
Top 10 Advanced Persistent Threat (APT) Groups That Dominated 2024
Advanced Persistent Threats (APTs) are among the most sophisticated and persistent cyber adversaries in the world. Unlike ordinary cybercriminals, APT groups are usually state-sponsored or highly organized entities that engage in long-term espionage, data theft, and sabotage. Their operations use advanced tactics, techniques, and procedures (TTPs) to target governments, critical infrastructure, and major corporations.
APTs are not opportunistic hackers looking for quick wins; instead, they use advanced malware, zero-day exploits, and social engineering techniques to infiltrate high-value networks. Their ability to go undetected for months or even years makes them one of the most dangerous threats to cybersecurity.
Why You Need to Know About APT Groups
Awareness of APT groups and their tactics is critical for cybersecurity professionals, business leaders, and government agencies. These organizations pose a significant threat to sensitive information, national security, and business operations. Understanding their strategies allows organizations to implement stronger security measures, develop proactive defense mechanisms, and respond effectively to potential threats. Understanding APT activities aids in identifying vulnerabilities, mitigating risks, and staying ahead of emerging cyber threats.
By staying informed about APT operations, organizations can:
- Identify and mitigate vulnerabilities before they are exploited.
- Recognize tactics and techniques used by known adversaries.
- Strengthen cybersecurity postures with targeted defense strategies.
- Implement threat intelligence solutions to detect and respond to APT activities.
SOCRadar Labs provides detailed intelligence on the latest APT activities, attack vectors, and malware trends. Explore our Threat Actor Intelligence page to stay ahead of cyber adversaries:
SOCRadar Labs Threat Actor page
With actionable intelligence, organizations can proactively defend against APT threats and safeguard their digital assets.
As cyber warfare continues to evolve, knowledge of APT activity is no longer optional—it’s essential for resilience and proactive defense. Here are the top APT groups shaping the global threat landscape in 2024.
1. Salt Typhoon
Salt Typhoon, a Chinese state-sponsored APT, has been active since 2020 and is linked to China’s Ministry of State Security. Known by names like GhostEmperor and FamousSparrow, the group focuses on infiltrating critical communication networks and exfiltrating sensitive data. In 2024, its activities have intensified, with a primary focus on the telecommunications sector, exploiting zero-day vulnerabilities to maintain long-term persistence in compromised systems.

Read more about Salt Typhoon
Notable Attacks in 2024
A major breach in 2024 saw Salt Typhoon infiltrating U.S. Internet Service Providers (ISPs) such as AT&T and Verizon. The group compromised court-authorized wiretap systems, granting unauthorized access to sensitive communications. In November 2024, the group expanded its operations to T-Mobile, targeting customer call records and metadata. These breaches raised significant concerns about national security, as they allowed the threat actors to monitor and manipulate communications on a large scale.
The exposure of these breaches led to an immediate response from U.S. authorities, including the FBI, NSA, and CISA, which worked to mitigate the impact and prevent further infiltration. The Cybersecurity and Infrastructure Security Agency (CISA) issued updated security protocols urging telecommunication providers to adopt stronger network segmentation, access controls, and traffic monitoring to counter future threats.
U.S. Senator Mark Warner called the Salt Typhoon campaign the “worst telecom hack in U.S. history,” highlighting its severe national security implications. While the breach initially affected fewer than 150 victims, millions of related contacts are now at risk, emphasizing the far-reaching consequences of such attacks.
2. Lazarus Group
The Lazarus Group, a North Korean state-sponsored APT, is one of the most notorious cyber adversaries, known for its espionage, financial theft, and disruptive attacks. Attributed to North Korea’s Reconnaissance General Bureau (RGB), Lazarus has been active since at least 2009, carrying out operations aligned with the country’s strategic and financial objectives.
Unlike many APTs focused solely on intelligence gathering, Lazarus prioritizes financial gain, executing large-scale cyber heists, ransomware campaigns, and cryptocurrency thefts.

Read more about Lazarus Group
Notable Attacks in 2024
In 2024, the group ramped up its attacks, utilizing Operation DreamJob, which used CookiePlus malware to target the nuclear sector, and Operation 99, which infiltrated Web3 and cryptocurrency developers through fake recruitment campaigns on platforms such as LinkedIn.
Lazarus is also allegedly responsible for high-profile cryptocurrency heists, such as the WazirX Exchange breach in July 2024, when the group stole $230 million, and the DMM Bitcoin attack in Japan, which resulted in a $308 million theft. The group continues to use social engineering, zero-day exploits, and advanced malware to compromise financial institutions and steal digital assets.
In early 2024, Lazarus exploited CVE-2024-4947, a Google Chrome zero-day vulnerability, in its DeTankZone campaign, a sophisticated operation that tricked cryptocurrency traders into downloading malicious software. The exploit allowed Lazarus to steal sensitive financial data, reinforcing its reputation as a leading cybercriminal organization.
As one of the most aggressive and financially motivated APTs, Lazarus remains a top concern for cybersecurity professionals. Organizations must prioritize threat intelligence, network security, and proactive countermeasures to defend against Lazarus’s evolving cyber threats.
3. APT31
APT31, also known as ZIRCONIUM or Judgment Panda, is a Chinese state-sponsored APT group engaged in cyber espionage and intelligence gathering on behalf of China’s national interests. The group is known for its sophisticated spear-phishing campaigns, malware deployment, and exploitation of zero-day vulnerabilities to target governments, businesses, and political entities worldwide.

Read more about APT31
Notable Attacks in 2024
In March 2024, the U.S. Department of Justice (DOJ) unsealed an indictment against seven individuals linked to APT31, charging them with conspiracy to commit cyber intrusions and wire fraud. These operatives, believed to be working under China’s Ministry of State Security (MSS), allegedly targeted U.S. businesses, political officials, and critics of the Chinese government through a highly coordinated 14-year-long espionage campaign.
APT31 employs dual-phase cyber tactics, collecting initial data on victims through fake news articles embedded with tracking links, which is then used for sophisticated network intrusions. The group has targeted political figures, election campaign staff, and US companies, with a focus on economic espionage, intellectual property theft, and transnational repression.
Silobreaker connects APT31 to collaborations with APT27, another Chinese threat actor, in the EastWind campaign targeting Russia’s government and IT sectors in August 2024. According to reports, APT31 shares cyber infrastructure, such as the FLORAHOX relay network, with other Chinese cyber-espionage groups to improve operational anonymity.
4. APT41
APT41, also known as Double Dragon, is a Chinese state-sponsored APT group that uniquely engages in both espionage and financially motivated cybercrime. Unlike most Chinese APTs that focus solely on intelligence gathering, APT41 has been implicated in large-scale cyber heists, targeting both government institutions and private enterprises.
Notable Attacks in 2024
APT41 has expanded its arsenal in 2024, deploying advanced malware such as DodgeBox and MoonWalk. DodgeBox employs DLL sideloading, DLL hollowing, and call stack spoofing to evade detection, while MoonWalk leverages Windows Fibers and Google Drive for command-and-control (C2) communication. These new tools demonstrate APT41’s continued evolution in evasion techniques and persistence.
The group also remains active in KEYPLUG malware attacks, targeting Italian organizations and government entities. Additionally, APT41 continues to utilize ShadowPad malware and Cobalt Strike, which were deployed in a Taiwanese government-affiliated research institute breach that started in mid-2023.
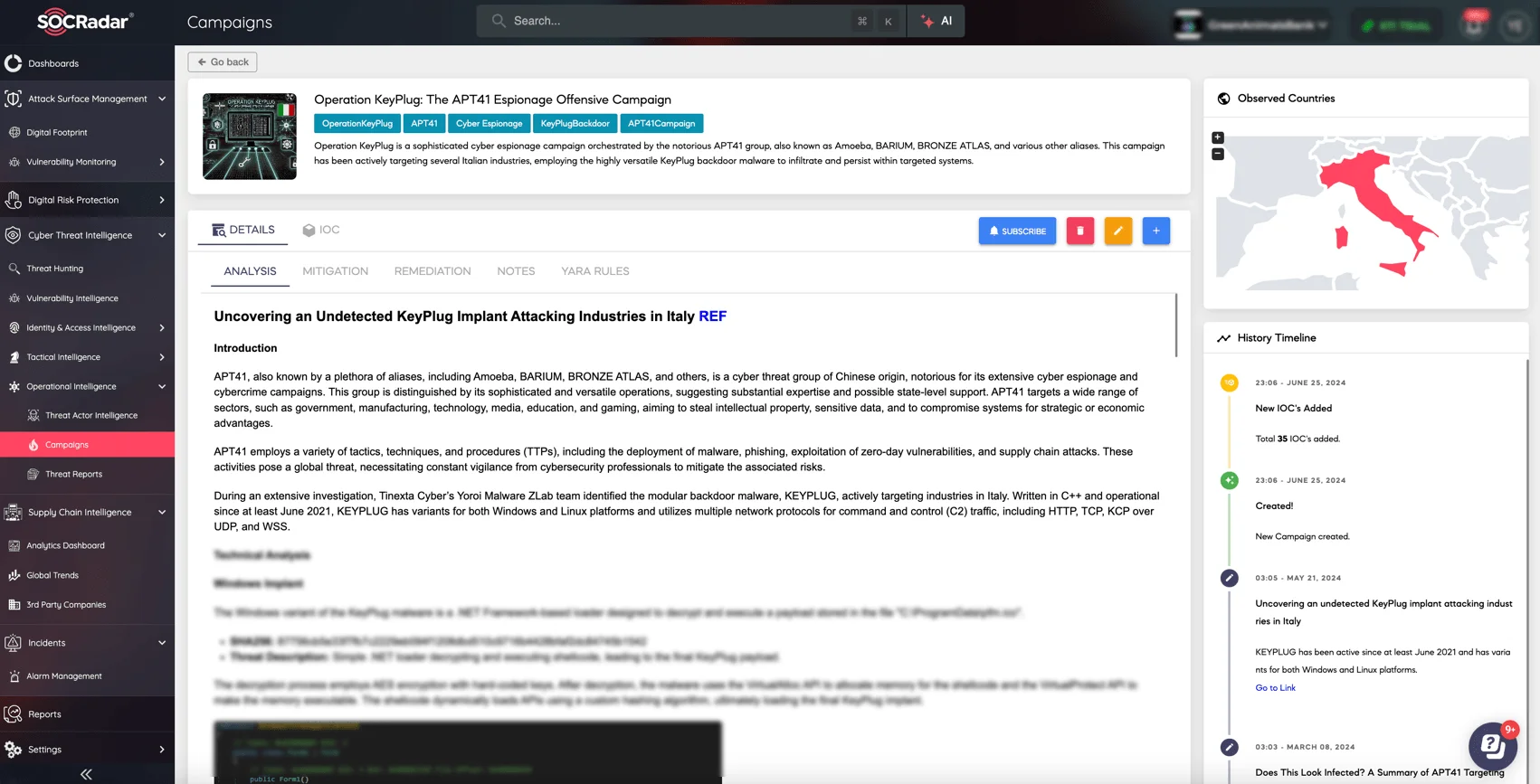
Details of APT41 Operation KEYPLUG on SOCRadar XTI platform’s Campaigns page
APT41’s operations demonstrate its ability to conduct both state-sponsored espionage and independent financial cybercrime, making it a uniquely versatile and dangerous threat actor in 2024. Organizations must monitor its evolving TTPs and implement robust cybersecurity defenses to counter its attacks effectively.
5. Kimsuky
Kimsuky, also known as APT43, is a North Korean cyber-espionage group that has been active since 2013. The group primarily targets South Korea, the United States, and Europe, focusing on intelligence gathering, particularly in political and military sectors.
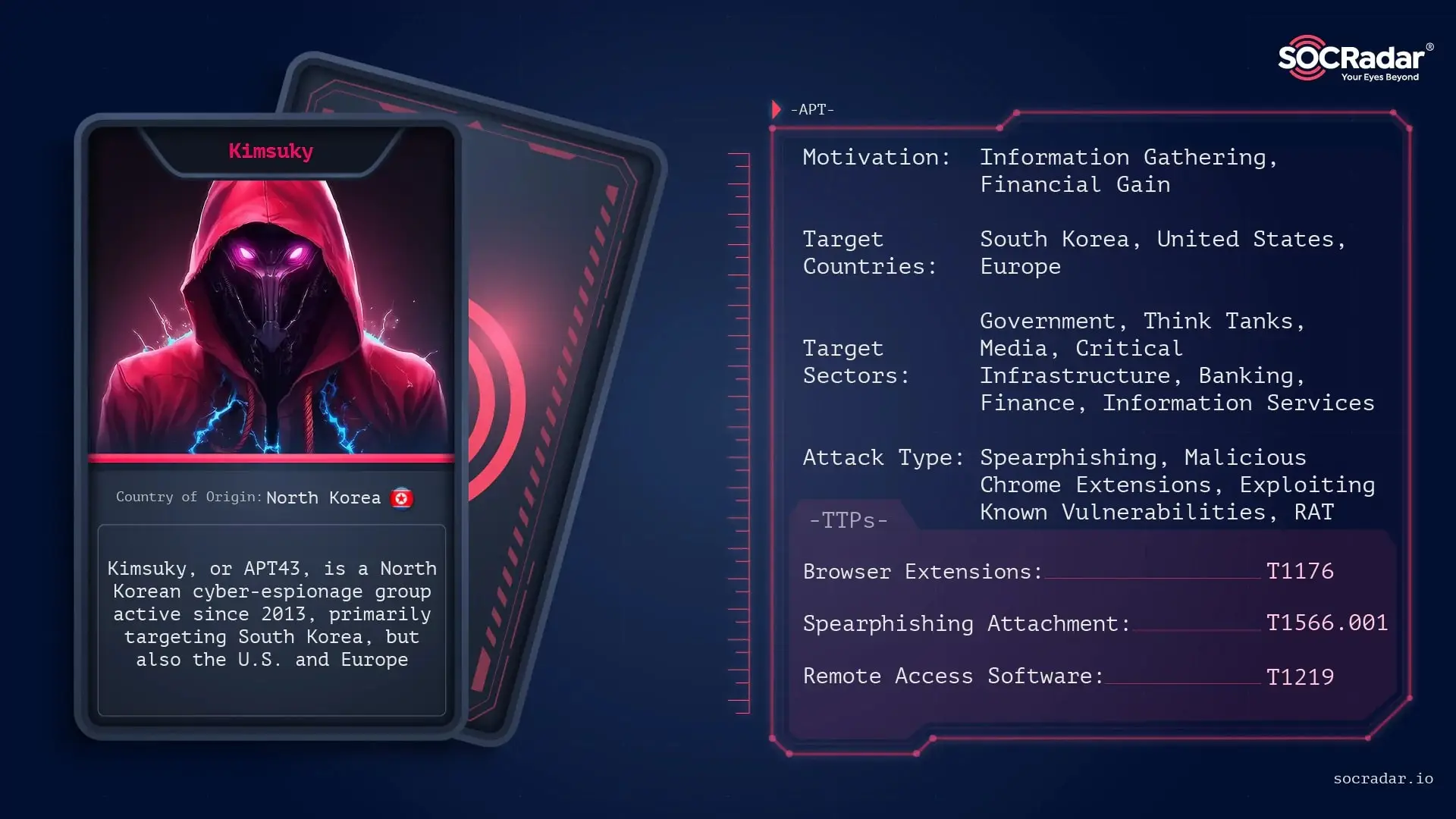
Read more about Kimsuky
Notable Attacks in 2024
In 2024, Kimsuky evolved its tactics by shifting towards malwareless attacks to evade Endpoint Detection and Response (EDR) solutions. Instead of deploying malware, the group increasingly relies on credential-harvesting phishing campaigns that impersonate trusted institutions such as government agencies and financial entities. These phishing attacks use deceptive domains, such as naverbox.pe[.]kr and evangelia[.]edu, to trick victims into providing sensitive login credentials.
Kimsuky has also been linked to the Sparkling Pisces campaign, which introduced two newly discovered malware variants: KLogEXE and FPSpy. KLogEXE is an advanced keylogger capable of capturing keystrokes and monitoring user activity, while FPSpy is a sophisticated backdoor designed for long-term persistence and data exfiltration. These tools highlight Kimsuky’s continuous evolution and growing technical sophistication.
Security researchers warn that Kimsuky remains a persistent and evolving threat, emphasizing the need for organizations to enhance email security, implement Multi-Factor Authentication (MFA), and conduct regular security awareness training to mitigate phishing risks.
6. APT29
APT29, also known as Cozy Bear, is a Russian cyber-espionage APT group associated with Russia’s Foreign Intelligence Service (SVR). The group has been active since at least 2008 and is known for targeting governments, diplomatic entities, and critical industries across the United States and Europe.

Read more about APT29
Notable Attacks in 2024
In 2024, APT29 launched several high-profile campaigns, including the exploitation of WinRAR vulnerabilities (CVE-2023-38831) to infiltrate European embassies. The group also leveraged malware such as WINELOADER to target German political parties and conducted phishing campaigns using Microsoft Teams chats to steal credentials from government and NGO employees.
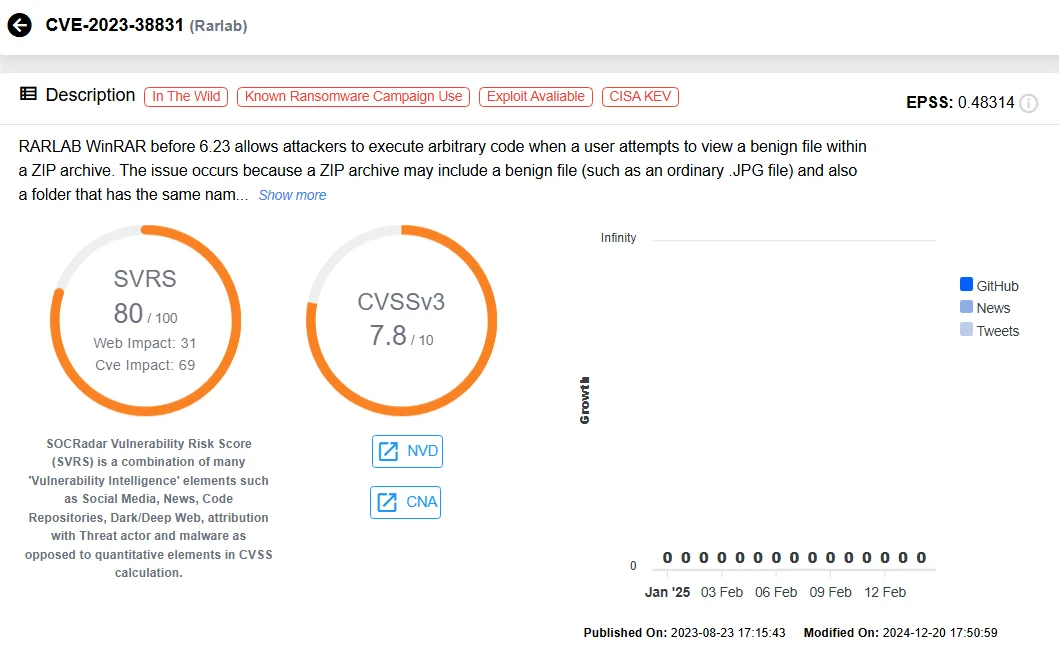
Vulnerability card of CVE-2023-38831 (SOCRadar Vulnerability Intelligence)
A significant escalation of APT29’s operations came in early 2024, when the group was linked to a large-scale espionage campaign targeting Ukrainian state and military agencies, as well as industrial enterprises. According to AWS and Ukraine’s CERT-UA, the hackers used phishing emails disguised as messages from Amazon or Microsoft to steal Windows credentials. These attacks granted access to victims’ disks, network resources, printers, audio devices, and clipboard data, allowing APT29 to execute third-party programs or scripts remotely.
Unlike its usual narrowly focused spear-phishing tactics, APT29 expanded its phishing operations to a wider set of targets in this campaign. The attackers used deceptive domain names mimicking AWS to lure victims into revealing their credentials. AWS, in response, seized the domains abused in the operation to disrupt APT29’s infrastructure.
Additionally, between November 2023 and July 2024, APT29 conducted a watering hole attack against Mongolian government websites, including cabinet[.]gov[.]mn and mfa[.]gov[.]mn. The attackers leveraged iOS WebKit (CVE-2023-41993) and Chrome exploit chains (CVE-2024-5274 & CVE-2024-4671) to compromise unpatched devices. The iOS attack used a cookie stealer framework to exfiltrate browser data, while the Chrome exploit leveraged obfuscated JavaScript and sandbox escapes to steal login credentials, account data, and browsing history.
7. Star Blizzard
Star Blizzard, formerly known as SEABORGIUM and Callisto Group, is a Russian state-sponsored APT linked to the Federal Security Service (FSB). The group has been active since at least 2019, conducting long-term espionage campaigns against NATO countries, think tanks, defense entities, academia, NGOs, and governmental organizations. Star Blizzard is known for its highly targeted spear-phishing attacks, using social engineering, fake domains, and email impersonation to infiltrate high-value targets.
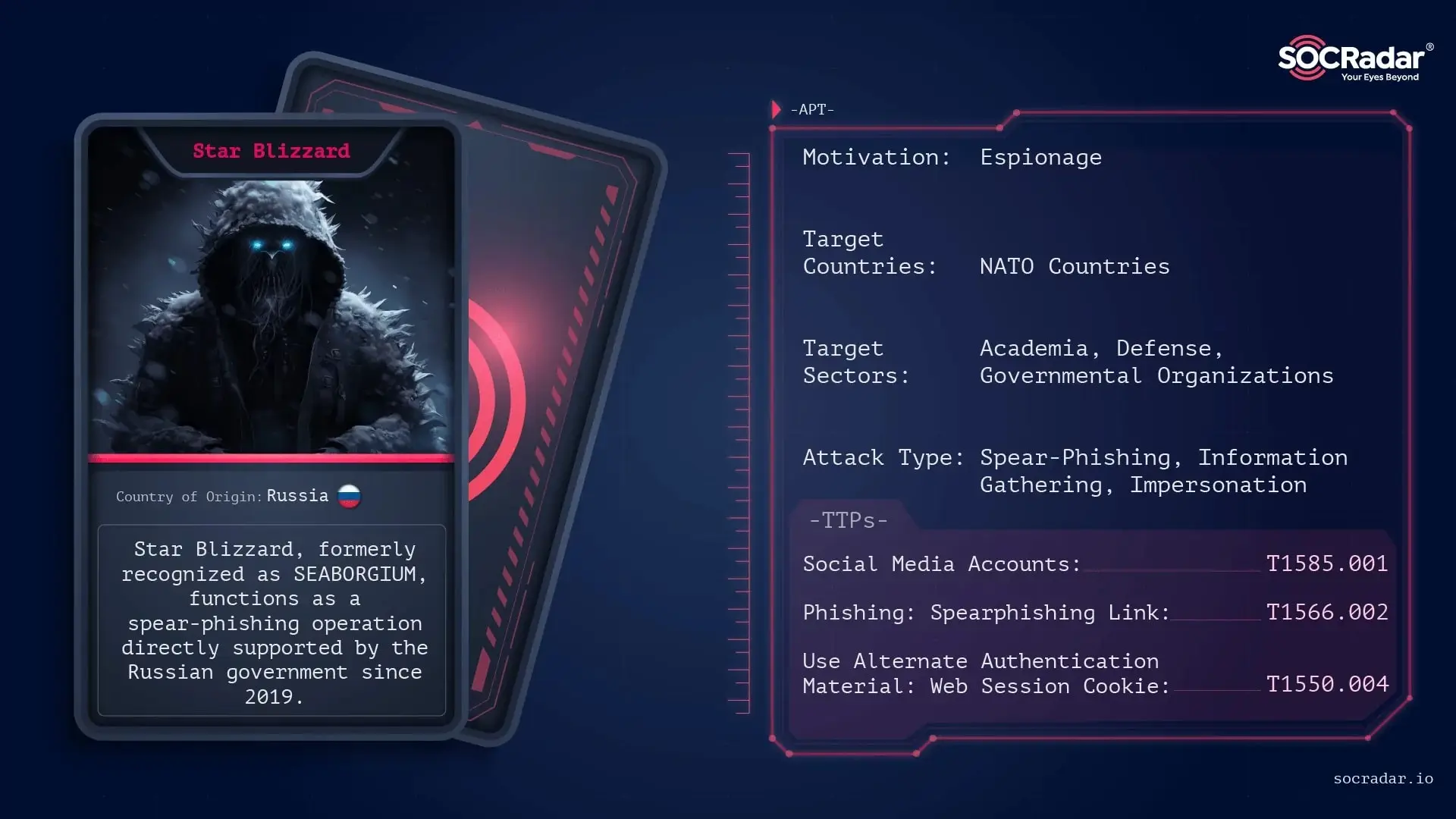
Read more about Star Blizzard
Notable Attacks in 2024
In 2024, Star Blizzard launched an extensive credential-harvesting operation, focusing on the United States and United Kingdom. The U.S. Department of Justice (DOJ) and Microsoft seized over 100 domains used in its phishing campaigns. The group employed deceptive emails impersonating trusted contacts, leading victims to fake login pages where credentials were stolen. This campaign targeted journalists, government officials, military personnel, and energy sector employees, aiming to gain access to classified and sensitive communications.
Star Blizzard’s WhatsApp spear-phishing campaign, detected in November 2024, marked a tactical shift. The group exploited QR codes in phishing emails, tricking victims into linking their devices to a malicious WhatsApp Web session. Once connected, attackers accessed private messages and sensitive data. The campaign leveraged broken QR codes in initial emails to prompt direct communication with victims, followed by a fraudulent WhatsApp invitation to lure them into scanning the malicious QR code. This operation highlighted the increasing sophistication of social engineering techniques used by state-sponsored actors.
Despite the 2024 disruptions by U.S. and UK authorities, Star Blizzard quickly adapted, shifting its focus from government and military targets to civil society organizations, exiled Russian dissidents, and policy researchers. Security researchers have warned of continued operations, with evidence suggesting the group is refining its phishing tactics to bypass MFA through session hijacking techniques. As Star Blizzard remains a persistent threat, organizations must strengthen email security, scrutinize QR codes, and enforce phishing-resistant authentication methods to mitigate risks.
8. APT28
APT28, also known as Fancy Bear, STRONTIUM, BlueDelta, and Forest Blizzard, is a Russian state-sponsored APT group linked to Russia’s military intelligence agency (GRU). The group has conducted cyber-espionage campaigns targeting government agencies, defense contractors, and critical infrastructure across Europe, Central Asia, and North America. In 2024, APT28 intensified its operations, deploying new malware strains and exploiting vulnerabilities to infiltrate high-value networks.
Notable Attacks in 2024
One of the group’s most notable campaigns in 2024 involved the use of “GooseEgg,” a custom exploit targeting CVE-2022-38028, a Windows Print Spooler vulnerability. By modifying JavaScript constraints files, APT28 achieved SYSTEM-level privileges, enabling them to execute remote commands, install backdoors, and move laterally within networks. GooseEgg was primarily used against government, educational, and transportation sectors in Ukraine, Western Europe, and North America. In response, CISA added CVE-2022-38028 to its Known Exploited Vulnerabilities (KEV) Catalog in April 2024, urging organizations to patch the flaw by May 14.
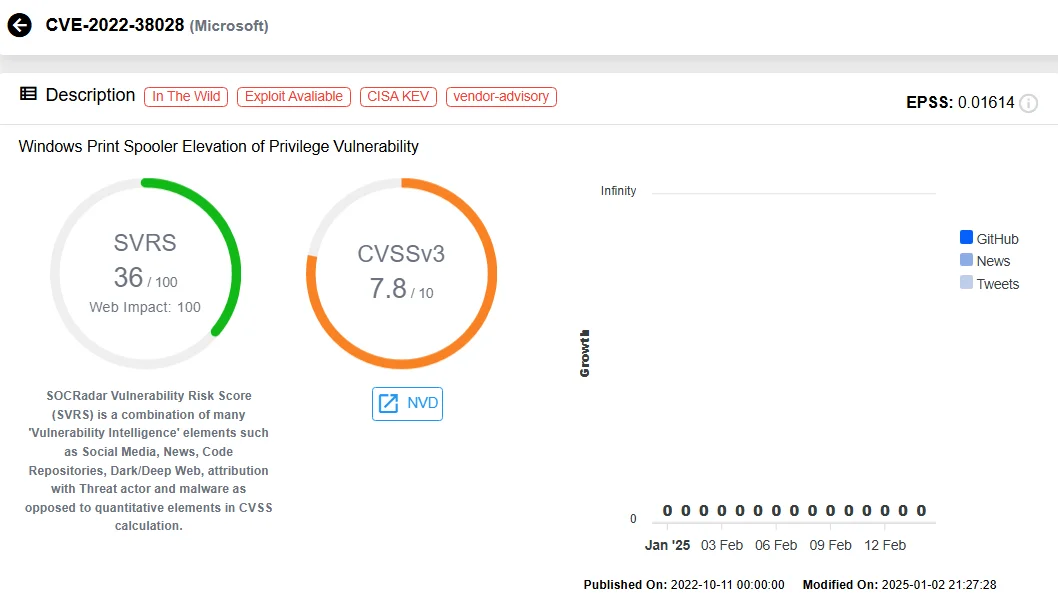
Vulnerability card of CVE-2022-38028 (SOCRadar Vulnerability Intelligence)
APT28 also increased its cyber-espionage activities in Central Asia and Kazakhstan. Using the alias UAC-0063 (TAG-110), the group launched phishing campaigns that used weaponized Microsoft Word documents to install the Hatvibe loader and CherrySpy backdoor. These operations targeted diplomatic, military, and economic entities, with a particular emphasis on Kazakhstan’s foreign relations, nuclear energy negotiations, and intelligence cooperation among Central Asian states. The campaign used legitimate documents stolen from Kazakhstan’s Ministry of Foreign Affairs and repurposed them to deliver malware via diplomatic correspondence.
In Ukraine, APT28 targeted scientific research institutions and gained initial access through vulnerabilities in HFS web servers. The group’s continued interest in Ukrainian infrastructure is consistent with Russia’s broader intelligence-gathering goals amidst ongoing geopolitical tensions. Furthermore, in May 2024, Poland reported a large-scale espionage campaign attributed to APT28, emphasizing the group’s aggressive targeting of NATO-aligned countries.
APT28 continues to pose a significant cyber threat, and its activities reflect Russia’s strategic intelligence priorities. Organizations should apply security updates, monitor for Indicators of Compromise (IoCs), and strengthen their defenses against spear-phishing and credential theft. Despite ongoing mitigation efforts, APT28’s tactics continue to evolve, posing a persistent threat to global cybersecurity.
9. Flax Typhoon
Flax Typhoon, also known as Ethereal Panda, Storm-0919, UNC5007, and Red Juliet, is a China-linked APT group specializing in cyber espionage and information theft. The group primarily targets Taiwanese government, academic, and defense entities but also conducts operations against U.S. critical infrastructure, European organizations, and various industries across Asia. In January 2025, the U.S. Department of the Treasury sanctioned Beijing-based Integrity Technology Group Inc., citing its role in enabling Flax Typhoon’s cyber operations from 2022 to 2023, particularly against U.S. telecommunications, media organizations, and government agencies.
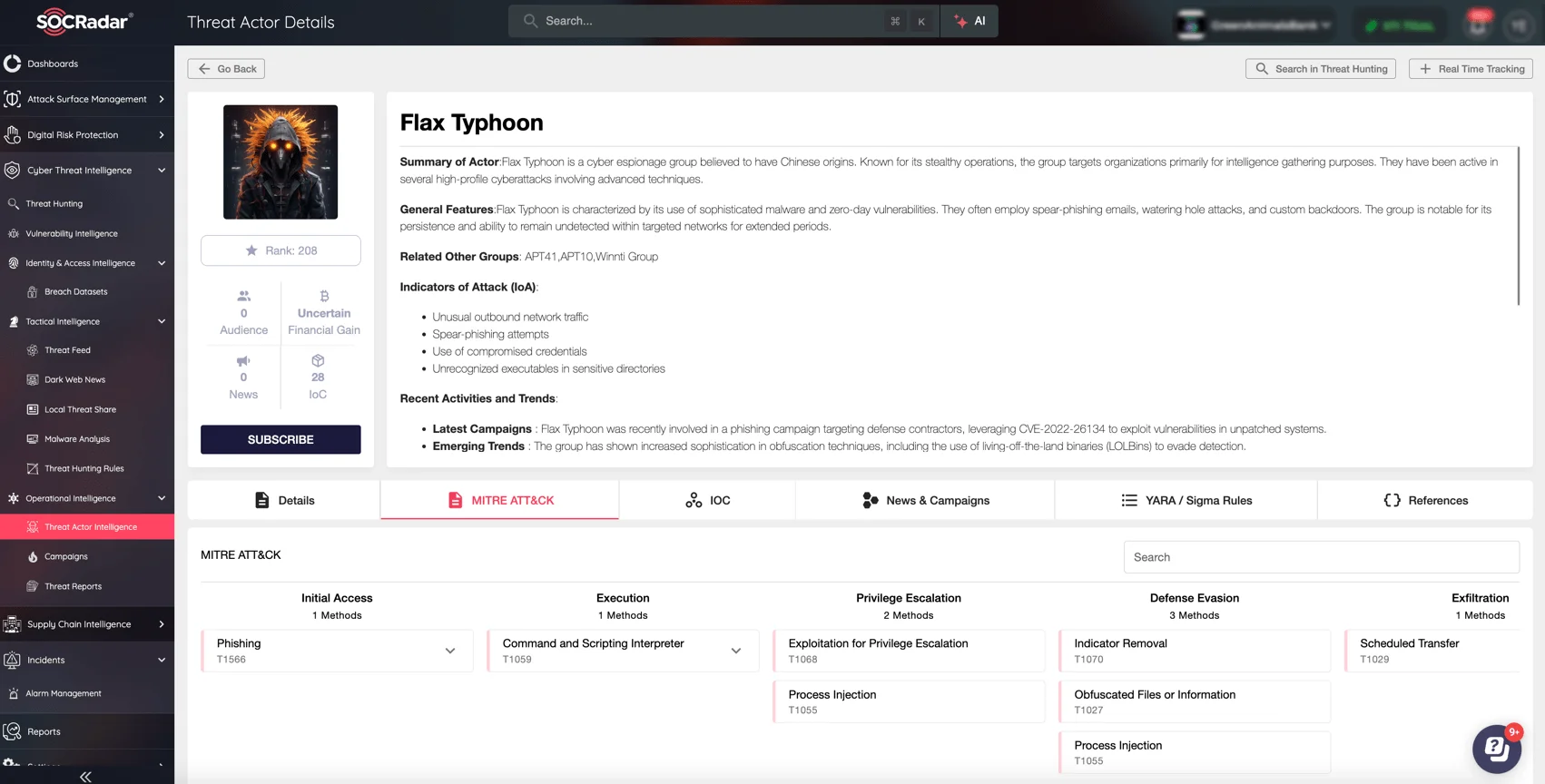
SOCRadar’s Threat Actor Intelligence explores Flax Typhoon’s threat actor profile, highlighting its tactics, indicators of attack, and recent activities.
Notable Attacks in 2024
In 2024, Flax Typhoon intensified its cyber campaigns, operating a large-scale botnet controlled via China Unicom Beijing Province Network IPs. By mid-2024, the botnet had infected over 260,000 compromised devices, including SOHO routers, NAS servers, and IoT endpoints. The attackers used custom Mirai-based malware and leveraged known vulnerabilities in Fortinet, Ivanti, Zyxel, Atlassian Confluence, and PHP to expand the network.
The botnet facilitated reconnaissance, exploitation, and lateral movement across U.S. and Taiwanese military, government, and telecom infrastructures. Researchers identified Flax Typhoon conducting reconnaissance and cyber intrusions against Atlassian Confluence servers and Ivanti Connect Secure appliances, as well as scanning for vulnerabilities across U.S. defense contractors, IT providers, and government agencies.
Despite mitigation efforts, the botnet remains active, and security experts warn that Flax Typhoon could use it for future large-scale cyber operations, including espionage and disruption campaigns. Organizations are advised to monitor for IoCs, apply patches, and strengthen IoT security defenses to mitigate the risks posed by Flax Typhoon’s evolving cyber warfare tactics.
10. Volt Typhoon
Volt Typhoon, also known as BRONZE SILHOUETTE, is a Chinese state-sponsored APT group specializing in cyber espionage. The group has been active since at least 2021, with a primary focus on critical infrastructure, defense, telecommunications, and governmental entities across the U.S. and Asia-Pacific. Its tactics emphasize stealth, leveraging “Living off the Land” (LotL) techniques, custom malware, and zero-day vulnerabilities to maintain persistence in compromised networks.
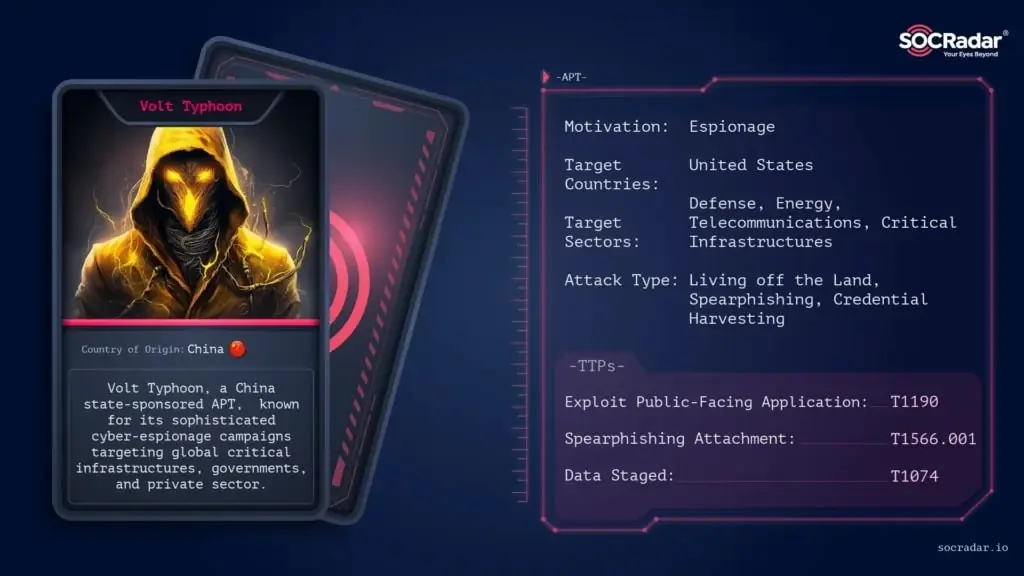
Read more about Volt Typhoon
Notable Attacks in 2024
In early 2024, Volt Typhoon intensified its cyber operations, exploiting CVE-2024-21762, a Fortinet FortiOS SSL VPN vulnerability, to deploy malware and establish long-term access to targeted environments. The group also expanded its espionage activities in the Asia-Pacific region, using advanced reconnaissance techniques to infiltrate defense ministries, economic agencies, and private sector firms in telecommunications, energy, and technology. This campaign aimed to collect intelligence on geopolitical strategies, trade negotiations, and military operations.
A key component of Volt Typhoon’s strategy involved botnets and custom malware infrastructure. In December 2023, the U.S. FBI disrupted the KV Botnet, a network of compromised routers linked to Volt Typhoon. Despite the botnet remotely uninstalling malware from infected systems—the botnet’s command-and-control (C2) infrastructure remained active throughout 2024. Security researchers tracked JDY cluster activity, a subset of the botnet targeting Cisco RV320/RC325 routers, which saw continued activity despite law enforcement interventions.
By mid-2024, Volt Typhoon also exploited CVE-2024-39717, a zero-day vulnerability in Versa Director SD-WAN systems, deploying the VersaMem web shell to steal credentials and establish long-term access within ISP and MSP networks.





































