
The Wolf in Sheep’s Clothing: How Cybercriminals Abuse Legitimate Software
[Update] November 9, 2023: Added FBI’s notice, see under the title: “FBI Warns of Ransomware Threats via Third Parties and Legitimate Tools.”
Cybersecurity is an ever-evolving space, this may be fueled by the idea of making the space and everything around it a smidge safer; however, there is also the other side of the coin, threat actors keep finding ways to attack organizations, and one of their sneakiest ways is the abuse of legitimate software, and dual-use software, such as Cobalt Strike. This practice involves the misuse of authentic, often widely-used software for malicious purposes. The reasons behind this strategy are manifold. Primarily, it stems from a desire for stealth. By leveraging these software, attackers can infiltrate and navigate networks undetected, thereby increasing their chances of achieving their objectives without discovery. This method also complicates the attribution of an attack, making it harder to identify the culprits. Furthermore, the use of these software may lower the barriers to entry into the world of cybercrime, enabling even less-skilled hackers to conduct disruptive attacks.
The issue of legitimate software abuse is not one that is likely to disappear anytime soon. As technology continues to advance, threat actors invariably find ways to exploit it for their own malicious ends. Consider the rise of cloud technology, for instance. As more organizations migrate their data to the cloud, the infrastructure itself becomes a target for misuse. Legitimate cloud-based tools, such as Dropbox and Google Drive, which were designed to facilitate data storage and sharing, are now being repurposed by attackers for nefarious activities, such as in the case of APT29’s campaigns around mid-2022.
The widespread availability of these tools further exacerbates the problem. Since they can be accessed and used by a broad spectrum of individuals, it becomes increasingly challenging to determine who is behind a specific incident. Some of these tools, in their original design, were not intended to be malicious, while others have controlled malicious properties (simulating attacker behavior, etc.). However, they possess functionalities that, when used with malicious intent, can cause significant harm. Regrettably, traditional cybersecurity solutions are often ill-equipped to manage these threats effectively, making it a pressing issue that demands attention and newer solutions.
FBI Warns of Ransomware Threats via Third Parties and Legitimate Tools
The FBI also emphasizes the seriousness of exploiting legitimate software, as we’ve discussed in this article. They released a notification titled “Ransomware Actors Continue to Gain Access through Third Parties and Legitimate System Tools” to warn about recent ransomware risks and suggested measures to enhance security. They observed an increase in ransomware incidents targeting casinos through third-party providers. Furthermore, they shed light on the activities of a group known as Silent Ransom Group (SRG), which used phishing tactics to steal data and extort victims.
What Are the Most Common Software Abused?
Legitimate software and dual-use software, often integral to daily operations, are being repurposed for malicious activities, making them a hidden threat within our systems. The abuse of such software is not limited to a select few but spans a wide range of tools, each with its unique functionalities that can be exploited. In the following sections, we will delve into some of these commonly abused software, shedding light on their legitimate uses and how they are manipulated for malicious intent.
The abuse is not a random act but a calculated move by threat actors. They choose software that is widely used and trusted, making their activities blend in with regular network traffic, thus evading detection and so on.
In our exploration, we will look at software ranging from remote monitoring and management tools to penetration testing tools. Each of these tools has been exploited by threat actors to carry out their malicious activities. By understanding the extent of this issue, we can better equip ourselves to detect and counter these hidden threats.
Cobalt Strike
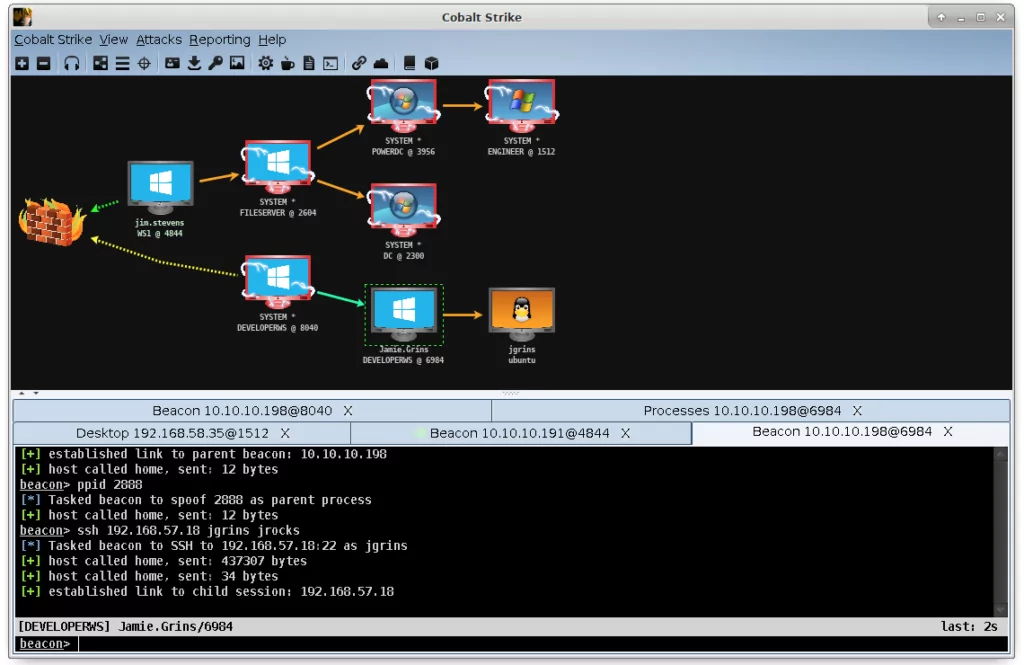
Cobalt Strike is a commercial adversary simulation software that is primarily designed for use by red teams. However, it has also been co-opted by various threat actors, ranging from ransomware groups to advanced persistent threats (APTs) engaged in espionage. The two main elements of Cobalt Strike are the team server, which acts as the command and control (C2) center, and the client, which is used by operators to connect to the team server.
The team server component of Cobalt Strike is responsible for accepting connections from clients, receiving beacon callbacks, and handling web requests. The client, on the other hand, is the interface that operators use to connect to the team server. This can be done either locally or remotely. The term beacon refers to Cobalt Strike’s default malware payload, which establishes a connection to the team server. Any active callback sessions from a target are also referred to as beacons.
Threat actors leverage Cobalt Strike in their attacks by using it as an effective means of controlling systems they have compromised. It allows them to execute commands, deliver additional malware, and traverse a compromised network. The beacon payload is particularly appealing to threat actors as it can enable them to maintain control over a compromised system while keeping a low profile, thereby making detection and removal more challenging. The beacon payload can be configured to communicate via various protocols, which enhances its versatility and allows threat actors to blend in with regular network traffic.
To understand how Cobalt Strike is leveraged in cyber attacks, we can look at a report shared by Talos Intelligence about a campaign using Cobalt Strike. There are two methods reported to be used in the report.
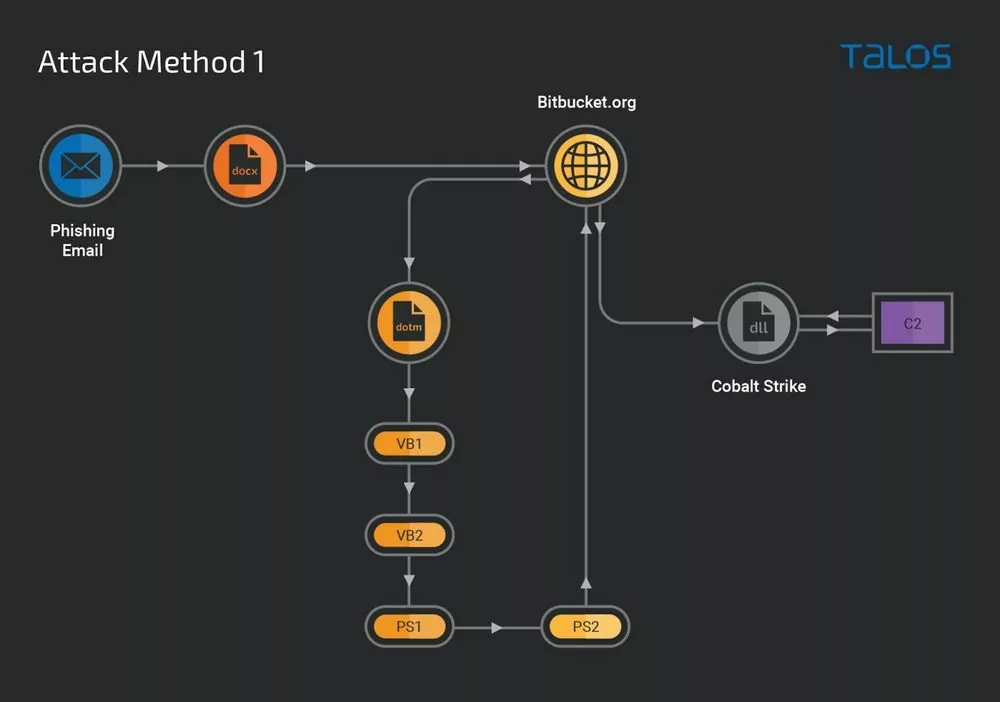
The first method begins with a phishing email containing a malicious Microsoft Word document. This document is designed to exploit a known vulnerability (CVE-2017-0199, CVSS:7.8 High) in Microsoft Office, which allows for remote code execution. When an unsuspecting victim opens this document, it triggers the download of a malicious Word document template from an attacker-controlled repository. This downloaded template then executes an embedded malicious Visual Basic script, leading to the generation and execution of further obfuscated VB and PowerShell scripts. The end result of this intricate chain of events is the deployment of a Cobalt Strike beacon. This beacon, a leaked version of the legitimate tool, is configured to perform targeted process injection of arbitrary binaries, effectively camouflaging the malicious activity within legitimate traffic.
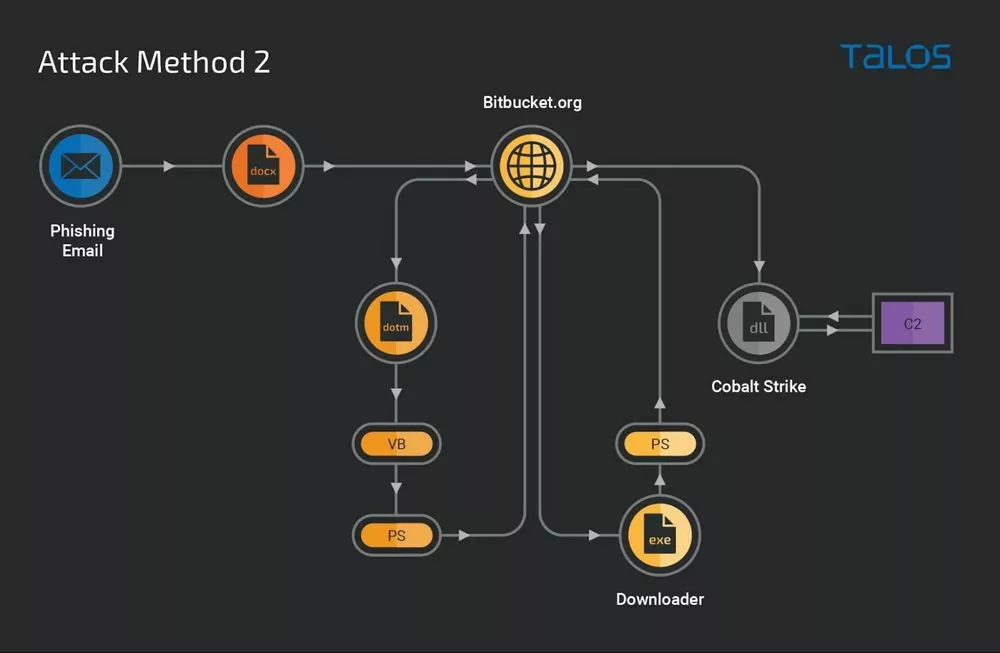
The second method follows a similar initial path but diverges at the point of the downloaded template. Instead of executing an embedded maliciousVisual Basic script, the malicious VB, in this case, downloads and runs a Windows executable. This executable then triggers malicious PowerShell commands to download and implant the payload, which, like the first method, is a Cobalt Strike beacon. This beacon is configured similarly to the first, designed to blend malicious traffic with legitimate traffic and perform various malicious operations, such as injecting other malicious binaries into the running processes of the infected machines
In both methods, the dual-use nature of Cobalt Strike allows threat actors to blend their malicious activities within the sea of legitimate traffic, making detection significantly more challenging. It also provides them with a versatile toolset to perform a variety of malicious operations, further emphasizing the potential dangers posed by the abuse of legitimate software.
Remote Monitoring and Management (RMM) Software
RMM software is a type of application that is widely used by IT departments across organizations of all sizes. These tools, which include AnyDesk, Atera, TeamViewer, ConnectWise, SimpleHelp, Syncro, and others, are designed to facilitate the management and monitoring of IT systems. However, their legitimate use has not prevented them from being exploited by malicious actors. In fact, the misuse of RMM software by threat actors has become so prevalent that the Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert about it.
Threat actors leverage RMM software in their attacks in various ways. In one widespread cyber campaign identified by CISA in October 2022, cybercriminals used phishing emails to lead victims to download legitimate RMM software—specifically, ScreenConnect (now ConnectWise Control) and AnyDesk. The actors then used these tools in a refund scam to steal money from the victim’s bank accounts. While this campaign appeared to be financially motivated, it could potentially lead to other types of malicious activity.
CISA noted that the actors did not install downloaded RMM clients on the compromised host. Instead, the actors downloaded AnyDesk and ScreenConnect as self-contained, portable executables configured to connect to the actor’s RMM server. The use of portable executables of RMM software provides a way for threat actors to establish local user access without the need for administrative privilege and full software installation. This effectively allows them to bypass common software controls and risk management assumptions.
Additionally, these software are not only used for financial gains. State-sponsored groups also leverage legitimate software to stealthy gain persistence. In two different instances, it was found that MuddyWater, Iranian APT Group, used SimpleHelp and ScreenConnect to ensure persistence on victim devices.
Biggest Offenders
Ransomware groups have been increasingly leveraging legitimate software/tools to conduct their cyber attacks, and the reasons behind this can be multifaceted. However, the main leverage threat actors have is the stealth that these tools bring. The use of legitimate tools allows these threat actors to blend in with normal network traffic, making their activities harder to detect and block. This stealthy approach increases the chances of a successful attack and prolongs the dwell time within the victim’s network.
As we already highlighted, Cobalt Strike is one of the most frequently weaponized software for threat actors. In the hands of cybercriminals, it has many capabilities, ranging from lateral movement to backdoor. Another tool, PsExec, a utility for running processes on remote systems, can be abused for arbitrary command shell execution and lateral movement. Mimikatz, a dual-use tool like Cobalt Strike, built as a proof-of-concept code to demonstrate the vulnerabilities in Microsoft authentication protocols, is also used for credential dumping, extracting usernames, passwords, and other credentials that might be used to escalate privilege in other phases of the attack.
The Metasploit Framework is also a powerful open-source tool that can be used for penetration testing and vulnerability assessment. While it can be used to help security professionals identify vulnerabilities in systems and networks, it can also be leveraged by threat actors. In the hands of malicious individuals, Metasploit can be employed to exploit known vulnerabilities, deliver payloads, and establish control over compromised systems. Thus, it can be weaponized for cyberattacks when abused outside its legitimate context. One last example, MegaSync, a cloud-based synchronization tool, is used for data exfiltration, which is the most crucial step for ransomware attacks.
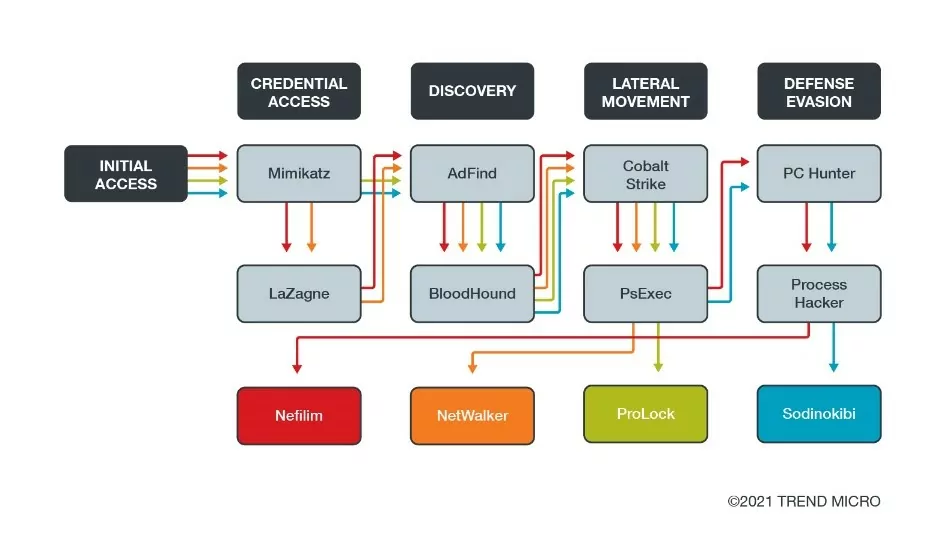
One of the most notorious actors in the ransomware space is the LockBit group. They heavily rely on legitimate software to conduct their malicious activities. Their operational strategy underscores the importance of abusing legitimate software. Their toolkit of legitimate software is diverse, each serving a unique role in their malevolent campaigns.
As detailed in a comprehensive profile by SOCRadar, the LockBit group leverages a variety of well-known software. It ranges from 7-zip, a file archiving tool, to AnyDesk and TeamViewer, solutions for remote access, and FileZilla, an FTP solution. Below, you can see the software LockBit uses mapped to the MITRE ATT&CK.
|
Chocolatey |
||
|
AdvancedRun |
||
|
7-zip |
||
|
Backstab |
||
|
Bat Armor |
||
|
Defender Control |
||
|
GMER |
||
|
PCHunter |
||
|
PowerTool |
||
|
Process Hacker |
||
|
TDSSKiller |
||
|
ExtPassword |
||
|
LostMyPassword |
||
|
Microsoft Sysinternals ProcDump |
||
|
T1555.003 – Credentials from Password Stores: Credentials from Web Browsers |
PasswordFox |
|
|
Bloodhound |
||
|
Advanced Internet Protocol (IP) Scanner |
||
|
Advanced Port Scanner |
||
|
SoftPerfect Network Scanner |
||
|
Seatbelt |
||
|
Splashtop |
||
|
AnyDesk |
||
|
Atera Remote Monitoring & Management (RMM) |
||
|
ScreenConnect (also known as ConnectWise) |
||
|
TeamViewer |
||
|
ThunderShell |
||
|
T1071.002 – Application Layer Protocol: File Transfer Protocols |
FileZilla |
|
|
Ligolo |
||
|
PuTTY Link (Plink) |
||
|
T1567.002 – Exfiltration Over Web Service: Exfiltration to Cloud Storage |
FreeFileSync |
|
|
MEGA Ltd MegaSync |
||
|
WinSCP |
||
|
Mimikatz |
||
|
Microsoft Sysinternals PsExec |
||
|
LaZagne |
||
|
Impacket |
||
|
Ngrok |
||
|
AdFind |
||
|
Rclone |
Table 1: Software used by LockBit mapped to MITRE ATT&CK
Mitigations and How Can SOCRadar Help?
- Phishing is commonly used by threat actors these days as an initial access vector, as we see in the events shared on the post. Therefore, protection against phishing becomes a priority against cyber attacks in general and specifically for the abuse of legitimate software. This protection should include tools to analyze attachments from phishing emails as well as user training. SOCRadar provides a malware analysis feature to help on analyzing potentially malicious email attachments.
- It can be hard to track which vulnerabilities are on the rise and which software has vulnerabilities. Regularly updating systems can help prevent attackers from known vulnerabilities. However, it may not be enough. SOCRadar provides Attack Surface Management module, which continuously monitors your digital assets, identifying any outdated systems or applications that may pose a security risk. By providing real-time visibility into your attack surface, it enables you to proactively address vulnerabilities before they can be exploited, thereby enhancing your organization’s overall cybersecurity posture.
- It goes without saying, keep offline backups regularly. Ransomware groups leverage legitimate software heavily. In the event of a ransomware attack, offline backup of systems can limit the potential damage received.
- Employ the principle of least privilege in your environment. Threat actors leverage software that is used in red team activities. If the principle is employed properly, an out-of-place activity may reveal an attacker on the system.
- To mitigate the risks associated with the abuse of these tools, it’s crucial to establish and enforce strict policies. These policies should dictate who has the authority to install and use such software. By tying the use of these tools to specific permissions, time frames, and conditions, organizations can ensure that only authorized personnel have access. This not only reduces the risk of internal misuse but also makes it harder for external threat actors to exploit these tools. It’s essential to regularly review and update these policies to adapt to the evolving threat landscape and to communicate them clearly to all employees.
- To keep track of new attack techniques, indicators of compromise (IoCs), and other relevant threat data, employ a threat intelligence service. SOCRadar can provide detailed insights about emerging threats through modules such as supply chain intelligence and vulnerability intelligence. If any skewed version of legitimate software, such as AnyDesk, has an IoC pointing it out, you can proactively update security measures in your system for a better chance against the threat.
The abuse of legitimate software continues to pose a significant threat. This tactic, employed by a wide range of threat actors, from financially motivated cyber criminals to state-sponsored APT groups, presents unique challenges in terms of detection and mitigation. The stealthy nature of these attacks, coupled with the inherent trust associated with legitimate software, makes them particularly effective. Moreover, the widespread availability and diverse functionalities of these tools offer threat actors a versatile arsenal for their malicious intents.
However, understanding the threat is the first step toward effective mitigation. By shedding light on the abuse of legitimate software, we try to aim to raise awareness about this threat and provide actionable insights to help organizations bolster their defenses. While the task may seem daunting, remember that cybersecurity is a continuous journey. Regular audits, user training, and the implementation of robust security policies are crucial in this endeavor. Furthermore, leveraging threat intelligence services can provide real-time insights into emerging threats and help organizations stay one step ahead of the threat actors.


































