The Year of Takedowns: Significant Law Enforcement Operations of 2024
As 2024 comes to a close, the global fight against cybercrime has witnessed a series of groundbreaking law enforcement operations that highlight the importance of international collaboration, and proactive intelligence gathering. From dismantling sophisticated ransomware groups to cracking down on Dark Web marketplaces, law enforcement agencies worldwide have successfully targeted criminal networks operating in the digital underworld. These operations have not only disrupted illegal activities but also reinforced the resilience of global cybersecurity frameworks.
This article provides a comprehensive overview of the most significant operations in 2024, showcasing how the collective efforts of governments, private sector organizations, and cybersecurity experts have shaped the year’s achievements in combating cybercrime.
You can get your Free Dark Web Report now!
January
Grandoreiro banking malware operation disrupted
Brazil’s Federal Police, in collaboration with cybersecurity researchers, have dismantled the Grandoreiro banking malware operation, active since 2017 and responsible for financial fraud targeting Spanish-speaking countries.
The operation received crucial support from Spain’s National Police, Caixa Bank, Interpol and ESET whose contributions were instrumental in identifying and apprehending those managing the malware’s infrastructure.
The Brazilian authorities reported five arrests and carried out thirteen search and seizure operations across Sao Paulo, Para, Mato Grosso, Santa Catarina and Goias.
50,000 Bitcoin from piracy site seized
Authorities in Saxony, eastern Germany, have secured 50,000 Bitcoin from the former operator of the piracy website Movie2k.to, following a voluntary transfer to a state-managed wallet.
Active between 2008 and 2013, Movie2k.to operated in a legal gray area, offering links for users—mainly English and German speakers—to stream or download movies and TV shows, without hosting any copyrighted content directly.
February
Warzone RAT infrastructure seized by FBI
The FBI has successfully dismantled the Warzone RAT malware operation, seizing its infrastructure and arresting two individuals linked to the cybercrime activities.
One of the suspects, 27-year-old Daniel Meli from Malta, was apprehended for his involvement in distributing Warzone RAT (also known as “AveMaria”), a remote access trojan extensively used in cybercrime.
First developed in 2018, Warzone RAT is a type of commodity malware equipped with numerous features that facilitate cybercriminal activities. These include UAC bypass, hidden remote desktop, password and cookie theft, keylogging, webcam recording, file manipulation, reverse proxy, remote shell, and process management.
International Operation Against LockBit ransomware
Law enforcement agencies from 10 countries have collaborated to dismantle the infamous LockBit ransomware operation in a coordinated effort called “Operation Cronos.”
A banner displayed on LockBit’s data leak website reveals that the site is now under the control of law enforcement.

A banner displayed on LockBit’s data leak website
LockBit Ransomware Members Arrested, Decryptor Released
Law enforcement arrested two LockBit ransomware operators in Poland and Ukraine, developed a free decryption tool to restore encrypted files, and seized over 200 cryptocurrency wallets after breaching the gang’s servers in a coordinated international crackdown.
The U.S. Justice Department unsealed two of these indictments, charging Russian nationals Artur Sungatov and Ivan Gennadievich Kondratiev (aka Bassterlord) for their roles in LockBit attacks.
March
German Police Seized Nemesis Market
German authorities have dismantled the infrastructure of the darknet cybercrime marketplace Nemesis Market, carrying out operations in Germany and Lithuania and effectively shutting down the platform.
On Wednesday, March 20, 2024, the Federal Criminal Police Office (BKA) and the Frankfurt Cybercrime Combating Unit (ZIT) executed the takedown, seizing the website and confiscating approximately $100,000 in cash.
Launched in 2021, Nemesis Market served as a hub for illicit activities, offering illegal drugs and narcotics, stolen data, credit cards, and cybercrime services, including ransomware, phishing, and distributed denial-of-service (DDoS) attack tools.
You can check our article on Top 10 Dark Web Markets for more information.
April
Phishing Service Provider LabHost Taken Down by Law Enforcement
On Thursday, April 18, 2024, the UK’s Metropolitan Police Service, in collaboration with international law enforcement agencies and trusted private sector partners, successfully dismantled the Phishing-as-a-Service (PhaaS) provider LabHost. The operation was strategically coordinated to coincide with several key arrests connected to the case.
LabHost, also known as LabRat, first appeared in late 2021 as a PhaaS platform. Over time, it expanded to offer a wide range of phishing pages targeting banks, prominent organizations, and service providers globally, with a particular focus on Canada, the US, and the UK.
By the time of its takedown, it had more than 2,000 criminal users who had deployed over 40,000 fraudulent websites.
LabHost Splash Page
You can analyze registered domain names globally for fakes and look-alikes to protect your organization with SOCRadar’s Phishing Domain Detection module.
May
LockBitSupp Unmasked
The leader of the LockBit cybercrime group has been identified and sanctioned by the UK, US, and Australia following an international disruption operation led by the National Crime Agency.
Dmitry Khoroshev, also known as LockBitSupp, who operated under the cover of anonymity and previously offered a $10 million reward for anyone uncovering his identity, now faces asset freezes and travel bans.
Additionally, US authorities have unsealed an indictment against him and are offering a reward of up to $10 million for information that leads to his arrest or conviction.

Dmitry Khoroshev
BreachForums Seized by FBI
The FBI has taken control of the BreachForums hacking forum, known for leaking and selling stolen data.
The seizure took place shortly after the forum was used to release data stolen from a Europol law enforcement portal.
In addition to the forum, the FBI has also seized its associated Telegram channel and other channels operated by Baphomet.

BreachForums Splash Page
Over 100 malware loader servers seized
An international law enforcement operation, dubbed Operation Endgame, has taken down over 100 servers worldwide that were being used by several major malware loader operations, including IcedID, Pikabot, Trickbot, Bumblebee, Smokeloader, and SystemBC.
The operation involved 16 searches across Europe, resulting in the arrest of four individuals—three in Ukraine and one in Armenia.
The seized infrastructure, spanning Europe and North America, hosted over 2,000 domains used for illicit activities, all of which are now under the control of authorities.
Operation Endgame was a collaborative effort involving law enforcement agencies from Germany, the United States, the United Kingdom, France, Denmark, and the Netherlands.
August
UK Shut Down ‘Russian Coms’
The United Kingdom’s National Crime Agency (NCA) has dismantled Russian Coms, a prominent caller ID spoofing platform exploited by hundreds of criminals to carry out approximately 2 million scam calls.
Victims spanned more than 107 countries, including the United Kingdom, the United States, New Zealand, Norway, and France.
Advertised on platforms like Snapchat, Instagram, and Telegram, Russian Coms initially operated as a handset service and later evolved into a web app.
Cryptonator taken down for laundering ransom payments and stolen cryptocurrency
U.S. and German law enforcement authorities have successfully seized the domain of the cryptocurrency wallet platform Cryptonator, a service reportedly utilized by ransomware operators, darknet marketplaces, and other illicit entities. In addition, the platform’s operator has been formally indicted.
Launched in 2014, Cryptonator is an online cryptocurrency wallet that enables users to store digital assets and exchange between various cryptocurrencies within their personal accounts.
SOCRadar Ransomware Intelligence
Explore SOCRadar’s Ransomware Intelligence module and gain comprehensive insights with detailed group profiles, MITRE Visualizer, and actionable IOCs. These insights will empower you to stay ahead of evolving threats and enhance your cybersecurity strategy.
Dispossessor ransomware servers seized by the FBI
The Federal Bureau of Investigation (FBI) announced the successful seizure of servers and websites associated with the Radar/Dispossessor ransomware operation. This milestone was achieved through a coordinated international investigation involving the U.K.’s National Crime Agency, the Bamberg Public Prosecutor’s Office, and the Bavarian State Criminal Police Office (BLKA).
Since August 2023, the Dispossessor ransomware group has focused on targeting small to mid-sized businesses across multiple industries worldwide.
You can visit our Dark Web Profile: Dispossessor Ransomware article to read more about Dispossessor ransomware.
September
Encrypted Messaging Platform Ghost Taken Down by Europol
Europol, in collaboration with law enforcement agencies from nine countries, has successfully taken down Ghost, an encrypted communication platform heavily utilized by organized crime networks involved in drug trafficking, money laundering, and other illicit activities.
The Ghost platform was designed with cutting-edge security features to leave little to no traceable evidence.
This coordinated international operation, fueled by critical evidence gathered from the platform, resulted in synchronized raids across multiple jurisdictions. The crackdown led to 51 arrests: 38 in Australia, 11 in Ireland, and one each in Canada and Italy.
47 Crypto Exchanges Taken Down by Germany
German law enforcement has taken down 47 cryptocurrency exchange platforms that were involved in illegal money laundering activities. These services, popular among cybercriminals and ransomware operators, enabled the anonymous exchange of cryptocurrencies by bypassing mandatory KYC regulations.
The lack of identity verification created a safe haven for threat actors to launder illicit funds, reducing the risk of detection, prosecution, or tracing their financial activities.
October
FSB Hackers’ Attack Infrastructure Seized by DoJ and Microsoft
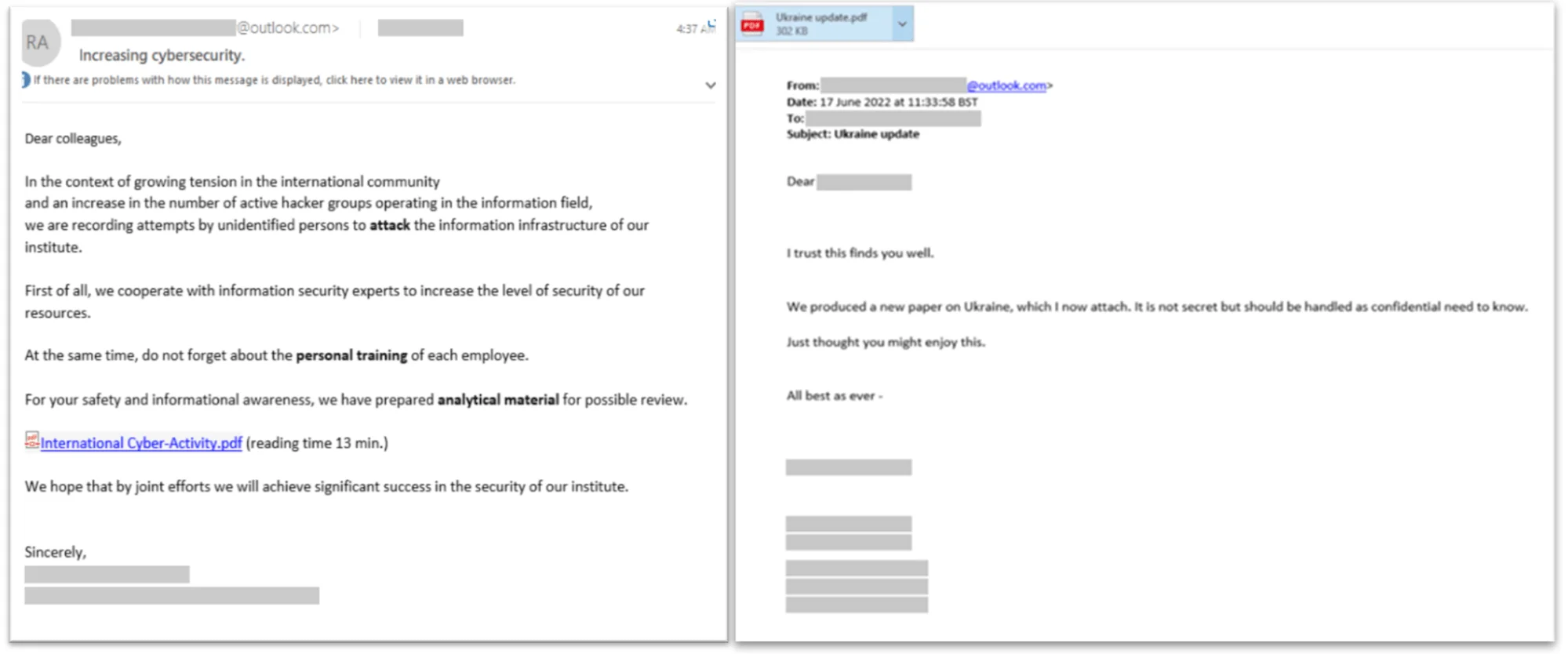
Examples of phishing emails from Star Blizzard, Source: Microsoft
Microsoft and the U.S. Department of Justice have successfully seized more than 100 domains operated by the Russian hacking group ColdRiver. These domains were primarily used to conduct spear-phishing campaigns targeting U.S. government employees and nonprofit organizations across Russia and beyond. Five Eyes attributed ColdRiver’s activities to Russia’s Federal Security Service (FSB).
ColdRiver’s operations were focused on U.S. companies, former and current employees of the U.S. Intelligence Community, and other personnel from important departments as well as contractors.
Sipultie Market Seized by Finland
Finnish Customs, in collaboration with international agencies, have successfully taken down the darknet marketplace Sipulitie, a platform used for the anonymous sale of illegal narcotics.
The operation was made possible through a coordinated effort involving Finnish Customs, Europol, Swedish police, Polish law enforcement, and cybersecurity researchers from Bitdefender.
Sipulitie emerged in February 2023 as a successor to Sipulimarket, a similar platform that authorities dismantled in December 2020. Sipulimarket had been operational since April 2019 and amassed over €2 million before its shutdown.
Authorities have now seized both Sipulitie and Tsätti, a chat-based platform for drug sales launched by the same administrator, displaying a takedown notice on the platforms to inform visitors of the successful operation.
USDoD Arrested
Brazilian authorities have arrested the infamous hacker known as USDoD, a key figure behind several high-profile cyberattacks, including breaches of the FBI’s InfraGard system and National Public Data. The arrest was part of a coordinated law enforcement effort dubbed Operation Data Breach.
USDoD’s most significant breaches include:
FBI InfraGard: A portal designed for secure threat intelligence sharing between law enforcement and private entities.
National Public Data: The breach exposed personal data, including social security numbers, of hundreds of millions of U.S. citizens, making it one of the largest leaks of its kind.
You can visit our Dark Web Profile: USDoD article to read more about USDoD
Dutch National Police Seized Redline and Meta Infostealer Infrastructure

Operation Magnus (Source)
The Dutch National Police have successfully dismantled the network infrastructure behind the Redline and Meta infostealer malware operations as part of “Operation Magnus.”
Redline and Meta are notorious infostealer malware, designed to extract sensitive information from infected devices. This includes browser-stored credentials, authentication cookies, browsing history, cryptocurrency wallets, SSH keys, and confidential documents.
Once stolen, this data is often sold on underground forums or used to facilitate large-scale cyberattacks, including data breaches, ransomware incidents, and espionage campaigns.
What is RedLine Stealer and What Can You Do About it?
Snowflake Hackers Binn and Moucka Arrested
Moucka suspected of orchestrating a series of large-scale breaches targeting Snowflake accounts has been arrested in Canada at the request of U.S. authorities.
The suspect, identified as Connor Moucka, is accused of being involved in approximately 165 data breaches earlier this year. Hackers reportedly gained access to Snowflake accounts by compromising employee login credentials. High-profile victims include AT&T, Ticketmaster, Advance Auto Parts, one of the largest U.S. school districts, Neiman Marcus, Santander, and LendingTree.
Connor Moucka and John Binns stand accused of orchestrating an international hacking and extortion scheme that targeted more than 10 organizations. After stealing sensitive data, they allegedly demanded ransom payments in digital currency, amounting to approximately $2.5 million.
The breaches sparked global concern due to the massive volume of stolen data. AT&T’s breach exposed call and text logs for over 100 million customers, while the Ticketmaster incident impacted approximately 560 million users.
November
1,037 servers taken down, 41 Arrested during Operation Synergia II
Interpol announced the arrest of 41 individuals and the dismantling of 1,037 servers operating across 22,000 IP addresses as part of Operation Synergia II, a large-scale international law enforcement effort targeting cybercrime.
Authorities successfully took down approximately 76% of these IPs, seized 59 servers, and confiscated 43 electronic devices, which will undergo forensic analysis for further evidence. Alongside the 41 arrests, investigations are ongoing into 65 additional suspects linked to illicit cyber activities.
PopeyeTools Market Seized by the US
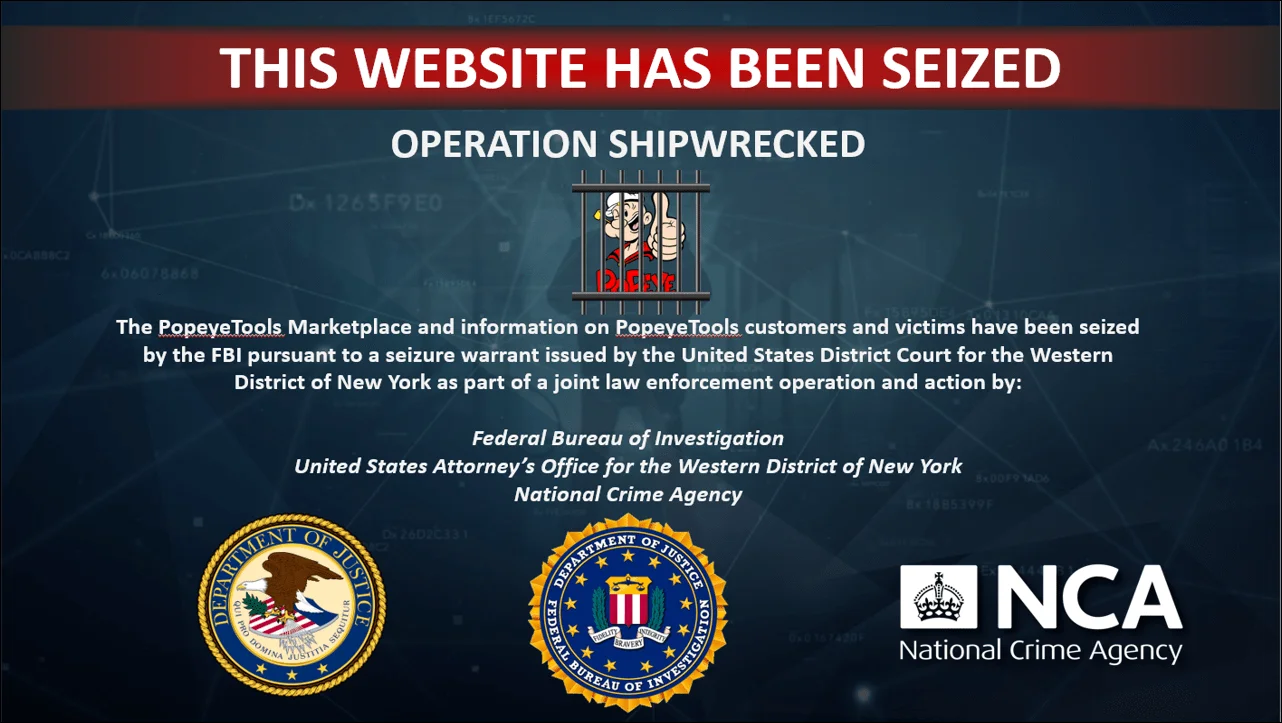
PopeyeTools Splash Page
PopeyeTools, a clearnet marketplace, operated as a hub for cybercriminal activity, offering stolen financial and personal data, as well as tools designed to facilitate fraud and cyberattacks.
In addition to seizing multiple domains associated with the illicit platform, authorities have confiscated cryptocurrency valued at $283,000, which is directly linked to the site’s illegal operations.
Over 1,000 arrested in Africa as part of ‘Operation Serengeti’
Law enforcement agencies across 19 African countries arrested 1,006 individuals suspected of involvement in significant cybercriminal activities during a two-month initiative known as Operation Serengeti.
The operation, which ran from September 2 to October 31, was coordinated by Interpol and Afripol, targeting various cybercrimes including ransomware, Business Email Compromise (BEC), digital extortion, and online scams.
The efforts resulted in the dismantling of 134,089 malicious infrastructures and networks. Investigators linked these activities to over 35,000 identified victims who collectively suffered financial losses nearing $193 million. Operation Serengeti also successfully recovered approximately $44 million.
Italy Took Down Pirate Streaming Service
An extensive international law enforcement operation has successfully dismantled a pirate streaming service that catered to over 22 million users globally, generating approximately €250 million ($263 million) per month.
This action, dubbed “Taken Down,” was announced by Italy’s Postal and Cybersecurity Police Service, which collaborated with Eurojust, Europol, and various other European nations, marking it as the largest operation of its kind both in Italy and internationally.
As part of the operation, authorities seized over 2,500 illegal channels and their associated servers—nine of which were located in Romania and Hong Kong. Additionally, they confiscated cryptocurrencies valued at over €1.65 million ($1.74 million) and approximately €40,000 ($42,000) in cash. The estimated annual financial damages caused by this illegal service exceed €10 billion ($10.5 billion).
Authorities uncovered a hierarchical transnational organization that illegally captured and redistributed content from major broadcasting platforms such as Sky, Dazn, Mediaset, Amazon Prime, Netflix, Disney+, and Paramount. The pirated content included IPTV channels, live broadcasts, and on-demand offerings. The police reported that these illegal streams were made available through multiple live-streaming websites.

SOCRadar Brand Protection Module
Empower your security teams for brand protection from being discredited, legal trouble, and your intellectual property falling into the hands of malicious actors. SOCRadar’s Brand Protection Services helps organizations check the exposure of their sensitive data by regularly monitoring the surface/Dark Web and other sources like Telegram channels.
December
INTERPOL Arrested 5,500 as part of HAECHI-V
A global law enforcement operation has resulted in the arrest of over 5,500 individuals linked to financial crimes and the seizure of more than $400 million.
This coordinated effort involved authorities from 40 countries as part of the latest phase of Operation HAECHI-V, according to INTERPOL.
Matrix Encrypted Chat Service Seized by the Police

A splash page announcing the takedown of the MATRIX platform by international law enforcement
An international law enforcement operation, codenamed Operation Passionflower, has successfully dismantled MATRIX, an encrypted messaging platform utilized by cybercriminals for coordinating illegal activities while evading law enforcement. The operation was a collaborative effort involving multiple European countries, including France, the Netherlands, Italy, Lithuania, Spain, and Germany, and was coordinated by Europol and Eurojust.
The investigation into MATRIX began after authorities recovered the phone of a shooter involved in the attempted assassination of journalist Peter R. de Vries in July 2021. This led to the discovery that the device was configured to connect to the MATRIX platform. A joint investigation team (JIT) formed by Dutch and French authorities enabled police to monitor and intercept an impressive 2.3 million messages sent in 33 different languages through the service.
During the operation, law enforcement executed simultaneous raids across several countries, resulting in the arrest of five suspects and the seizure of numerous assets. Authorities confiscated 970 encrypted phones, €145,000 in cash, and approximately €500,000 in cryptocurrency.
Crimenetwork Taken Down by Germany
Germany has dismantled “Crimenetwork” and arrested its administrator for facilitating the sale of illegal goods.
Established in 2012, Crimenetwork had become a significant hub for criminal activity, boasting over 100 registered sellers and approximately 100,000 users, primarily from German-speaking regions. The platform enabled users to buy and sell a variety of illegal services.
The arrested administrator, a 29-year-old individual known online as “Techmin,” is facing serious charges under Section 127 of the German Criminal Code for operating a criminal online marketplace, along with violations of narcotics laws.
According to the BKA, from 2018 to 2024, transactions on Crimenetwork amounted to around 93 million euros ($98 million), with payments made using Bitcoin and Monero.
Russian Crypto Networks Disrupted as part of Operation Destabilise
The U.K. National Crime Agency (NCA) announced the success of an international investigation aimed at dismantling Russian money laundering networks that facilitated serious organized crime across the U.K., Middle East, Russia, and South America.
This operation, known as Operation Destabilise, resulted in the arrest of 84 individuals associated with two Russian-speaking networks, Smart and TGR, and led to the seizure of £20 million (approximately $25.4 million) in cash and cryptocurrency.
The investigation revealed that these networks were instrumental in facilitating transactions for various illicit actors, including drug gangs and cybercriminals.
The NCA highlighted that the Smart network was involved in funding Russian espionage operations from late 2022 to mid-2023.
Scattered Spider Suspect Arrested
U.S. authorities have apprehended a 19-year-old named Remington Goy Ogletree, also known online as “remi,” who is linked to the infamous Scattered Spider cybercrime gang. He faces charges for breaching a U.S. financial institution and two unnamed telecommunications companies.
Ogletree allegedly infiltrated the networks of these organizations by using credentials obtained through text and voice phishing attacks aimed at their employees. In these schemes, he impersonated the IT support departments of the victims during calls, pressuring employees to access phishing sites where they unwittingly provided their usernames and passwords.
You can read more about Scattered Spider in our blog post: Dark Web Profile: Scattered Spider
Manson Market Shut Down by Europol
Europol announced the shutdown of Manson Market, a marketplace that facilitated large-scale online fraud. This operation resulted in the seizure of over 50 servers associated with the service, along with the arrest of two suspects. Authorities collected more than 200 terabytes of digital evidence during the operation.
Manson Market was utilized to sell sensitive information illegally obtained from victims through phishing and vishing (voice phishing) schemes. Scammers impersonated bank employees to extract personal details from victims, and fake online shops were set up to trick users into providing their payment information.
In addition to the servers, law enforcement confiscated over 80 data storage devices, cell phones, computers, and cash and cryptocurrency valued at more than €63,000 ($66,500). The marketplace also had a presence on Telegram, where one channel shared credit card details daily, including numbers, expiration dates, and CVV codes.
27 DDoS-for-hire Platforms Taken Down
As part of ‘Operation PowerOFF,’ law enforcement agencies from 15 countries have successfully taken down 27 DDoS-for-hire services, commonly referred to as “booters” or “stressers.” This initiative aims to combat cybercrime, particularly focusing on distributed denial-of-service (DDoS) attacks.
The operation led to the arrest of three administrators responsible for these illicit platforms and the identification of approximately 300 customers utilizing these services.
Rydox Market Seized
Albanian law enforcement, in collaboration with international partners, has successfully seized the Rydox cybercrime marketplace and arrested three of its administrators. The operation involved the arrest of Kosovo nationals Ardit Kutleshi, Jetmir Kutleshi, and Shpend Sokoli.
Since its inception in February 2016, the Rydox marketplace has facilitated over 7,600 sales involving stolen personal information such as credit card details, login credentials, and sensitive data from thousands of U.S. citizens. Additionally, it offered more than 321,000 cybercrime products to over 18,000 users, which included tools and materials for committing various cybercrimes.
The U.S. authorities also seized the Rydox domain and approximately $225,000 in cryptocurrency linked to the defendants during this coordinated operation.
Servers hosting the illicit marketplace were taken offline in Kuala Lumpur, Malaysia, with assistance from the Royal Malaysian Police.
SOCRadar Advanced Dark Web Monitoring
Advanced Dark Web Monitoring is vital to your organization’s cybersecurity infrastructure, providing a comprehensive overview of potential risks in the Dark Web ecosystem.
Spain Conducted a Crackdown on a Voice Phishing Gang
The Spanish police, in collaboration with their Peruvian counterparts, executed a coordinated operation targeting a large-scale voice phishing (vishing) scam. This crackdown resulted in the arrest of 83 individuals across both countries. The operation involved 29 simultaneous raids that led to the seizure of cash, mobile phones, computers, and relevant documents.
The investigation revealed that the scammers operated a significant call center network employing around 50 agents across three distinct facilities. They managed to defraud over 10,000 victims, amassing approximately €3 million ($3.15 million) in illicit proceeds. The calling agents utilized stolen databases and pre-written scripts to deceive victims into providing sensitive banking information.
Conclusion
The year 2024 stands as a testament to the growing effectiveness of law enforcement in addressing the complex challenges of cybercrime. By leveraging advanced technologies and fostering unprecedented levels of global cooperation, agencies have made significant strides in dismantling criminal networks, recovering stolen assets, and restoring trust in digital ecosystems.
SOCRadar’s Integrated Takedown service
SOCRadar’s Integrated Takedown service, developed entirely in-house, is your strategic partner in the fight against digital threats like counterfeit websites and impersonating domains. We actively neutralize these dangers, ensuring your digital landscape accurately and authentically represents your organization’s true values and identity.
Unlike other solutions that rely on third-party services, our Integrated Takedown module is fully powered by our own on-demand service. This ensures seamless automation of fake domain detection and takedown processes, providing unmatched control, efficiency, and reliability.
The ever-evolving nature of cyber threats serves as a reminder that this battle is far from over. As we move into 2025, it is essential to continue investing in intelligence-sharing, public-private partnerships, and technological innovation to stay ahead of adversaries. The successes of 2024 serve as a beacon of hope and a call to action for the continued pursuit of a safer cyberspace for all.