
What are Threat Hunting Tools?
Threat hunting is how computer security specialists aggressively seek out and eliminate cyber dangers that have infiltrated their computer network invisibly. Threat hunting is searching for new possible risks and vulnerabilities beyond recognized alerts or malicious attacks.
Threat hunting’s objective is to transform operational obstacles into strengths. It is a force multiplier in threat intelligence, security operations, and incident response. A frequent adage in incident response is “it is not an issue of IF, but “WHEN” your network will be hacked.”
Threat hunting offers a different approach — assume that a threat has already happened but has gone unnoticed. By proactively recognizing breaches and detecting malicious activity that automated tools miss, companies may reduce threats and leverage the insights to strengthen their security posture.
What is the Difference Between Threat Hunting and Incident Response?
By their very nature, incident response systems are reactive. In most cases, an intrusion detection system or procedure issues an alarm, and operators swarm the issue until the danger is neutralized and the resulting harm is reduced. On the other hand, threat hunting is a proactive, hypothesis-driven activity that aims to discover and eradicate threats that have already entered an organization’s network or critical systems.
That is not to imply that threat hunting is just a detection exercise; it is also a hypothesis-driven approach to prevention. The most successful threat hunting occurs when it can inform an organization’s security posture, hardening attack surfaces to avoid problems before they occur.
Whereas a comprehensive incident response capability relies on rapid incident detection and the capacity to triage and fix issues as they arise, threat hunting is most effective when influencing system architecture and configuration changes. This mitigates risk and strengthens incident response mechanisms in the event of future assaults.
What are Threat Hunting Tools?
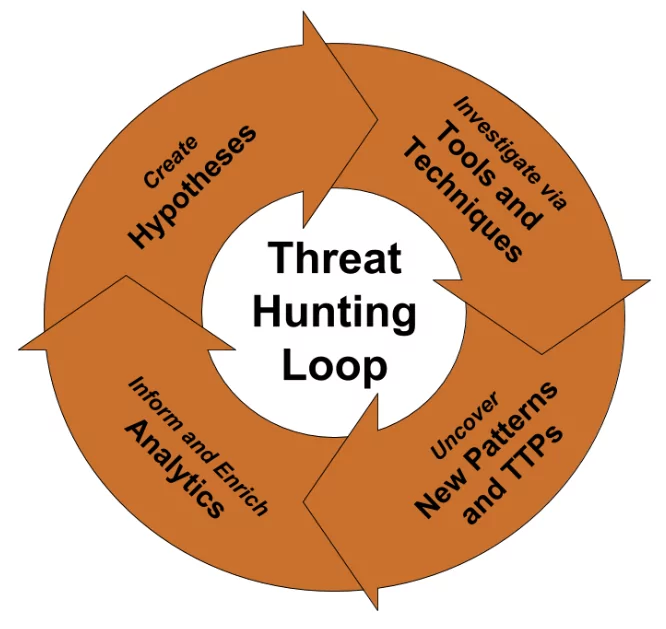
To begin threat hunting, companies should concentrate on three essential steps:
- Developing a hypothesis.
- Carrying out the theory, and ultimately.
- Extensively experimenting and testing to achieve findings.
As with any scientific approach, hypotheses should be actionable, testable, and subjected to ongoing scrutiny for validity by the analysts who generate them and the team.
As previously stated, testing a theory in threat hunting typically compares it to Indicators of Compromise (IoCs). Observing and analyzing signs such as privileged user activity, login attempts, HTML answers, registry changes, port access abnormalities, or use patterns that depart from established regional and seasonal trends can all assist threat hunters in validating their ideas.
Maintaining a current state of knowledge is one of a danger hunter’s best abilities. The cybersecurity sector is awash with blogs, threat reports, and white papers, which may be valuable to threat hunters looking to keep an update—maintaining a thorough grasp of the sorts of attacks, malware, and mitigations that the industry encounters may go a long way toward developing more credible hypotheses and determining which threats are capable of overcoming intrusion detection and response systems.
Like consuming external knowledge sources, companies must preserve institutional knowledge on episodes that have previously occurred. Typically, attacks leave a trail of evidence pointing to the weaknesses that enabled them to appear. Robust endpointdetection and response systems can trace assaults from start to finish, significantly aiding future threat hunting actions.
Managed Detection and Response (MDR)
MDR identifies and remediates advanced threats through threat information and proactive threat hunting. This sort of security solution can assist shorten the dwell time of assaults and responding quickly and decisively to network threats.
SIEM
Security information and event management (SIEM) combine security information management (SIM) with security event management (SEM) to provide real-time monitoring and analysis of security events, as well as tracking and logging of security data. SIEMs can detect anomalous user activity and other abnormalities that serve as critical leads for further investigation.
Security Analytics
Security analytics strives to go above the capabilities of traditional SIEM systems by providing deeper insights into your security data. By combining the large amounts of data collected by security technologies with more sophisticated, quicker, and integrated machinelearning and artificialintelligence, security analytics may speed threat investigations by providing detailed observability data for cyber threat hunting.
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.



































