Threat Actor Profile: ScarCruft / APT37
[Update] October 17, 2024: “ScarCruft Exploits CVE-2024-38178 to Deploy RokRAT Malware”
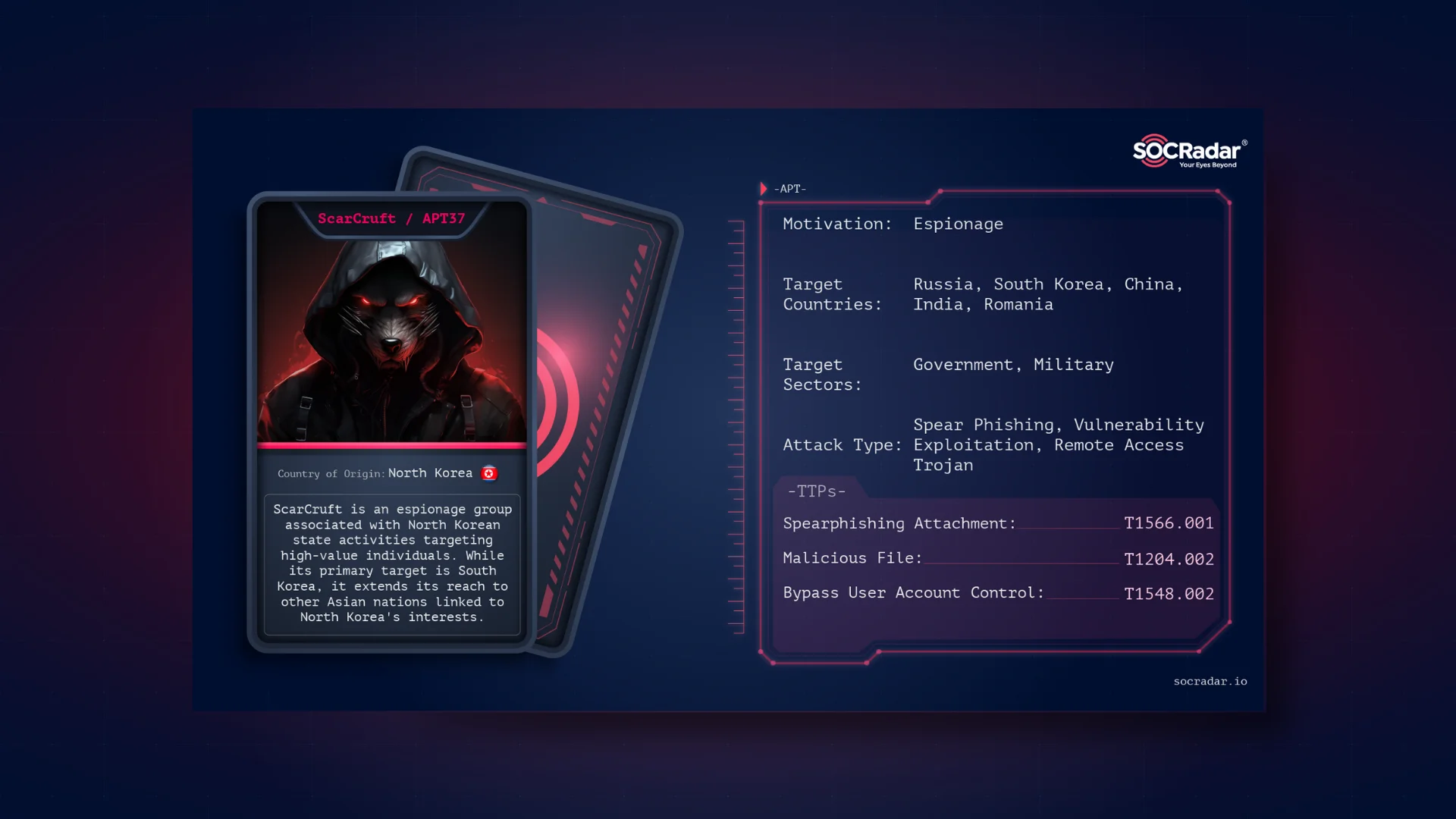
ScarCruft, also widely known as APT37 or Reaper APT, is an espionage group associated with North Korean state activities that target high-value individuals. The group has been active since 2012, and while its primary target is South Korea, ScarCruft extends its reach to other Asian nations linked to North Korea’s interests.
SOCRadar Threat Actor Card of ScarCruft / APT37
The group’s interests lie heavily in government, military bodies, and industries aligned with North Korea’s concerns.
Employing watering-hole attacks and sophisticated exploits, ScarCruft infiltrates systems to install backdoors and conduct reconnaissance. They innovate with malware development and experiment with infection chains, often employing decoy documents associated with other North Korean groups.
Utilizing zero-day exploits and spear-phishing tactics, which form the backbone of their sophisticated attack methodologies, ScarCruft orchestrates attacks across various countries, including Russia, Nepal, China, and more.
Constantly evolving, ScarCruft refines its methods, including the use of weaponized Microsoft Compiled HTML Help (CHM) files, exploring new file formats, and enhancing evasion techniques.
Their persistence and sophistication make ScarCruft a formidable threat to South Korea and North Korea-associated interests, leveraging advanced tactics to fulfill their espionage goals.
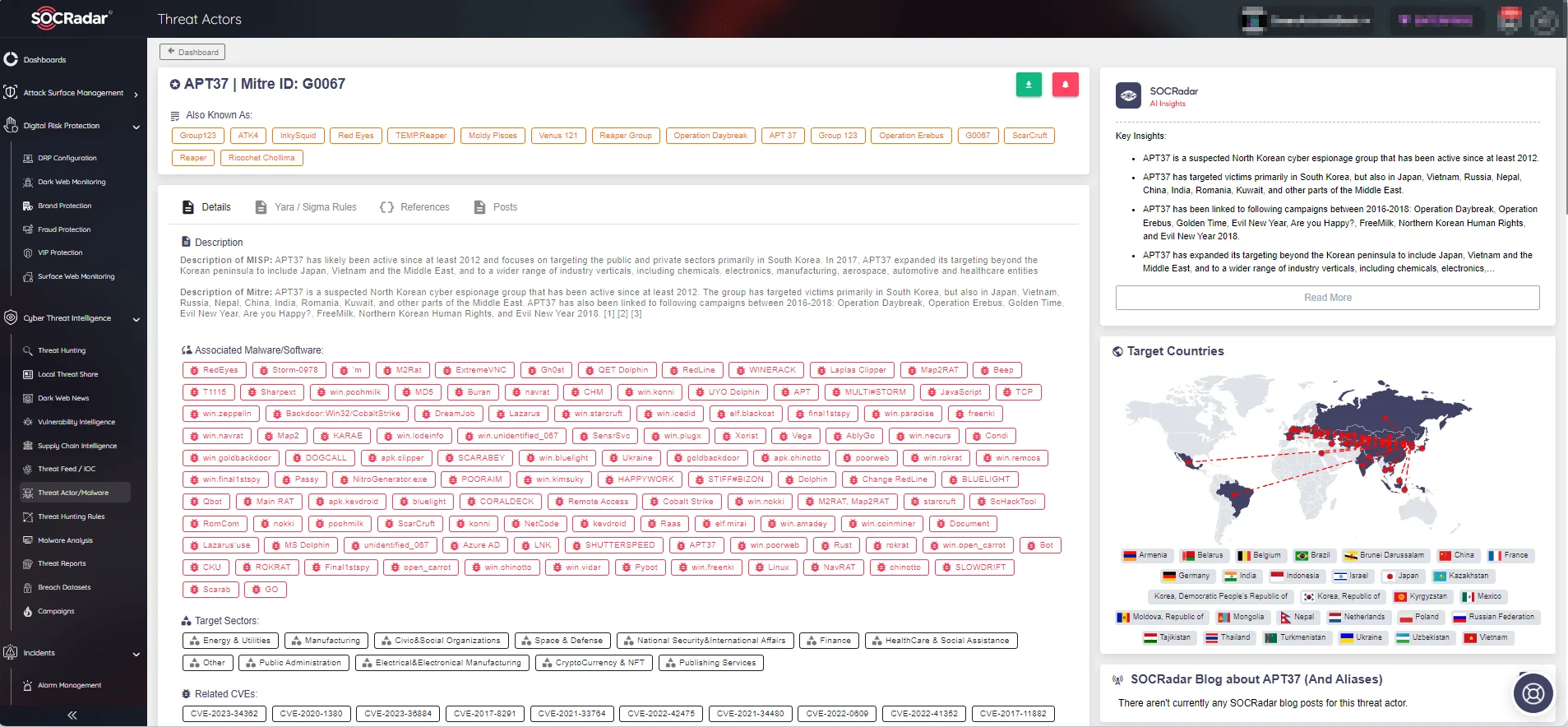
Threat actor page of APT37 (ScarCruft) on SOCRadar platform
How Does ScarCruft / APT37 Attack?
ScarCruft employs diverse methods to deploy its backdoors, including spear-phishing and strategic web compromises. They exploit zero-day vulnerabilities for sophisticated attacks and have been noted for watering-hole attacks, compromising websites commonly visited by their targets to distribute their backdoors via malicious code.
A standout method is the use of Dolphin malware. Dolphin is a backdoor facilitating extensive spying capabilities like drive monitoring, file exfiltration, keylogging, screenshot capture, and browser credential theft.
Another malicious tool used by the APT group, BLUELIGHT, was previously deployed in a watering-hole attack on a South Korean online newspaper.
ScarCruft experiments with malware delivery routes, such as oversized LNK files for RokRAT distribution, and employs social engineering – deceiving targets via phishing to deliver malware.
What sets ScarCruft apart is its utilization of the self-decoding technique, an uncommon method among APT groups, to efficiently distribute malware. The self-decoding technique involves encoding a malicious payload within another file or code for evasion purposes. When the document is opened or the code is executed, the payload is dynamically decoded and executed. Additionally, the group employs unconventional channels for its operations, leveraging social networking sites and cloud platforms for Command and Control (C2) communication.
The tactics of ScarCruft evolve continuously as the group keeps finding novel methods to bypass security measures and enhance their operational effectiveness.
Key Takeaways from the Tactics Used by the Threat Actor:
- Spear Phishing: ScarCruft initiates intrusions through spear phishing emails, employing social engineering to entice users into opening malicious attachments to deliver backdoors.
- Compromised Websites: The group employs compromised websites to retrieve second-stage malware, indicating a multi-stage attack strategy.
- Social Networking and Cloud Platforms: ScarCruft leverages social networking sites and cloud platforms for Command and Control (C2) communication, utilizing unconventional channels for their operations.
- Self-Decoding Technique: ScarCruft stands out for using the self-decoding technique, a less common method among APT groups, to distribute malware efficiently.
Malware Used by ScarCruft / APT37
ScarCruft (APT37) uses a variety of customized tools to extract sensitive data from compromised systems, including Chinotto, RokRat, BLUELIGHT, GOLDBACKDOOR, and Dolphin. These tools facilitate remote access, data theft, and command execution while evading detection.
ScarCruft employs a diverse range of malware in its operations, such as Microsoft Compiled HTML Help (CHM) files, to install additional malware on target systems. The group is also known to have developed malware targeting mobile devices, using Windows Bluetooth APIs to collect data from connected devices. Another malicious tool used by the group while targeting mobile – alongside desktop – devices is the Chinotto spyware.
Notably, ScarCruft has been associated with a previously unknown malware family called NOKKI, and furthermore, in early 2023, researchers linked ScarCruft to a malware strain named M2RAT, a Remote Access Trojan (RAT) adept at bypassing antivirus and intrusion detection systems.
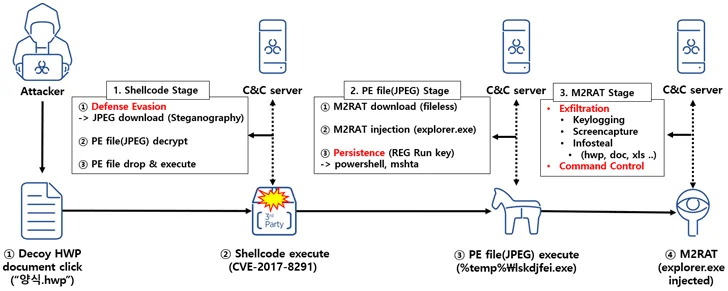
The flow of attacks deploying M2RAT (AhnLab)
Vulnerabilities Exploited by ScarCruft / APT37
ScarCruft (APT37) has exploited various vulnerabilities in its cyber espionage campaigns. One notable instance involved ScarCruft leveraging a zero-day vulnerability in the JScript 9 scripting language (CVE-2022-41128), enabling the group to infect South Korean targets with malware.
Additionally, ScarCruft utilized steganography techniques to distribute malware by exploiting a vulnerability in HWP EPS (Encapsulated PostScript) files. Furthermore, the group employed Flash Player exploits, like CVE-2016-4117, to deliver malware through watering hole attacks.
ScarCruft also targeted vulnerabilities in Microsoft Office applications, such as Word, using them to distribute malware via compromised documents.
What Are the Countries/Industries Targeted by ScarCruft / APT37?
Target Countries:
ScarCruft’s victims have been observed in several countries, including:
- Russia
- Nepal
- South Korea
- China
- India
- Kuwait
- Romania
These countries have reported ScarCruft-related activities and targeted attacks. It is worth noting that ScarCruft primarily targets South Korea, but it has also targeted other Asian countries and organizations with North Korean interests.
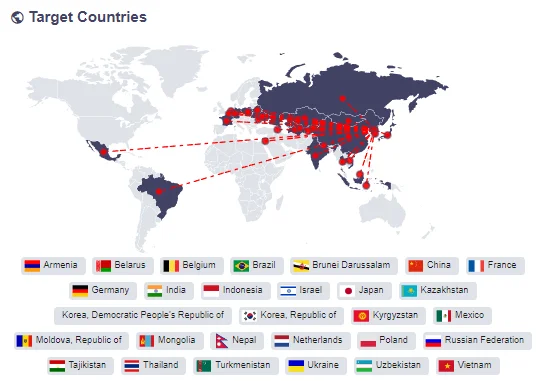
Countries previously targeted by ScarCruft (SOCRadar Threat Actors page)
Target Sectors:
ScarCruft primarily targets sectors and industries that are aligned with North Korea’s interests.
The group’s target industries include government and military organizations, with the goal of gathering intelligence from these bodies, while it directs attacks against various industries in diverse sectors based on North Korea’s interests.
ScarCruft is also known to have targeted individuals associated with North Korea – like academics, novelists, and activists; the group also monitors North Korean defectors and journalists.
Campaigns Related to ScarCruft / APT37

Bing AI illustration of APT threat actors orchestrating a campaign
APT37 (ScarCruft) has been linked to several campaigns and activities. Here are some notable campaigns associated with APT37:
APT37 Campaigns in 2016 – 2018
- Operation Daybreak
- Operation Erebus
- Golden Time
- Evil New Year
- Are you Happy?
- FreeMilk
- North Korean Human Rights
- Evil New Year 2018
NPO Mash Breach (2021)
In a 2021 campaign, ScarCruft breached Russia’s leading missile manufacturer, NPO Mashinostroyeniya (NPO Mash). The attack was not solely attributed to ScarCruft, another known North Korean nation-state threat group, Lazarus, was also involved.
It appeared that the breach commenced in late 2021 and continued until May of the following year – the attackers maintained access for several months before detection. ScarCruft breached the email server, while Lazarus implanted backdoors into NPO Mash’s systems.
And in May 2022, NPO Mash detected a suspicious file, later identified as an OpenCarrot backdoor linked to Lazarus, capable of reconnaissance and file manipulation. ScarCruft was also found compromising NPO Mash’s Linux email server during the incident.
NPO Mash’s appeal as a target lies in its possession of highly classified intellectual property associated with sensitive missile technology, and the attack was regarded as a strategic espionage mission to support North Korea’s missile program – the attack also stands as a recent example of the group’s high-value targeting.
ScarCruft Exploits CVE-2024-38178 to Deploy RokRAT Malware (2024)
North Korean threat actor ScarCruft has been linked to the exploitation of CVE-2024-38178, a now-patched vulnerability in Windows, to install the RokRAT malware.
RokRAT, known for its sophisticated remote access capabilities, can collect data from widely-used applications and evade detection by utilizing cloud services like Dropbox and Google Cloud for Command and Control (C2) operations.
The flaw, which affects the Scripting Engine in Internet Explorer mode of Edge, was patched by Microsoft in August 2024 Patch Tuesday Update. It allows remote code execution if a user clicks a specially crafted URL.
ScarCruft’s continued focus on exploiting browser vulnerabilities highlights their ongoing efforts to target systems in South Korea and beyond.
AhnLab researchers have named this campaign Operation Code on Toast, as ScarCruft exploited a “Toast” application vulnerability used in Korea. This campaign is notable for utilizing a compromised advertisement server to distribute malicious code.
Indicators of Compromise Related to RokRAT
MD5:
- e11bb2478930d0b5f6c473464f2a2b6e
- bd2d599ab51f9068d8c8eccadaca103d
SHA-256:
- 736092b71a9686fde43d3c4abd941a6774721b90b17d946c9d05af19c84df0a4
- 95a19bb2cc53c2ff2edff89161acb9c50ea450fa8a53bbddde2ca3007b1a1345
SHA-1:
- 9a17d9b44af34aca4e94242c54e001d761993763
- f0891b2fd83037f982acfaac17dcd77b091534db
Conclusion
Since its inception in 2012, ScarCruft has demonstrated a profound interest in targeting high-value individuals and institutions, primarily centered around South Korea but extending its reach to other Asian nations aligned with North Korea’s counterintelligence interests.
The group’s modus operandi involves targeting government, military bodies, various industries, as well as individuals associated with North Korean concerns, showcasing their broad spectrum of interests and objectives. Employing watering-hole attacks, zero-day exploits, and spear-phishing tactics, ScarCruft infiltrates systems to install backdoors and conduct reconnaissance.
The recent campaign involving ScarCruft’s breach of Russia’s leading missile manufacturer, NPO Mashinostroyeniya (NPO Mash), highlights the group’s evolving tactics and strategic focus. Collaborating with Lazarus, another North Korean nation-state threat group, ScarCruft orchestrated a sophisticated attack, maintaining access for several months before detection.
In essence, ScarCruft’s operations epitomize the evolving landscape of cyber espionage, posing significant challenges to the cybersecurity of government organizations and more worldwide. As ScarCruft continues to refine its tactics and expand its sphere of influence, vigilance, and collaboration among security communities remain critical in mitigating the threat posed by this sophisticated adversary and alikes.
Recommendations: Guarding Against ScarCruft
To protect against ScarCruft (APT37) and mitigate the risk of their cyber espionage activities, here are some recommendations:
- Keep software up to date: Regularly update operating systems, applications, and security patches to address known vulnerabilities. APT37 has been known to exploit zero-day vulnerabilities, so staying up to date is crucial.
- Implement strong security measures: Deploy robust security solutions, including firewalls, intrusion detection systems, and antivirus software. Regularly update and configure these tools to ensure they provide effective protection against known threats.
- Enable Multi-Factor Authentication (MFA): Implement MFA for critical accounts and systems to add an extra layer of security. This helps prevent unauthorized access even if passwords are compromised.
- Educate employees: Conduct regular security awareness training to educate employees about phishing attacks, social engineering techniques, and safe browsing habits. APT37 often uses spear-phishing emails as an initial attack vector.
- Monitor network traffic: Implement network monitoring tools to detect suspicious activities and anomalies. Monitor for any signs of unauthorized access, data exfiltration, or unusual network behavior.
- Implement strong access controls: Restrict user privileges and implement the principle of least privilege. Limit access to sensitive systems and data to only those who require it.
- Regularly back up data: Maintain regular backups of critical data and ensure they are stored securely. This helps mitigate the impact of potential data breaches or ransomware attacks.
- Establish an incident response plan: Develop an incident response plan that outlines the steps to be taken in the event of a security incident. This will help minimize the impact and facilitate a swift response.
These recommendations serve as general cybersecurity best practices and may not comprehensively counter all tactics employed by APT37; to directly address the threats they may face, organizations must remain vigilant and stay informed about the latest threat intelligence, and use advanced platforms like SOCRadar to monitor their attack surface.
You can elevate your organization’s security strategy with SOCRadar’s insights – The SOCRadar XTI platform, with its Cyber Threat Intelligence capabilities, can assist you stay ahead of emerging threats posed by threat actors like ScarCruft, ensuring your defenses are continuously fortified and updated against evolving risks.
MITRE ATT&CK TTPs of ScarCruft / APT37
Indicators of Compromise (IoCs) Related to ScarCruft / APT37
The Indicators of Compromise of ScarCruft (APT37), as listed by Zscaler, are as follows:
Archive File Hashes
| MD5 hash | Archive filename |
| 3dd12d67844b047486740405ae96f1a4 | (20220120)2022년 총동창회 신년인사001.rar |
| e9cd4c60582a587416c4807c890f8a5b | (양식) 제20대 대통령 취임식 재외동포 참석자 추천 명단(국민의힘당원 000).rar |
| 6dc7795dde643aae9ced8e22db335ad1 | 1.rar |
| e3879ea3f695706dfc3fc1fb68c6241d | 2017-APEC.rar |
| 17bc6298bf72fa76ad6e3f29536e2f13 | 2022 후기 신-편입생 모집요강.rar |
| 54a99efd1b9adec5dc0096c624f21660 | 2022-01-27-notification.rar |
| f3f4cf7876817b1e8a2d49fe9bd7b206 | 2022-03-22.rar |
| bb182e47e1ffc0e8335b3263112ffdb1 | 2022-04-14.rar |
| 9d85c8378b5f1edefb1e9837b3abb74f | 2022.04.27.rar |
| cb33ef9c824d16ff23af4e01f017e648 | 2022.rar |
| 75fe480a0669e80369eaf640857c27cd | 20220315-112_Notice.rar |
| 6db5f68b74c8ba397104da419fcc831d | 202203_5_06.rar |
| cfd73942f61fbb14dded15f3d0c92f4a | 20220510_115155.rar |
| 5c67c9266e4267d1bf0862bf2c7bd2a5 | 20220913.rar |
| 1531bba6a8028d38d36c0a91b91159c3 | 20220916093205755684_TSA.rar |
| afdc59ec36ac950de08169162783accd | 2022년 국방부 부임이사 안내(몽골리아).rar |
| 06c112968cdde43c3424bdf0a2a00928 | 20230302_Guide.rar |
| 6ab401c83095129a182b9be0359d602d | 3사복지업무.rar |
| 93e94b673c6d1ea6d615c0102dc77610 | Ambassador Schedule Week 6 2023.rar |
| e32f59fd5acbe01d2171ba6c2f24e3ca | Announcement.rar |
| 7b60dc663e1025e8892b96fa9fc34f00 | BoanMail.rar |
| 5e95023c6ac3f3fefe00cfc2b4b1d093 | CR_20230126.rar |
| 353370ade2a2491c29f20f07860cf492 | CV.rar |
| 120a677df1c4d1f0792b6547d3b60183 | DBLife-2022_08_05.rar |
| 02baa23f3baecdc29d96bffea165191b | Details.rar |
| c3325c43b6eea2510f9c9f1df7b7ce22 | Documents.rar |
| 04a7290e04fd1855140373aa3d453cef | DriverSet.rar |
| 87c3e8e4308aac42fed82de86b0d4cb6 | Estimate.rar |
| 328dc6e7acce35abaaf3811bac2bc838 | H2O 견적서.rar |
| e9230cf7615338ab037719646d67351b | HealthDoc.rar |
| cf012ca48b5e1f6743be7e0d10cdfd2e | Introduce.rar |
| 34d3e5306cff0bfe831ccd89d095ef33 | Invoice_1514_from_Evo3_Marketing_Inc.rar |
| 717dab257423d5fd93d0d02f3ff242e7 | KB_20220111.rar |
| 0164d8a2d27cfd312fb709c60c351850 | KB_20230126.rar |
| c23c17756e5ccf9543ea4fb9eb342fde | KN0408_045 정영호.rar |
| 31793153b12f1187287007578017abd4 | KakaoTalk_20220419_103447534.rar |
| 030df9bca0a35bcd88d5897482ee226d | LG유플러스_이동통신_202207_이_선.rar |
| 8eb56493d984b3c2fa4c2dedb6871dd7 | LG유플러스_이동통신_202208_이_선.rar |
| 0c2375825dcae816a1f9b53f8f82d705 | MAIL_20230125151802.rar |
| 93817f6dfe3a7596eeef049eda9c8b18 | Message.rar |
| 3fe6722cd256d6d5e1d5f5003d6a01a5 | NTS_eTaxInvoice.rar |
| c1b6390f0ef992571fa9ed3c47eb0883 | News about Foreign affairs, The High North and Ukraine.rar |
| 6dc7795dde643aae9ced8e22db335ad1 | Oxygen_Generator.rar |
| 3b52f149e220da28bf9cd719570979ce | Payment.rar |
| e5c509a33db926f3087c3a52546b71f2 | Provincil’s letter.rar |
| d5ad2c1790c715d88b5e05ca4329417d | References.rar |
| 4d27d6b01f85a4b40650e6bc7cc18ed3 | SamsungLife.rar |
| 3a4f4b1fb30fbb70c14dea600a56ca68 | SecureMail.rar |
| 5a8bdfb0008767cdb05dfcc3223e9a70 | TermsOfService.rar |
| 881ccfd6c11b774b80b304ab78efef53 | Transaction.rar |
| f2be2c1e80769a45761d0b69a46a627f | TransactionGuide.rar |
| f7a73eaf15ee8d8f3257a359af5987eb | WooriCard_14day_20220609.rar |
| b6c4137868e2c305241093e967b2d60b | WooriCard_20211222.rar |
| 715d408b45e5334a985e7e6279fa80ac | WooriCard_20220401.rar |
| b2ce0ba21ae1e982a3a33a676c958bec | XQQ-2022-D27.rar |
| b9f423b42df0df0cb5209973345d267c | [INSS] National Security and Strategy (Winter 2022).rar |
| ab0dc3964a203eea96a233c8d068de95 | [붙임] 제20대 대통령선거 제1차 정책토론회 시청 안내문.rar |
| fbc339cd3f4d39af108b4fdb70202b22 | boanmail-202101-j08.rar |
| fbc339cd3f4d39af108b4fdb70202b22 | boanmail_202201_2_505824.rar |
| 0db43beb06845026cf33c59baa66b393 | boanmail_202201_5_02-10424.rar |
| 237bcbe07219eb24104815205cc01d24 | boanmail_202201_5_80222982.rar |
| 2bf05e2526911b3bdb7f77cbbe4155f3 | db-fi.rar |
| 0923c69808352feb9a57a766c611b7d4 | dbins_secure.rar |
| 8c3bb54dcd4704a0f0b307863345c5d1 | email_1649225531086.rar |
| 0947efee85596a17bdd1e798826d48aa | enkis.rar |
| 93675086f33fb0708982eafea5568f05 | final exam questions 2022 summer KED.rar |
| 8faabae5e6766a6a93a56014cca5c295 | hi_security_mail.rar |
| 9e7099b32f6bd36724a71f6c3cb21d17 | issue.rar |
| 9c6d553682813724424a7fcc7af8729d | mmexport1638437859483.rar |
| 6da10cc37edee7e16c520f2f95cd9304 | pay_202111_5_00-10290.rar |
| f07a3d146f32bfa8f53e5cae7178559e | pay_202111_5_01-10104.rar |
| 0beeb858734cd7da03b1284e7fe00b22 | pay_202111_5_02-12972.rar |
| 8c4cbe900cf69c739882cef844b1ac11 | pay_202111_5_04-10220.rar |
| 31da11dbf80715138261904b2249a7f8 | pay_202111_5_04-14213.rar |
| 1803d81e1d0ccb91c752ecb4bc3b6f0c | pay_202111_5_12-11985.rar |
| 06b7207879bd9ed42b323e16bb757a3c | pay_202202_5_06-10325.rar |
| 28b807be70e49ebc0c65455f430d6408 | pay_202205_5_01-10104.rar |
| c97a32c7555fc81f296fee0a65fec079 | pay_202209_5_01-502479.rar |
| 1e05dbe1846c1704b9a7a1db13fdd976 | samsungfire.rar |
| 38d9ff50b68144a9a40d1e7e3d06adb0 | security-guide.rar |
| f0b7abea21984790d2906adf9653c542 | securityMail.rar |
| 04802790b64d66b9257ae119ee7d39a5 | security_20220813.rar |
| a8bcbb34e11d7b23721ec07eadb5ddc5 | shinhancard_20220218.rar |
| eecf78848dde0d41075e35d3aa404697 | 제39기 모집요강 및 입학지원서-재송.rar |
| ef5aa1dfbfc4c9128a971e006da0cb8b | 새로 바뀐 COVID-19 시기 자가격리 정책.rar |
| e5865d8cee159ac02ee53ef52f4058ac | 오피스 365 + 설치설명서 입니다.rar |
| 882d4d6528404c3ceacee099f59bfab4 | 텅스텐 W 99.rar |
| b7275a3931fb85f723a4ceec9478c89e | 다문화 문제 답.rar |
| f96fa367261df9cc2b021318ce361ec6 | 취임식 관련 자료.rar |
| 8d7141882a95be5dcfa8ce90d7079541 | 공고문(기술관리).rar |
| ff2ccc12007bbf3f5934a5dfdc8430ee | 황선국-차예실의 요르단 이야기-34.rar |
| 3c3fc3f47abf0ec7a3ab797b21b123e2 | 공고문.rar |
| acf9bad00bc1d2649ad918b0524c7761 | 계약사항 안내문.rar |
| cb33ef9c824d16ff23af4e01f017e648 | 문의사항.rar |
| 802bf381dd7f7f6cea077ab2a1814027 | 보안메일.rar |
| 89d1888d36ff615adf46c317c606905e | 협조요청.rar |
| 0d15b99583b3b9638b2c7976b4a1d2ef | 통일교육11.rar |
| 8113798acc4d5690712d28b39a7bb13a | 백산연구소 (830 LNG) 22.01.17.rar |
| 4987ed60bb047d4ca660142b05556125 | 백산연구원 소방서.rar |
| b840485840480d42b3b8e576eecdf2ee | 제로깅크루_명단.rar |
| e8ab4f80ebad24260869e89bca69957d | 폴리프라자Ⅲ, 4월 근무 현황.rar |
| 87aaf50fc5024b5e18f47c50147528b4 | 조성호기자님_마키노기자책소개.rar |
| 11b0c0577e12400cddc7b62b763a1dd1 | 사업유치제의서-PC모듈러pdf.rar |
| fa797b29229613f054378c8a32fcefbc | 통일미래최고위과정_입학지원서.rar |
CHM File Hashes:
| MD5 hash | Filename |
| 914521cb6b4846b2c0e85588d5224ba2 | (20220120)2022 – 001.chm |
| 2ffcb634118aaa6154395374f0c66010 | (양식) 제20대 대통령 취임식 재외동포 참석자 추천 명단(국민의힘당원 000).chm |
| 24daf49d81008da00c961091cbfc8438 | 0-Introduction.chm |
| 624567dae70fc684b2a80b5f0f1de46d | 1.Brefing.chm |
| 2ab575f9785239d59395ec501ceaec2e | 2017 – APEC.chm |
| 684a61eedb2ec26d663c3d42a107f281 | 2022 – Guide.chm |
| a48ac5efd350341beab9a4fdfb7f68d7 | 2022-01-27-notification.chm |
| 030c3873f1a45eab56dca00fa8fa9a14 | 2022-04-14.chm |
| a6b30fc17d6ff9aa84fb93c3f05a4171 | 2022-06-24-Document.chm |
| b4adb4fede9025f6dd85faac072a02e7 | 2022-Important.chm |
| b2d7c047dc1c7fb7074111128594c36e | 2022.04.27.chm |
| edb87c2cabcc402173fa0153f4e8ae26 | 2022.chm |
| d020d573d28e3febb899446e3a65e025 | 20220315-112_Notice.chm |
| 7058661c3f944f868e5a47c4440daa9b | 20220510_115155.chm |
| d431c37057303e5609f0bffa83874402 | 20220623103203983_6_조사표_기업용.chm |
| 820d302655d5cd5dd67859f7a5cb74fe | 20220913_Main.chm |
| 8db5578f5245c805c785ae38ea8a1363 | 20220916_Password.chm |
| c29d11961b9662a8cb1c7edd47d94ae5 | 20230302_Guide.chm |
| cae4d578b1bdaa4e193095f035cecbc6 | Account Information.chm |
| 9bf4576a1381c15c08060ca6cfd59949 | BoanMail.chm |
| c0bfb9f408263c1bc574a08fa164a61f | BookBriefing.chm |
| e9562655c36d46f4b6534f189ae453a0 | Content-Introducing.chm |
| 6bd63cf73cab3305686f2ee41d69bd42 | Covid-19-Notice20211028.chm |
| 012f0dd04c9c810c14cdde08cfbca3c5 | DBLife-2022_08_05.chm |
| 00a7c9ad2e975e19034838a14f73a46a | Details.chm |
| 77a6f57ccefeda14d5faf44cc37b69da | Estimate.chm |
| 211b412fe5c4b207eb39384499b93342 | H2O Note.chm |
| 3a23ee36f792e241772e81aeeccf8aa8 | Introduce.chm |
| 532ec6d88c728afecfcf8fbb38fb8add | Invoice_1514_from_Evo3_Marketing_Inc.chm |
| 2a982b843cf92081fc4202e11a1f7234 | KB_20220111.chm |
| aa68044e16a115af4ea1de3d062c4e41 | KB_20230126.chm |
| 0bf53a165b2bd64be31093fefbb9fb51 | KakaoTalk_20220419_103447534.chm |
| f11b9fb8208b9949859785810f251334 | KakoBank-N202111.chm |
| 097edc04368d411593fff1f49c2e1d9c | LG유플러스_이동통신_202207_이_선.chm |
| 45bd3001517f5e913ddde83827f4cc29 | MAIL_20230125151802.chm |
| 0bf993c36aac528135749ec494f96e96 | Message.chm |
| 549162b9ec4c80f9a0ca410ff29c8e98 | NTS_eTaxInvoice.chm |
| c09939e972432968976efc22f556bd0f | News about Foreign affairs, The High North and Ukraine.chm |
| 79d5af9d4826f66090e4daf6029ed643 | Password.chm |
| 9e1a2b331fd1e4ee77880d8f62025cd1 | Password12.chm |
| 5f2dcb1e51c8d574f43c8f7c7f84d9fa | Related to the inauguration ceremony.chm |
| a5ce8fe31da94fdea9c25f3abcdd5982 | SamsungLife.chm |
| 8a74a931e6ed4ae477547707da2fd76c | SecureMail.chm |
| 0012f5bfe97421d39751eb20d857ae09 | TermsOfService.chm |
| 22652b383d9ea880a4644a35cd5fadaf | Transaction.chm |
| 73715c82e31702f56858226557f98444 | WooriCard_14day_20220609.chm |
| b34761f5272c9109c47780f415d28631 | WooriCard_20211222.chm |
| 2c697d27cd2e455ae18b6744a47eef4f | WooriCard_20220401.chm |
| 2cf2805529ebc68884979e582e12cf8d | XQQ-2022-D27.chm |
| 67cc91e889b4a597a6486db0e92fa4d1 | [INSS] Briefing and Guide.chm |
| 1f4038a9c6266b60f784c37efbb832f5 | [붙임] 제20대 대통령선거 제1차 정책토론회 시청 안내문.chm |
| ac7f8e5245f9736a1323509a537e54eb | baeksan (830 LNG) 22.01.17.chm |
| ee06a0d6e5645248db88c279ec0e8624 | contents.chm |
| a13fb4e11b31d109a1b145f20ea4b929 | db-fi.chm |
| 0fb698efce9476c3f2b603b30f5e35d5 | dbins_secure.chm |
| d942353d15077352dcae83dd04869e1a | email_1649225531086.chm |
| ac51f29d609c73cce8db67c86aa49ba0 | enkis_choe.chm |
| 7f030cbf7ce41b9eb15693ee92b637a5 | hi_security_mail.chm |
| a85dc5403cb1fe7d0ae692a431e1eae3 | issue.chm |
| 5e2e5b71503adedf786bc69f3849750f | jungsan_202203_5_06-10325.chm |
| 7cba0c911b74d889f05f8b954926aa67 | jungsananne_202201_2_505824.chm |
| 174ae3db1dd4c61037bc7a5bf71d1366 | jungsananne_202201_5_02-10424.chm |
| 498b20e20af190c6650f03e8adf9a5b7 | jungsananne_202201_5_80222982.chm |
| 92974d1677fa840fcc3d6599df86d38f | mmexport1638437859483.chm |
| 19c0583e57385f574c9986de6a26adae | pay_202111_5_00-10290.chm |
| e73b6c906f1070d569a0e9b70304be01 | pay_202111_5_01-10104.chm |
| b1d2c6233d56ef3aeaa08cff7a7d2971 | pay_202111_5_02-12972.chm |
| c0d25429f924016765711cd860fd03f9 | pay_202111_5_04-10220.chm |
| 8a5e7f281b51c2b9e364c26e3f699019 | pay_202111_5_04-14213.chm |
| faf6139671f07db49056f4e0470ab188 | pay_202111_5_12-11985.chm |
| a372e8dfd1940ef4f9e74095a8bf3bd7 | pay_202201_2_505824.chm |
| 561b29a5650ff7fe6e63fa19c29ee240 | pay_202201_5_02-10424.chm |
| 093ad28a08314e8fe79c26828137ab0a | pay_202201_5_80222982.chm |
| d32ccdcf79932dd9d7eaf4fd75bfade2 | pay_202202_5_06-10325.chm |
| deed5eb8b19dae07720e97b485a5f1e4 | pay_202203_5_06-10325.chm |
| 886702585a3951882801b9eecb76c604 | pay_202205_5_01-10104.chm |
| 6ac4b333e6d7f64aee5c32e20d624f2e | pay_202209_5_01-502479.chm |
| 441adf67527915c09cfe29727b111a6a | samsungfire.chm |
| 122208301a3727c5fc7794ff0f7947bf | security-guide.chm |
| 79e158af8ded991ee95a0f10654576ce | securityMail.chm |
| e7104d3e388530a43623981138112e03 | security_20220813.chm |
| af89179ef2c8365ca413fed8553159fa | shinhancard_20220218.chm |
| b7b1095620b8629c73191d5c05afc446 | z email content.chm |
| 681a21cb83e82da88f42f9fb0dd764b6 | 다문화 문제 답-추가.chm |
| 5f2dcb1e51c8d574f43c8f7c7f84d9fa | 취임식 관련 자료.chm |
| 72a38aa3e128d2ffca141a41a4101dca | 황선국-차예실의 요르단 이야기-34.chm |
| 632104e97870c1177c211f5e2d963b75 | 요약문.chm |
| ffba3072600a1f06d260137f82371227 | 공지사항.chm |
| e557693cc879beeb1a455cac02724ea7 | 보안메일.chm |
| 71389f565a5ebe573c94d688fa6f23ea | 통일교육11.chm |
| 920ccffa488d2b0e9aa19acc5f31fc3a | 제로깅크루_명단.chm |
| 7c53f15614d5f9cf2791cb31811893a7 | 폴리프라자Ⅲ, 4월 근무 현황.chm |
| fb60a976bbed174effa6081a35abee87 | 사업유치제의서-목차.chm |
| bca3f0b4a5a1cbcd3efa1ca0df7f0d4b | 통일미래최고위과정_입학지원서.chm |
LNK Files:
| MD5 hash | Filename |
| eb7a6e3dc8bbc26f208c511ec7ee1d4c | LG유플러스_이동통신_202208_이_선.html.lnk |
| c5f954436e9623204ed961b9b33e769d | 계약사항 안내문_1.pdf.lnk |



































