The Ransomware Playbook: Evolving Threats and Defense Strategies for 2024
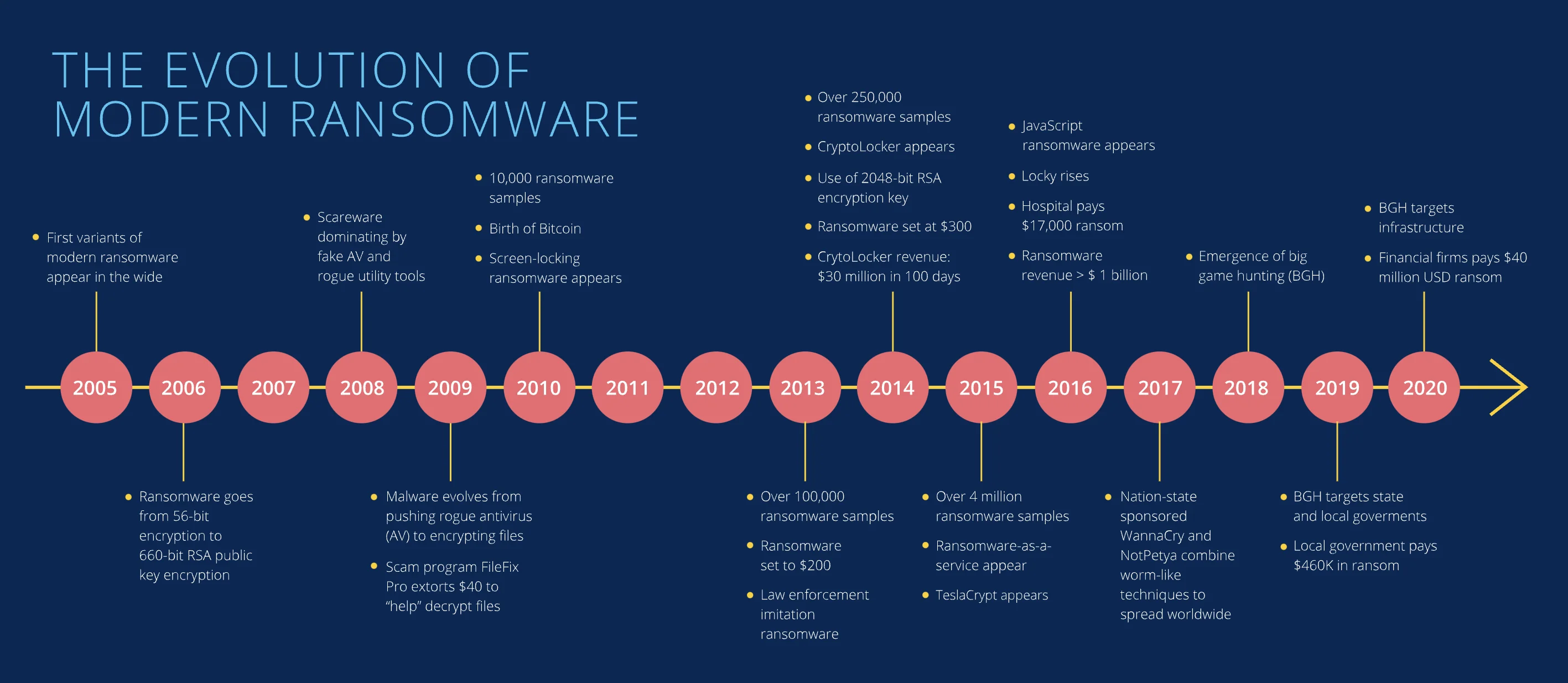
In 2024, ransomware will continue to rank as one of the most pervasive and effective threats to organizations globally. Attackers constantly refine their methods and use ever-more sophisticated attacks to cause maximum damage and attain the highest profit margins. Payments in 2023 smashed through the USD 1 billion mark, and the overall economic damage caused by ransomware—including direct financial loss, customer and partner trust, and impairment to company valuation—could go as far as USD 30 billion.
In recent discussions about the scope of ransomware attacks, one alarming example occurred when milking robots were paralyzed by ransomware, tragically leading to the death of a cow. This case highlights the alarming reality that no industry is off-limits, no system is invulnerable, and even living things can be affected by these increasingly pervasive threats.
As ransomware groups become more sophisticated with their assaults, the cyber defense strategies must keep pace. Layering traditional defenses against malicious actors is not enough to ensure ransomware avoidance. Organizations face a need to develop more flexible and forward-thinking methods to protect their digital assets and continue operations in hostile cyberspace.
In this article SOCRadar’s Advisory CISO, Ensar Seker, will detail the ransomware landscape today, outline the novel defense strategies set to emerge in 2024, and delve into best practices protecting organizations from these ever-evolving assails and persistent threats. By leveraging these innovative strategies and best practices, organizations can strengthen their defensive posture when facing ever-escalating threats.
The Current Ransomware Landscape
These attacks became more frequent, the attack methods became more advanced, and the financial and operational consequences of ransomware attacks became huge.
Evolving Tactics and Techniques in Ransomware Attacks
Ransomware attacks have significantly evolved, moving beyond simple file encryption to employ complex, multifaceted extortion strategies. These tactics are designed to exert maximum pressure on victims, increasing the likelihood of ransom payments. Here, we explore the key tactics of single, double, triple, and quadruple extortion ransomware.
- Single Extortion: Single extortion ransomware represents the most traditional form of ransomware attack. This attack vector has been around for a long time and is identifiable by a simple single tactic of encrypting a victim’s data and bargaining a ransom for its decryption. This is the most basic of the attack vectors implemented by ransomware operators over the years. Single extortion, although available in some particularly modern ransomware variations, is usually far less sophisticated than the other multi-extortion tactics employed.
- Double Extortion: With this strategy, attackers encrypt a victim’s data and steal sensitive information. With this threat vector, the strategy is more sophisticated, and the pressure on the victims becomes more intense as they may see their sensitive data released into the public domain if they don’t pay the ransom. This tactic had been used significantly by ransomware groups such as Maze and REvil, who realized the extra leverage they gained if they could threaten to expose their stolen data. Once attackers enter a network, it’s usually the same way they’d enter in any phishing or pretexting attempt or by exploiting a vulnerability. Upon successful intrusion, they will conduct reconnaissance to locate the data of interest, steal it, and then encrypt data residing in the network. The blackmail letter will be sent together with the demand for the ransom, threatening a release of the stolen data if the victims do not comply.
- Triple Extortion: Triple extortion ups the ante, threatening additional means of disruption beyond encryption and exfiltration. This might involve conducting a DDoS attack against the victim’s systems or extending direct threats to the victim’s clients, suppliers, or other associates to wreak further operational and reputational damage on those ultimately targeted in the extortion scheme. AvosLocker, for example, reportedly uses DDoS to support its triple extortion strategy, thereby adding an element of upstream disruption to the mix in addition to the double extortion of encryption and exfiltration.
- Quadruple Extortion: The latest iteration in the evolution of ransomware adds yet another extortionate ploy – contacting third parties with whom the victim of an attack had business relationships and extorting them as well. Or threatening to expose data from third parties to heap further pressure on a victim to pay up. Thus, the REvil ransomware gang took such action against the hardware supplier Quanta before approaching Apple (one of Quanta’s clients) when their ransom demands were initially not met.
Key Statistics and Trends
Increase in Ransomware Attacks:
- Ransomware attacks surged 66% from 2022 to 2023, with a notable spike in October 2023.
- In 2023, 72% of businesses worldwide were targeted by ransomware attacks, a significant increase from previous years.
Prevalence and Impact:
- In the last year, 59% of organizations were hit by ransomware, with 70% of these attacks resulting in data encryption.
- The average ransom payment increased by 500% over the last year, with 63% of ransom demands being $1 million or more.
Financial and Operational Costs:
- The average cost of recovering from a ransomware attack reached $2.73 million in 2023.
- Despite paying ransoms, 27% of organizations could not recover their data.
- A ransomware group called Dark Angels made headlines this past week when it was revealed the crime group recently received a record $75 million data ransom payment from a Fortune 50 company.
Attack Vectors and Methods:
- The primary infection vector has shifted from botnets to exploiting known vulnerabilities in public-facing applications.
- Attackers increasingly use legitimate software tools (e.g., PsExec, PowerShell, WMI) to carry out attacks, a tactic known as “living off the land.”
Targeting Diverse Platforms
At first, ransomware attacks exploited vulnerabilities in the Windows operating system. However, hackers have broadened their attack surfaces to include macOS and Linux servers, as they have become commonplace in data networks under the control of companies and governments, demonstrating the versatility of ransomware groups.
Ransomware-as-a-Service (RaaS)
Ransomware-as-a-Service (RaaS) actively encourages lower-skill-level cybercriminals to participate in more sophisticated ransomware operations. The RaaS model provides access to tools and infrastructure needed to conduct ransomware operations in exchange for sharing the profits with the service provider. By establishing this business model, RaaS massively increases the population of potential attackers and attack rates. It’s no secret nowadays that being in cybersecurity is big business.
Top 8 Notable Ransomware Families
The ransomware landscape in 2023 and 2024 has been heavily influenced by the activities of several high-profile ransomware families, each known for their sophisticated and destructive tactics. These groups have not only leveraged advanced encryption techniques but have also increasingly turned to double extortion methods, where they steal data before encrypting it and threaten to release this data if their ransom demands are not met. This approach significantly increases the pressure on victims, often leading to higher ransom payouts and more widespread damage.
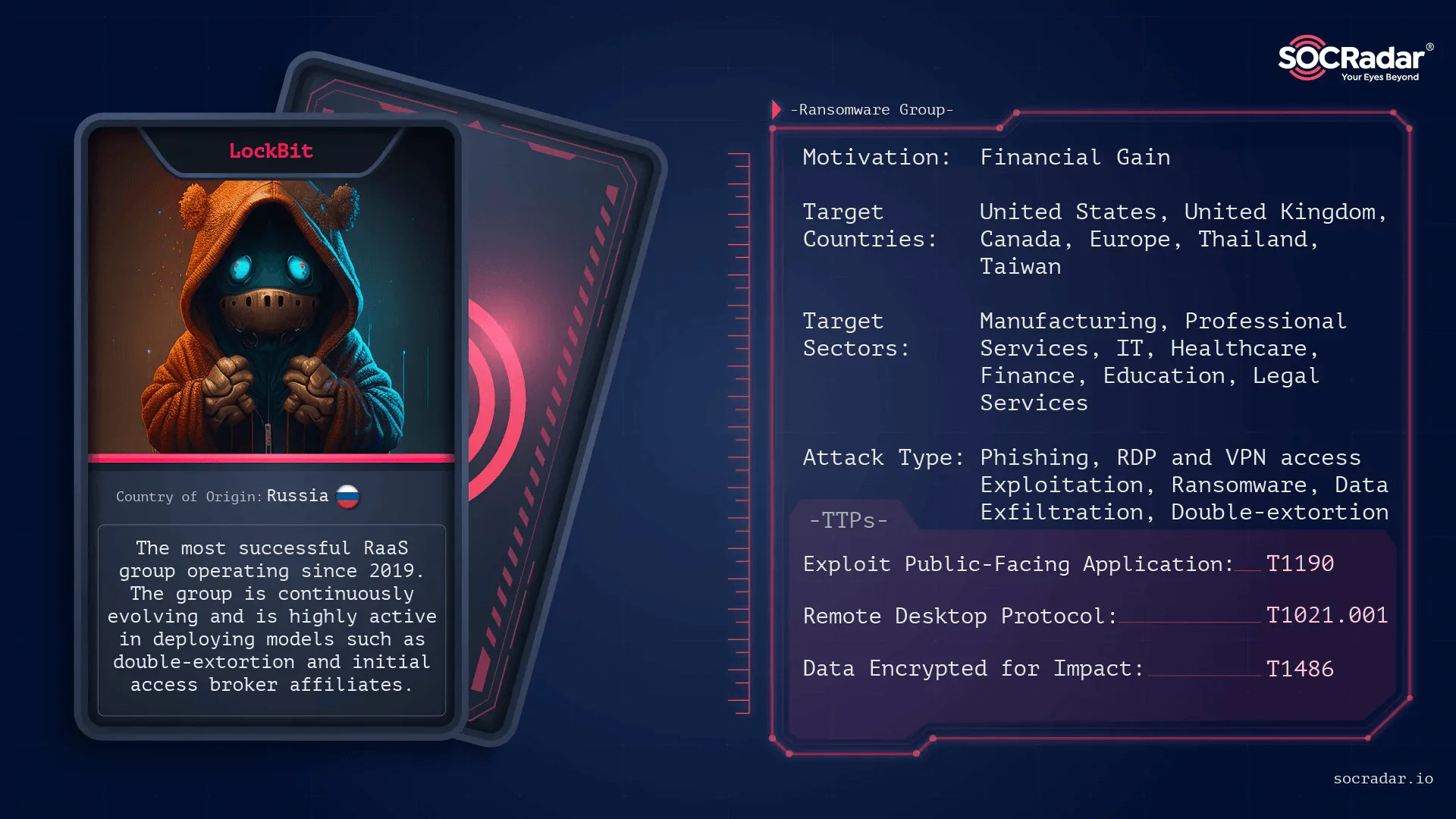
LockBit 3.0: One of the standout ransomware families of this decade is LockBit 3.0. This variant of the globally notorious ransomware got off to a strong start in February 2022, when it became the most commonly detected type of ransomware on corporate networks, according to a report from the security research firm Quick Heal. Like other leading ransomware, it benefitted immensely from a builder leak: a cache of code, domains, and all the cybercrime infrastructure needed to execute a launching ransomware campaign being leaked online. LockBit 3.0 had one of the biggest builder leaks in 2022 when an affiliate of the group let a builder leak go public. Within weeks of this leak, several independent cybergangs, with their clans of minions, were using their own custom-flavored LockBit variants to take on new victims after building their affiliates with the leaked starter codes. So, it’s not surprising that LockBit 3.0 remains a dominant force today, along with many other ongoing ransomware campaigns.
It has been tied to many breaches against everything from major corporations to government ministries and academia. The slew of high-profile LockBit attacks in 2023 – Boeing and even India’s National Aerospace Laboratories – demonstrated the group’s effectiveness in targeting and penetrating high-value victims, including large, well-defended corporations and enterprises. That’s no cheap trick. Sophisticated attack tools used by powerful cybercriminals require clever workarounds to overcome a sprawling array of defenses.
LockBit’s quick and widespread deployment in 2023 focused on compromise and extortion (not data theft with ‘double or nothing’ conditions attached) as the basic tactical strategy, proving that ransomware actors have moved successfully beyond ‘spray and pray’ malware onslaughts to show targeted aggression. The proliferation of LockBit and copycat offerings shows just how complex ransomware has become, as the trend is towards invasive and explosive deployment across various criminal networks.
However, international authorities struck a significant blow to LockBit 3.0 with Operation Cronos, which dismantled critical infrastructure and led to the arrest of key individuals involved, disrupting the group’s ability to carry out attacks. As we head into 2024, LockBit 3.0 continues to pose a dangerous threat to businesses worldwide, but the successful operation against it underscores the need for coordinated global efforts to outwit technologically driven attacks.
BlackCat/ALPHV: Debuting in December 2021, BlackCat quickly became the most aggressive and effective ransomware gang on the planet. By 2023, BlackCat had become the second most active ransomware group. Then, in December 2023, when law enforcement seized parts of their infrastructure, the gang bounced back rapidly. BlackCat ‘unseized’ several sites within the day and kept infringing on their seizure orders as if the enforcement action hadn’t happened. BlackCat is a group focused on constantly adapting, learning from previous successes and failures, and swiftly expanding its reach. BlackCat adopted a sophisticated, agile, and highly effective attack model even in its early days.
The group hammered virtually all types of organizations, a point driven home by the infection of Citrix. The group’s ability to keep reinventing marketing by hacking, even after a coordinated law enforcement action directly targeted them, speaks to their operational savvy and ability to shape-shift at will. However, in a surprising turn, BlackCat/ALPHV abruptly shut down operations in what security researchers describe as an ‘exit scam,’ posting a fake law enforcement seizure notice on their leak site after allegedly receiving a $22 million ransom from Change Healthcare. The move, which left an affiliate partner unpaid and still holding stolen data, underscores the lack of trust even within the ransomware ecosystem. Every time a government strikes, BlackCat responds by adapting and growing stronger, but this exit scam may make affiliates wary of future collaborations with any rebranded group linked to BlackCat.
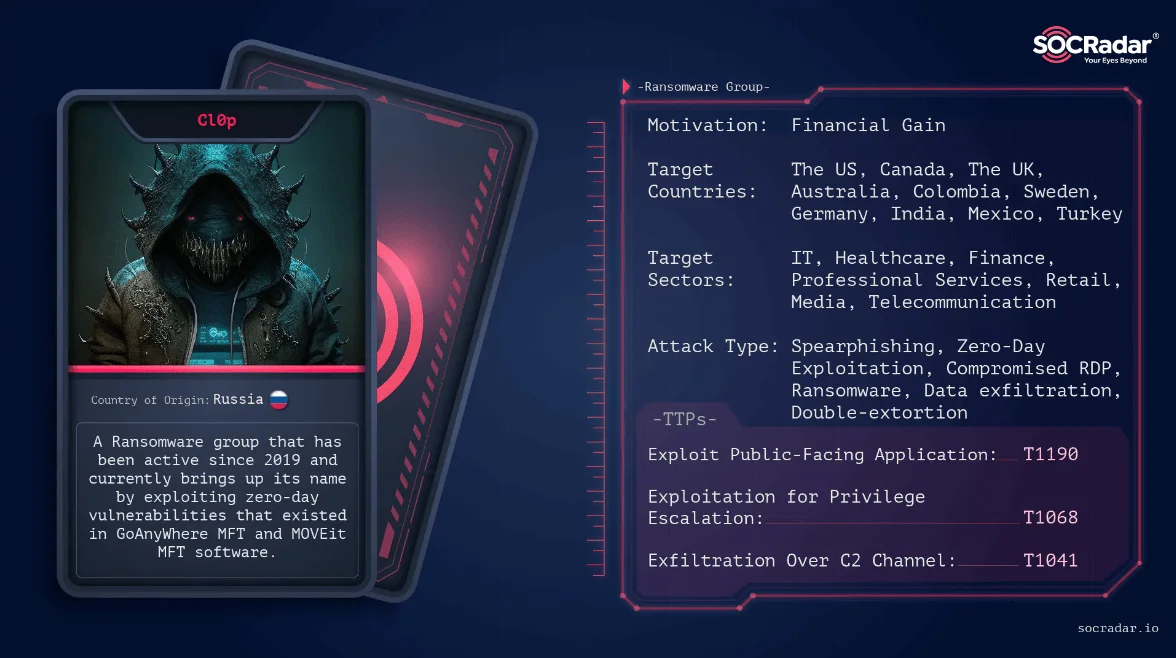
Cl0p: Cl0p became one of the most famous ransomware groups of 2023, ranking third overall for activity. This infamy stems primarily from its mass-scale exposure of a vulnerability in the MOVEit file transfer system, prompting numerous data leaks across more than 2,500 organizations worldwide. It exploited a widespread, highly dangerous software vulnerability that drew attention to Cl0p’s ability to find critical holes in widely used technology and to the damage that ransomware groups can inflict when they hammer such flaws with millions of dollars of attack resources.
Cl0p is part of the FIN11 threat actor, famed for double extortion: using tactics that not only lock up victims’ data but also hold a knife over their heads by threatening to publicize sensitive details to put extra pressure on the victim to pay the ransom. Cl0p’s attacks have often targeted the healthcare sector and many other vital industries. Because of these strategic and potent strikes, Cl0p’s rise represents a central core of relatively core ransomware activity and an essential part of today’s core threat to the global advancement and dissemination of networked technology.
RansomHub: RansomHub surfaced in February 2024 and soon became the most dominant ransomware. Only a few months later, RansomHub was rebranded and took up the pseudonym of its predecessor. RansomHub – soon to be known as the Knight ransomware – was reportedly a revival of the Knight group, which likely emerged from the disbanded Ragnar Locker gang. Between the months of February and June 2024, RansomHub became the most dominant ransomware group in existence – and, by June 2024, it was the most prevalent ransomware group. In just four months, they were responsible for 21 percent of published ransomware attacks.
RansomHub’s swift and brutal rise illustrates the rapid dynamics and continual change of the ransomware ecosystem: new groups can swiftly gain importance and thereby harm many organizations. Gaining such a large share of attacks in such a short time illustrates just how volatile the ransomware ecosystem really is. RansomHub was resurrected, thereby becoming the most dominant and most prevalent ransomware. This shows just how quick-moving the ransomware threat is and how frequently organizations need to develop new defenses. The emergence of RansomHub again shows how ransomware evolves. Ransomware keeps coming back with ever-new looks, constantly changing forms and disguises, as developers attempt to exploit potential vulnerabilities to shut down systems.
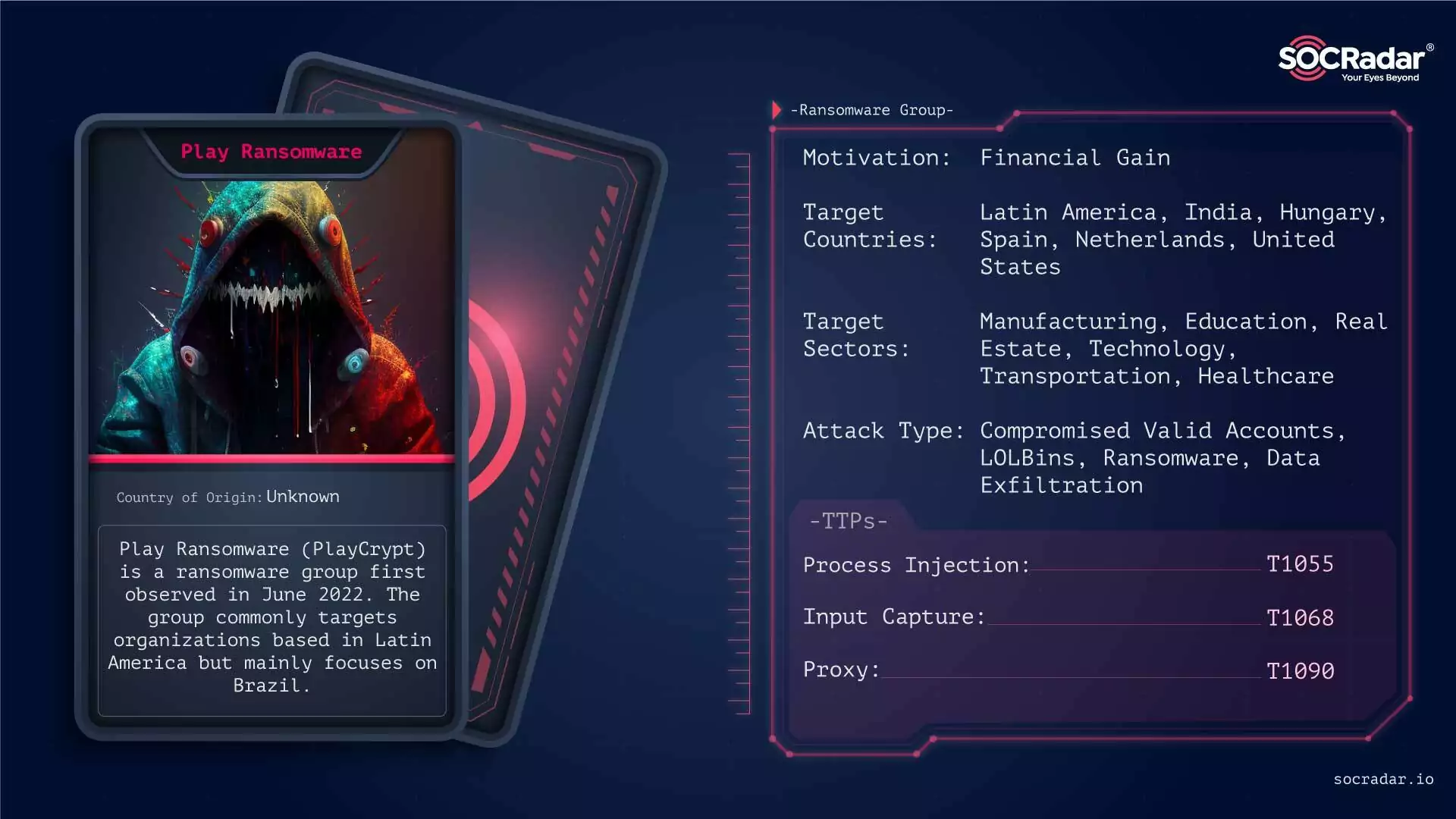
Play: Play ransomware is projected to take second place, with 8 percent of all ransomware attacks as of June 2024. This group first emerged in June 2022 and has quickly grown to pose a significant threat. It has targeted businesses and infrastructure across North and South America and Europe, as well as a variety of public and private targets across sectors, mostly in the Americas but also Russia and Europe. The group’s documented attacks disrupt operations in multiple sectors and are responsible for extensive digital damage, demonstrating the sophisticated nature of their attacks and how influential disruptions can be.
Play has orchestrated dozens of high-profile attacks, often targeting businesses and infrastructure essential to national and economic security, while usually publicly declaring victims well in advance. These statistics highlight Play’s operational capability and the strategic selection of its targets.
Akira: It became the first new ransomware family to surface in 2023 and stole 5 percent of reported ransomware attacks by June 2024 – a single group driving nearly two percent of these incidents. Akira also attacks both Linux systems in addition to Windows, something very few ransomware groups – if any others – can do. The presence of multi-platform ransomware like Akira illustrates the technical prowess of modern ransomware groups. Coding adaptations for Linux and Windows is a task that malware developers previously chose to skip because two operating systems aren’t twice as much work, but essentially four times as much since they differ in code and features. A team producing high-quality multi-platform ransomware needs complex support to ensure scalability. Akira’s presence suggests a hunger that signifies the expanding footprint of ransomware groups.
Medusa and 3AM: Medusa has targeted high-profile entities and generally charts a cautious path to avoid noise to maximise impact and enable substantial ransom demands, likely also founded on analysis that has identified the threat surfaces of specific targets. 3AM is a relatively new general-purpose ransomware coded in Rust that not only shows significant crossover indicators but appears to have become directly connected to the supply chain of LockBit through a LockBit affiliate, when 3AM was applied to the LockBit target, as opposed to initially LockBit, and the LockBit website blocks were first observed.
The evolution of Cybercriminal Tools-for-Hire into Ransomware-as-a-Service (RaaS), where the attackers bundle malware or coding as a service offering, has dramatically expanded the types of organizations at risk On the one hand, we have Medusa, and on the other 3AM, a relatively new general-purpose ransomware, written in Rust that has since seen explosive growth. 3AM first emerged with indicators of significant crossover in mid-January 2022, and by early February, it was reported on Dark Web forums as a replacement option for the LockBit ransomware.
What is clear from the case discussed here is that ransomware groups and their creation evolve as with other forms of malware. Cybercriminal Tools-for-Hire has evolved to RaaS, where the attackers bundle malware or coding as a service offering. This evolution has dramatically expanded the types of organizations at risk by potentially unleashing a plethora of new strains designed to overcome defenses and exploit vulnerabilities. This is manifested by the different behavior exhibited by Medusa (later emergent strains) and 3AM (later emergent strain).
Rhysida: The Washington Times, a significant conservative newspaper based in the U.S., has reportedly fallen victim to the Rhysida ransomware group. Rhysida came to prominence on the ransomware scene during the first half of 2023 and, over that time, has been relentless in its attacks on hospitals, doctors’ surgeries, and other high-profile targets. Its stated aim is to ‘help organizations find vulnerabilities,’ its victims include, among many others, the British Library and the US video game developer Insomniac Games. The message seems clear: we’re here, we’re bad, and we’re willing to target any public institutions and private enterprises we need to to achieve our goal. The fact that the group appears to have chosen the health sector for special attention is extremely concerning: the public perception that these organizations exist to improve and save human life makes them especially vulnerable to attacks that could cause anything from disruption to, potentially, loss of life.
Despite its belligerent and destructive nature, Rhysida has taken what can only be described as an unusual public-relations stance. The group refers to itself as a ‘cybersecurity team’ and claims that it’s in the best interests of its victims to be attacked by the group. Ransomware groups are usually blunt in their business: they extort money from victims. So, it’s surprising to hear that Rhysida performs attacks to reveal vulnerabilities in its victims. It claims these attacks are being conducted as ‘white-hat hacking’ – supposedly to help the identified organizations improve their defenses. Rarely do ransomware groups try to place their activities into a moral framework. Perhaps it’s simply a way to explain its conduct away, to appear as the ‘good guys.’ Or perhaps it reflects the reality of this new world of cybercrime, where ransomware groups are locked in an increasingly competitive struggle for market share in the murky business of ‘selling bytes’.
Sector-Specific Impacts of Ransomware
Manufacturing was the most targeted sector in 2023, accounting for 25.66% of attacks. One in five sensitive data items selected by healthcare organizations was hit However, where one sector has seen large-scale ransomware attacks, others will not be far behind. While an average of one in five targeted data items resulted from a ransomware infection across all sectors, some industry verticals have documented a higher average share. The impact of ransomware on health, government, and financial services will now be examined.
Healthcare: Healthcare providers are particularly susceptible to ransomware, and the median cost for healthcare organizations lost to ransomware derives from the disruption in service and the risks to patient outcomes when these digital workflows fail. When hospitals get hit, it’s the patients who suffer the consequences: procedures get delayed while administrators scramble to restore the workflows; emergency departments divert ambulances from their services to nearby providers; and interventional care that might run the risk of a poor health outcome without electronic access to a patient record might no longer be possible because secure communication between clinicians becomes an arduous task. Delays in patient care and outcomes, they say, are the most valid troubleshoots of ransomware.
The scale of operations means that healthcare organizations hold particularly personal databases – and personal data is highly valuable. Healthcare records commonly include financial and Social Security information and personally identifiable health information that can be of interest to cybercriminals but is difficult for the compromised organization to conceal. When ransomware hits hospitals and clinics, cybercriminals often include data dumps of sensitive patient information as part of the ransom demand. Patient health and safety, including reputational risk for hospitals, mounts pressure for healthcare providers to capitulate to a ransom demand to safeguard patient confidentiality and avert the potentially crippling financial and regulatory penalties that can result from ubiquitous data breaches related to digital healthcare records.
The costs of a ransomware attack can be catastrophic for healthcare organizations. The overall disruption to operations, including remediation and recovery, as well as legal and regulatory fines, can be staggering. The average cost to healthcare organizations per data breach is nearly double what an average company in other sectors might spend to mitigate the same crime.
Government: Government agencies are obvious, enticing targets for the creators and distributors of ransomware because of the critical public services they provide and the personal details they manage Government agencies provide some of the most essential services to the public community, including public safety, transportation, healthcare, cybersecurity and infrastructure management, among others. A ransomware attack on a government agency can jeopardize these critical services. Disruption of routine operations, from providing public services to protecting the homeland’s security, can have cascading effects. Chaos and loss of public trust can result if critical infrastructure is affected, such as emergency response or utilities.
If operations are impacted, our lives and liberties may be affected for an extended period. Ransomware operators that target government agencies can cause significant levels of operational disruption for victims, from public safety agencies to critical infrastructure managers. For instance, in New York City’s recent cyberattack, chaos ensued, requiring the physical reversion of clocks to the pre-computer age. Hospitals had to turn away patients, maintenance crews had to fix broken elevators, and morgues had to resort to using primitive methods such as writing down information.
What makes these attacks attractive to attackers is the potential financial payoff: government agencies will likely have the means to pay the ransom to quickly restore operations. A Chicago ransomware attack saw more than 100 municipal computers infected with malware, crippling the city government’s ability to provide services. The officers ended up paying a small amount of bitcoin (the digital currency used in such attacks) to end this IT nightmare. Educators and schools also face this challenge. Hawaii’s school system was hit by ransomware in March 2022, causing data loss, the inability to process food-ordering software for summer lunches, and shutting down email. Data breaches leading to exposures can worsen the damages. In a world where people are willing to give up personal data for a free cup of coffee or an entertainment app, governments have large amounts of media such information through ransomware can lead to a severe reputational hit for any organization that relies on its consumers’ trust.
For government agencies, if compromised or partially compromised personal data leads to public safety risks and national security problems, these reputational hits will produce political and social consequences. Loss of trust by citizens and political constituents for their government agencies will be catastrophic for those who collect and manage the information. The ultimate threats are political – a hack that leads to a reduction in people’s trust in the government’s ability to protect their personal information will erode the public’s confidence in government agencies. Citizens will no longer believe that their personal information – including legal records, medical records, police files, tax information, or financial information – is secure. Long-term impacts can occur if classified or sensitive information is exposed. Compromising sensitive data or threatening it – for instance, pending medical information on veterans receiving treatment in public hospitals or coronavirus vaccination records – will undermine trust.
Financial Services: The financial services sector is a common target for ransomware as it operates a vast network of continuous and complex transactions involving the trade of financial instruments and services, as well as the transfer and storage of vast amounts of personal information on retail and corporate customers. This critical data is perimeter to multiple money transfer systems, trading systems, online payment systems and customer access login facilities. An attack on one is likely to impact on the others. All this data is of huge value on the dark web, in which it is often traded for the purpose of extortion.
The potential for financial and reputational loss to a financial services business from this type of breach is extremely high. Customers place a great deal of trust in financial services and expect them to be protected. Once breached, that trust can be difficult or impossible to restore, and the business in question can then face significant scrutiny from regulators responsible for maintaining public trust in the sector. From an economic perspective, there’s no doubt that an organization that falls victim to ransomware can suffer a wide range of potential financial impacts. The most obvious of these is the loss of financial value arising from the direct disruption to data availability.
For financial services businesses, this could manifest in a loss or curtailment of core financial operations such as money transfer systems, trading systems, online payment systems, or customer access login facilities. There are also potential economic consequences as a result of third-party disruption. The financial sector is highly interconnected. An attack on one organization, even a small one, could cascade through the system, bringing affected operations to a standstill. This can potentially disrupt markets and even lead to widespread economic instability. So, not only does the financial services sector have a higher degree of interdependence than most other industries, but it also has the potential to impact the wider economy on a macro scale.
Regulatory requirements Financial services businesses are also subject to a very complex regulatory framework in terms of their approach to data protection and cybersecurity. When a ransomware attack happens, it can be very difficult for an affected business to meet its compliance requirements on protecting sensitive data, not to mention avoid any potential sanctions that remain an ever-present risk for any business that fails to protect itself adequately from cyber attacks. A breach that exposes a firm’s inability to protect its systems could result in a regulatory fine or, even worse, a lawsuit. Ensuring compliance with these regulations is not easy and requires growing investment in cybersecurity controls.
Emerging Ransomware Tactics
One of the notable advancements in ransomware tactics is the implementation of intermittent encryption, a method that differs significantly from traditional approaches, unlike conventional ransomware, which encrypts entire files, intermittent encryption targets only specific portions of a file. This partial encryption approach presents substantial challenges for detection because the files maintain statistical similarities to their original, unencrypted state. As a result, security tools, which often rely on identifying significant changes in file structure, find it more difficult to detect these attacks.
1. Intermittent Encryption
Intermittent encryption complicates detection and enhances the efficiency of ransomware attacks. By focusing on encrypting only parts of files—such as uniform-sized blocks or the initial segments of files—attackers can encrypt a greater number of files in a shorter period. This speed advantage allows the ransomware to cause widespread damage before security measures can respond effectively, increasing the likelihood that the attack will succeed in extorting a ransom. The evolution of this tactic reflects the broader trend in ransomware development, where attackers continuously innovate to outmaneuver security defenses and maximize the impact of their attacks.
Key Features
- Speed and Efficiency: By encrypting only parts of files, attackers can encrypt a larger number of files in a shorter time frame. This speed is crucial for evading detection systems, often triggered by the high resource usage associated with full file encryption.
- Stealth: The partial encryption approach makes it harder for security tools to distinguish between legitimate and malicious file modifications. This stealthiness allows ransomware to operate under the radar, reducing the chances of early detection and intervention.
Advantages for Attackers
- Faster Execution: Intermittent encryption significantly reduces the time required to encrypt data, allowing attackers to complete their operations before detection.
- Evasion of Detection: By encrypting only portions of files, ransomware can evade detection methods that rely on monitoring file input/output operations or analyzing file similarity.
- Increased Pressure on Victims: Victims may find recovering partially encrypted files from backups more challenging, increasing the likelihood of paying the ransom.
Several ransomware families have adopted intermittent encryption, including LockFile, Qyick, and BlackCat (ALPHV). These variants utilize different patterns and techniques to maximize the impact of their attacks while minimizing detection risks.
2. Data Theft and Exfiltration
Lately, ransomware groups have started to leverage aspects of the double extortion model by stealing and exfiltrating data even while encrypting it. This shift to adding data theft and exfiltration to the basic model (and subsequently holding them over the heads of victims) represents a serious erosion of the sanctity of data, exacting even further costs on victims who can hardly afford them.
It starts with an attacker exploiting vulnerabilities in a victim’s network, such as by deploying a phishing campaign, exploiting a system vulnerability, or stealing passwords. After establishing a foothold on the network, the attacker conducts internal reconnaissance to identify valuable and sensitive information, such as personally identifiable information, financial records, intellectual property, proprietary code, and other sensitive content. Following reconnaissance, the attacker extracts and steals the most valuable assets and exfiltrates the data from the victim’s network to a location under the attacker’s control.
Once the data has been stolen, the attackers move to the second part of a ransomware attack: they encrypt the victimized entity’s files, making them unavailable without a decryption key. Next, the actors behind the ransomware deliver their demand for a ransom payment. But they don’t stop there: they add an expiry threat, saying that if the threatened amount isn’t paid, they reserve the right to publish the stolen data. Thus, the victim would lose not only access to the stolen information but also exposure to compromising data. That’s what double extortion is: the combination of blocking the victim’s access to data and exposing that data publicly or through the sale to prurient interests on the so-called dark web. With this type of attack, the added pressure on victims increases considerably, and what looks like a broad level of coercive capability might force an organization to acquiesce to the ransom demand in order to avoid public dissemination of its sensational – or, as frequently seems to be the case with the medical-services sector, mundane – data.
3. AI-Driven Attacks
The infusion of AI capabilities into ransomware allows for more sophisticated campaigns than in the past and nearly undetectable attacks. Because programs like WormGPT are so easy to use, even novice hackers can execute complex campaigns that were once only possible for experienced actors.
How AI Enhances Ransomware Attacks?
- Sophisticated Phishing Campaigns: An AI tool can write realistic phishing emails, taking the text from available data sources to make it look like real communication. This means that phishing is becoming an even more effective attack on the environment so that ransomware can plant malicious seeds.
- Automation and Efficiency: AI will automate parts of the attack cycle, such as reconnaissance and exploitation,, so the attacker doesn’t have to involve as many humans in the attack lifecycle. Likewise, by optimizing and scaling attacks, AI can automate a lot of the computational burden to identify the vulnerability and exploit it.
- Real-Time Adaptation: The potential for AI-based ransomware that could automatically modify malware code in real-time to slip around signature- defenses.
- Language and Cultural Adaptation: Tools that help write phishing emails in multiple languages with appropriate grammar, cultural references, and localization increase the pool of possible victims and make attacks more convincing. Language and cultural adaptation will be among the most critical areas of natural language generation in the future. Generative language, in the form of formal and informal text via spoken or written means, is just the beginning.
Emerging Defense Strategies
- Advanced Moving Target Defense (AMTD): A sophisticated cyber target deflection strategy that continually changes the attack surface, providing insurmountable complexity and expense for the attacker. The key principle is that regular changes in system configurations, network paths, and other aspects thwart the attacker’s reconnaissance and exploitation. It’s akin to a moving target, hard to hit.
Technical Implementation:
- Dynamic IP Addressing: Frequently changing the IP addresses of critical systems to prevent attackers from locking onto a target.
- Micro-segmentation: Carving off small pieces of the network and putting each piece into an isolated segment with its controls for security and the ability to move.
- Software Diversity: Using multiple versions of software and operating systems in the same setting to limit the power of a single exploit.
- AI and Machine Learning-Driven Security: Artificial intelligence and machine learning are increasingly central to many modern cybersecurity defenses. These technologies ‘learn’ from the data, spot patterns, and decide what to do next with little or no human interaction. They’re especially useful for quickly detecting anomalies – the first hints of a ransomware attack.
Technical Implementation:
- Behavioral Analysis: Look at how users interact with their computers. Establish a norm. ‘Normal’ activity is anything that adheres to that norm. Any drifts or variations from this norm can trigger an alert.
- Automated Threat Detection: ML algorithms can sift through vast amounts of data to detect indicators of compromise (IoCs) much faster than traditional methods.
- Predictive Analytics: AI can analyze previous attack vectors and predict likely future ones, strengthening defenses against them.
- Self-Healing Endpoints: Minimising disruptions – and, most importantly, no forced downtime – makes its way into endpoint protection through a novel concept seen in a few commercial products: the so-called self-healing endpoint, or automatically-remediating endpoint. Self-healing endpoints would, in theory, detect the damage from a ransomware infection and return it to normal operation without human intervention or forcing that endpoint into protection or isolation.
Technical Implementation:
- Automated Rollbacks: Leveraging snapshots and backups to automatically revert systems to their pre-attack state upon detecting malicious activity.
- Integrity Monitoring: Continuous checking of critical system files and configurations for unauthorized changes or corruption, triggering automatic repairs.
- Resilient Architectures: Implementing redundancy and fault tolerance within system architectures to ensure that the overall system remains functional even if one part is compromised.
- Multi-Layered Defense Approach: A layered defense is designed to use numerous security measures at different locations within the network to create an overall security posture that protects against intrusion, even if one of the layers is breached.
Technical Implementation:
- Layered Access Controls: Implementing role-based access controls (RBAC) and multi-factor authentication (MFA) to restrict access to critical resources.
- Network Segmentation: Dividing the network into segments that can be individually secured and monitored to prevent lateral movement by attackers.
- Defense-in-Depth: Using firewalls, intrusion detection systems (IDS), and endpoint protection platforms (EPP) to have multiple points of detection and prevention.
- Proactive Threat Hunting: Proactive, active threat hunting is finding evidence of a threat long before any damage has been done. It’s not enough to be reactive; monitoring malware and attempting to detect indicators of compromise (IoCs) is only a halfhearted effort. Before something does or could cause harm, it must be acted upon.
Technical Implementation:
- Threat Intelligence Integration: Utilising threat intelligence feeds to stay up to date on ransomware groups’ latest TTPs.
- Anomaly Detection Tools: Employing software that can spot unusual aberrations in network behavior that act as indicators of an attack.
- Incident Response Drills: Conduct regular simulations of attacks to improve the efficacy of the threat-hunting team and processes.
- Data Exfiltration Prevention: Avoiding a ransomware attack requires preventing data exfiltration. Since we are also becoming more immersed in double extortion, enterprises need to invest in sophisticated detection and mitigation controls to pinpoint and block malevolent data transfers.
Technical Implementation:
- Data Loss Prevention (DLP) Solutions: Deploying DLP software to monitor, detect, and block unauthorized data transfers within and outside the network.
- Encryption: Ensuring that all sensitive data is encrypted, whether in transit or at rest so that it remains inaccessible to attackers who manage to breach network defenses and install a backdoor.
- Network Monitoring: Use state-of-the-art network monitoring software to look for suspicious patterns of data flows and prevent exfiltration that can go unnoticed.
Future Ransomware Trends
Here are some trends as ransomware keeps evolving, which will reshape the threat landscape in 2024 and beyond. Threat Actors are now gaining confidence to attack large enterprise companies, testing the current state of cybersecurity and public reaction to such high-profile attacks. Intense criminal competition forces cybercriminals to demonstrate they deserve access to exploits and resources to avoid competition from other threat actors. Attacks are increasingly nuanced and complex, involving intermediaries in the ransom negotiation process.
Increased Use of AI and Machine Learning
- Sophistication and Adaptability: Threat actors use AI and machine learning to create more sophisticated and intelligent ransomware strains. Because formidable security measures are now in place, security experts believe that successful ransomware attacks require malware strains that can evade traditional security measures. More sophisticated and intelligent ransomware is now possible because machine learning allows ransomware to become more adaptive to ever-changing measures. Advanced machine learning can automate the various stages of the attack process and make ransomware more efficient and less reliant on threat actors’ manual guidance.
- Advanced Phishing and Evasion: AI can help craft better spoofing emails or automatically conduct research on attack targets, making going after businesses easier, more effective, and stealthier. Deliberately rendering them virtually indestructible, AI-powered malware encoded to mutate in real-time, dynamically altering its code structure in response to efforts to neutralize it.
- Lower Barrier to Entry: AI tools such as large language models reduce the technical barrier to entry for cybercriminals, making it so that even less technically savvy actors can mount sophisticated campaigns.
Focus on Critical Infrastructure
- Targeting Vital Sectors: Ransomware groups repeatedly infiltrate critical sectors, such as energy and transportation. An attack on the energy sector could result in a mass blackout that causes human casualties.
- Potential Impact: Interfering with key infrastructure can create cascading operational consequences across an economy, major economic losses, and risks to national security. Major infrastructure sectors also highlight the importance of tighter protections of critical national services.
Enhanced Collaboration Among Cybercriminals
- Alliances and Resource Sharing: Alliance-building among cybercriminals and increased resource-sharing are fuelling more coordinated and potent ransomware campaigns. This is because their expertise and tools can be pooled, which leads to larger and more impactful campaigns.
- Advanced and Sophisticated Ransomware-as-a-Service (RaaS): The RaaS model increases collaboration in cybercrime by allowing purchasers to rent ransomware tools and infrastructure and assault their targets without creating their malware.
The future of ransomware is characterized by increased sophistication, a focus on critical infrastructure, and enhanced collaboration among cybercriminals. To prevent the escalation of ransomware, every enterprise will need to strengthen its cybersecurity defenses through improved detection and response systems, including AI-based tactics. By staying vigilant and proactive, businesses can better protect themselves against the growing threat of ransomware attacks in 2024 and beyond.
Get the SOCRadar’s “A 100M+ USD Negotiator’s Guide to Surviving Ransomware” Whitepaper!
References
- https://www.researchgate.net/publication/381910812_The_Evolution_of_Ransomware_Tactics_Techniques_and_Mitigation_Strategies
- https://www.armordot.com/2024/07/06/evolution-of-ransomware-new-tactics-and-defenses-in-2024/
- https://www.ncb.coop/blog/ransomware-has-evolved-updated-2024-trends-best-practices
- https://infosecwriteups.com/ransomware-evolution-and-defense-strategies-481c79fc5a13
- https://www.sophos.com/en-us/content/state-of-ransomware
- https://www.reliaquest.com/blog/q2-2024-ransomware/
- https://socradar.io/top-50-cybersecurity-statistics-in-2024-essential-insights-on-ransomware-phishing-industry-trends-and-more/
- https://therecord.media/ransomware-tracker-the-latest-figures
- https://www.acronis.com/en-us/blog/posts/quadruple-extortion-ransomware/
- https://www.upguard.com/blog/double-extortion-ransomware
- https://www.sentinelone.com/cybersecurity-101/threat-intelligence/what-is-double-extortion/
- https://www.paloaltonetworks.com/cyberpedia/what-is-multi-extortion-ransomware
- https://www.zscaler.com/resources/security-terms-glossary/what-is-double-extortion-ransomware
- https://www.cdotrends.com/story/3994/ransomwares-sneaky-new-trick-intermittent-encryption-here
- https://guardiandigital.com/resources/blog/ransomware-groups-make-the-move-to-intermittent-encryption
- https://www.techtarget.com/searchsecurity/news/252525641/Intermittent-encryption-attacks-Whos-at-risk
- https://www.sentinelone.com/labs/crimeware-trends-ransomware-developers-turn-to-intermittent-encryption-to-evade-detection/
- https://blog.checkpoint.com/security/newest-ransomware-trend-attackers-move-faster-with-partial-encryption/
- https://www.munichre.com/specialty/global-markets-uk/en/insights/cyber/what-is-intermittent-encryption.html
- https://www.forbes.com/councils/forbestechcouncil/2023/02/01/intermittent-encryption-is-a-growing-ransomware-threat-that-requires-a-proactive-cyber-defense/
- https://www.mailgun.com/blog/email/ai-phishing/
- https://www.crawco.com/blog/artificial-intelligence-and-the-increasing-complexity-of-phishing-attacks
- https://www.cnbc.com/2023/11/28/ai-like-chatgpt-is-creating-huge-increase-in-malicious-phishing-email.html
- https://www.metacompliance.com/blog/phishing-and-ransomware/how-ai-enables-sophisticated-phishing-attacks
- https://siliconangle.com/2024/04/23/zscaler-report-warns-ais-growing-role-sophisticated-phishing-attacks/
- https://krebsonsecurity.com/2023/08/meet-the-brains-behind-the-malware-friendly-ai-chat-service-wormgpt/
- https://www.darkreading.com/cyberattacks-data-breaches/wormgpt-cybercrime-tool-heralds-an-era-of-ai-malware-v-ai-defenses
- https://www.fbi.gov/contact-us/field-offices/sanfrancisco/news/fbi-warns-of-increasing-threat-of-cyber-criminals-utilizing-artificial-intelligence
- https://blog.barracuda.com/2023/11/13/ai-ransomware-adapt-stay-protected
- https://blog.purestorage.com/perspectives/the-threat-of-ai-powered-ransomware-attacks/
- https://www.domaintools.com/resources/blog/the-most-prolific-ransomware-families-2023-edition/
- https://thehackernews.com/2024/01/3-ransomware-group-newcomers-to-watch.html
- https://www.blackfog.com/the-top-10-ransomware-groups-of-2023/
- https://www.hhs.gov/sites/default/files/ransomware-healthcare.pdf
- https://www.dhs.gov/sites/default/files/2022-09/Ransomware%20Attacks%20.pdf
- https://www.ncbi.nlm.nih.gov/pmc/articles/PMC9856685/
- https://logrhythm.com/blog/healthcare-ransomware-attacks/
- https://www.xorlab.com/en/blog/impact-of-ransomware-healthcare-sector
- https://blog.purestorage.com/perspectives/the-threat-of-ai-powered-ransomware-attacks/