
Top 10 Cybersecurity Books
With new threats and challenges emerging every day within the cybersecurity field, to stay ahead of the curve, it’s necessary to keep learning. One of the best ways to do this is by reading cybersecurity books, as they provide insights into the world of cybersecurity, from understanding the fundamentals to exploring its concepts. They can also offer real-world examples and case studies, helping readers to understand how these concepts apply in practice.

AI illustration by Bing
Whether you’re a beginner just getting started in the field or a professional looking to expand your knowledge, there’s a cybersecurity book for you, ranging from Practical Malware Analysis for experts to The Cuckoo’s Egg for those looking for entertaining stories. Here are the top ten cybersecurity books that you should read.
Spam Nation

Spam Nation: The Inside Story of Organized Cybercrime – from Global Epidemic to Your Front Door by Brian Krebs is a riveting exploration of the world of cybercrime. Published in 2014, this non-fiction book dives into the global spam problem and the organized cybercrime behind it.
Brian Krebs is a highly respected cybersecurity journalist who previously worked at The Washington Post; this book illustrates his investigative reporting skills. If you want to learn more about him, check out our blog post on the Top 10 CTI Experts.
The book takes a thorough look at various aspects of cybercrime, including bulletproof-hosting providers and botnets like Conficker and Storm. It examines the business operations of cybercriminals, including money laundering and the use of technology such as Black SEO. Krebs delves into the intricate tactics employed by cybercriminal groups to evade law enforcement and maximize profits, which makes it.
Tribe of Hackers

Tribe of Hackers: Cybersecurity Advice from the Best Hackers in the World by Marcus J. Carey and Jennifer Jin is one of the unique and insightful cybersecurity books. Published in 2019, this book stands out due to its format – a compilation of interviews with 70 security experts, offering a wide range of perspectives on technical and professional issues in cybersecurity.
Tribe of hackers covers a broad spectrum of cybersecurity topics, including defensive and preventative techniques. It delves deep into crucial areas such as penetration testing, incident response, digital forensics, and offensive ethical hacking techniques.
The success of Tribe of Hackers spurred the release of another book by the same authors titled “Tribe of Hackers Red Team: Tribal Knowledge from the Best in Offensive Cybersecurity” on August 13, 2019. This book delves deeper into Red Team security.
What distinguishes Tribe of Hackers is its real-world perspective. The authors have gathered advice from some of the world’s best hackers, providing readers with a unique view of the ever-changing cybersecurity books sphere. The book emphasizes the importance of a straightforward approach to cybersecurity and argues that defenders can have an advantage over adversaries.
Blue Team Handbook

Blue Team Handbook: Incident Response Edition by Don Murdoch, GSE, MBA, is a highly regarded resource from cybersecurity books. This book was released in 2014, and it is a valuable resource for cybersecurity professionals.
The book discusses various topics, including the incident response process, attacker methodologies, network analysis, Indicators of Compromise (IoCs), and more. What differentiates it is its practical approach, which incorporates real-life experiences and techniques from the author’s extensive career in the industry.
Check SOCRadar Lab’s IOC Radar service, for it is an essential tool in this endeavor. It provides enriched data about threat actors, and malware, using artificial intelligence algorithms to enhance the information. This service is not just about providing data; it’s about making that data actionable and relevant to your specific needs.
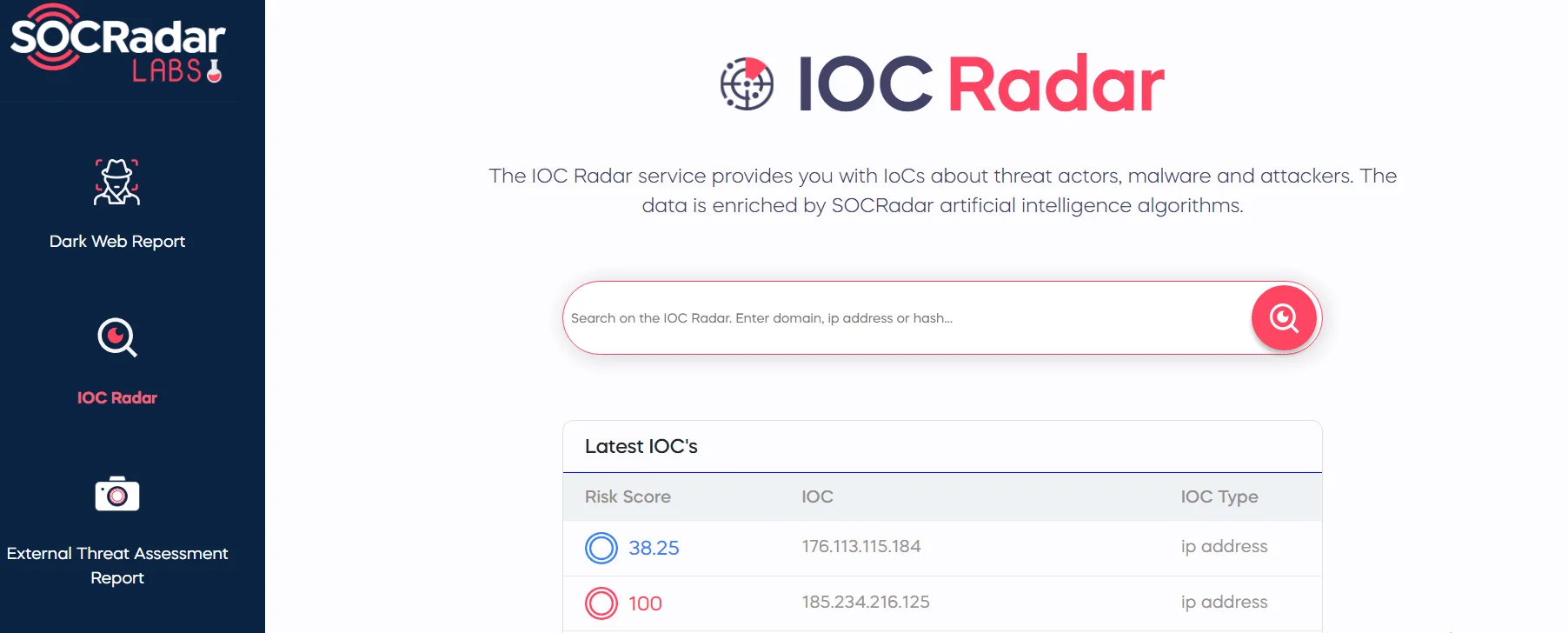
SOCRadar Lab’s IoC Radar
Don Murdoch is a seasoned professional in information security, having taught CISSP and intrusion analysis courses for the SANS Institute. His expertise and experience in the field make this book an invaluable resource for anyone interested in cybersecurity.
In 2018, BookAuthority.com ranked the book third among the 100 Best Cybersecurity Books of All Time, highlighting its importance within cybersecurity books.
The Web Application Hacker’s Handbook

The Web Application Hacker’s Handbook: Finding and Exploiting Security Flaws 2nd edition is a gem in the field of cybersecurity literature. It was published in 2011 and authored by Dafydd Stuttard and Marcus Pinto. This book serves as a comprehensive guide for understanding, finding, and exploiting web application security flaws.
The book’s structure is meticulously designed, beginning with the fundamentals of web application vulnerabilities, followed by deeper dives into security mechanisms and attack strategies. The wide spectrum of topics covered includes custom code development like JavaScript, AJAX, ASP.NET, and many more.
The book reveals how to overcome new technologies and techniques aimed at defending web applications against attacks. It discusses new remoting frameworks, HTML5, cross-domain integration techniques, UI redress, framebusting, HTTP parameter pollution, hybrid file attacks, and more.
Even though the book is old it’s still a must-read within cybersecurity books as it explores the various web protocols, explains how web coding works, and more basic fundamentals in detail.
Ghost in the Wires

Ghost in the Wires: My Adventures as the World’s Most Wanted Hacker was published in 2011 and is an astonishing cybersecurity book by Kevin Mitnick, one of the most known hackers in history. This book is a fascinating tale of his life as a hacker, gazing into his social engineering skills and his run away from law authorities.
Mitnick’s journey from a well-known hacker to an esteemed cybersecurity expert is a significant theme of the book. The narrative contains specifics about Mitnick’s hacking skills, demonstrating the art of deception and manipulation in the industry.
The book has marginally impacted cybersecurity, inciting dialogue and pushing boundaries. It is part of Mitnick’s legacy, alongside his other works such as “The Art of Deception.”
Opinions of “Ghost in the Wires” have been mixed, with some admiring Mitnick’s skills and change while others condemn his lack of remorse for his actions. Regardless, the book is recognized as a substantial work in cybersecurity and has been praised by many.
Countdown to Zero Day

Countdown to Zero Day: Stuxnet and the Launch of the World’s First Digital Weapon by Kim Zetter was published in 2014, it is a hooking look at the world of cyber warfare, which earned it its spot as one of the top cybersecurity books. It discusses in detail a malware called Stuxnet, which targeted Iran’s nuclear program, marking a historic event in cyber warfare.
Zetter’s novel intertwines the complicated technical features of the world’s first cyberweapon Stuxnet with the mystery of its origins and its impact on the Iranian nuclear program. The book relates the bizarre story of the security professionals who discovered a top-secret sabotage effort that had been planned for years.
Countdown to Zero Day extends beyond the story of Stuxnet, exploring the history and future of cyber warfare. It raises moral questions about cyber warfare and the security of the SCADA (Supervisory Control and Data Acquisition) system. The book also gives some insights into how the white hats and black hats operate.
The Dark Net

Another cybersecurity book is The Dark Net: Inside the Digital Underworld which was published in 2014 by Jamie Bartlett and is an interesting exploration into the hidden corners of the internet. This book provides a non-sensationalist look at various underground and emergent subcultures that exist away from the mainstream internet, including those on Tor and the Deep Web.
Despite its title, the book is not solely about the darknet, dark or deep web. It offers an expanded view, diving into various aspects of the internet, such as the evolution of cryptocurrencies, the rise of Bitcoin, the practice of trolling on 4chan, and the raise of pro-anorexia and bulimia web forums.
The book also discusses the history of the dark web and the Tor browser. It provides thoughtful reporting and covers a wide range of people, from highly skilled programmers to convicted pedophiles. The book focuses on the fundamentals of internet security and the right to privacy. It portrays the dark web as a platform for free communication away from the prying eyes of governments and corporations.
Sandworm: A New Era of Cyberwar and the Hunt for the Kremlin’s Most Dangerous Hackers

Sandworm: A New Era of Cyberwar and the Hunt for the Kremlin’s Most Dangerous Hackers was published in 2019 by Andy Greenberg an award-winning senior writer for WIRED. It focuses on APT group Sandworm, which is believed to be Russia-sponsored.
The book provides a chilling narrative of Sandworm’s role in some of the most devastating cyberattacks in history, including the 2016 U.S. Presidential Election interference and the NotPetya malware attack. It provides a stark warning about the potential for future, more destructive cyber warfare, highlighting the blurred lines between digital and physical conflict.
Sandworm has targeted Industrial Control Systems (ICS) in various sectors including energy, national security, and more. They use spear phishing to gain initial access for their attacks. For more information on the group’s targets and motivations, please visit our profile page: APT profile: Sandworm.
If you want to keep track of recent ransomware activities, use SOCRadar’s Threat Hunting module. This powerful tool, which enables users to identify threats and respond to them as quickly as possible, exemplifies the proactive, hands-on approach to cybersecurity that these books advocate.
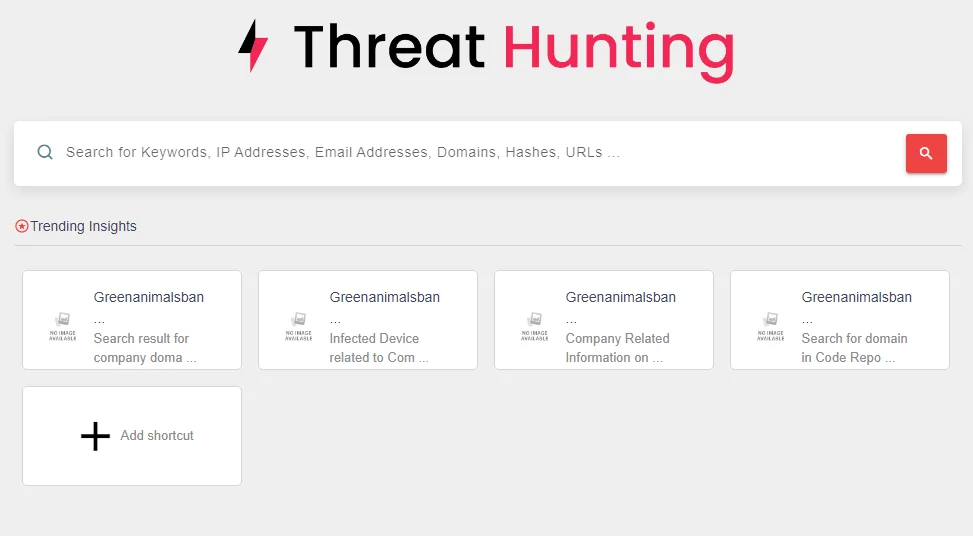
SOCRadar’s Hunting module
Practical Malware Analysis

Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software by Michael Sikorski and Andrew Honig. Despite being published in 2012, the book’s lessons remain relevant to today’s encounters. As it’s one of the best cybersecurity books that serves as an excellent introduction to reverse engineering and malware analysis.
The book offers hands-on exercises with malware samples and uses major analysis tools like IDA Pro, OllyDbg, and WinDbg, to set up a fitting virtual environment for malware analysis and to extract network signatures and host-based indicators.
The book is not for beginners. It requires a decent knowledge of C programming language, Assembly language, and the x86 architecture, as most advanced analysis occurs at the assembly level. The book doesn’t spend time teaching code so you need to have prior knowledge. The book also delves into networking components requiring a basic understanding of TCP/IP networks.
Most of the tools used in the book are widely available and free to use. With a chapter dedicated to the main tools, providing extra exposure to the important software used by professional analysts.
Understanding the nature of threats in the cybersecurity field is crucial. This is where tools like SOCRadar’s Malware Analysis module come into play. This advanced tool performs a comprehensive analysis of various file types, determining their potential maliciousness, extracting Indicators of Compromise (IoCs), and highlighting suspicious code fragments.
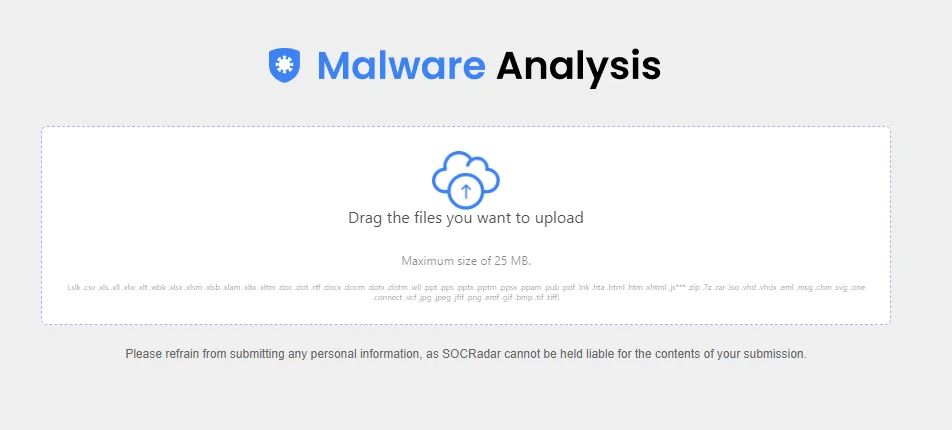
SOCRadar’s Malware Analysis module
The Cuckoo’s Egg

The Cuckoo’s Egg: Tracking a Spy Through the Maze of Computer Espionage by Cliff Stoll. Since its publication in 1989, “The Cuckoo’s Egg” has sold over a million copies and has significantly shaped the field of network defense.
Cliff Stoll, an astronomer and systems manager at Lawrence Berkeley Lab, was propelled into the world of cybersecurity by a 75-cent accounting error. This error led him to discover unauthorized access to his system, marking the start of his thrilling pursuit of ‘Hunter,’ a hacker infiltrating U.S. computer systems and stealing sensitive information. Stoll’s one-man mission, which eventually roped in the CIA, revealed a KGB-fuelled spy ring, providing readers with an amusing story.
The Cuckoo’s Egg is an insightful journey into cybersecurity’s beginnings. Its relevancy remains as it underscores the enduring importance of cybersecurity fundamentals. A must-read for anyone interested in cybersecurity, or those who enjoy real-life spy narratives and law enforcement dramas.



































