
What Should We Learn From the Conti’s HSE Ireland Attack?
Conti ransomware attacks can target almost any organization. The attack on HSE Ireland last year demonstrates that threat actors can even target critical sectors such as healthcare. A more proactive understanding of cyber security is required against these rising attacks. This article shares the whole picture of this particular cyber incident.
HSE is the Largest Employer in Ireland

The Health Service Executive is the publicly financed healthcare system in the Republic of Ireland, responsible for providing health and individual social support. The HSE, which started to operate on 1 January 2005, comprises around 54 acute hospitals, 4,000 locations, and over 70,000 devices like personal computers and laptops. The foundation, whose annual budget is €16.05 billion, is the most considerable employer in Ireland, with more than 130,000 staff, including its direct employees and those hired by organizations sponsored by the HSE.
Conti’s HSE Attack
In the early hours of Friday 14 May 2021, threat actors subjected the HSE to a severe cyberattack through the illegal infiltration of their technological infrastructure using Conti ransomware. The HSE started its Critical Incident Process, resulting in the decision to shut down the whole HSE IT systems and unplug the connection of the National Healthcare Network from the worldwide internet to determine the cyber attack‘s impact and terminate the hacker’s access to the HSE’s system. This instantly caused healthcare employees to lose access to all HSE-provided systems such as laboratory IT frameworks and patient information systems.
The cyberattack also caused the loss of non-clinical, financial, and procurement systems. There was an immediate disruption, and most healthcare workers returned to pen and paper for proceeding patient care. An independent report published by PwC (PricewaterhouseCoopers) focused on the Irish HSE cyber-attack has discovered that the effects could have been even worse than if cybercriminals had hit the Covid-19 vaccination process or specific medical systems. On the other hand, PWC notes that the HSE is nevertheless vulnerable to cyberattacks of a similar character.
The HSE authorized PWC to conduct a complicated analysis of the breach, its causes, and suggestions as part of the recovery action. PwC report is beneficial for associations that want to enhance their anti-ransomware defenses accepting the learned lessons of this ransomware attack on Ireland’s healthcare systems.
It Started With a Phishing E-mail: Stages of HSE Attack
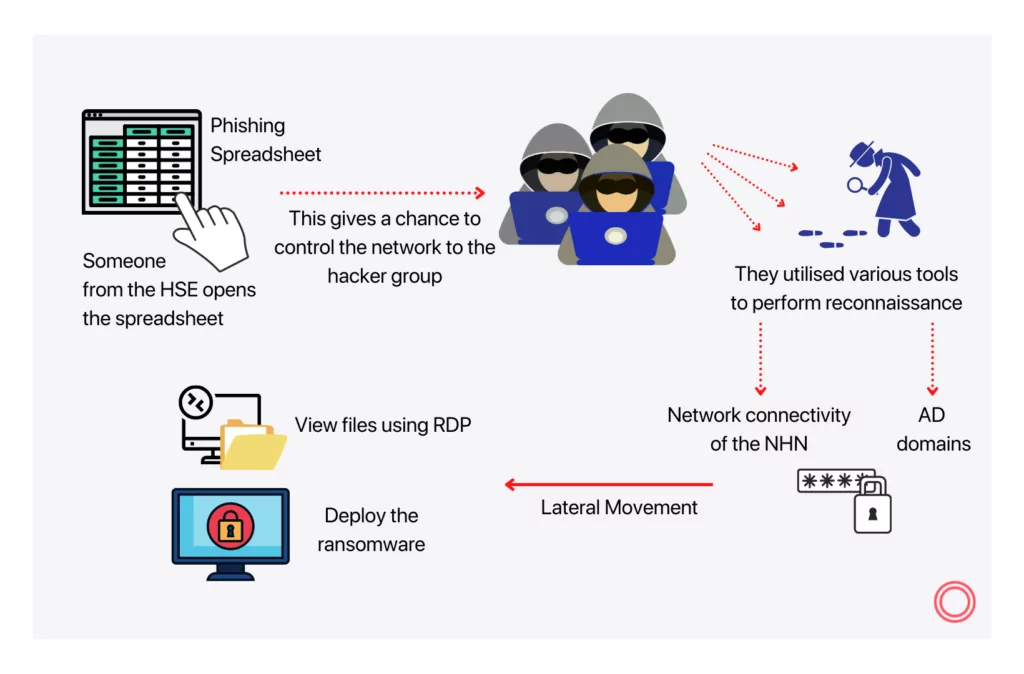
On 18 March 2021, somebody from the Irish HSE clicked a spreadsheet sent to them by a phishing email two days ago. The cybercriminal group that sent the email went through the networks over two months. They operated several tools typically used by human-operated ransomware gangs to accomplish reconnaissance and lateral movement through the HSE’s systems. Then, the ransomware group benefited from the network connectivity provided by the NHN (“National Healthcare Network”) besides the bidirectional confidence between several AD (Active Directory) domains to shift laterally across to seven hospitals quickly.
Following the lateral movement, they scanned local or remote directories on environments across the healthcare systems and four institutions, reached files and tried to open them using RDP (Remote Desktop Protocol), copied files, and deployed ransomware throughout multiple establishments associated with the NHN. There were numerous warning signals that the threat actors were at work; however, the report uncovered that anyone did not launch an investigation, which implied a missed significant opportunity to interfere. Finally, at 01:00 BST on Friday 14 May, the hacker gang released their ransomware, whose impact will be destructive.
Highlighted key findings and lessons learned
- The HSE did not have a single responsible for cybersecurity at the management level at the time of the incident. The absence of a complex cybersecurity approach or adaptation plan could be attributed to a lack of cybersecurity administration. Moreover, the HSE did not have a centralized cybersecurity function addressing cybersecurity risk and controls.
- The antivirus instrument was over-relied upon to catch and prevent threats on endpoints. There was no adequate security monitoring ability to detect, analyze and react to security alerts across the HSE’s IT environment.
- Visibility across the public-facing digital assets and technologies needed to detect exploited critical vulnerabilities was not sufficient at the time of the attack.
- Multi-factor authentication across the applications required remote access was not enabled that could prevent attackers from gaining quick access to internal systems.
The HSE expressed that it has already started executing suggestions in the report and engaging with the Department of Health to agree on a multi-year ICT transformation program. HSE chair Ciarán Devane talked about this point and stated, “It is clear that our IT systems and cybersecurity preparedness need major transformation.”
How to Protect Yourself from Ransomware with SOCRadar?
With SOCRadar’s AttackMapper, RiskPrime, and ThreatFusion modules, you can create a holistic and proactive security system against ransomware. When you have all of these modules, you can strengthen your cyber security with many functions such as taking inventory of your digital assets open to the internet, receiving critical port notifications, detecting 0-Day vulnerabilities, monitoring deep and dark web, detecting phishing domains, analyzing suspicious files and many more.
References
1- https://www.hse.ie/eng/services/publications/conti-cyber-attack-on-the-hse-full-report.pdf
2- https://www.bbc.com/news/technology-59612917
3- https://www.siliconrepublic.com/enterprise/hse-cyberattack-pwc-report-ransomware
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access


































