An Analysis of Central Banks Hackings: Who is Next?
By SOCRadar Research
Critical infrastructures are the basis for the functioning of the countries’ system, and they are essential to continue the country’s operations, such as financial services, education, public health, food and agriculture, military, and so on. Nation-state threat actors whose intention is damaging a country usually prefer attacking one of the critical infrastructures of the target country.
A way to damage any country’s financial stance and reputation is attacking its financial services, particularly the country’s central bank. When it comes to the finance sector, money-minded threat actors such as ransomware groups must be considered. The finance industry was one of the most affected industries by ransomware in 2022, and 14 out of 16 critical infrastructure industries were targeted by ransomware attacks last year, which puts central banks as a possible target of ransomware.
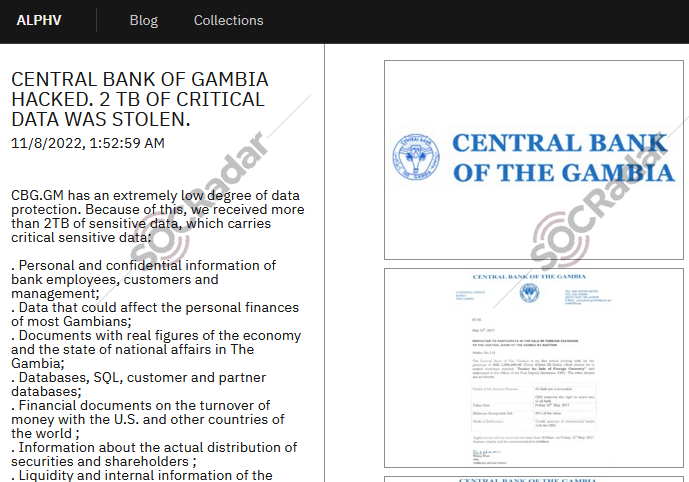
Recently, on November 8, 2022, a ransomware group called BlackCat -also known as AlphVM or AlphaV- announced that they stole the Central Bank of Gambia‘s 2TB of critical data. The group mostly targets finance and professional services industries.
Most Common Types of Attacks Central Banks Experience
Phishing:
The most common initial attack vector is phishing, and its occurrence is rising every year. Phishing and other social engineering attacks have been regarded as the most likely type of attack vectors by all central banks.
Distributed Denial of Service (DDoS):
It is an attack type that disrupts the normal traffic of a targeted server, service, or network by overwhelming the infrastructure with an abnormal amount of Internet traffic. On August 26 2018, the Central Bank of Spain suffered a DDoS that affected access to its website.
Ransomware:
It is a type of malware that encrypts the files of its victim and holds them for ransom. Ransomware operators or groups threaten their victims by leaking the data they hold to guarantee payment. This attack type is considered one of the highest costing risks. BlackCat ransomware group mentions a critical point by saying, “CBG.GM has an extremely low degree of data protection.” in their announcement.
Supply Chain Attacks (Third-party Attack):
It is a type of cyberattack that aims to harm an organization by targeting less secure elements of an organization’s supply chain, such as external partner or vendor which has access to systems and data.
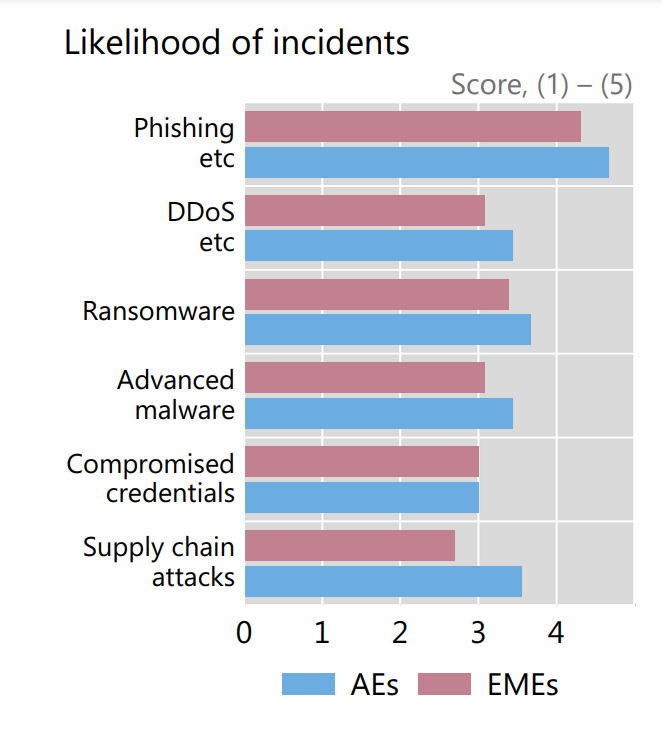
According to Bank for International Settlements (BIS) report, the central banks in Advanced Economies (AEs) are more worried about supply chain attacks than the central banks in Emerging Market Economies (EMEs). The increased use of third-party products in advanced economies may be a factor.
Observed Cyberattacks Central Banks Have Suffered
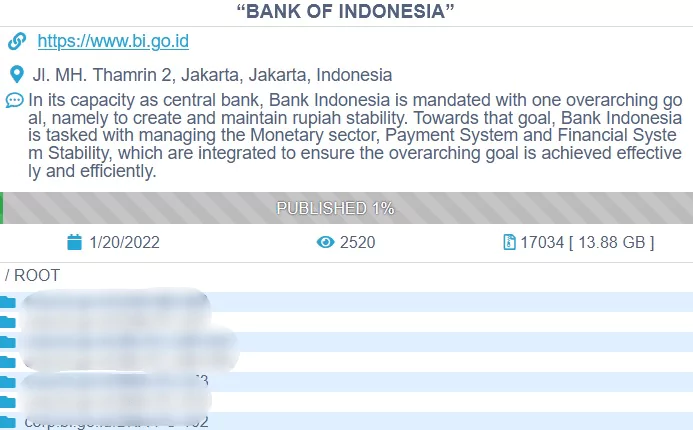
Bank Indonesia
In January 2022, the central bank of the Republic of Indonesia, Bank Indonesia (BI), suffered a ransomware attack from the Conti ransomware group. According to Reuter’s article, public servers at Bank Indonesia were not disrupted and worked without a shortage. To CNN’s report, only “non-critical data” belonging to BI employees have been stolen, and the amount of stolen data is 13.88GB, according to Conti’s claim.
European Central Bank
According to APnews’ article on July 12, 2022, the European Central Bank -which is a Frankfurt-based central bank for the 19 countries such as Austria, Belgium, Finland, and so on – was targeted in a cyberattack attempt, but there was no compromise.
Central Bank of Bahrain
On July 4, 2022, in a hacker forum monitored by SOCRadar, threat actors shared information alleged to be the database of the Central Bank of Bahrain.
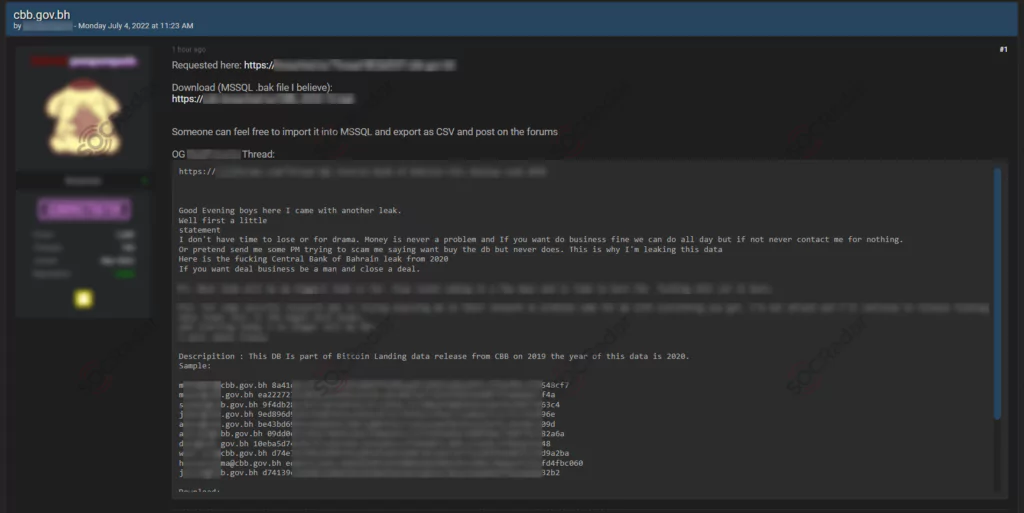
Another dark web forum post has been observed that was posted in 2020. 13GB of leaked data contains backup files and email addresses of Central Bank of Bahrain employees.

Central Bank of Russia
On March 25, 2022, Anonymous announced on Twitter that one of their members -The Black Rabbit World (Thblckrbbtworld)- leaked the Central Bank of Russia.
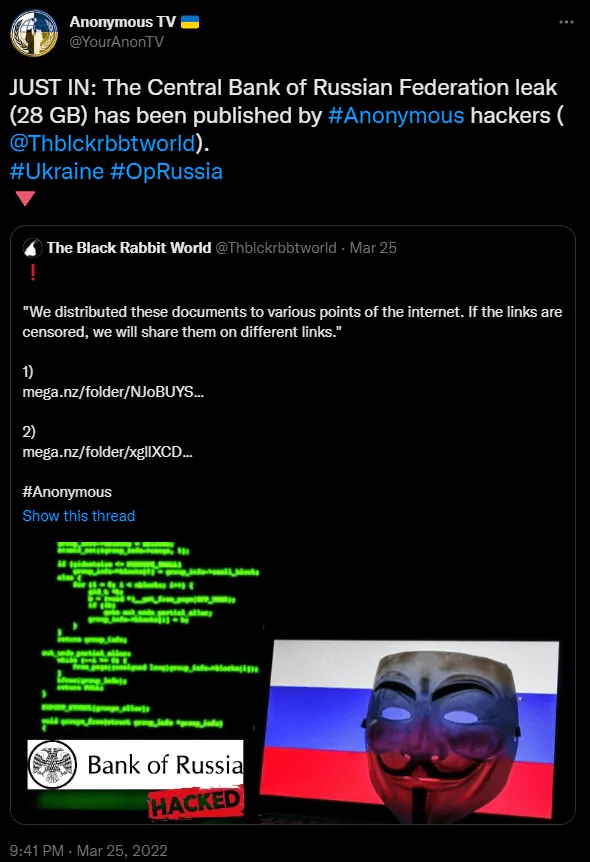
After the announcement, posts about it on the dark web hacker forums have increased.
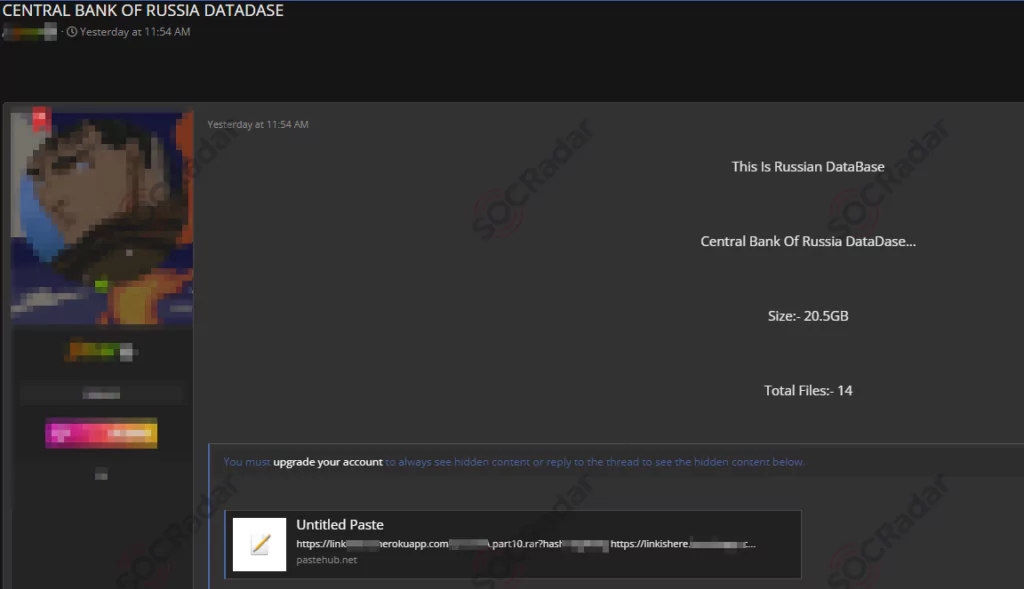
According to Anonymous, the number of leaked data ranges between 20 to 30 gigabytes, and more than 35,000 files have been leaked. Data contains many documents, such as trade information, tables, and financial accounting documents. The motive of this incident is thought to be the Ukraine-Russia war.
Central Bank of Tunisia
In March 2022, the Conti ransomware group posted a new announcement about the Central Bank of Tunisia as their victim.
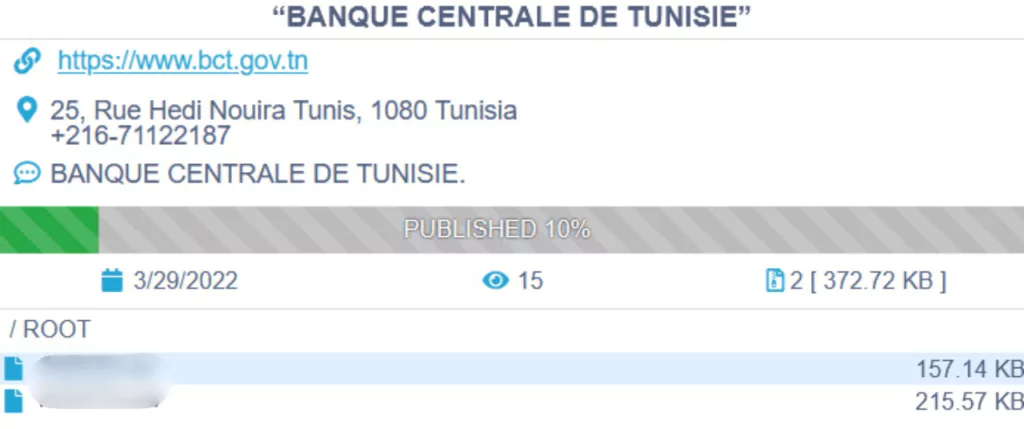
Many documents have been published by Conti that contain business contracts, investment documents, budget plans, etc.
Bank of Zambia
The Bank of Zambia announced that they suffered a ransomware attack by Hive ransomware that disrupted some of their IT applications, such as the Bureau De Change Monitoring system and website, on May 9, 2022.

The Hive ransomware claims that the group has encrypted the Bank of Zambia’s Network Attached Storage (NAS) device. According to Cybersafe’s article, some test data may have been leaked, the bank had protected the core systems, and the Bank of Zambia refused to pay the ransom.
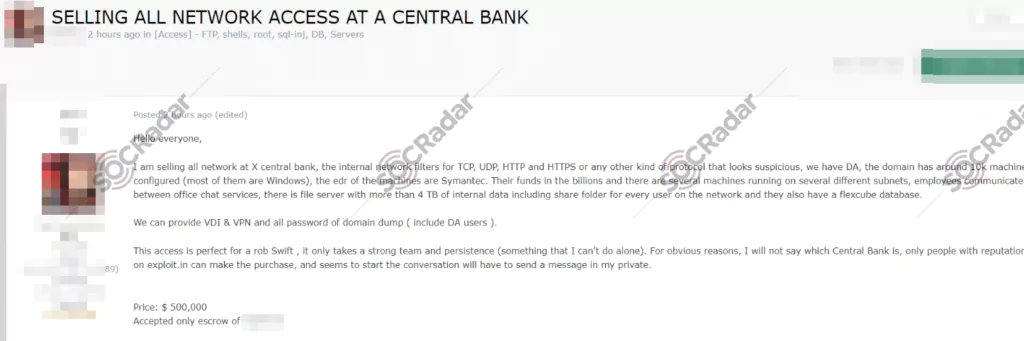
An Unknown Central Bank Compromised
A post that sells the network access to the IT Infrastructure of an unknown Central Bank was also observed by SOCRadar’s Dark Web Researchers.
Conclusion
The frequency and sophistication of cyberattacks increase day by day, and the risk in financial institutions -which is one of the most attacked industries- rises at the same time. Even though the finance sector seems aware of the risks, threat actors could be successful with their attacks and can speak about how central banks’ data protection levels are extremely “low.”
Regarding SOCRadar’s Research team’s observations, phishing and ransomware attacks have been seen more in cyberattacks on central banks. But we did not encounter a ransomware group that specifically targets central banks around the globe. Ransomware groups are targeting the financial industry as well as other sectors such as healthcare and technology.
There are some essential recommendations by CISA to organizations to prevent these attacks:
- It is critical for the organization to create, maintain, and exercise a basic cyber incident response plan and associated plan that includes how response and communication will continue during a ransomware incident.
- Back up regularly, secure your backup data using encrypting, and ensure your backup data is offline.
- Regular vulnerability scans to identify and address vulnerabilities are vital, especially for devices in the internet-faced form.
- Because the threat actors use it to propagate malware across the organizations, disabling or blocking Server Message Block (SMB) is another critical point.
- Everyone working in the organization should be given cybersecurity awareness training.
- Implementing filters at the email gateway should be adequate for known malicious indicators.
- Apply the principle of least privilege to all systems and regularly audit user accounts and admin privileges.
- Implementing MFA is a must.
- Monitor remote access logs often.
Threat actors whose intentions are financial gain and fame usually announce their malicious activities on Dark Web hacker forums. SOCRadar Dark web team monitors dark web forums on 7/24 and informs its customers immediately if they find anything suspicious.
SOCRadar also monitors unwanted exposure to protect organizations against external cyber threats. It collects and processes data using advanced analytics algorithms with its analyst team. Monitoring can help organizations detect if their executives, employees, customer credentials, emails, or customer accounts have been compromised.
Organizations gain visibility into their growing attack surface using SOCRadar’s AttackMapper. It helps organizations get automatically informed by the severity of unknown internet-facing digital assets such as the organization’s IP, DNS, and domain addresses.