing cyber threat landscape. With SOCRadar’s expertise and solutions, organizations can fortify their security stance, mitigate risks, and shield their digital infrastructure from potential threats.



































