
Countering Nation-State Cyber Attacks with Threat Intelligence
In recent years, attacks targeting critical infrastructures and political figures of states have increased. These attacks are often supported by one or more different states and carried out by skilled nation-state threat actors using advanced techniques to access sensitive information and to cause damage to services and infrastructures. They cause significant problems with wide-ranging and severe consequences for national security.
Many different techniques and deceits are used when attacks on states and nations. Phishing attacks are the most commonly used method among them. Threat actors deceive their targets by redirecting them to malicious links through deceptive emails or advertisements.
They also take over their targets using malicious software such as malware and ransomware. As a result of these attacks, they can gain access to the system and get the information they want.
Another frequently used method is Denial-of-Service (DoS) attacks. Attackers cause the system to slow down or even crash by sending heavy network traffic to their targets. In addition, threat actors can easily infiltrate target systems using security vulnerabilities they discover (zero-day vulnerabilities).
Supply chain attacks are also among the methods used. In such attacks, attackers target third-party software to gain access to target systems.
Finally, cyber attacks can also be carried out using Advanced Persistent Threats (APTs). APTs are a type of threat that can remain in the system for a long time and are difficult to detect. These attacks aim for durability in target systems and can be used for various hidden purposes.
The 2022 report published by SOCRadar clearly shows how widespread these attacks are. According to the data in the report, the most targeted country in 2022 was the United States, with the manufacturing industry ranking first in terms of industry.
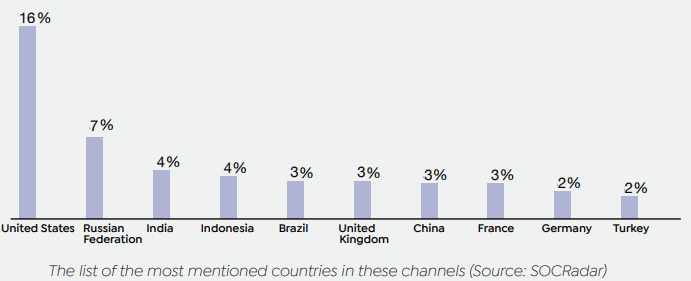
The same report also contains some cyber-attacks that took place in 2022 and targeted countries. Threat actors used these techniques mentioned in this article for the attacks between Russia-Ukraine, China-Taiwan, and China-India. DDoS attacks by Russia targeting Ukraine’s Ministry of Foreign Affairs and Ministry of Defense disrupted banking services. The tension between China-Taiwan escalated with the US sending representatives to Taiwan, and attackers hacked billboards in Taiwan and carried out DDoS attacks on government websites. Chinese-linked hackers used instant credit applications, part-time job promises, and fake cryptocurrency trading schemes to steal $529 million from Indian citizens.
Evaluating Threat Intelligence in Nation-State Cyber Attacks: Stages and Effectiveness

Many attacks are carried out on nations and states worldwide, and we can find examples of how threat intelligence is used both before and after an attack. One such example is the attack on Ukrainian energy companies in 2015.
In December of that year, threat actors believed to be supported by the Russian government carried out attacks on energy companies in two western regions of Ukraine. According to a report by Booz Allen Hamilton in 2016, the attack began with a spear-phishing campaign. The attackers then used malware called BlackEnergy2 and KillDisk to spread throughout target systems, gaining authorized access to real-time systems. The attack was designed to take control of many devices on the systems.
BlackEnergy2 was a tool used by attackers to infiltrate target systems, while KillDisk was used after the attack to disrupt the system and make it difficult to restore certain system files. These devices included power distribution devices, control centers, and their components. The attackers took control of these devices, cutting off electricity flow.
After the attack, threat intelligence analysts tracked the actors’ activities, discovered the malware they used, and identified the TTPs used in the attack. They also found the command and control servers used in the attack, allowing them to gather more information about the actors’ motivations and goals. This work by analysts led to tighter network security protocols, increased information exchange between energy companies and the government, and countermeasures to prevent similar attacks against Ukraine in the future. Other countries also learned from this example and added new solutions to their defense strategies.
Technical Approaches for Predicting and Mitigating Nation-State Threats
Threat intelligence plays a critical role in cybersecurity. This process identifies and analyzes information gathered about potential threats, attack patterns, and intentions. This information allows cybersecurity experts to identify IoCs and prevent threats, thereby strengthening the defenses of organizations/states. Additionally, threat intelligence helps organizations/states develop security policies and be prepared for future attacks.
The mission of threat intelligence is to collect information about tactics, techniques, and procedures (TTPs) used by threat actors. Over time, this information plays a role in identifying the unique characteristics of threat actors and tracking their harmful activities.
Threat intelligence identifies and tracks infrastructure elements used in attacks, such as command and control servers, domains, and IP addresses. By leveraging these elements that make up the threat actor’s infrastructure, it can be determined when they are active, and their activities can be tracked as they move from one target to another.
Threat Intelligence is also used to monitor social media and similar platforms to examine and track the behaviors of threat actors. Communication channels, social media accounts, user accounts, and groups on dark web platforms used by threat actors are monitored for this purpose. Thus, their abilities, targets, and motivations can be understood by monitoring threat actors. This helps predict their next moves and develop effective defense strategies.
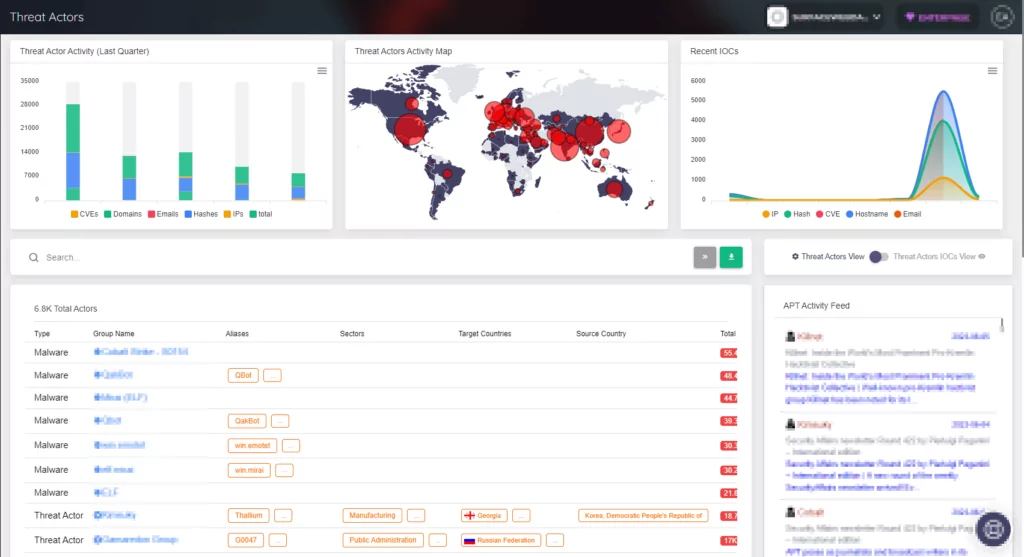
In summary, attacks targeting nations and states seriously threaten critical infrastructure and political figures. Threat intelligence usage is important for tracking and monitoring to prevent and predict these attacks. The concept of security should never be pushed into the background. The measures taken and strategies developed to provide a safer environment for states and nations.
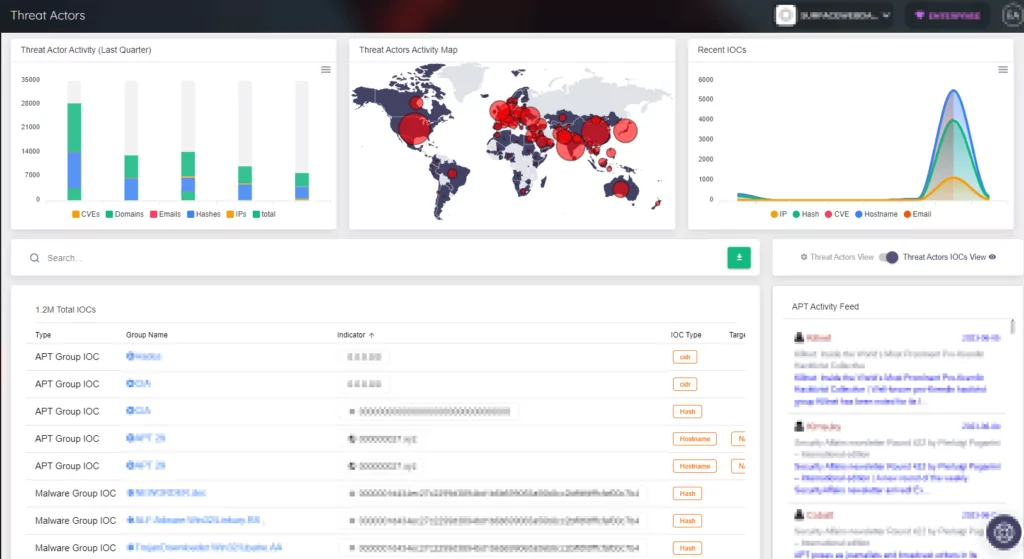
SOCRadar provides advanced threat intelligence and analysis capabilities to help its customers stay protected against nation-state attacks. The company’s threat detection and analysis systems use machine learning and human expertise to identify and analyze threat indicators from multiple sources. Its security operations center collaborates with customers to develop customized threat detection and response strategies. SOCRadar helps its customers stay ahead of nation-state attackers and quickly respond to potential threats.



































