
Top 10 Best Free Cyber Threat Intelligence Sources and Tools in 2025
In 2023, we compiled a list of the top free Cyber Threat Intelligence (CTI) sources to help security teams stay ahead of evolving threats. Since then, the cyber landscape has shifted dramatically, with AI-powered attacks, deepfake-based fraud, and increasingly sophisticated ransomware operations becoming more prevalent. As a result, real-time and accessible threat intelligence is more crucial than ever.
While many paid CTI solutions offer advanced capabilities, free intelligence sources remain indispensable for SOC analysts, researchers, and businesses looking to enhance their cybersecurity posture without significant financial investment. These tools provide access to malware indicators, IP reputation data, phishing reports, and vulnerability intelligence, helping defenders respond to threats more effectively.
This 2025 update builds on our previous list from 2023 and reflects:
- New or improved CTI platforms with enhanced free-tier offerings.
- The rise of AI-driven threats and threat intelligence’s growing role in cyber defense.
To further support security professionals, we also recommend checking out this comprehensive list of 50 Free Online Tools for SOC Analysts, which includes valuable resources for threat detection, incident response, and forensic analysis.
Let’s dive into the top 10 free CTI sources for 2025 and how they can help you stay ahead of emerging cyber threats.
1. SOCRadar Free Edition
Since 2023, SOCRadar has significantly expanded its free threat intelligence capabilities to address the evolving cyber threat landscape. With the rise of AI-powered phishing, supply chain compromises, and more sophisticated ransomware attacks, security teams need more comprehensive intelligence to stay ahead.
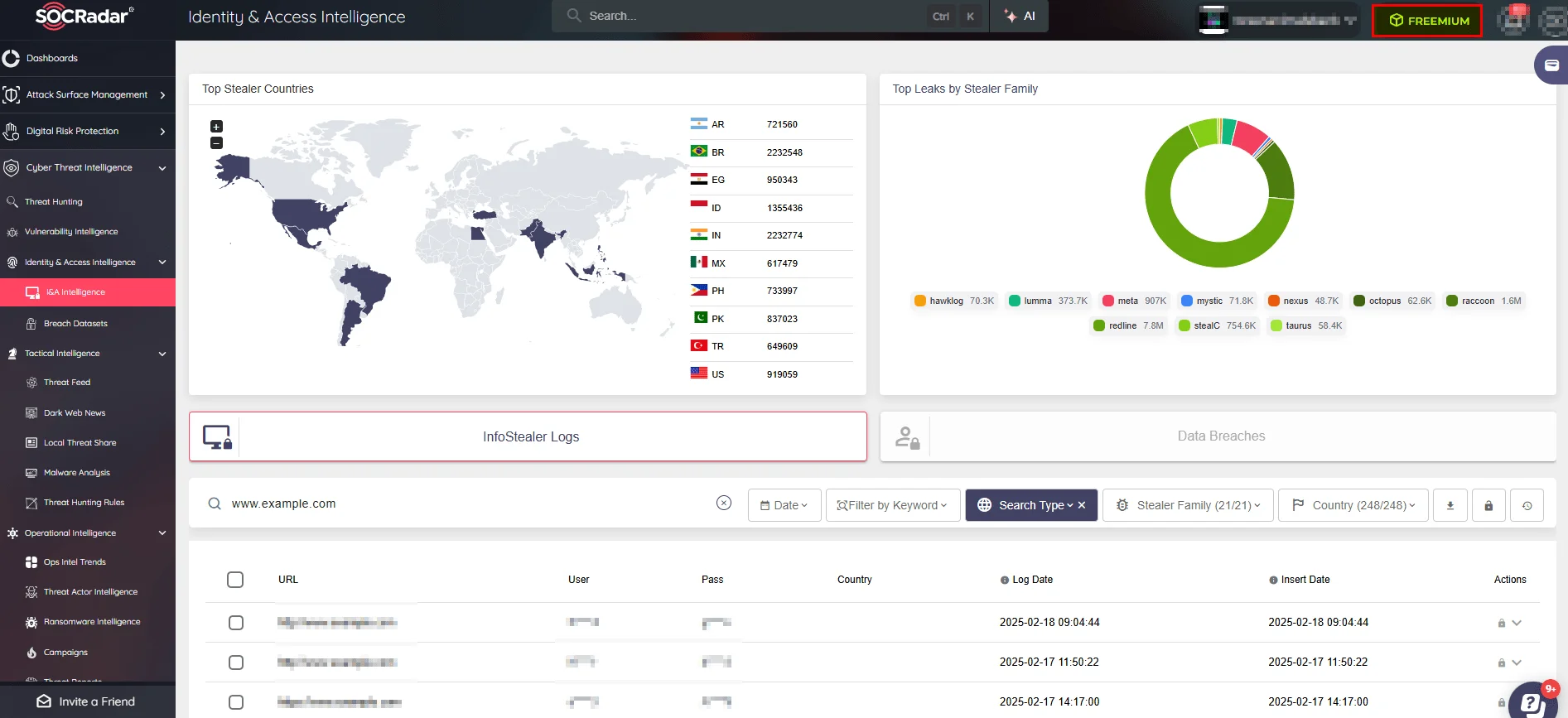
SOCRadar Free Edition launched to equip growing startups with the same cyber security perspective and tools that only large organizations such as Banks can afford.
Key Features & Enhancements:
- Expanded Dark Web Monitoring – Tracks a wider range of underground forums, marketplaces, and leak sites for exposed credentials and sensitive data.
- Enhanced Attack Surface Management (ASM) – Provides better visibility into externally exposed assets, helping organizations mitigate risks associated with cloud adoption and misconfigurations.
- Real-Time Threat Feeds – Delivers up-to-date intelligence on ransomware groups, APT activities, and actively exploited vulnerabilities, keeping security teams informed.
- Improved Fraud and Brand Protection – Detects domain impersonation, phishing attempts, and unauthorized data leaks to help organizations prevent fraud and reputational damage.
As cyber threats continue to grow in sophistication, SOCRadar Free Edition remains a crucial resource for organizations looking to strengthen their defenses without additional costs.
2. VirusTotal
VirusTotal continues to be one of the most widely used cyber threat intelligence platforms, relied upon by SOC analysts, incident responders, and cybersecurity researchers for quick malware analysis. With the rise of AI-generated threats, polymorphic malware, and sophisticated phishing campaigns, the ability to quickly scan and assess suspicious files, URLs, domains, and IPs has become even more crucial in 2025.

VirusTotal public page
VirusTotal aggregates data from dozens of antivirus engines, sandbox solutions, and security vendors, making it a powerful tool for detecting and investigating emerging threats. Its extensive database and strong integration with threat intelligence frameworks allow organizations to correlate findings with real-world attack patterns.
Key Features:
- Multi-engine malware scanning – Cross-checks suspicious files against multiple AV vendors for better detection accuracy.
- Comprehensive URL and IP reputation analysis – Helps identify phishing sites, malicious infrastructure, and command-and-control (C2) servers.
- Community-driven intelligence – Researchers and analysts share new threat indicators, enriching VirusTotal’s database.
- Integration with threat intelligence platforms – Enables SOC teams to correlate findings with frameworks like MITRE ATT&CK and track APT activity.
- Behavioral analysis of files – Provides deeper insights into how malware executes, helping security teams detect zero-day threats.
As cyber threats become increasingly sophisticated, VirusTotal remains an essential tool for quickly verifying and understanding potential security risks.
3. AlienVault OTX
AlienVault Open Threat Exchange (OTX) remains one of the largest community-powered threat intelligence sharing platforms, widely used by security teams, threat researchers, and SOC analysts. In 2025, its role is more critical than ever as cyber threats grow in complexity and speed, requiring faster collaboration and intelligence sharing.
AlienVault Open Threat Exchange
With thousands of contributors worldwide, OTX provides access to real-time threat indicators, including malware signatures, IP reputation data, phishing domains, and exploit activity. Security professionals use it to enrich investigations, detect threats earlier, and strengthen defenses against evolving attack tactics.
Key Features:
- Community-driven threat intelligence – Contributions from security researchers, enterprises, and government agencies enhance real-time threat detection.
- IoC (Indicators of Compromise) sharing – Provides actionable data on malware, botnets, phishing campaigns, and suspicious IP addresses.
- Integration with SIEM and security tools – Allows easy incorporation of threat intelligence feeds into incident response workflows.
- Crowdsourced attack trend insights – Helps analysts track emerging cybercrime tactics across industries and geographies.
- Custom pulse creation – Users can generate and share their own threat intelligence collections for specific attack campaigns.
As cybercriminals leverage new techniques like AI-enhanced attacks and more aggressive supply chain compromises, AlienVault OTX continues to be an essential resource for real-time, collaborative cyber defense.
4. MISP (Malware Information Sharing Platform)
MISP also remains a widely used open-source platform for sharing, storing, and analyzing threat intelligence. As cyber threats become more interconnected in 2025, the need for structured, collaborative intelligence sharing has grown, making MISP an essential tool for SOC teams, security researchers, and government agencies.
MISP Project, Home page
The platform enables organizations to exchange Indicators of Compromise (IoCs), track adversary behaviors, and correlate attack patterns across industries. Its open-source nature and strong community support allow for continuous improvements, keeping it relevant for modern cyber defense.
Key Features:
- Collaborative threat intelligence sharing – Facilitates real-time exchange of malware samples, phishing indicators, and threat actor profiles.
- IoC correlation and enrichment – Helps detect connections between different attack campaigns and ongoing threats.
- Integration with SIEM, SOAR, and other security tools – Automates threat intelligence ingestion for faster response times.
- Support for structured intelligence formats – Works with MITRE ATT&CK, STIX/TAXII, and other frameworks for better intelligence mapping.
- Scalability and customization – Adaptable to various security environments, from small teams to large enterprises and government agencies.
With cyber threats evolving rapidly, MISP continues to be a crucial resource for organizations looking to improve intelligence sharing and strengthen their security posture.
5. Shodan
Shodan is a critical tool for cybersecurity professionals, researchers, SOC analysts, and threat intelligence teams looking to uncover exposed assets and assess security risks. As organizations expand their digital footprint in 2025, the platform plays an even greater role in identifying vulnerable devices, misconfigured systems, and internet-facing assets before attackers exploit them.
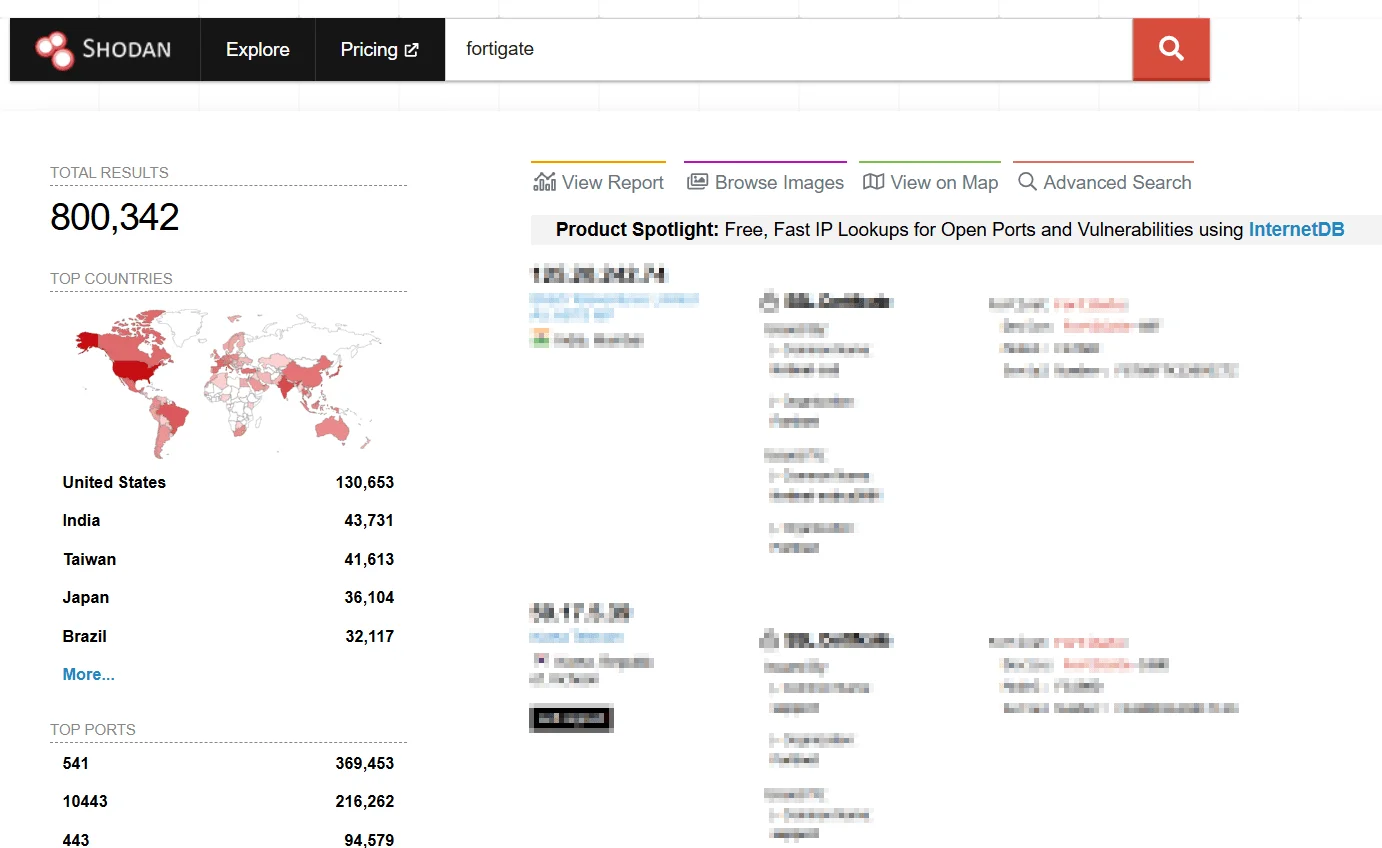
Shodan, searching for FortiGate devices
Unlike traditional threat intelligence platforms like VirusTotal or MISP, which focus on malware and IoCs, Shodan specializes in mapping the attack surface, helping security teams proactively secure their infrastructure. It is often used alongside AlienVault OTX and MISP to enrich investigations by correlating IoCs with exposed systems.
Key Features:
- Internet-wide device scanning – Identifies publicly accessible IoT devices, webcams, databases, and critical infrastructure.
- Searchable exploit database – Helps researchers find known vulnerabilities (CVEs) affecting specific services and ports.
- Real-time network exposure monitoring – Alerts security teams to newly exposed cloud instances, open ports, and unpatched servers.
- Threat intelligence integrations – Can be combined with MISP, SIEM platforms, and other security tools for enhanced context.
- Historical data and trend analysis – Tracks how attack surfaces change over time, helping organizations detect risky misconfigurations early.
As the number of internet-connected devices continues to grow, Shodan remains an essential tool for organizations aiming to reduce their external attack surface and stay ahead of potential threats.
6. Cisco Talos’ Intelligence Center
Cisco Talos Intelligence has long been recognized for its enterprise-grade threat intelligence, but its freely available tools and resources have made it even more accessible to SOC analysts, researchers, and cybersecurity professionals. With the increasing sophistication of zero-day exploits, ransomware campaigns, and APT operations, Talos’s free threat intelligence feeds, malware analysis reports, and security advisories have become valuable assets for organizations of all sizes.
Cisco Talos’ Intelligence Center
Unlike community-driven platforms like AlienVault OTX or MISP, Cisco Talos leverages its extensive network telemetry and security product ecosystem to provide highly actionable intelligence. When combined with tools like VirusTotal for malware analysis and Shodan for attack surface monitoring, Talos enhances an organization’s ability to detect, analyze, and mitigate cyber threats proactively.
Key Features:
- Threat intelligence feeds – Provides up-to-date information on malware campaigns, phishing domains, and botnet activities.
- Publicly available security advisories – Alerts organizations to newly discovered vulnerabilities and emerging threats.
- Malware analysis reports – Offers detailed insights into malicious file behavior, threat actor techniques, and mitigation strategies.
- Integration with security platforms – Works with SIEM, SOAR, and endpoint security tools to improve detection and response.
With threat actors evolving their tactics, Cisco Talos’s free intelligence offerings in 2025 remain a useful resource for cybersecurity professionals aiming to stay ahead of emerging threats and protect their networks effectively.
7. GreyNoise
In 2025, the rise of automated scanning, bot-driven reconnaissance, and mass exploitation of vulnerabilities might make tools like GreyNoise more valuable. As attackers increasingly probe the internet for weak points, GreyNoise helps SOC analysts and threat hunters differentiate between background internet noise and real threats.
GreyNoise’s Trends
A standout feature is its free IP scanning lookup, which allows users to quickly determine whether an IP address is associated with harmless scanning activity or a legitimate cyber threat. Additionally, GreyNoise’s Trend Tags provide real-time insights into which CVEs, attack techniques, and protocols are being actively scanned, giving organizations an early warning about potential exploitation trends.
Key Free Features:
- Free IP Lookup Tool – Enables users to check whether an IP is linked to widespread scanning or a targeted attack.
- Trend Tags – Tracks actively scanned vulnerabilities, exploited CVEs, and attack methods, helping security teams anticipate emerging threats.
- Noise vs. Targeted Threat Differentiation – Reduces false positives by categorizing mass scanners vs. real attackers.
- Threat Intelligence Enrichment – Enhances SIEM, SOAR, and TIP integrations with additional context on suspicious IP activity.
- Real-Time Attack Trends – Provides a global view of internet-wide scanning behavior, allowing defenders to stay ahead of evolving tactics.
Unlike Cisco Talos or AlienVault OTX, which focus on malware and threat intelligence feeds, GreyNoise specializes in tracking global scanning behavior, making it a valuable companion to tools like Shodan for attack surface monitoring and MISP for IoC correlation.
8. OpenPhish
In 2025, the sophistication of phishing attacks continues to grow, with AI-generated phishing emails, deepfake-based scams, and more evasive credential theft techniques becoming widespread. As a result, real-time, automated phishing intelligence is more critical than ever, and OpenPhish remains a trusted free resource for identifying and mitigating these threats.
OpenPhish’ home page
Unlike Cisco Talos or AlienVault OTX, which provide generalized threat intelligence, OpenPhish is specifically designed to detect and analyze phishing sites in real-time. It uses automated crawling and machine learning-based detection to continuously update its database of known phishing URLs. Security teams often integrate OpenPhish with tools like VirusTotal for malware analysis, MISP for threat intelligence sharing, and GreyNoise for contextual enrichment, making it an essential component of phishing defense strategies.
Key Free Features:
- Real-Time Phishing URL Feeds – Automatically detects and lists newly discovered phishing sites.
- Machine Learning-Based Detection – Uses AI-driven analysis to identify malicious domains and phishing campaigns.
- Free Phishing URL Lookup – Allows security teams to check whether a URL is associated with phishing activity.
- Threat Intelligence Integration – Compatible with SIEM, SOAR, and TIP platforms for streamlined phishing detection.
- Regularly Updated Threat Feeds – Provides a continuous stream of new phishing sites, helping organizations proactively block malicious domains.
With phishing attacks increasingly bypassing traditional email security measures, OpenPhish’s free real-time feeds and automated phishing detection capabilities remain critical in 2025 for organizations looking to stay ahead of evolving threats.
9. URLhaus
The fight against malware distribution via malicious URLs has become even more challenging, with cybercriminals using short-lived domains, and compromised legitimate sites to evade detection. URLhaus, a project by abuse.ch, remains a go-to free resource for security teams looking to identify and take down malware-hosting URLs in real time.
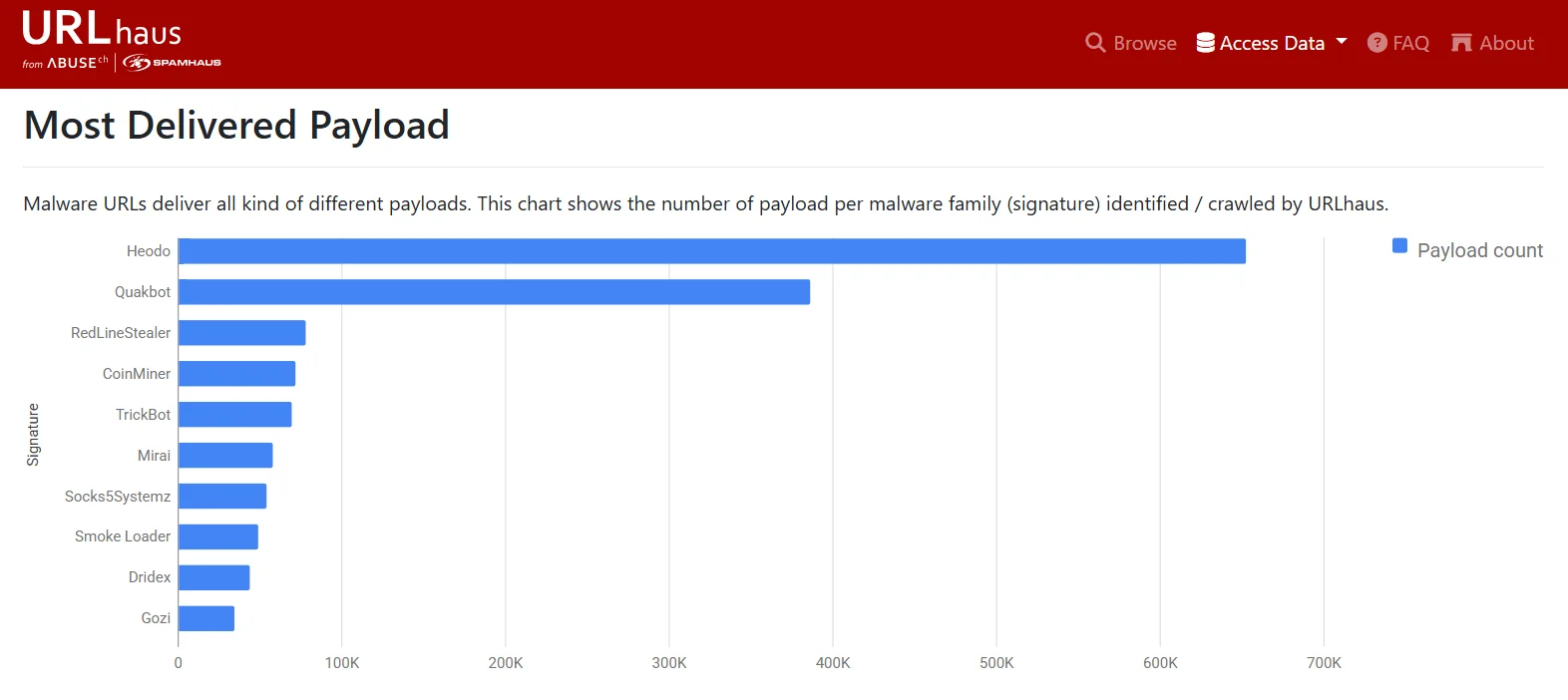
Unlike OpenPhish, which focuses on phishing-specific threats, URLhaus specializes in tracking malware distribution networks. Security professionals often integrate it with VirusTotal for scanning suspicious URLs, MISP for threat intelligence sharing, and GreyNoise for additional context on malicious IPs. As threat actors rapidly shift their infrastructure, URLhaus’s community-driven approach ensures a continuously updated list of dangerous URLs.
Key Free Features:
- Real-Time Malware URL Feeds – Continuously updated database of malicious URLs used to distribute malware.
- Community-Driven Intelligence – Security researchers and analysts contribute new malware URLs, strengthening collective defense.
- Automated URL Submissions – Allows organizations to report and analyze suspicious URLs in bulk.
- Threat Intelligence Integrations – Compatible with SIEM, SOAR, and TIPs, enabling automated blocking of malicious domains.
- Fast Takedown Requests – Works with hosting providers to quickly take down active malware distribution sites.
As threat actors increasingly use automation and fast-flux hosting to rotate malicious domains, URLhaus remains a critical free resource in 2025, helping organizations track, block, and disrupt malware campaigns in real time.
10. CISA Known Exploited Vulnerabilities (KEV) Catalog
In 2025, as attackers increasingly exploit zero-days and unpatched vulnerabilities, the need for real-time, authoritative vulnerability intelligence has never been greater. The CISA Known Exploited Vulnerabilities (KEV) Catalog remains a critical free resource for security teams looking to prioritize patching efforts based on real-world exploitation.

CISA
Unlike general vulnerability databases like CVE or NVD, CISA KEV focuses exclusively on vulnerabilities that are actively exploited in the wild. It helps organizations cut through the noise by highlighting high-risk flaws that pose an immediate threat. Security teams often integrate KEV data with Shodan for exposed assets, Cisco Talos for threat intelligence correlation, and MISP for vulnerability tracking, making it an essential tool for cyber defense and risk management.
Key Free Features in 2025:
- Authoritative Exploited Vulnerability List – Provides a curated list of vulnerabilities confirmed to be actively exploited.
- Real-Time Updates – Continuously updated with new high-risk CVEs based on observed exploitation.
- Mandatory Compliance for U.S. Federal Agencies – Serves as a benchmark for vulnerability remediation policies.
- Integration with Security Tools – Supports SIEM, SOAR, and vulnerability management platforms for automated alerting.
- Prioritization for Patch Management – Helps organizations focus on fixing the most critical security flaws first.
With ransomware groups, APTs, and botnets increasingly targeting known vulnerabilities, CISA KEV remains an essential resource in 2025, helping organizations stay ahead of real-world threats and improve their vulnerability management strategies.
Bonus: SOCRadar Labs
In 2025, SOCRadar Labs continues to provide free cybersecurity tools and research to help security teams analyze threats, track vulnerabilities, and strengthen defenses. Offering resources like attack surface monitoring, threat intelligence feeds, and dark web insights, SOCRadar Labs remains a valuable addition to any defender’s toolkit.
For an extensive range of free cybersecurity tools, check out SOCRadar Labs.
Conclusion
The cyber threat intelligence landscape in 2025 continues to evolve, with threat actors leveraging automation, AI-driven attacks, and rapidly shifting infrastructure. Staying informed and using the right intelligence sources is more important than ever. Whether monitoring for malware trends, phishing campaigns, or exploited vulnerabilities, the tools listed in this article help organizations proactively defend against modern cyber threats.
It’s important to note that this top 10 list doesn’t aim to compare or rank the tools. Rather, it’s a curated collection of useful resources that we believe will be valuable for security teams in 2025. These tools serve as critical components in any comprehensive defense strategy, offering insights into the evolving threat landscape.




































