
What We Learned from Medibank Ransomware Incident
[Update] January 23, 2024: “Australian Government Imposes Sanctions on Medibank Ransomware Culprit”
[Update] December 2, 2022: On December 1, 2022, the hackers published another post declaring that they closed the case for Medibank by dumping more data on the dark web. The local post was published on November 30: “Happy Cyber Security Day!!! Added folder full. Case closed.”
In less than a month, Medibank is the second Australian business to experience a significant data breach after the telecommunications giant Optus. On October 12th, David Koczkar, the chief executive of Medibank, got an internal notification about suspicious behavior found on the network. Since then, the story of the hack and the data breach has evolved in several different directions, and new voices have joined the fray.
Timeline of the Medibank Attack
Medibank, one of the largest Australian private health insurance providers, released a statement about unusual activity in their network but stated that there was no evidence of compromised customer data found on October 13th. The statement also said some customer-facing systems would shut down to investigate and respond to the suspicious activity.
The next day, October 14th, Medibank sent an email to its customers. The email made the same points as the statement. In addition, it mentioned that Medibank was getting help from external cybersecurity experts, and they were in contact with relevant government agencies.
Five days after the initial incident, on October 17th, Medibank claimed that there was still no evidence of any customer data leaving their IT system in a new statement. However, in this statement, they admit that the unusual activity was consistent with ransomware, but they said nothing on their system was encrypted.
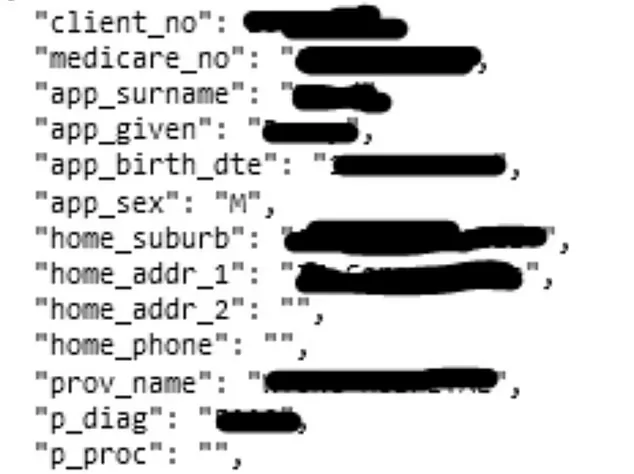
On October 19th, the hackers contacted Medibank with a sample of 100 customer records to show that customer data was compromised. Medibank issued another statement on October 20th about the 100 policies and admitted that information like first name and last name, address, date of birth, policy number, and phone numbers were compromised for these policies. But there was no evidence that threat actors stole credit card data. Medibank also said the stolen data came from their ahm and international student systems and did not say anything explicit about their other customers in the same statement.

From this point forward, things went from bad to worse for Medibank. After communicating with the hackers multiple times, Medibank released a statement accepting their direct customers may have also been affected by the breach after seeing more files shared with them. The next day, they confirmed that their direct customers were also affected, in addition to ahm and international customers.
In a statement on November 7th, they announced that attackers stole 9.7 million customers’ data in the breach. In addition, it said that the hackers contacted Medibank and wanted a $10 million ransom to avoid publishing the stolen data on the dark web. Still, Medibank refused the ransom demand in accordance with the extensive advice from cybersecurity experts and with the position of the Australian Government.
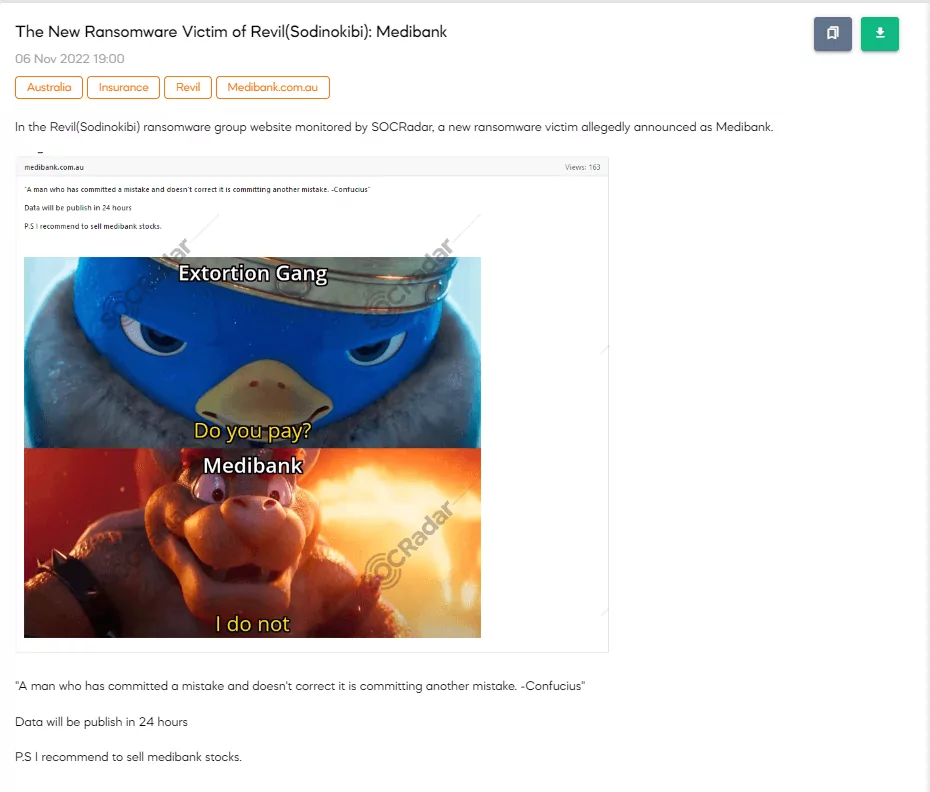
The hackers responded to this statement with a cryptic meme and said they would publish data in 24 hours on November 8th.
On November 9th, following through on their threats, the hackers released a portion of the stolen data from the breach. The information was in two categories, a “good list” and a “naughty list.” In the naughty list, there were the Medibank customers who had received medical attention for substance abuse, alcoholism, or mental disorders. The information is posted on a ransomware leak website linked to BlogXX, which is thought to be a reorganization of the former Russian ransomware gang REvil.

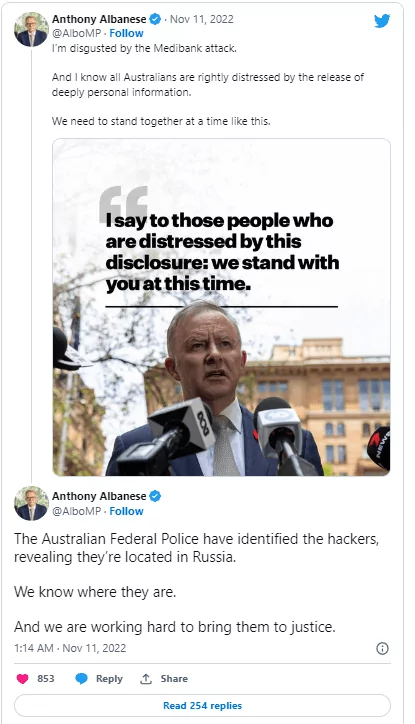
On November 11th, Australian Prime Minister Anthony Albanese claimed that Australian Federal police knew where Medibank attackers were and working hard to bring them to justice.
How did the Breach Happen?
The cyber attack affecting Medibank could be classified as a ransomware attack even though hackers did not / could not encrypt the data. During the exfiltration, the security team noticed the unusual activity. However, the hackers claimed they were in the IT systems for a month.
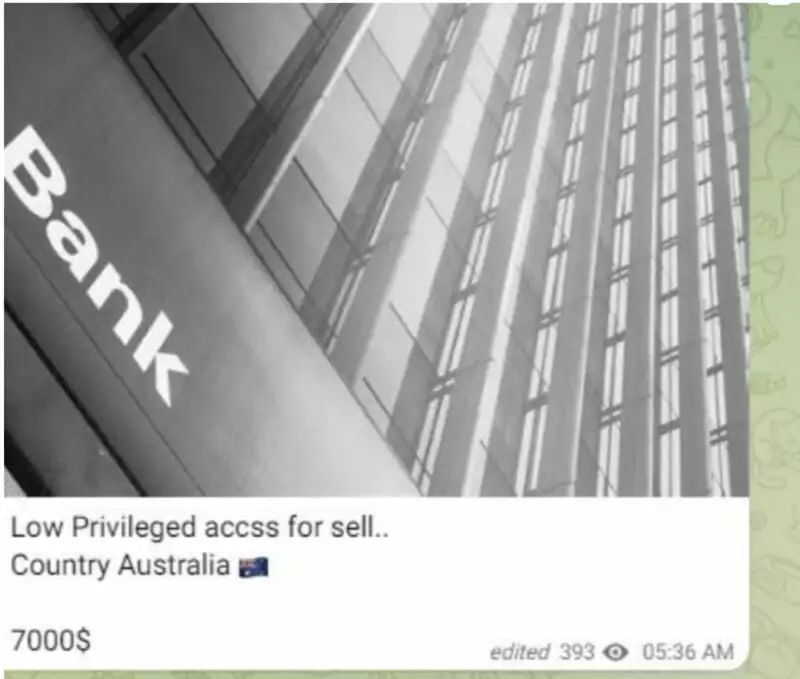
In ransomware attacks, the initial access point is generally gathered using phishing attacks. We do not know how threat actors stole the initial credentials in this attack. What we know is that the credential used for the attack was bought and sold in a Telegram channel. An unidentified bidder bought and sold these credentials on the dark web, then used them to access Medibank’s internal network.
Once inside, the threat actor located a customer database and then utilized the privileged credentials that were taken to develop a script to automate the exfiltration of customer data. After compressing 200 GB worth of data from Medibank’s systems to 5GB, they used two established backdoors to extract this stolen data from a zip file after compressing it. At this time, the security team at Medibank allegedly noticed unusual behavior and sealed both backdoors—but not before the data had been stolen.
How Could We Stop These Attacks?
After these kinds of attacks happen, there always be discussions about how this could have been prevented if this or that has been done, like network segmentation, multiple-factor authentication, implementing the principle of least privilege, etc. These are all best practices, and every person and company should practice them zealously. However, most of these precautions will only help after the attack starts. Recently, hackers have launched more complicated attacks and waited for the best time to execute the attacks and exfiltration. In the case of Medibank, hackers gained initial access a month before the exfiltration and used this time to get ready and establish the backdoors. When the security team discovered the attack, it was already too late.
As an Extended Threat Intelligence company, SOCRadar’s approach is to stop these attacks before they happen. SOCRadar analysts follow Telegram channels, forums, and markets on the dark web for our customers.
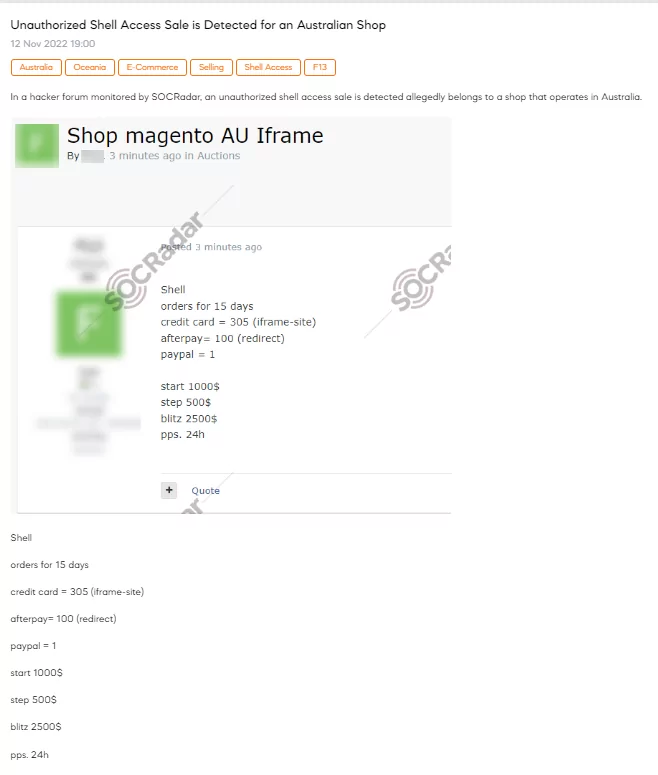
Australian Government Imposes Sanctions on Medibank Ransomware Culprit
The Australian government has invoked its cyber sanctions framework for the first time, legislated in 2021, to penalize Russian individual Aleksandr Ermakov for his involvement in the Medibank data breach.
The Australian Signals Directorate and the Australian Federal Police identified Ermakov as the culprit behind the Medibank attack, affecting the data of 9.7 million Medibank customers.
Under the sanctions, providing assets, including cryptocurrency and ransom payments, to Ermakov becomes a criminal offense, carrying a penalty of up to 10 years in prison. Authorities are actively pursuing further leads related to the Medibank attack, collaborating with cyber authorities in the US and UK to address the broader threat posed by “a number of Russian cyber gangs” targeting Australia.
How Could SOCRadar Help?
The actions taken by western countries against ransomware operators about a year ago created some serious reactions, one of which is that communication on the dark web has changed. Now, hackers prefer Telegram channels with smaller audiences. This move made gathering intel even for companies with resources to follow the dark web.
You could follow tens of Telegram channels, forums, and markets on the dark web in the SOCRadar platform, and you could learn about what was shared or talked about your company, industry, and country through SOCRadar notifications and alerts free for a year with SOCRadar freemium membership. Even better, you could experience more features with our 2-week trials.
References:
- https://www.theguardian.com/australia-news/2022/nov/12/medibank-v-the-hackers-how-the-health-insurer-fell-to-a-mass-data-theft
- https://techcrunch.com/2022/11/11/australia-tells-medibank-hackers-we-know-who-you-are/
- https://www.upguard.com/breaches/medibank-data-leak



































