
A Snapshot of 2023 CWE Top 25 Most Dangerous Software Weaknesses

The 2023 CWE Top 25 Most Dangerous Software Weaknesses is a list that ranks the most widespread and critical weaknesses that can lead to serious vulnerabilities in software. An attacker can often exploit these vulnerabilities to take control of an affected system, steal sensitive information, or disrupt service.
The list is prepared by the Homeland Security Systems Engineering and Development Institute, which is sponsored by the Department of Homeland Security and operated by MITRE. It was released on June 29, 2023.
The aim of the list is to guide developers and security response teams in identifying and rectifying common software weaknesses. The list helps professionals prioritize the most dangerous and prevalent vulnerabilities, thereby improving the overall security of their software. The list also serves as a valuable resource for education and awareness in the field of software security.
Let’s take a look at the list with the help of SOCRadar Threat Intelligence.
What is in the Top 25 CWE?
The 2023 CWE Top 25 list is derived from a comprehensive dataset of all CVE Records published in 2021 and 2022. However, to ensure accuracy, the dataset was refined by removing invalid records, those with insufficient information for accurate root cause mapping, or those marked as CWE-Other without an appropriate mapping within View-1003. To further enhance the list’s utility, a subset of 7,466 CVE records was independently analyzed for their root cause mappings. This involved remapping existing root cause mappings when necessary, using the entire CWE corpus for these remappings.
The ranking of the weaknesses in the list is determined through a scoring formula that combines the frequency of a CWE being the root cause of a vulnerability and the average severity of each of those vulnerabilities when exploited. This is measured by the NVD and the Common Vulnerability Scoring System (CVSS) score. The level of danger presented by a particular CWE is then determined by multiplying the severity score by the frequency score, ensuring that the list accurately reflects the most dangerous software weaknesses based on their prevalence and the severity of the vulnerabilities they cause when exploited.
While the CVSS is a valuable tool for assessing IT system vulnerabilities, it has limitations. It heavily relies on the base score for risk analysis, may lead to an inflated perception of risk, and it may not adequately represent non-IT systems. Additionally, it lacks fine granularity, its temporal metrics have limited impact, and its scoring formula can be overly complicated. To address these issues, CVSS v4.0 is being prepared for release. However, there is already a solution to these potential downsides. SOCRadar developed Vulnerability Risk Scoring (SVRS), which prioritizes higher-risk vulnerabilities by considering qualitative elements from various sources, such as Social Media, News, Code Repositories, Dark/Deep Web, and attribution with threat actors and malware. It provides a more comprehensive understanding of risks and enabling more effective risk management.
What Changed from 2022?
|
Rank |
ID |
Name |
Score |
CVEs in KEV |
Rank Change vs. 2022 |
|
1 |
Out-of-bounds Write |
63.72 |
70 |
0 |
|
|
2 |
Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) |
45.54 |
4 |
0 |
|
|
3 |
Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) |
34.27 |
6 |
0 |
|
|
4 |
Use After Free |
16.71 |
44 |
+3 |
|
|
5 |
Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) |
15.65 |
23 |
+1 |
|
|
6 |
Improper Input Validation |
15.5 |
35 |
-2 |
|
|
7 |
Out-of-bounds Read |
14.6 |
2 |
-2 |
|
|
8 |
Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) |
14.11 |
16 |
0 |
|
|
9 |
Cross-Site Request Forgery (CSRF) |
11.73 |
0 |
0 |
|
|
10 |
Unrestricted Upload of File with Dangerous Type |
10.41 |
5 |
0 |
|
|
11 |
Missing Authorization |
6.9 |
0 |
+5 |
|
|
12 |
NULL Pointer Dereference |
6.59 |
0 |
-1 |
|
|
13 |
Improper Authentication |
6.39 |
10 |
+1 |
|
|
14 |
Integer Overflow or Wraparound |
5.89 |
4 |
-1 |
|
|
15 |
Deserialization of Untrusted Data |
5.56 |
14 |
-3 |
|
|
16 |
Improper Neutralization of Special Elements used in a Command (‘Command Injection’) |
4.95 |
4 |
+1 |
|
|
17 |
Improper Restriction of Operations within the Bounds of a Memory Buffer |
4.75 |
7 |
2 |
|
|
18 |
Use of Hard-coded Credentials |
4.57 |
2 |
-3 |
|
|
19 |
Server-Side Request Forgery (SSRF) |
4.56 |
16 |
2 |
|
|
20 |
Missing Authentication for Critical Function |
3.78 |
8 |
-2 |
|
|
21 |
Concurrent Execution using Shared Resource with Improper Synchronization (‘Race Condition’) |
3.53 |
8 |
1 |
|
|
22 |
Improper Privilege Management |
3.31 |
5 |
7 |
|
|
23 |
Improper Control of Generation of Code (‘Code Injection’) |
3.3 |
6 |
2 |
|
|
24 |
Incorrect Authorization |
3.16 |
0 |
4 |
|
|
25 |
Incorrect Default Permissions |
3.16 |
0 |
-5 |
Table 1: Top 25 CWE
The 2023 CWE Top 25 list shows some interesting changes compared to the 2022 list. The top three most dangerous software weaknesses remain the same, with CWE-787 (Out-of-bounds Write), CWE-79 (Improper Neutralization of Input During Web Page Generation, also known as ‘Cross-site Scripting’), and CWE-89 (Improper Neutralization of Special Elements used in an SQL Command, or ‘SQL Injection’) retaining their positions.
However, there have been notable shifts in the rankings of other weaknesses. For instance, CWE-416 (Use After Free) has climbed up three places to the 4th position, and CWE-78 (Improper Neutralization of Special Elements used in an OS Command, or ‘OS Command Injection’) has moved up one place to the 5th position. Conversely, CWE-20 (Improper Input Validation) and CWE-125 (Out-of-bounds Read) have both dropped two places to the 6th and 7th positions, respectively.
Further down the list, CWE-862 (Missing Authorization) has made a significant leap, moving up five places to the 11th position. This upward trend indicates an increase in the number of instances where a software product fails to ensure that an actor is authorized to perform an action, leading to a potential security risk. The shift in ranking is potentially due to systems becoming increasingly complex and interconnected. As we incorporate more services and functions into our digital systems, the need for robust authorization controls becomes crucial.
On the other hand, CWE-269, or Improper Privilege Management, has seen a significant rise of 7 ranks this year. This particular weakness occurs when a system grants unauthorized privileges or permissions to an actor, potentially leading to unauthorized actions. A contributing factor to this rise might be the increasing adoption of cloud infrastructures, which are often managed via Identity and Access Management (IAM) systems. These systems can be quite complex, with intricate layers of user roles and permissions that, if not properly managed, can leave the system vulnerable to attacks. In addition, cloud systems can have critical vulnerabilities affecting the system, further enhancing the arsenal for attackers, such as the critical CVE-2022-29972 vulnerability on Azure.
These changes reflect the evolving landscape of software vulnerabilities and highlight the need for continuous monitoring and updating of security practices.
Snapshot: Top 5 CWE
CWE-787 – Out-of-bounds Write
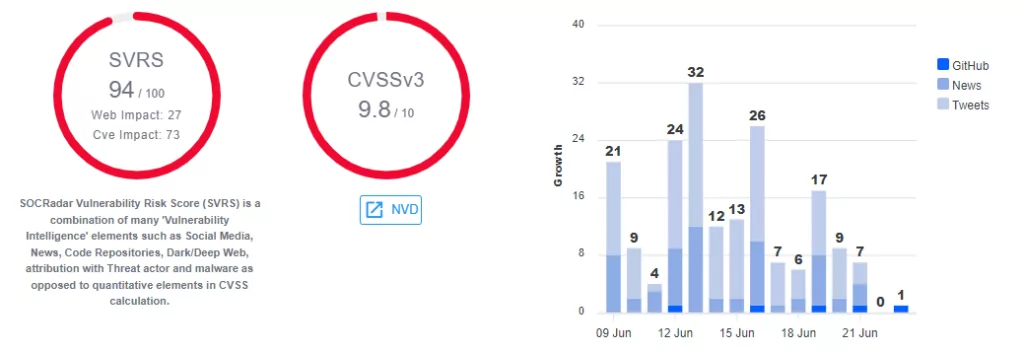
Out-of-bounds Write weakness occurs when the software writes data past the end or before the beginning of the intended buffer. This can corrupt data, crash the program, or lead to the execution of malicious code. CWE-787 has the highest number of vulnerabilities, 70, listed on the CVE KEV catalog.
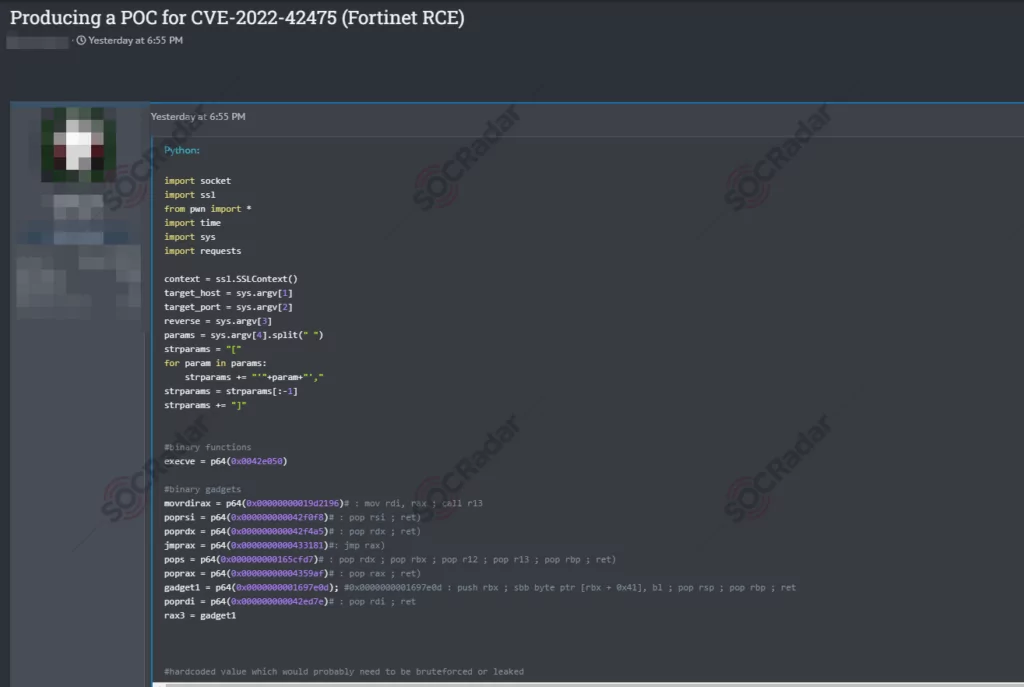
On March 2023, SOCRadar detected a proof-of-concept (PoC) shared on a dark web forum for an Out-of-bounds Write vulnerability (CVE-2022-42475) which affects FortiOS SSL-VPN and FortiProxy SSL-VPN. It can potentially allow a remote unauthenticated attacker to execute arbitrary code or commands via specifically crafted requests. Earlier this year, SOCRadar reported on the exploitation of the vulnerability by BoldMove Malware.
SOCRadar constantly monitors underground places to get ahead of the curve. If a vulnerability is trending on the dark web, you can receive a heads-up to implement the required security measures.
CWE-79 – Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’)
Cross-site scripting (XSS) vulnerabilities occur when an application includes untrusted data in a new web page without encoding according to context or updates an existing web page with user-supplied data using a browser API that can create HTML or JavaScript (DOM XSS). XSS allows attackers to execute scripts in the victim’s browser, which can hijack user sessions, and access Document Object Model (DOM).
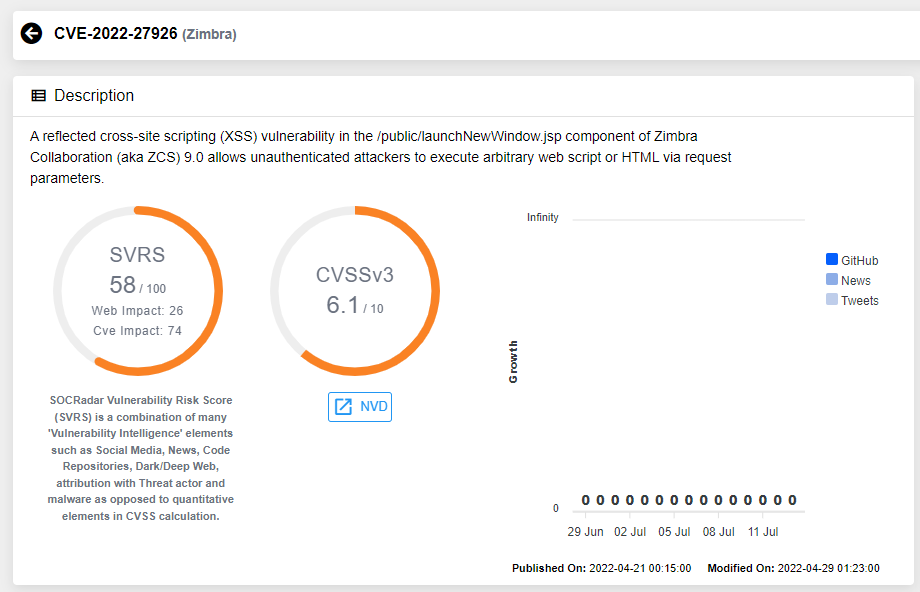
Just a couple of months ago, SOCRadar reported that Winter Vivern has initiated a phishing scheme aimed at infiltrating the email systems of governmental agencies across various European nations. The group exploited an XSS flaw in Zimbra Collaboration software tracked as CVE-2022-27926.
CWE-89 – Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’)
SQL Injection involves the insertion of SQL query via the input data from the user to the application. A successful SQL injection exploit can read sensitive data from the database, modify database data, execute administration operations on the database, recover the content of a given file present on the DBMS file system, and in some cases, issue commands to the operating system.
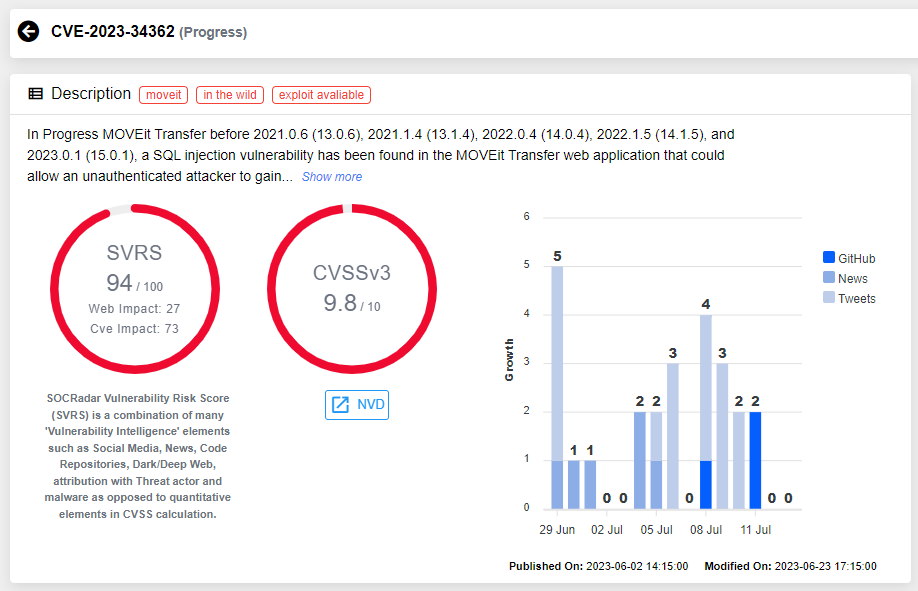
In May 2023, The CL0P ransomware group publicly claimed responsibility for the exploitation of a SQL injection zero-day vulnerability in MOVEit Transfer, CVE-2023-34362. Since then, they publicly announced hundreds of ransomware victims. This massive wave of victims was the result of CL0P leveraging the MOVEit Transfer vulnerability.
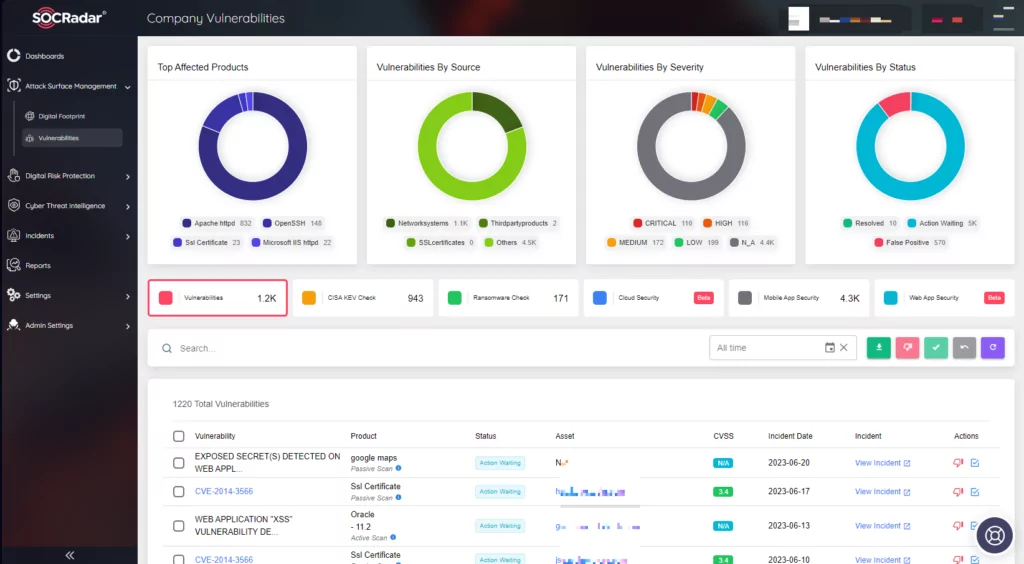
SOCRadar, with its Attack Surface Management service, constantly monitors external-facing digital assets and provides additional visibility and context regarding the severity of unknown external-facing digital assets in an automated manner. With it, you can track what CVEs are in your environment and can get helpful information on how to act against them.
CWE-416 – Use After Free
Use-after-free refers to the attempt to access memory after it has been freed, which can lead to a variety of adverse consequences—ranging from the corruption of valid data to the execution of arbitrary code, depending on the instantiation and timing of the flaw. The attempt to execute a freed object can be particularly pernicious, as it may often be assumed that the object’s memory is still allocated and that the object is still valid.
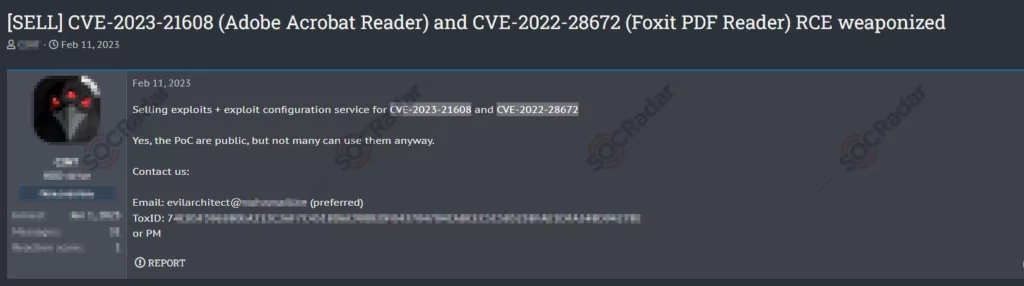
Back in February 2023, SOCRadar detected an exploitation sale for CVE-2023-21608, a use-after-free vulnerability on Adobe Acrobat Reader, and CVE-2022-28672 vulnerability on Foxit PDF Reader.
CWE-78 – Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’)
OS command injection weakness occurs when the software constructs all or part of an OS command using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended OS command when it is sent to a downstream component. This can allow attackers to modify the command to be executed, leading to serious security breaches.
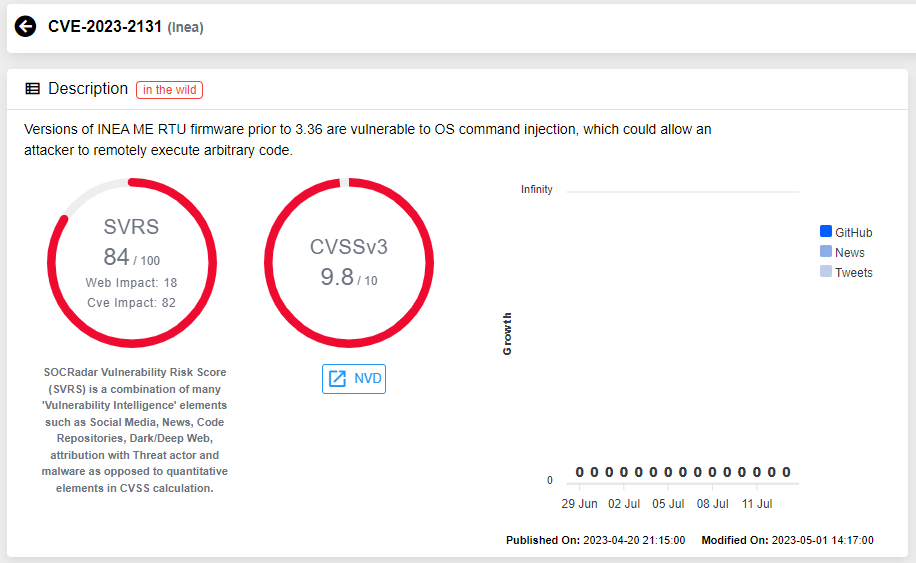
Back in April, a critical OS Command Injection vulnerability was discovered in a remote terminal unit (RTU) produced by Slovenia-based industrial automation company Inea. This vulnerability could potentially expose industrial organizations to remote cyber-attacks. The US Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory about the vulnerability pointing out the criticality of the vulnerability. The vulnerability is being tracked as CVE-2023-2131 and given a CVSS score of 9.8. The affected product provides a data interface between remote field devices and the control center via a cellular network and is used worldwide in industries such as energy, transportation, and water and wastewater.
Conclusion
The 2023 CWE Top 25 list is not just a ranking of software weaknesses; it’s a call to action for developers and security teams to prioritize and address these vulnerabilities in their software. The list serves as a roadmap for improving software security, highlighting the areas where efforts can have the most significant impact. The changes in the rankings from the previous year underscore the dynamic nature of software vulnerabilities and the need for continuous vigilance and adaptation in security practices.
The top five weaknesses provide a snapshot of the most pressing threats in software security. These weaknesses, if exploited, can lead to serious consequences such as data corruption, system crashes, or even the execution of malicious code. The examples provided by SOCRadar’s threat intelligence reports illustrate the real-world implications of these weaknesses and the importance of timely detection and mitigation. The continuous monitoring and updating of security practices are crucial in this ever-evolving landscape of software vulnerabilities. The 2023 CWE Top 25 list serves as a critical tool in this endeavor, guiding efforts toward the most prevalent and dangerous software weaknesses.



































