
SOCRadar’s End of Year Report: Phishing Threats in 2022
The year 2022 was challenging for global cybersecurity, with waves of cyberattacks during Russia’s invasion of Ukraine setting the tone for the rest of the year. This has also made it a challenging year for many large corporation CISOs, who had to deal with the constant threat of new cyberattacks.
Simple endpoint attacks evolved into more complex, multi-stage operations in 2022, and ransomware attacks impacted businesses of all sizes. Crypto mining attacks also provided cybercriminals with easy access to corporate networks, emphasizing the significance of dark web monitoring.
In response, companies of all sizes and sectors have sought protection, leading to an increase in demand for integrated cyber threat intelligence platforms like SOCRadar.
In conclusion, 2022 was a year of challenges and evolution in the cybersecurity field. As we move into 2023, it is essential to stay vigilant and invest in solutions that can provide actionable threat intelligence and proactive protection.
Get the full End-of-Year 2022 Report to learn more.
The Top Target Countries and Industries of 2022
The report covers various aspects of cybersecurity in a “top 10” format to specify trends through 2022. You can learn about the most significant leaks, other incidents, and most exploited vulnerabilities of 2022 by reading the report and the most targeted countries and industries in 2022. The very same countries and industries are potential targets in 2023.
The country’s level of cybersecurity awareness and the presence of more critical targets, such as infrastructure or businesses, are essential considerations for threat actors when targeting specific countries. Furthermore, a larger country corresponds to more devices, indicating a larger attack surface for attackers to exploit.
During 2022, threat actors on the dark web talked most about the following countries:
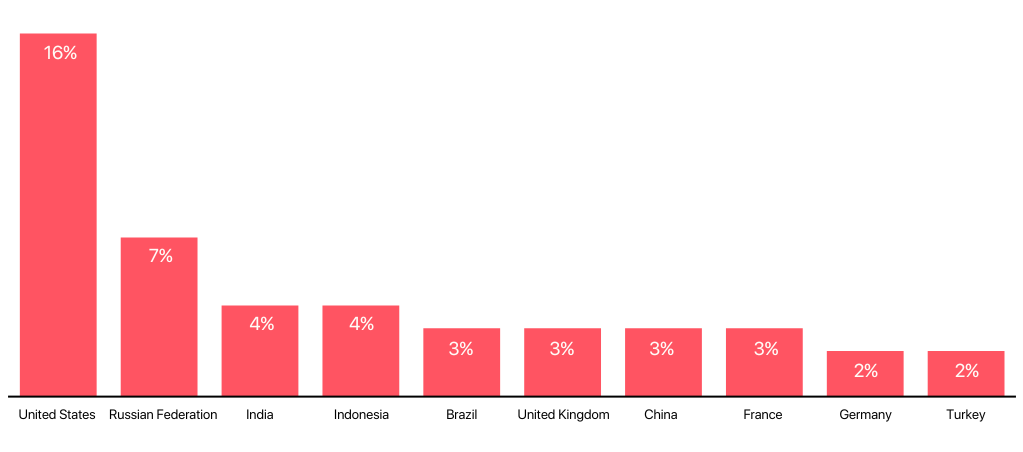
Some businesses are more vulnerable to cyberattacks than others, either due to the sensitivity of the data they store or work with or simply due to the motivations of threat actors. On the other hand, being attacked significantly reduces a company’s productivity and damages its reputation.
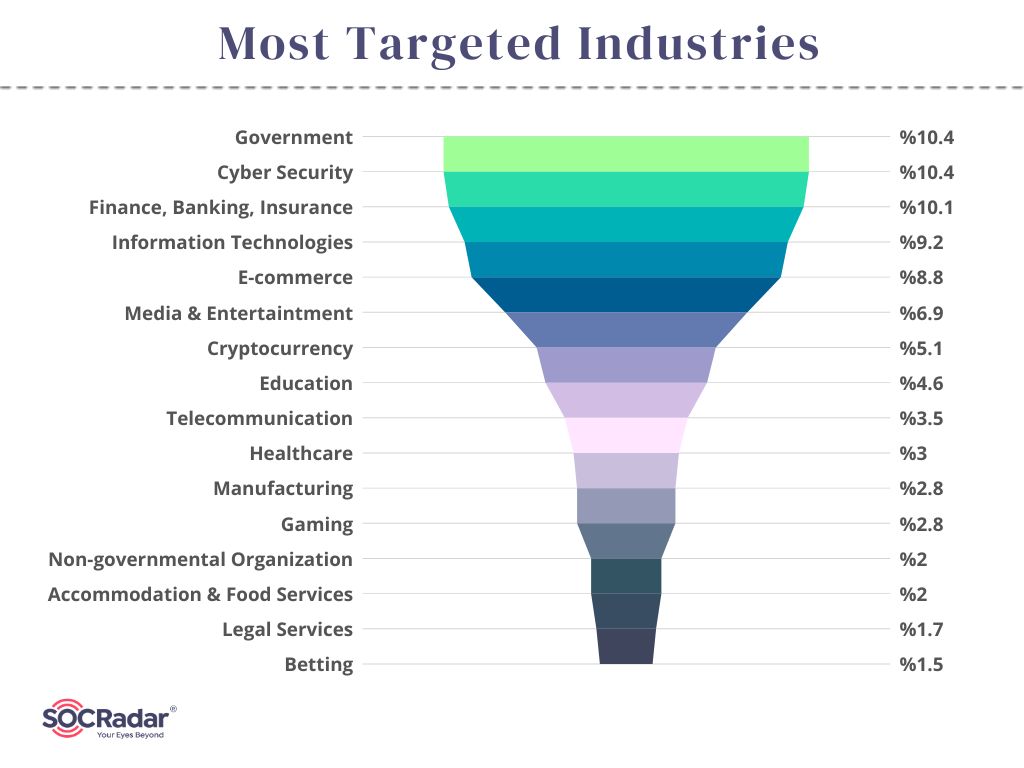
The following are the top ten industries that threat actors discussed the most on dark web channels:
- Government
- Finance
- Cybersecurity
- IT
- E-commerce
- Media & Entertainment
- Cryptocurrency
- Education
- Telecommunication
- Healthcare
These industries were targeted by various attacks in 2022, and the dark web posts mention businesses in these industries by leaking their data, selling the data, or exposing their weaknesses. However, as is to be expected, data leaks following attacks or breaches are more frequent on the dark web.
Threat actors may use the leaked data in a variety of attack techniques. Phishing is one of the more popular ways for threat actors to utilize leaked personal information.
Phishing Statistics in 2022
Because people are the most vulnerable part of an organization, phishing and social engineering are the most dangerous types, and many cyberattacks still start this way.
According to the report’s findings, the government and cybersecurity industries were the targets of 10.4% of all phishing attacks in 2022. Additionally, 10.1% of attacks targeted the finance, banking, and insurance sectors, making them the most used phishing targets.
Two leading suggestions for avoiding phishing sites have been around for a long time: carefully examine URLs and stay away from areas without an SSL certificate. People feel more secure and less worried when they see the tiny padlock symbol in the browser.
However, this technique is no longer helpful in identifying suspicious websites. Our research reveals that SSL certificates are used by 55% of impersonating domains to deceive users into believing they are secure.
Popular Phishing Domains in 2022
Using Phishing Radar, a free SOC tool from SOCRadar, we looked for potential impersonating domains on some of the most popular US websites. Among the 32 websites we mentioned in the report, social media networks make up the top 5 websites:
- tiktok[.]com
- instagram[.]com
- facebook[.]com
- linkedin[.]com
- discord[.]com
This outcome supports the growing trend of threat actors targeting mobile devices.
You can also check the report to find information about the most used top-level domains and the most affected countries.
LockBit was the Most Active Ransomware Group
Not all phishing campaigns are for financial scamming; a phishing attack can give way to many other threats, such as the spreading of malware or, be specific, ransomware. The ransomware group known as Royal Ransomware has been employing a distinctive strategy called callback phishing, which involves impersonating a company.
Apart from banking trojans, phishing, distributed denial-of-service (DDoS), and crypto-jacking, ransomware is one of the cybercriminals today’s much more impactful attacks.
The amount of ransom demanded to decrypt data also increases as ransomware’s geographic scope does. As we saw in 2022, ransomware groups could also cause significant harm to nonprofit and governmental organizations.
Before infecting additional devices, a ransomware attack typically starts on one. Most ransomware attacks begin with phishing or drive-by installations of related malware from suspicious websites.
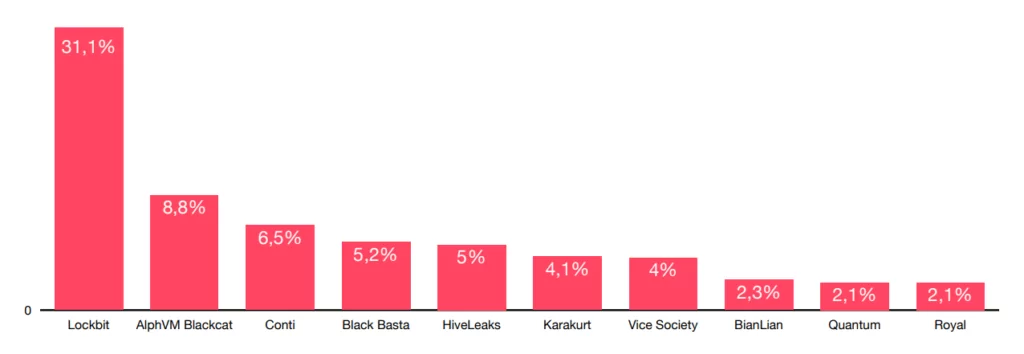
The graph below, which is taken from the report, shows that in 2022, LockBit was the most active ransomware group:
Threat intelligence can assist in identifying which organizations are possible targets at a given time. You can access relevant IoCs using the SOCRadar Threat Actors/Malware tab to track and index hackers, ransomware groups, and the malware they utilize.
Signature-based detection will become more complex as new and updated variants appear. SOC analysts should be able to follow current IoCs to remedy this problem, and organizations should support their cybersecurity technologies with cyber threat intelligence to take a more proactive defensive stance.
Further information is available in the report’s section titled “Ransomware Attacks in 2022.”
Identify Phishing Threats with SOCRadar
With more advanced techniques and higher success rates, phishing attacks have been steadily rising over the past few years and are expected to continue. It’s crucial to be informed of the most recent phishing techniques and to take precautions against them, such as being cautious of spam emails, avoiding providing personal information in response to an unsolicited request, and using a threat intelligence tool.
One of the services offered by SOCRadar is identifying and responding to spoof domains that attempt to collect login credentials and personally identifiable information from your staff and customers.
To automate phishing attack prevention, AI phishing controls must be implemented. Given the increasing number of these attacks, modernizing security infrastructure is crucial.
Download the SOCRadar 2022 End-of-Year Report and get more insights.



































