
Top Open Source Solutions for Building Security Operations Center II
A Security Operations Center (SOC) is a centralized function inside an organization that employs people, procedures, and technology to continually monitor and enhance an organization’s security posture. It also prevents, identifies, analyzes, and reacts to cybersecurity incidents.
What is Cyber Security Operations Center?
The security operations center (SOC) consists of the people, procedures, and technology responsible for monitoring, assessing, and managing the information security of a business.
A security operations center acts as the company’s intelligence center, collecting data in real-time from the organization’s networks, servers, endpoints, and other digital assets and using intelligent automation to detect, prioritize, and react to possible cybersecurity threats.
The rise of sophisticated threats placed a premium on gathering context from various sources. The security operations center is the correlation point for every event recorded inside the monitored company. It must determine how these occurrences will be controlled and acted upon.
Top Open Source Solutions for Building Security Operations Center
1- MISP

The Malware Information Sharing Platform (MISP) is an open-source platform that enables the sharing, storage, and correlation of indicators of compromise (IOCs) of targeted attacks, threat intelligence, financial fraud information, vulnerability information, and counter-terrorism information.
MISP assists security teams in ingesting and analyzing threat data on identified malware assaults, generating automated linkages between malware and their features, and storing data in an organized format. In addition, MISP contributes to the development of rules for network intrusion detection systems (NIDS) and permits the exchange of malware data with other parties. In simpler terms, MISP intends to establish a trusted platform by storing threat information locally and increasing malware detection to facilitate information flow across enterprises.
2- The Hive Project
Hive is an artificial intelligence-based project and process management solution used by companies such as Uber, Starbucks, Google, and Comcast. A scalable, open-source, and free Security Incident Response Platform tightly integrated with MISP (Malware Information Sharing Platform). It is designed to make the lives of SOCs, CSIRTs, CERTs, and any Information security practitioners dealing with security incidents that need to be investigated and acted upon quickly.
Multiple security operations centers and CERT analysts may work concurrently on investigations. All team members can access real-time information on new or existing cases, tasks, observables, and IOCs, courtesy of the integrated live stream.
Special notifications enable them to manage or delegate new duties and evaluate recent MISP events and alerts from different sources, including email reports, CTI providers, and SIEMs. They may then immediately import and study them.
3- Suricata

Suricata is the most popular independent, open-source threat detection engine. By integrating intrusion detection (IDS), intrusion prevention (IPS), network security monitoring (NSM), and packet capture (PCAP) processing, Suricata can rapidly identify, halt, and evaluate even the most complex assaults.
Suricata’s multithreaded nature enables its customers to grow horizontally on a single device by adding packet processing threads as required by traffic volume. Under the hood of the Bricata platform, it’s an automated process. There are no specific setups or anything else that an administrator must perform; this feature is exclusive to Bricata.
4- FAME
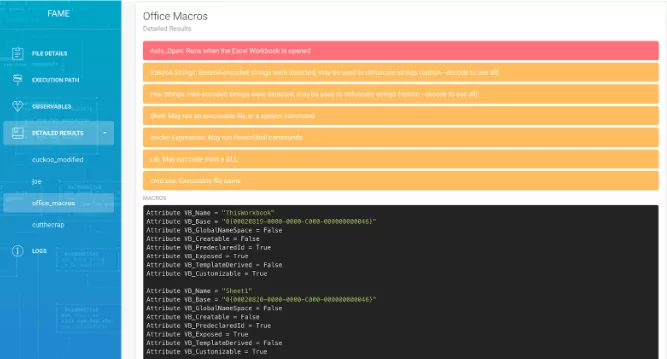
FAME is an open-source malware analysis platform designed to assist the study of malware-related files by utilizing as much information as possible to accelerate and automate end-to-end analysis.
FAME should be seen as a framework for malware investigation. Instead of building many scripts for various malware analysis-related activities, construct FAME modules that will be able to work together.
5- Cortex Project
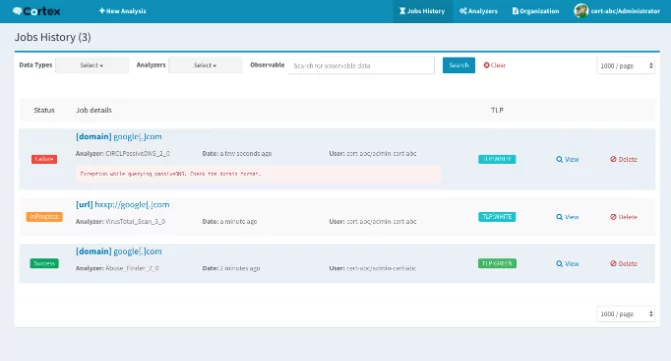
Cortex attempts to answer a challenge typically experienced by SOCs, CSIRTs, and security researchers during threat intelligence, digital forensics, and incident response. How to evaluate acquired observables at scale by querying a single tool instead of multiple?
The Hive Project has built Cortex, open-source and free software for this aim. Observables such as IP and email addresses, URLs, domain names, files, and hashes may be evaluated individually or bulk using a web interface. Through the Cortex REST API, analysts may also automate these activities.
By using Cortex, you won’t have to reinvent the wheel each time you want to utilize a service or a tool to evaluate an observable and assist you in investigating the current case. Utilize one of the several analyzers it provides. If a tool or service is absent, construct a suitable application quickly and make it accessible to the team.
6- GOSINT Framework
The GOSINT framework is a project for gathering, analyzing, and exporting high-quality compromise indicators (IOCs). A security analyst may gather and standardize structured and unstructured threat information using GOSINT.
By applying threat intelligence to security operations, confidence, context, and co-occurrence are added to alarm data. This involves using third-party research to security event data to discover similar or identical symptoms of harmful conduct. The framework is developed in Go with a frontend in JavaScript.
7- OpenCTI
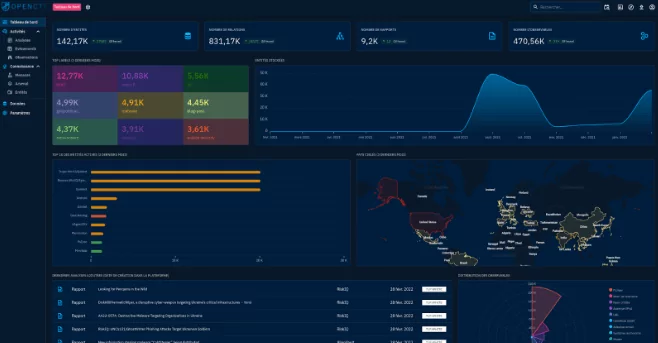
OpenCTI is an open-source framework for managing cyber threat intelligence and observables. It was designed to structure, store, organize, and display technical and non-technical information on cyber dangers.
Using a knowledge schema based on STIX2 specifications, the data are structured. It was created as a contemporary web application with a GraphQL API and a UX-focused UI. OpenCTI may also be integrated with other tools and apps, such as MISP, TheHive, MITRE ATT&CK, etc.
8- RTIR Project
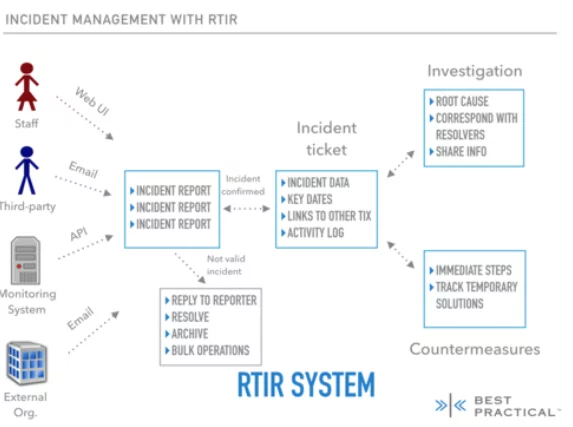
Request Tracker for Incident Response (RTIR) is an extension of RT that offers incident response teams preconfigured queues and procedures. It is the tool of choice for several CERT and CSIRT teams worldwide.
RTIR provides the capability to correlate critical incident report data from human and automated sources to identify trends and connect numerous incident reports to a single root cause issue.
You may handle communication with numerous parties, such as reporters, colleagues from other security teams cooperating on replies, and internal teams coordinating countermeasures.
9- Apache Metron
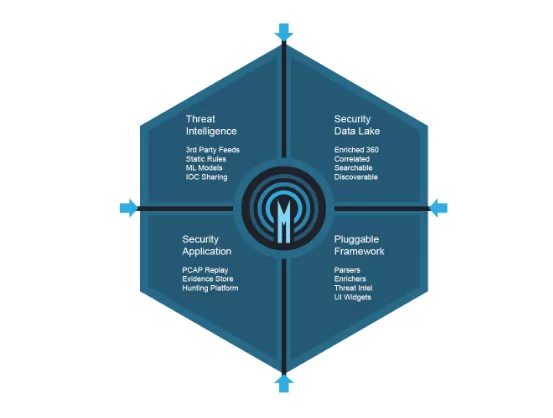
Metron combines a range of open source big data technologies to provide centralized monitoring and analysis solution for security. Metron delivers log aggregation, complete packet capture indexing, storage, sophisticated behavioral analytics, and data enrichment inside a single platform while integrating the most recent threat intelligence data into security telemetry.
10- Osquery
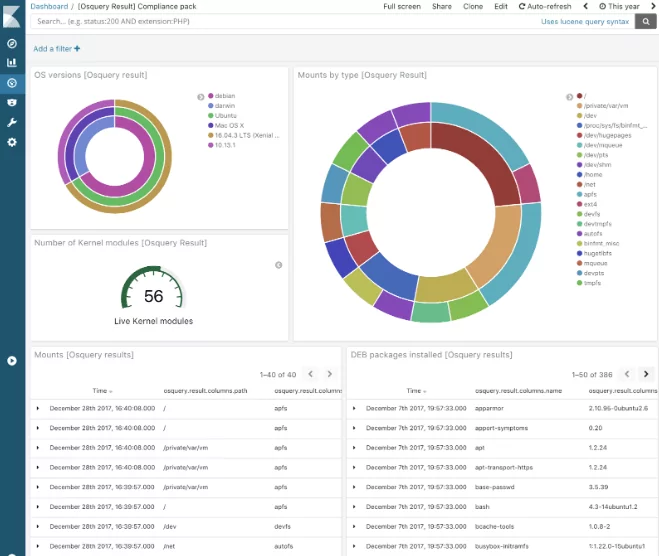
Operating system instrumentation, monitoring, and analytics framework driven by SQL. Supports Linux, macOS, and Windows.
An operating system is exposed as a high-performance relational database via Osquery. This enables you to investigate operating system data using SQL queries. SQL tables with Osquery describe abstract notions such as operating processes, loaded kernel modules, open network connections, browser plugins, and file hashes.
SQL tables are implemented using a straightforward API for plugins and extensions. Numerous tables already exist, and more are being composed: https://osquery.io/schema.




































