
Top 10 Phishing Attacks of 2024: Lessons Learned from a Year of Cyber Deception
Phishing remains one of the most common cyber threats, with attackers constantly refining their methods to exploit human and technological flaws. In 2024, phishing attacks have become more sophisticated, utilizing cutting-edge technologies such as artificial intelligence and deepfake tools to deceive even the most cautious users. These schemes, which range from individual targeting to organizational infiltration, pose significant risks to personal data, financial resources, and critical infrastructure.
According to the SOCRadar 2024 End of the Year Threat Report, phishing campaigns reached alarming proportions, with over 576,100 unique websites targeted, resulting in the detection of 2.9 million malicious domains. These campaigns used 3.2 million IP addresses to create 31,746 fake login pages.
Cryptocurrency and NFT sectors bore the brunt, with 19.11% of attacks targeting them, followed by Information Services at 18.95% and National Security sectors at 12.63%.
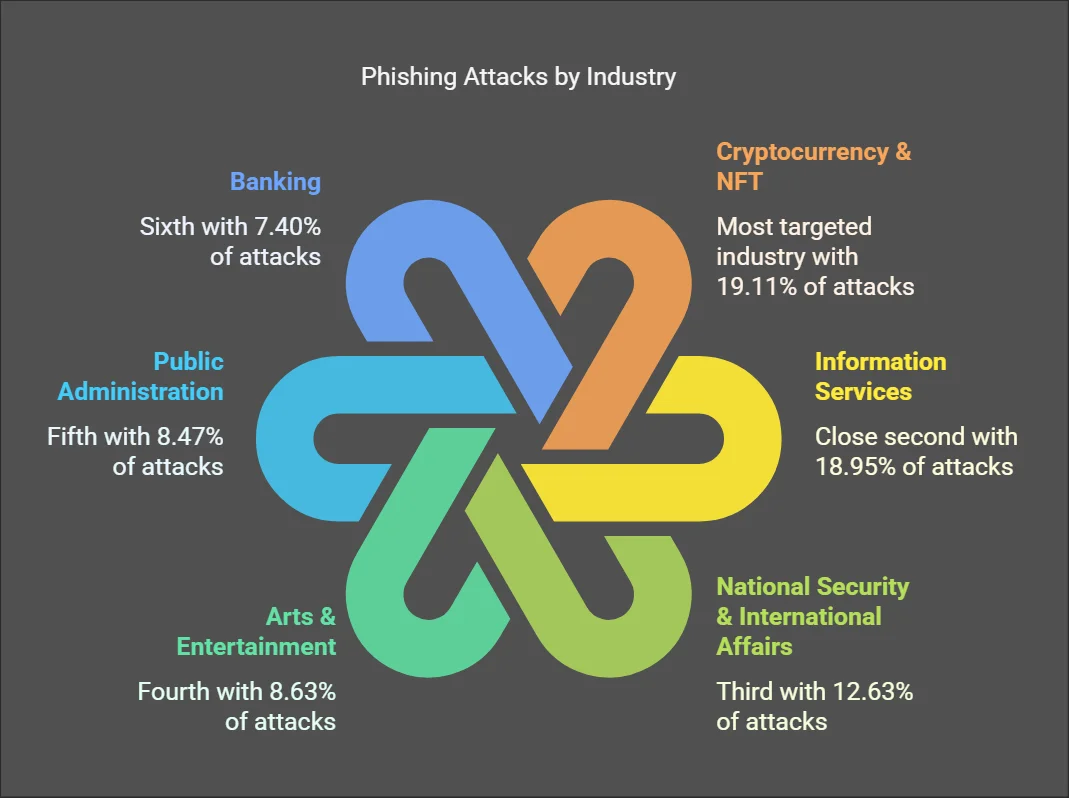
Phishing attacks industry distribution
Additionally, the report highlights that over 72% of phishing campaigns utilized advanced social engineering techniques, while 48% integrated AI-driven tools to craft convincing phishing emails. The United States experienced the highest number of phishing attacks globally, accounting for 34.89% of incidents, emphasizing the geographic and industry-specific concentration of these threats.
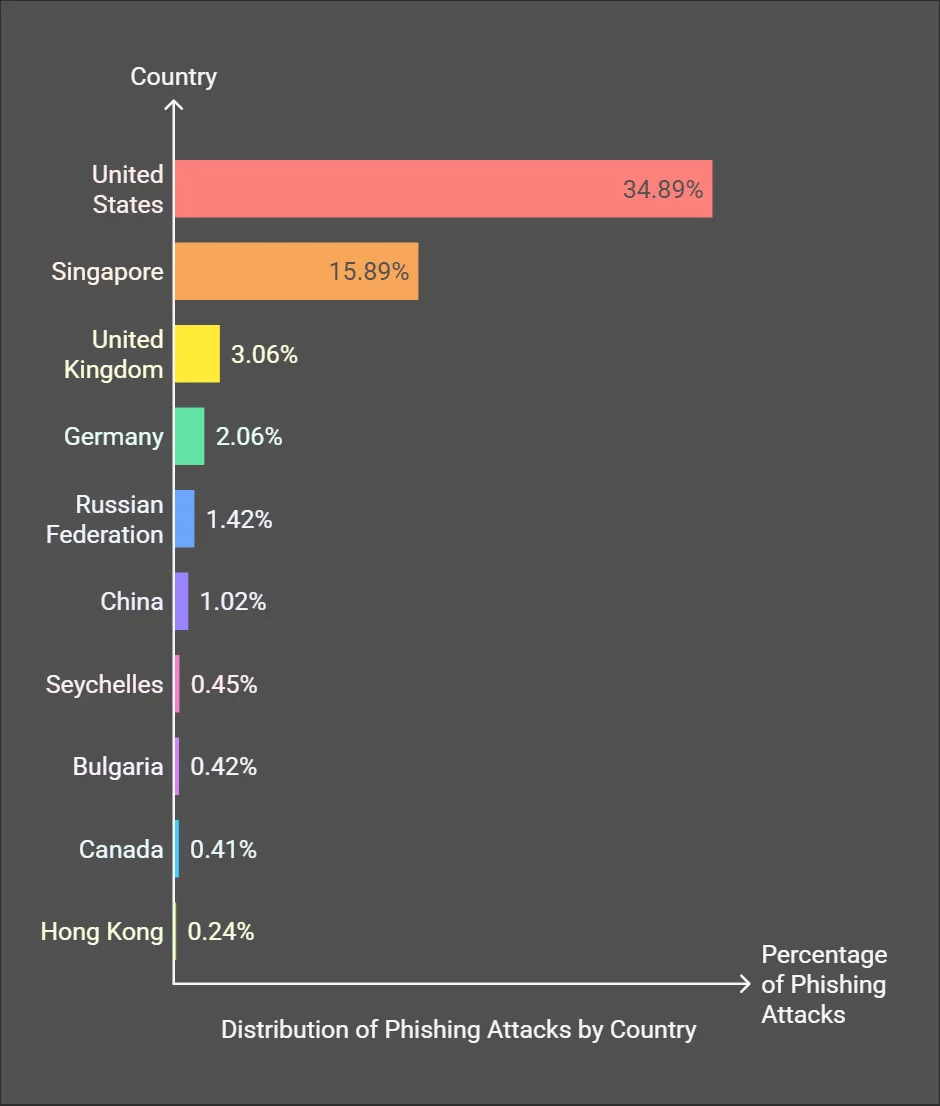
Phishing attacks targeted countries distribution
To combat the escalating phishing threats discussed in this blog, SOCRadar provides the Phishing Radar tool, a next-generation solution based on a strong big data platform. Phishing Radar detects domain spoofing and phishing campaigns using advanced machine learning and behavioral analytics by generating potential domain name variations and scanning global databases for malicious activity.
Explore phishing campaigns effortlessly with SOCRadar’s Phishing Radar – detect domain spoofing and protect your organization with advanced analytics
Phishing campaigns in 2024 included the strategic use of government (.gov) top-level domains (TLDs) around the world. According to a recent report, threat actors used vulnerabilities in.gov websites, such as open redirects and malicious content, to bypass secure email gateways (SEGs) and deceive unsuspecting users. Over 60% of these abuses were caused by vulnerabilities such as CVE-2024-25608, which affect the Liferay platform that is widely used by government organizations.
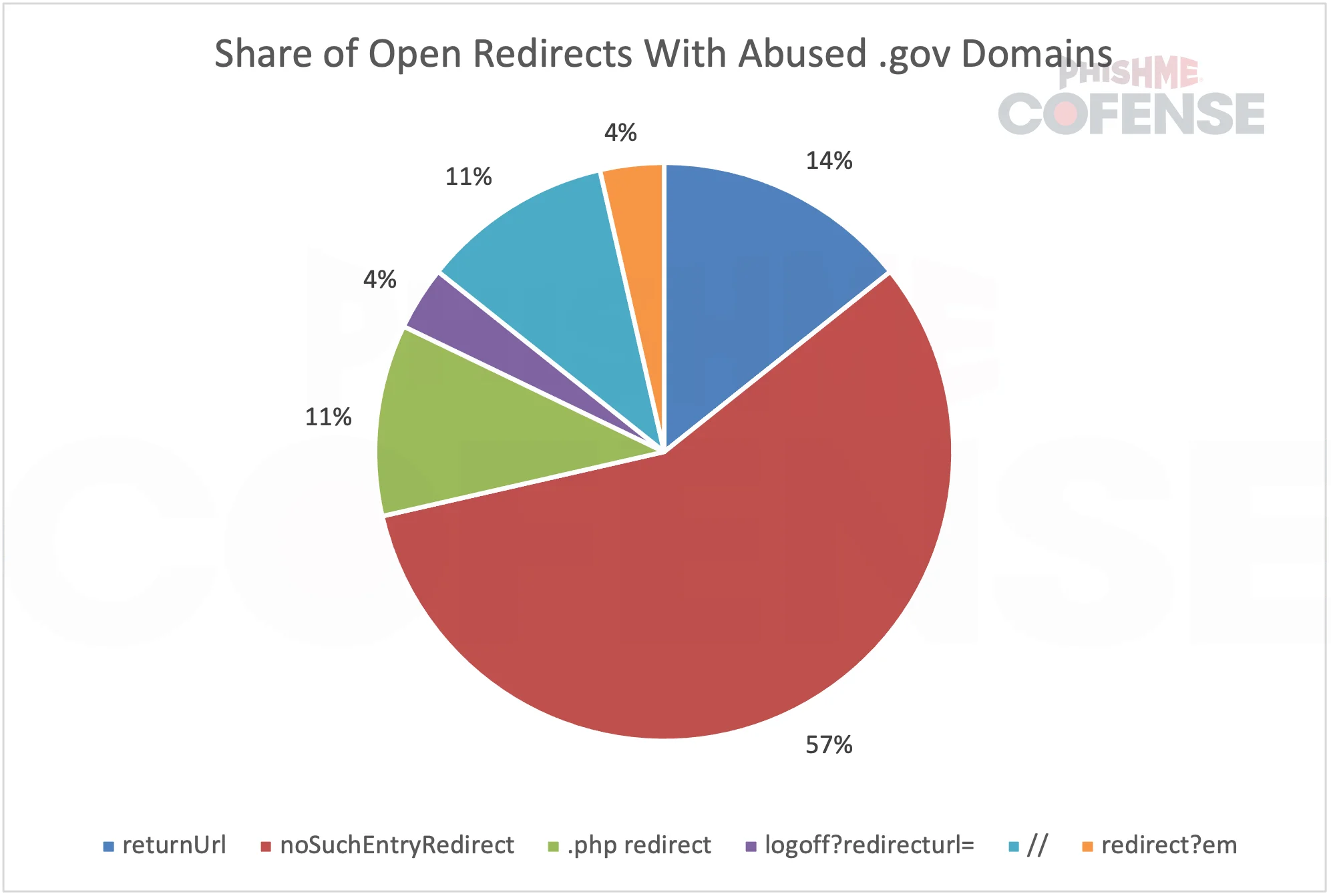
Breakdown of open redirect methods observed in abused .gov domains, with ‘noSuchEntryRedirect’ accounting for around 60% of cases. (Source: Cofense Intelligence)
Notably, government domains from Brazil and the United States were among the most exploited, demonstrating the global scope of this problem. This exploitation of.gov TLDs demonstrates how cybercriminals exploit trust in government domains to launch more successful phishing attacks.
This blog explores the top 10 phishing attacks of 2024, highlighting their methods, impact, and lessons learned. By understanding these incidents, you can better prepare yourself and your organization against the ever-changing tactics of cybercriminals.
1- How Cybercriminals Exploited Chrome Extensions
A recent phishing attack targeted Cyberhaven’s Chrome extension, compromising thousands of users through a malicious update. Attackers gained access by tricking an employee with a phishing email that mimicked official communication from the Chrome Web Store. This allowed them to inject malicious code into the extension, which exfiltrated sensitive information like cookies and authentication tokens. Over 600,000 users across various extensions were impacted, as attackers exploited OAuth flows and permissions to bypass security measures.
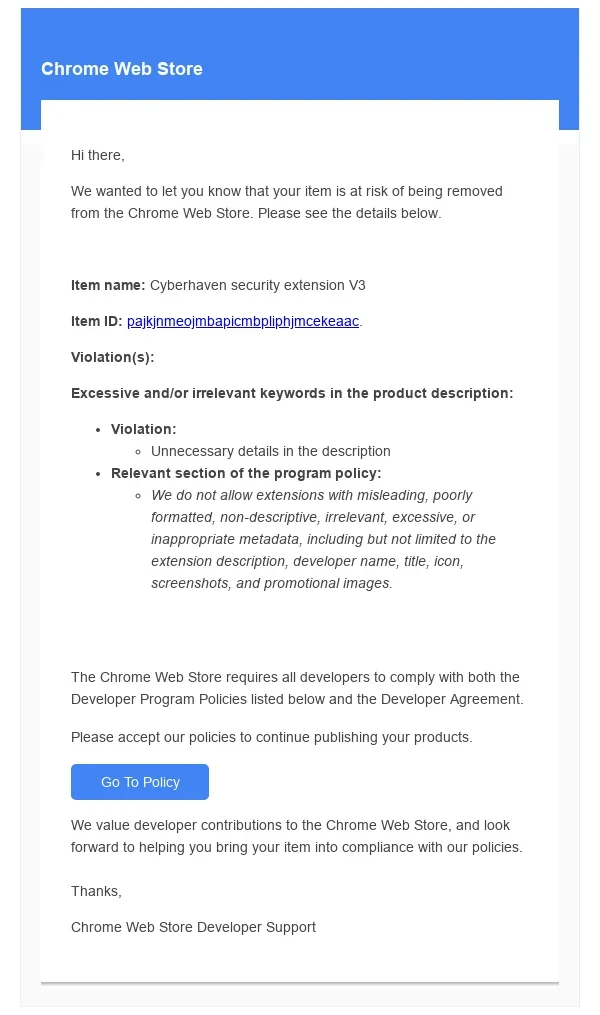
Phishing email by Chrome Web Store (Source: Cyberhaven)
Cyberhaven swiftly mitigated the attack by removing the compromised extension, releasing a secure update, and notifying affected users. They recommended users update to the latest version, revoke compromised credentials, and monitor browser logs for suspicious activity. This incident underscores the importance of vigilance in handling browser extensions, especially as investigations reveal the breach’s broader scope, affecting millions globally.
2- Phishing Campaign Exploits Roundcube Flaw to Target Governments
In June 2024, attackers exploited a vulnerability (CVE-2024-37383) in Roundcube Webmail to target government organizations in the CIS region. This medium-severity flaw allowed malicious actors to embed JavaScript in emails, bypassing security filters to execute cross-site scripting (XSS) attacks. The attackers tricked victims into providing sensitive credentials via fake login forms injected into Roundcube’s interface, which were then exfiltrated to malicious servers.
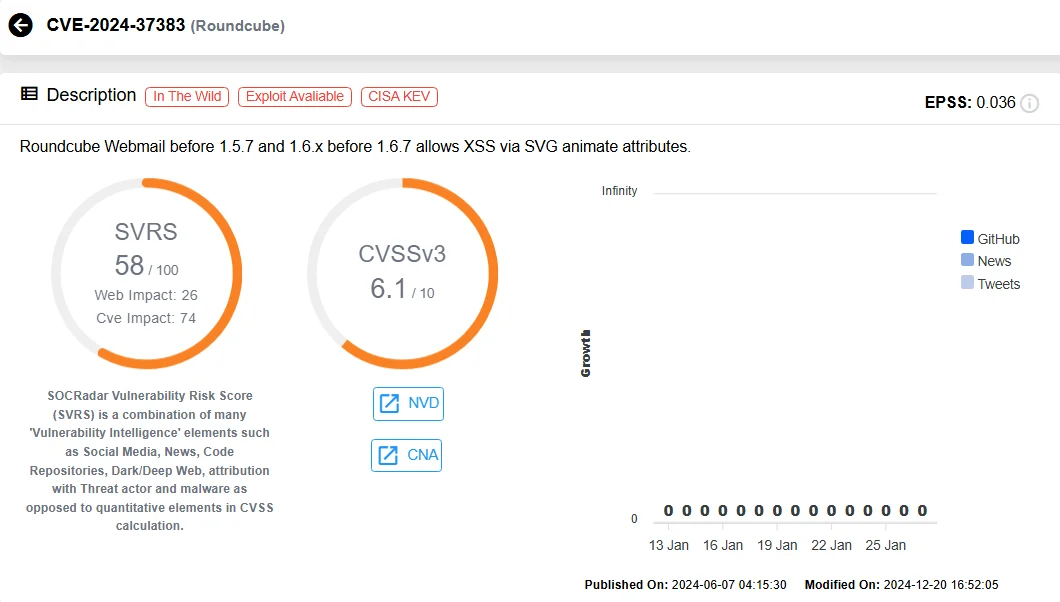
Details of CVE-2024-37383 (SOCRadar Vulnerability Intelligence)
Researchers discovered that phishing emails leveraged the vulnerability by embedding deceptive JavaScript payloads, often disguised within blank email attachments. These payloads enabled attackers to deploy fake login prompts, leading users to inadvertently disclose their credentials. The stolen information was sent to domains like libcdn.org, which served as command-and-control servers for the campaign.
To counter this threat, organizations using Roundcube are urged to update to patched versions (1.5.7 or 1.6.7 and newer) and implement monitoring tools to detect and mitigate suspicious activities. The attack highlights the importance of proactive vulnerability management and user education to defend against evolving phishing techniques.
3- European Retailer Pepco Loses Millions in Phishing Scam
Pepco Group, a European retailer operating brands like Poundland and Dealz, suffered a significant financial loss of €15.5 million due to a sophisticated phishing attack in Hungary. The attackers, likely employing Business Email Compromise (BEC) tactics, tricked the company into transferring funds to fraudulent accounts. This form of social engineering involved impersonating legitimate employees and manipulating payment processes, highlighting vulnerabilities in organizational communication protocols.

Pepco Retailer (Source: Pepco)
Experts noted that the use of AI tools may have facilitated the scam, enabling the creation of highly convincing phishing emails without grammatical errors, mimicking authentic correspondence. As the attack unfolded, Pepco launched investigations in collaboration with banking partners and law enforcement to recover the funds and secure their systems.
To avoid similar incidents, organizations should provide rigorous staff training, particularly for finance and accounting employees. Standardized payment verification processes, such as double-checking email transfer requests, can help to reduce risks. Pepco’s experience demonstrates the critical importance of strong security measures in combating increasingly sophisticated phishing attacks.
4- Russian Group Star Blizzard Exploits WhatsApp in Spear Phishing Campaign
Cybersecurity experts have identified a new spear phishing campaign by the Russian state-sponsored group Star Blizzard (also known as UNC4057 or Callisto), which leverages WhatsApp to compromise user accounts. Historically targeting diplomats and government officials, Star Blizzard has shifted focus to exploiting WhatsApp through malicious QR codes, enabling account takeover and exfiltration of sensitive information.
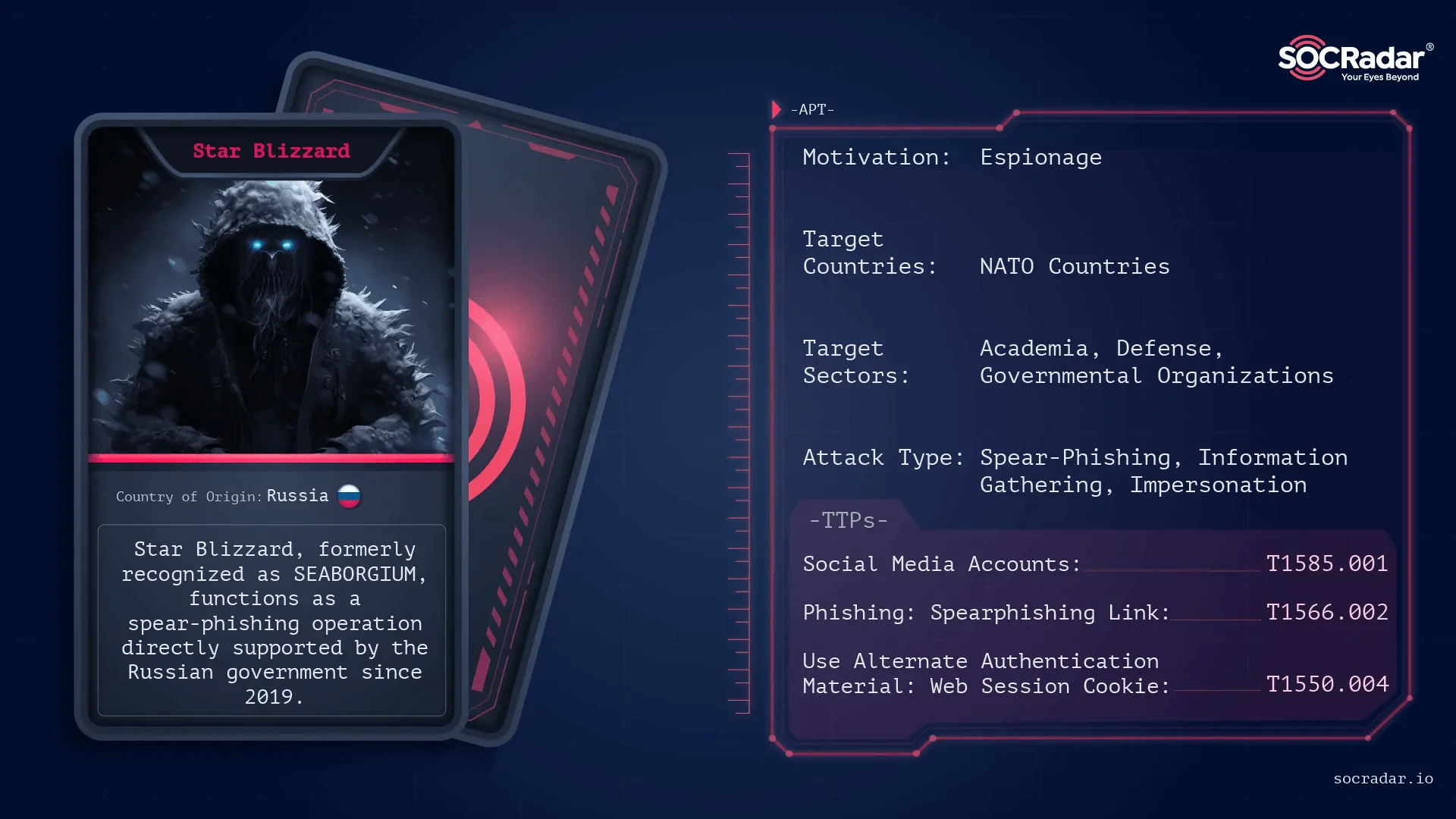
Threat actor card of Star Blizzard
This campaign, detected in November 2024, begins with phishing emails impersonating U.S. government officials. These emails invite victims to join fake WhatsApp groups supporting Ukrainian NGOs and include deliberately broken QR codes to prompt follow-up communication. When victims respond, attackers provide a shortened URL leading to a fraudulent WhatsApp invitation page with a malicious QR code. Scanning the code links the victim’s device to the attackers’ WhatsApp Web session, granting access to private conversations and data.
Experts warn that this attack, which relies on social engineering instead of malware, is particularly insidious and harder to detect. To mitigate risks, users should verify email authenticity, avoid scanning unsolicited QR codes, and regularly check WhatsApp’s “Linked Devices” section for unauthorized access. Organizations should also adopt robust security protocols, including phishing-resistant MFA and cybersecurity awareness training. Read more about How Star Blizzard Exploits WhatsApp in Spear Phishing Campaign.
5- New Phishing Campaign Delivers Keylogger Disguised as Bank Payment Notice
A phishing campaign discovered in March 2024 has been observed using a novel loader malware to distribute the Agent Tesla information stealer and keylogger. The attack begins with phishing emails impersonating bank payment notifications, urging recipients to open an attached archive file. The archive conceals a malicious .NET-based loader designed to evade detection through obfuscation and polymorphic behavior.
Once executed, the loader bypasses antivirus defenses and the Windows Antimalware Scan Interface (AMSI), retrieving the XOR-encoded Agent Tesla payload from a remote server. The malware then exfiltrates sensitive data via SMTP using a compromised email account, providing anonymity to the attackers. These sophisticated tactics ensure stealthy execution and make it challenging to trace the attack back to its source.
Combat cybercriminals’ evolving tactics with SOCRadar’s Operational Intelligence module, which provides real-time insights into the threat landscape. SOCRadar generates detailed profiles of threat actors, such as Agent Tesla, and maps them against the MITRE ATT&CK Framework to reveal their Tactics, Techniques, and Procedures (TTPs).
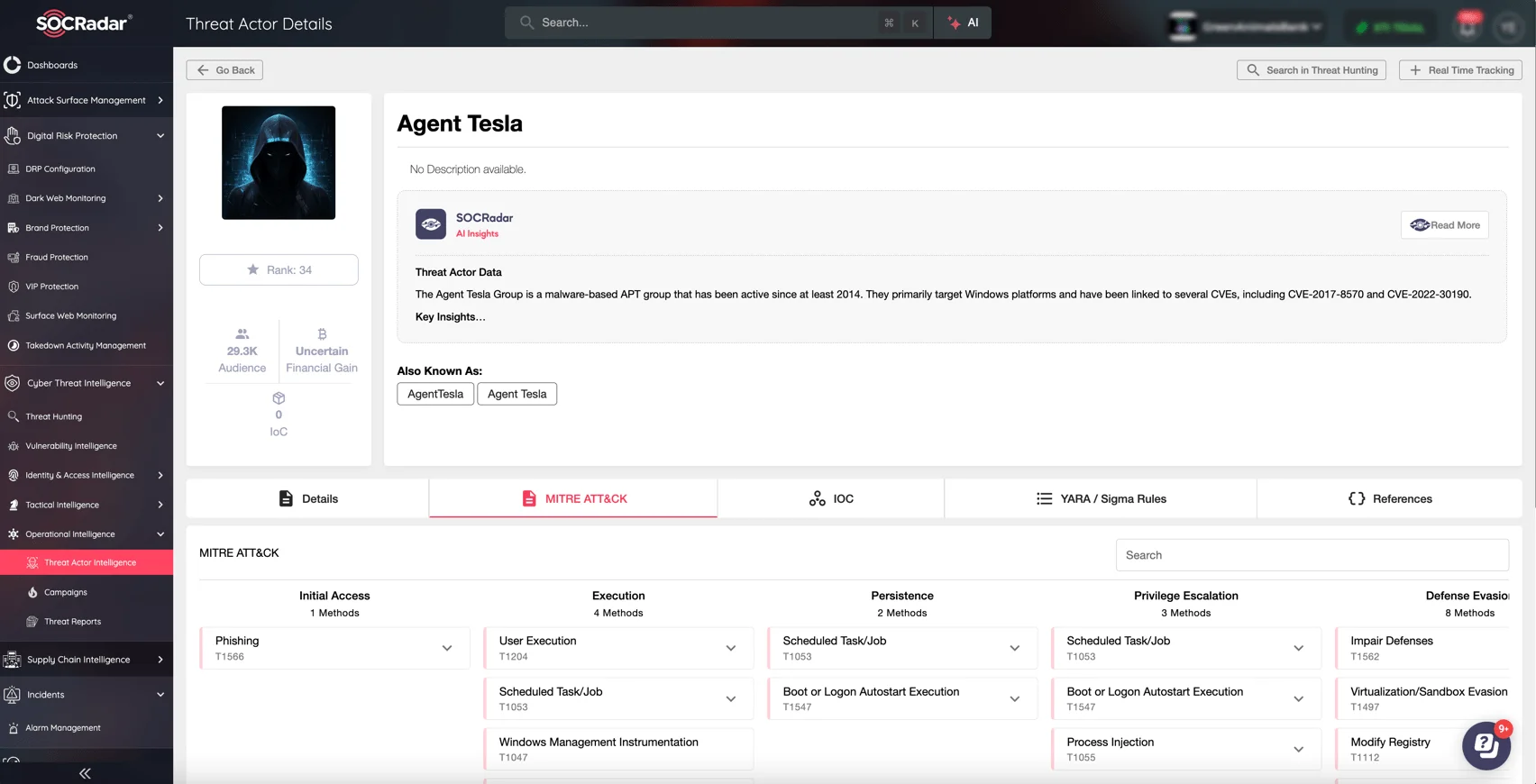
SOCRadar’s Threat Actor Intelligence module provides in-depth profiles, MITRE ATT&CK mappings, and actionable insights to track adversaries like Agent Tesla effectively.
Stay ahead with actionable intelligence, which includes dynamic data on recent campaigns, targeted industries, and geographic attack trends. Whether analyzing malware like Agent Tesla or tracking ransomware groups, SOCRadar converts raw threat data into actionable insights to strengthen your defenses.
6- North Korean Hackers Spoof Trusted Email Sources in Phishing Campaign
In May 2024, U.S. government agencies, including the NSA and FBI, issued a cybersecurity advisory warning about North Korean hackers exploiting weak DMARC configurations to send spoofed emails. These spear phishing campaigns, attributed to the Kimsuky group (also known as APT43 or TA427), target experts in foreign policy, nuclear disarmament, and U.S.-South Korea relations.
The attackers impersonate trusted entities using improperly configured DMARC records, allowing emails to bypass security filters. Victims are often engaged in extended benign conversations to build trust before attackers request sensitive opinions or analysis. Kimsuky has also been observed spoofing email reply-to fields, enhancing their deception.
A highlighted incident involved hackers posing as journalists to solicit responses on North Korean nuclear strategies, directing replies to fake accounts. The compromised journalist’s email added legitimacy, increasing the chance of victim engagement. Organizations are urged to enforce strict DMARC policies, rejecting emails that fail authentication checks, and monitor for suspicious interactions to mitigate such risks.
7- CEO Fraud with Deepfake Audio Costs UK Company $243,000
A sophisticated CEO fraud involving deepfake audio led to the theft of $243,000 from a U.K.-based energy company. In March 2024, cybercriminals used AI-powered voice generation to impersonate the CEO of the company’s parent organization. They instructed the U.K. company’s CEO to urgently transfer funds to a Hungary-based supplier, promising reimbursement.

AI illustration of CEO deepfake audio fraud
After the initial payment was forwarded through multiple accounts, including one in Mexico, the attackers attempted further fraud through follow-up calls. The U.K. CEO grew suspicious during the third call, noticing the use of an Austrian phone number, and halted any further transactions.
8- Ticket Heist Campaign Targets Paris 2024 Olympics
The Ticket Heist campaign, active since 2022, targets ticket buyers for major events like the Paris 2024 Olympics and UEFA EURO 2024. Researchers uncovered a network of 708 fraudulent domains impersonating official ticketing websites, luring users into purchasing fake tickets. Russian-speaking individuals were the primary targets, though English-speaking and Chinese-speaking users were also affected.
The fraudulent websites feature high-quality design to mimic legitimate platforms, including options to choose events, seats, and accommodation. Victims face inflated ticket prices, with costs exceeding €300 and sometimes reaching €1,000. The campaign’s sophistication suggests significant effort by attackers to maximize success.
9- Phishing Attacks in Progressive Web Apps (PWAs)
In 2024, phishing campaigns targeting mobile banking apps introduced a novel technique involving Progressive Web Apps (PWAs). This method, highlighted by SOCRadar Campaigns and analyzed by ESET researchers, impacts both iOS and Android users. Attackers create PWAs that imitate legitimate mobile banking apps, bypassing traditional app store security checks.
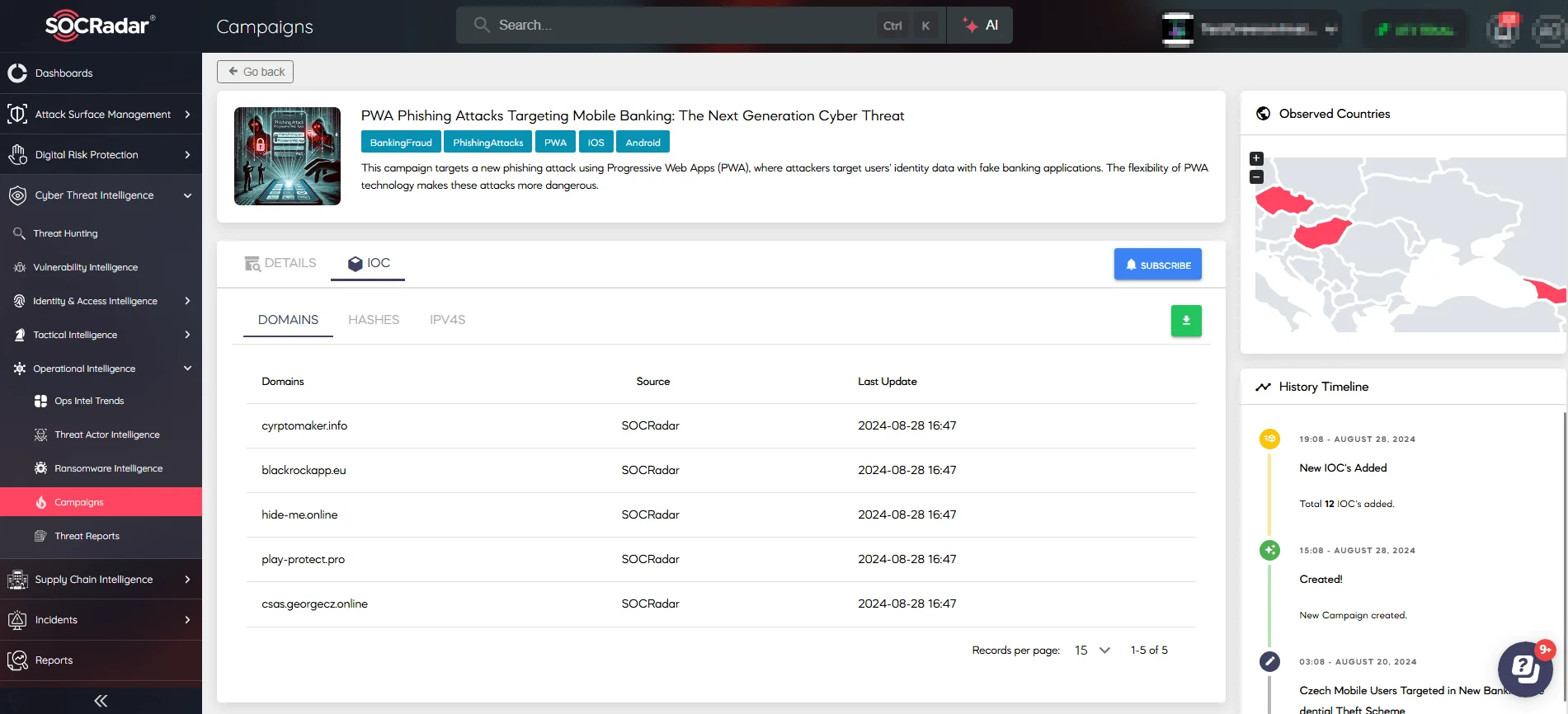
SOCRadar’s Campaigns PWA phishing attack targeting mobile banking
Android users face added risk due to WebAPK technology, where PWAs mimic apps downloaded from Google Play. On both platforms, phishing PWAs prompt victims to enter banking credentials, which are then exfiltrated to command-and-control (C&C) servers. Campaigns targeted banks in Czechia, Hungary, and Georgia, indicating a focused attack strategy.
This phishing method combines malvertising, SMS, and automated calls to deliver malicious links. The attacks emphasize the importance of scrutinizing app installation requests and using multi-factor authentication to safeguard sensitive information.
10- Phishing with Cloudflare Workers Targets Login Credentials
Phishing campaigns exploiting Cloudflare Workers, highlighted by SOCRadar’s Campaigns, used techniques such as HTML smuggling and transparent phishing. These methods enable attackers to bypass detection and intercept sensitive login credentials.
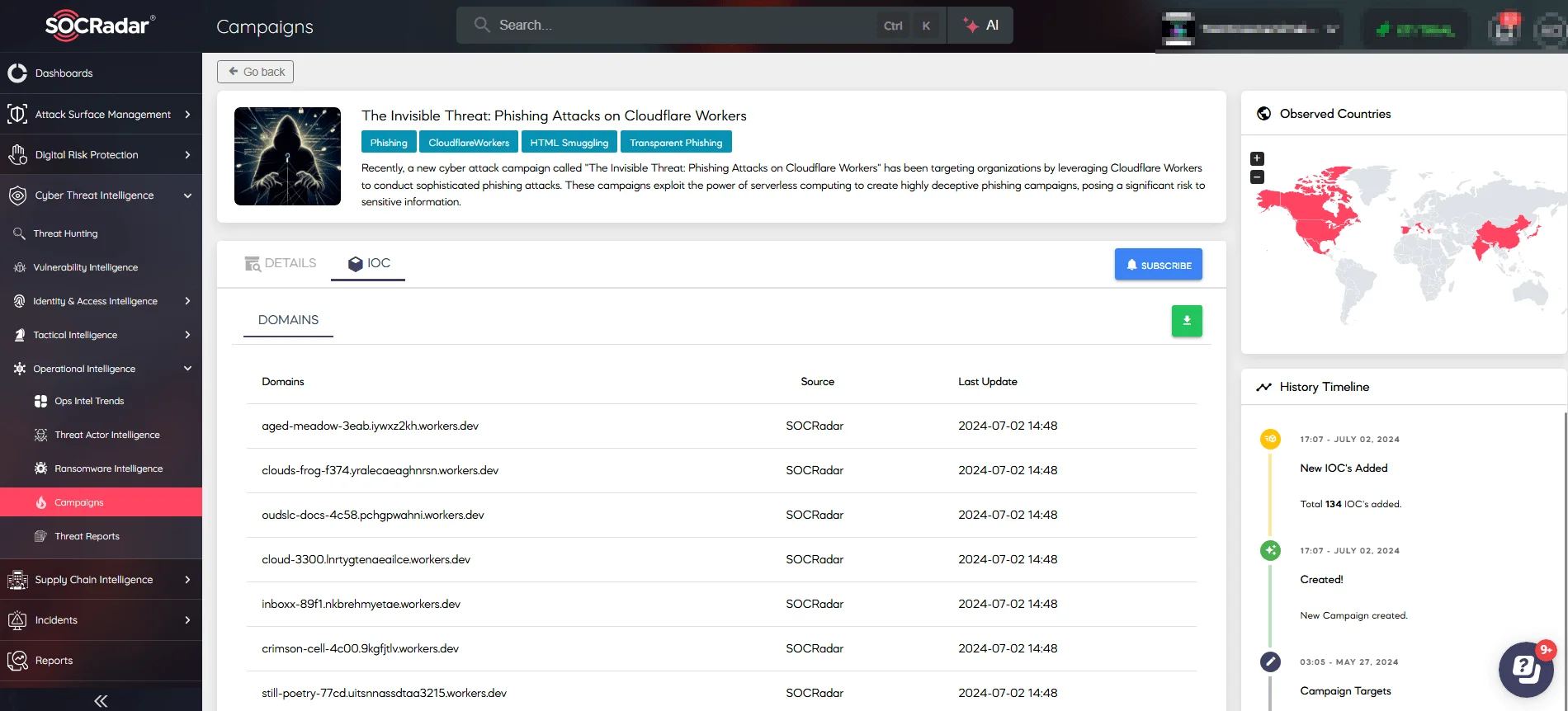
SOCRadar’s Campaigns Cloudflare workers phishing attack
HTML smuggling involves encoding phishing pages in Base64, which are reconstructed in victims’ browsers to evade network defenses. Transparent phishing employs a man-in-the-middle strategy, where attackers use Cloudflare Workers to mimic legitimate login pages and capture credentials, cookies, and tokens during real-time interactions.
These campaigns primarily targeted Microsoft, Gmail, Yahoo Mail, and cPanel Webmail users across Asia, North America, and Southern Europe. To mitigate these threats, organizations should implement URL filtering, inspect network traffic, and educate users on recognizing phishing links. Researchers recommended inspecting HTTP/HTTPS traffic, deploying URL filtering, and implementing Remote Browser Isolation (RBI) to mitigate threats. Users should verify URLs before accessing sensitive accounts and avoid interacting with links from untrusted sources.




































