
Top 10 CTI Blogs You Need to Follow
CTI blogs play an important role in keeping security professionals up to date on the latest threats, trends, and defensive strategies, providing in-depth analysis, expert insights, and timely updates.
These blogs are a valuable resource for cybersecurity enthusiasts, covering everything from tracking evolving threats and analyzing Advanced Persistent Threat (APT) groups to providing comprehensive annual threat landscape reviews and educational content.

An AI illustration by Bing
In this article, we explore the top 10 CTI blogs that have a significant impact in the field. These blogs not only provide a wealth of information, but also allow the cybersecurity community to collaborate, share insights, and fight back against threat actors.
Graham Cluley‘s blog is a leading source of CTI blogs, providing regular updates on the most recent security news. According to FeedSpot, the blog receives over 112,000 visits per month. Cluley’s blog, based in Oxford, England, is a must-read for anyone interested in data security.
Graham Cluley site main page
Cluley has been involved in the computer security industry since the early 1990s, bringing decades of experience to his writing and analysis. He started his career as a programmer, if you want to know more about him and other CTI experts check our blog about Top 10 CTI Experts.
Cluley’s blog covers an array of topics, including the most recent security news and in-depth analysis of various cybersecurity threats. His independence enables him to provide unbiased insights, making his blog a valuable resource for cybersecurity enthusiasts.
Graham Cluley’s blog is a must-visit for daily updates on the most recent threats, expert opinions, and practical cybersecurity advice. His profound background, combined with his involvement in the community through social media, and broadcasting, make his insights highly useful for anyone looking to stay up to date on cyber threats and how to defend against them.
2.Krebs on Security
Brian Krebs, the author of Krebs on Security, is a widely recognized cybersecurity journalist and former reporter for The Washington Post. Krebs has written more than 1,300 blog posts for the Security Fix blog, as well as hundreds of stories for online and print media.
His blog, based in Arlington, Virginia, is very well-known within CTI blogs, providing daily updates on the most recent security news and expert advice.
KrebsonSecurity main page
Krebs on Security is dedicated to uncovering online crime investigations and highlighting individuals and networks engaged in illegal online activities. Krebs’ investigative journalism revealed major data breaches, including the Target breach, which compromised 40 million credit and debit cards.
The blog provides frequent updates on the latest threats, security updates, and detailed reports on major data breaches. Its mission is to promote cyber justice by reporting on cyber criminals who face legal consequences for their actions.
3.Troy Hunt
Troy Hunt is a prominent cybersecurity expert who specializes in online security and cloud development. As an Australian Microsoft Regional Director and Most Valuable Professional (MVP), he has made significant contributions to the industry.
Troy Hunt main page
Troy Hunt’s blog is a valuable resource for anyone interested in CTI blogs. It addresses email address validation, data breaches, and cybersecurity incidents in easy-to-read posts with practical advice and a user-friendly approach.
The blog goes over the challenges of managing large data volumes while maintaining data integrity. It also allows Troy to share his personal experiences with phishing attacks and provide guidance for identifying scam messages.
4.Security Affairs
Security Affairs is another well-known blog in the field of cyber threat intelligence, offering daily updates on cybersecurity news. Created by Pierluigi Paganini, an ethical hacker and cybersecurity expert.
The blog contains a wealth of cybersecurity-related information, including regular interviews with ethical hackers that provide readers with insights into ethical hacking tools, skills, and industry trends.

Security Affairs main page
Security Affairs contributes to the field of cyber threat intelligence by sharing timely and relevant cybersecurity news, utilizing Open Source Intelligence (OSINT) and other forms of intelligence gathering to cover cyber threats.
As cyber threat intelligence evolves through Artificial Intelligence (AI) and Machine Learning (ML), Security Affairs incorporates these advancements to provide faster and more accurate threat analysis. The blog helps to transition from reactive to proactive cybersecurity by predicting emerging threats.
5.Wired
Wired is a popular site that covers a variety of topics, including technology, business, and cybersecurity. Although it is not a specialized cyber threat intelligence as the other CTI blogs, its reputation for in-depth reporting and analysis extends to cybersecurity, making it a significant player in cyber threat intelligence.
Wired main page
The site’s cybersecurity content is diverse, ranging from technical details of specific vulnerabilities to the broader implications of cyber threats for national security, privacy, and business. This ensures that readers are up to date on the most recent developments in cybersecurity.
Wired contributes to the field of cyber threat intelligence by increasing public awareness of cybersecurity issues. Its articles frequently shed light on complex cyber threats in a way that is accessible to a general audience, making it an interesting resource for both cybersecurity enthusiasts and the general public.
6.Schneier on Security
Schneier on Security a blog owned by Bruce Schneier, a “public-interest technologist,” an author, and a cybersecurity expert. He is known for his contributions to cryptography, privacy, and digital security. His expertise earned him the title of ‘Security Guru‘ by The Economist.
Schneier on Security main page
One of the interesting blogs you can find in it is “What Will It Take?,” This addresses the disparity between cybersecurity experts and the general public’s perceptions of cyber incidents. According to Schneier, cybercrimes are not being taken on a serious note, and that a ‘big enough’ event may be necessary to spur action.
Schneier on Security is a top CTI blog that provides in-depth analysis, real-world incident discussions, and a comprehensive approach to creating a secure Internet ecosystem. This blog is a must-read for anyone interested in understanding societal changes required to improve digital security.
7.Securelist
Securelist, powered by Kaspersky, provides detailed statistics on industrial threats, including the most commonly detected malicious objects and the threat landscape by industry and region. This information is invaluable for organizations looking to understand and mitigate potential cybersecurity risks.
Securelist main page
Securelist is known for its threat landscape reports, the most recent one being its Projections for 2024’s Advanced Threats Landscape which predicts that the landscape will be shaped in three main ways: the escalation of state-sponsored cyber warfare, the rise of cyber-physical attacks targeting critical infrastructure, and increased sophistication of financially-motivated cybercrimes. You can also check our blog post Cybersecurity Predictions: What Trends Will Be Prevalent in 2024?.
Securelist is also known for its security bulletins, which provide key statistics on a range of threats including ransomware, banking malware, miners, zero-day vulnerabilities, web attacks, and threats to macOS and IoT devices.
Kaspersky, the organization behind Securelist, is a globally recognized cybersecurity firm that develops a wide range of cybersecurity products and services. Its connection to Securelist ensures that the information provided on the blog is backed by extensive expertise in the field.
8.Unsupervised Learning
Unsupervised Learning, made by Daniel Miessler, provides a unique perspective on the intersection of Artificial Intelligence (AI) and cybersecurity, making it an invaluable asset for enthusiasts who are looking for top CTI blogs.
Daniel Miessler is a San Francisco-based information security professional and writer. He began the blog in 1999 as a way to collect technical knowledge, and it has since grown into his most important life project, with over 2,500 essays, posts, tutorials, articles, and other types of content.
The Unsupervised Learning Newsletter section offers readers useful information about cybersecurity trends, insights, and updates. It includes in-depth analysis, regular updates, emerging technologies, current events, and educational opportunities.
Unsupervised Learning Newsletter
As an example, Miessler’s “UL AI Course” is frequently mentioned, allowing readers to gain a better understanding of AI’s role in cybersecurity. The newsletter also provides valuable resources, such as AI projects and security program recommendations.
9.Dark Reading
Dark Reading is a popular CTI blog that serves as a trusted community for cybersecurity professionals.
Dark Reading main page
The website is divided into 14 topical sections, such as Cybersecurity Analytics, Cloud Security, Endpoint Security, and Threat Intelligence. Dark Reading’s content is created in collaboration with security researchers, specialists, and analysts to ensure the confidentiality of the information.
Dark Reading is a cornerstone of cybersecurity news, providing a wealth of resources and opportunities for community engagement. It is dedicated to providing deep coverage and growing an informed community.
10.SOCRadar
The SOCRadar blog is a valuable resource for organizations seeking comprehensive Cyber Threat Intelligence (CTI) and effective strategies to combat emerging threats. It provides information on critical vulnerabilities, major industry events, and insightful analysis of cyber threats.
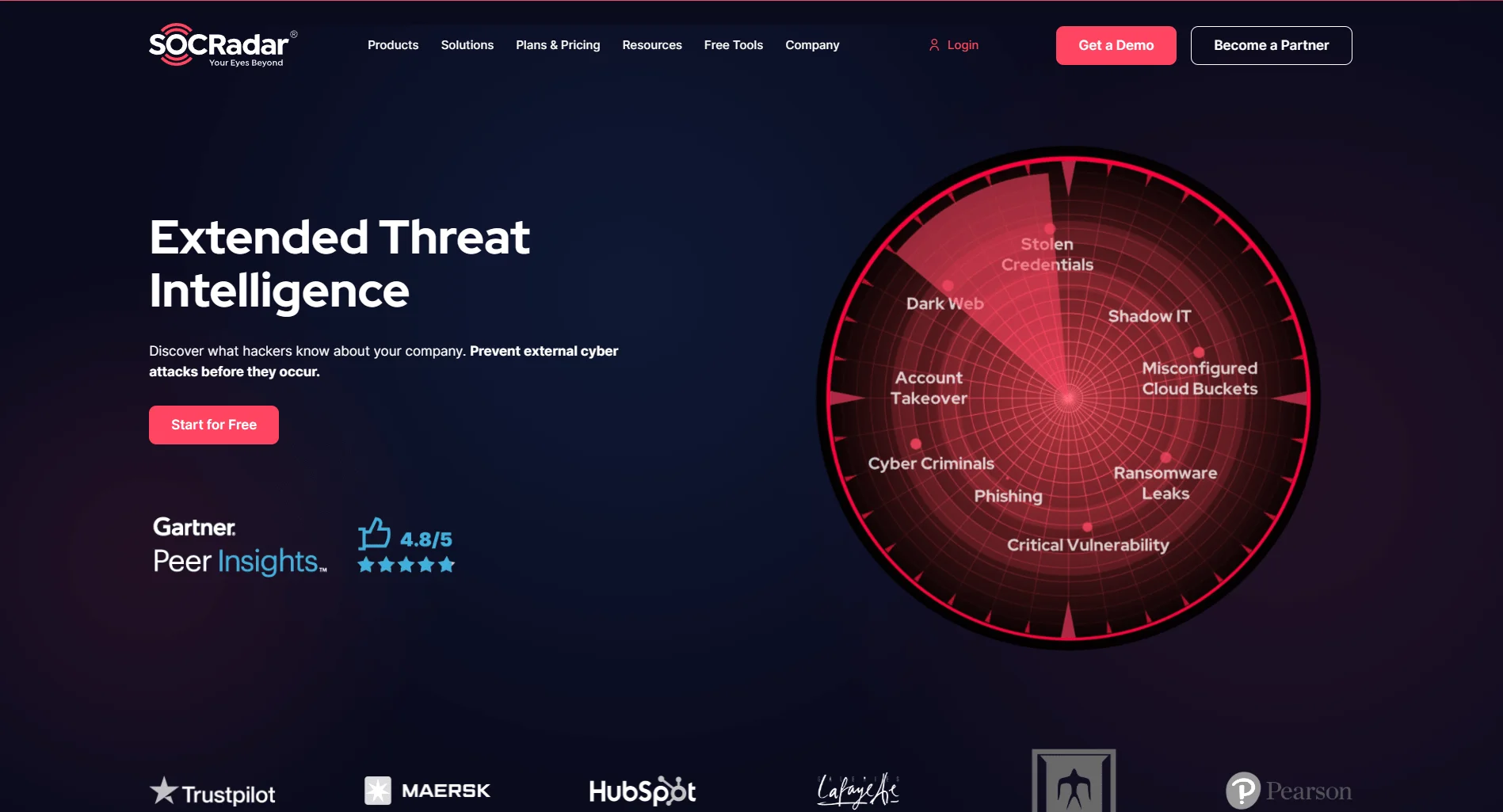
SOCRadar Extended Threat Intelligence
The standout feature of SOCRadar is its specialization in Dark Web intelligence. SOCRadar excels in profiling Dark Web threat actors, APT groups, hacker forums, and similar entities, offering an in-depth understanding of their operations, motivations, and targets.
SOCRadar blogs provide visualization of threat actors through Threat Actor Cards, enabling users to quickly grasp essential details about these entities.

SOCRadar Threat Actor Card of Hunters International
Furthermore, the blog provides a summary of each of our reports in three specific categories: Dark Web Reports, Country Reports, and Industry Reports. These reports offer valuable insights into evolving cyber activities within the Dark Web, as well as detailed analyses of threats targeting various industries and countries.
Additionally, users can access up-to-date and succinct information through the brief yet comprehensive Country and Industry threat landscape reports offered by SOCRadar Labs.
SOCRadar Labs
Ultimately, the SOCRadar blog serves as a strategic tool that equips organizations with actionable intelligence, enabling them to proactively defend against cyber threats and stay ahead of the rapidly evolving threat landscape.




































