Analysis of the Critical Infrastructure Industries From a Cybersecurity Perspective
‘By 2024, a cyberattack will so damage critical infrastructure that a member of the G20 will reciprocate with a declared physical attack’ is one of Gartner’s strategic planning assumptions about critical infrastructure.
Cyberattacks on critical infrastructure have increased considerably in recent years. The vulnerabilities of technological innovations and changes have been essential to this increase. Realizing that critical systems are more sensitive to interruptions, threat actors have advanced their attacks on organizations in the critical infrastructure industry.
Gartner made the assumption mentioned above in this context to raise awareness about the increasing frequency, impact, and sophistication of cyberattacks on critical infrastructure. On the other hand, President Biden signed the Cyber Incident Reporting for Crucial Infrastructure Act (CIRCIA) of 2022 into law in March 2022. CIRCIA required Cybersecurity & Infrastructure Security Agency (CISA) to establish the Ransomware Vulnerability Warning Pilot (RVWP) program, which began on January 30, 2023. As part of RVWP, CISA announced undertaking a new effort to warn critical infrastructure entities that their systems have exposed vulnerabilities that ransomware threat actors may exploit on March 13, 2023.
What are Critical Infrastructures?
Although the definition of critical infrastructures differs by country, in general, critical infrastructures are physical and virtual assets, systems, and networks that can cause loss of life, national security vulnerabilities, disruption of public order, and large-scale economic damage if their accessibility, confidentiality, and integrity are compromised.
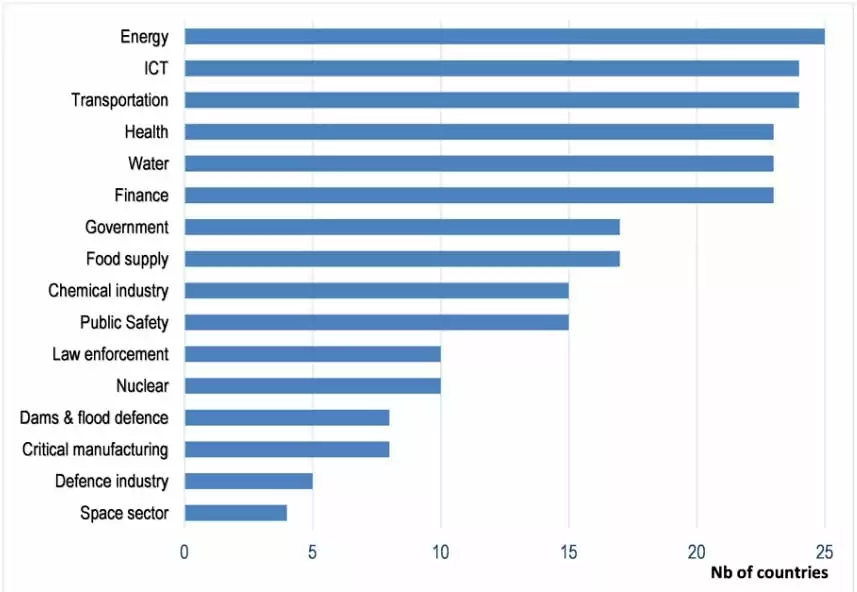
The chart above illustrates which industry is acknowledged as the critical infrastructure by how many members, based on responses from 25 OECD countries. CISA classified critical infrastructures based on functional and structural similarities, and 16 industries were designated as critical infrastructures.
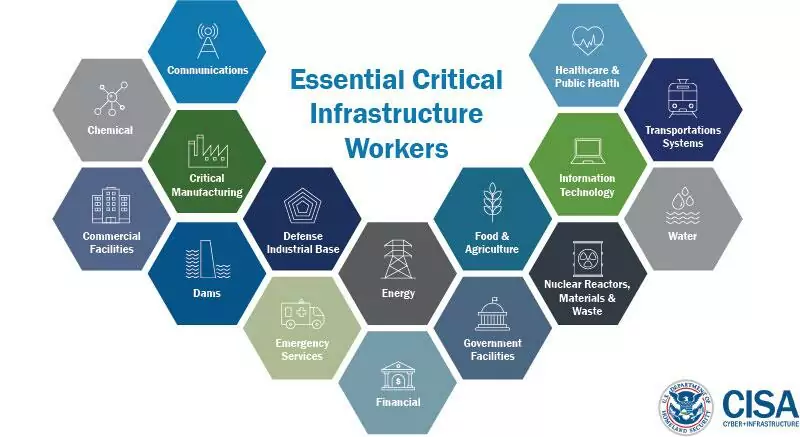
Critical infrastructures such as power generation and distribution, water and wastewater, healthcare, finance, transportation, food, and agriculture, which are vital to modern society, are also interdependent. An attack on one can affect others, and the resulting domino effect can cause social chaos.
Almost all critical infrastructures are targeted by many threat actors, such as state-sponsored threat actors, cyber terrorists, cybercriminals, and hacktivists. Ransomware, DDoS assaults, data breaches, supply chain attacks, and destructive attacks are carried out by threat actors with motivations such as demonstrating power, spreading terror, cyber espionage, disturbing social order, political advantage, and financial gain.
Why do Threat Actors target Critical Infrastructure Industries?
Digital systems control physical systems in many critical infrastructures, so attacks on such structures can potentially cause serious physical harm. Attacks on critical infrastructure can result in significant economic losses, threaten human life, or negatively impact the environment. Since systems in critical infrastructure industries must always be maintained operational, ensuring their availability and integrity is crucial. Furthermore, geopolitical tensions and political objectives play a significant role in attacks on these industries. These unique features of critical infrastructures also constitute their weaknesses against attacks. The reasons for attacks can be listed as follows:
- Companies in critical infrastructure industries are more intolerant to disruptions, so they may be braver negotiating with threat actors to minimize interruptions.
- Technological factors, system vulnerabilities, and widespread usage of attack tools ‘as a service,’ which are generally valid in the increase in all cyberattacks, also raise the risk for critical infrastructures.
- Some of the critical infrastructure industries are non-profit ones. Their budget is generally limited, and they do not have sufficient resources for cybersecurity investments.
- Many critical infrastructures use industrial control systems (ICS) and operational technology (OT) to control physical systems. Several ICS and OT systems were designed when digitalization was not so widespread. As a result, technological developments in recent years, such as the convergence of OT and IT and the usage of Industrial Internet of Things (IIoT) devices, have made critical infrastructure systems more vulnerable.
- After the Covid-19 pandemic, remote working solutions became popular, allowing remote access to industrial control systems (ICS) and IT/OT infrastructure assets.
- Most OT networks rely on unsecured networks that don’t use proper security controls and operate on legacy systems vulnerable to cybersecurity threats.
One example that summarizes critical infrastructure’s weak points against the cyberattacks occurred in Florida. In 2021, a water treatment plant in Oldsmar, Florida, was attacked. The facility was running Windows 7, which Microsoft discontinued support for in 2020. Threat actors exploited system security vulnerabilities, including the outdated operating system, and gained unauthorized access by abusing remote desktop-sharing software.
Notable Cyber Attacks Against the Critical Infrastructure Industries
Stuxnet is the most well-known cyberattack against critical infrastructure. The Stuxnet virus was used to attack the supervisory control and data acquisition (SCADA) systems at Iran’s uranium enrichment facilities in 2010. The system was closed network, and a USB memory stick delivered the malware.
The Stuxnet attack demonstrated that critical infrastructures could be the subject of cyberattacks which can cause physical damage. It also showed that an internet connection is not required to carry out a cyberattack. It is the most visible illustration of how minor vulnerabilities in a system can cause significant harm, and it has inspired cybercriminals to exploit vulnerabilities in critical infrastructure systems.
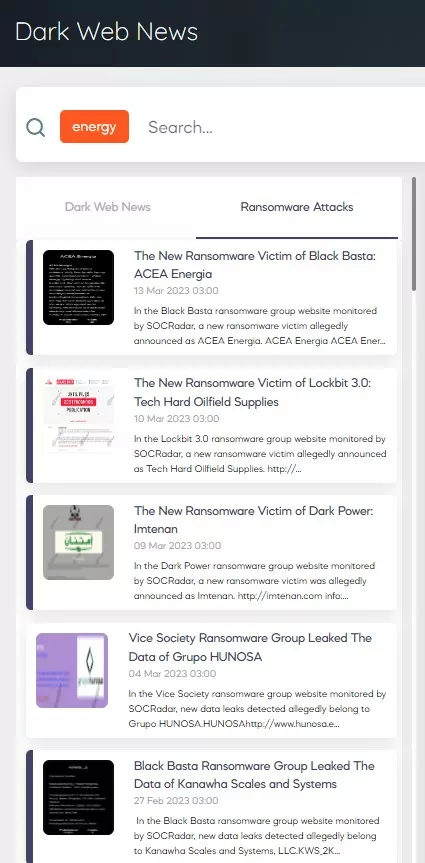
The attack on the Ukrainian power grid in December 2015 was one of the most damaging critical infrastructure attacks so far. The ‘BlackEnergy‘ malware was used in the attack attributed to Russian state-sponsored threat actors. In this attack, a combination of phishing email and malware, the attackers used the hard drive killer KillDisk, spear phishing, credential theft, VPNs, and remote access vulnerabilities, causing widespread power outages. The Ukrainian power grid was the subject of another attack in December 2016 using the ‘Industroyer’ malware, which is likely to have been carried out by the same attackers.
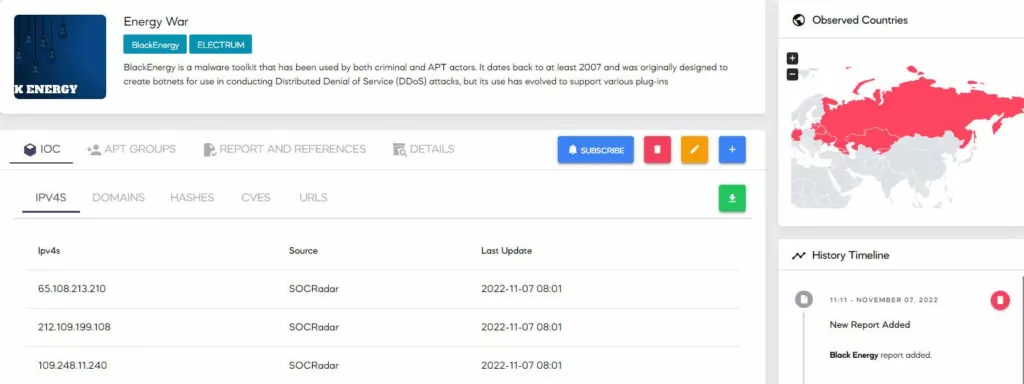
One of the first known attacks on the security systems of an industrial control system took place in December 2017. In this attack, believed to be nation-state sponsored, the Triton malware targeted the Safety Instrumented System, which is tasked with detecting and responding to operational hazards of a petrochemical plant in Saudi Arabia. The attack was detected without any casualties; however, it disrupted the operations of the petrochemical plant. The attack highlighted the necessity to protect security systems, whose duty is to ‘protect’ against cyber attacks.
In May 2021, one of the most devastating recent cyberattacks on critical infrastructures occurred in the U.S. The Colonial Pipeline, operated by the Colonial Pipeline Company and delivers more than 45% of the East Coast’s gas, diesel, and jet fuel, was the victim of a ransomware attack. Because it was unclear which systems had been compromised, the corporation was forced to shut down whole networks and operations. The company restored system function; however, gasoline was unavailable in some gas stations following the attack. The U.S. average gas price per gallon increased to the highest level in six years. The Colonial Pipeline incident revealed once again how profitable it is for attackers to target critical infrastructure systems.
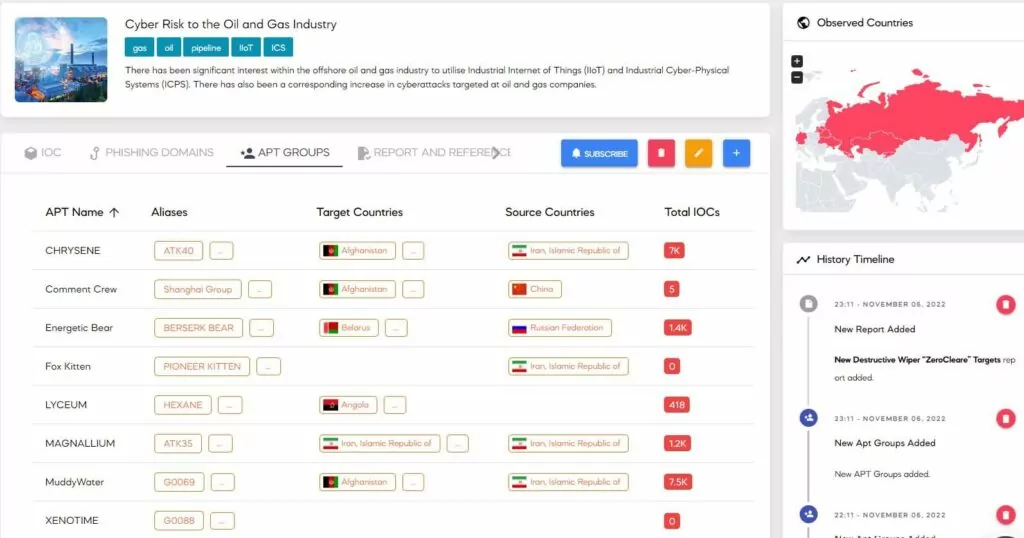
Cyberattacks targeted several critical infrastructure systems during Russia’s invasion of Ukraine, which continued for over a year since February 2022. This invasion has demonstrated once again that critical infrastructure systems are primarily targeted for military purposes, and deploying cyberattacks to eliminate these targets is less expensive and less risky in terms of personnel and equipment loss.
Meanwhile, cyberattacks on critical infrastructure industries like healthcare, finance, and government organizations are rising. According to the FBI’s 2022 Internet Crime Report, based on data from the Internet Crime Complaint Center (IC3), IC3 received complaints from 870 critical infrastructure organizations that they were being attacked by ransomware. Ransomware has affected at least one member of 14 of the 16 critical infrastructure industries.
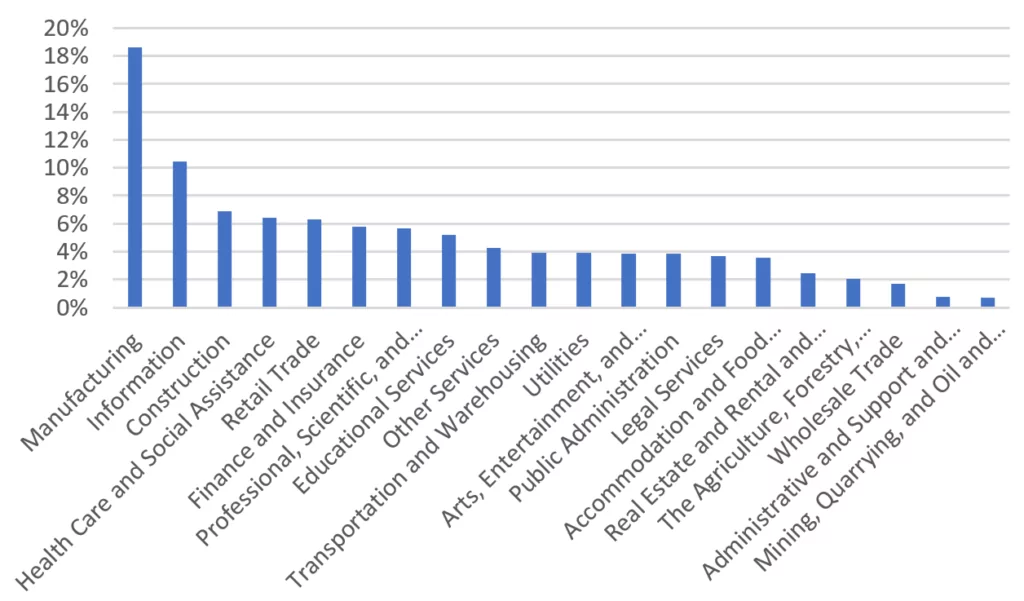
SOCRadar dark web analysts detected 2596 ransomware attacks in 2022. The distribution of these attacks by industry is shown below. Since education and retail are sub-industry of government and commercial facilities, respectively, it is worth mentioning that 8 of the top 10 most attacked industries are the critical infrastructure industry.
How to Defend Critical Infrastructures?
Several attacks on critical infrastructure firms have shown that threat actors exploit critical infrastructure vulnerabilities to launch sophisticated attacks. Unpatched vulnerabilities are among the most common targets for cyber attacks. In this context, through its announced RVWP, CISA aims to identify vulnerabilities commonly associated with known ransomware use and alert critical infrastructure assets of these vulnerabilities and mitigate them before a ransomware event occurs.
Organizations responsible for critical infrastructure must proactively recognize, assess, and respond to risks and vulnerabilities. Inventorying, monitoring critical infrastructure assets, and identifying vulnerabilities against all cyberattacks in the critical infrastructure industry accelerates cleanup and patch management, helping companies to increase their defenses against possible cyber attacks.
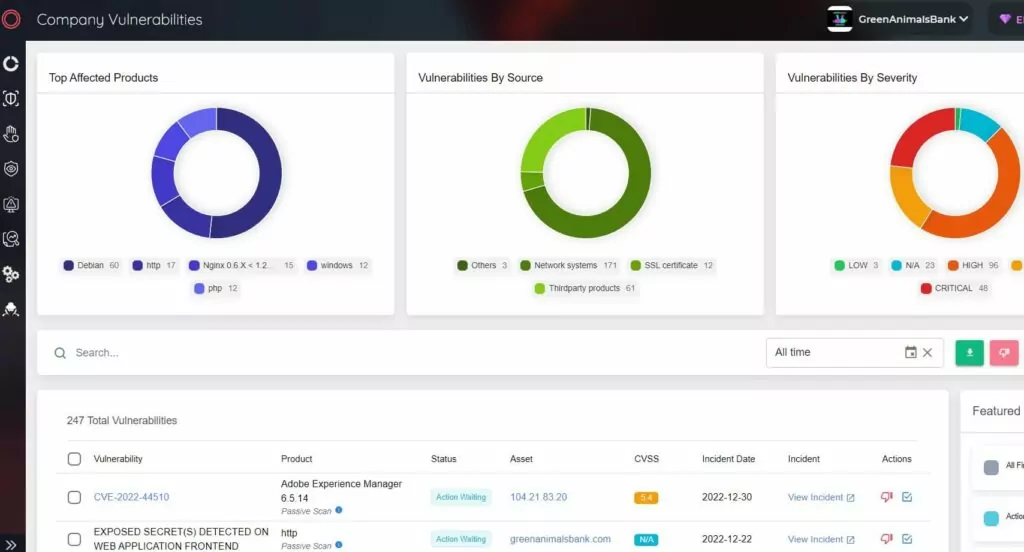
SOCRadar Extended Threat Intelligence provides an Attack Surface Management (ASM) solution for continuous discovery, inventory, classification, and prioritization with real-time monitoring to help gain comprehensive visibility into external-facing digital assets. Security experts can keep track of the vulnerabilities in the network using the SOCRadar XTI ASM solution. Understanding which vulnerabilities exist in critical infrastructure industry organizations can help minimize the attack surface threat actors may exploit.



































