
Patch Released for CVE-2023-25194 RCE Vulnerability in Apache Kafka
Patch Released for CVE-2023-25194 RCE Vulnerability in Apache Kafka The most recent patch for Apache Kafka fixes an unsafe Java deserialization vulnerability. The vulnerability, tr...
Cybercriminals Seek to Turn Humanitarian Crisis Into Opportunity
Cybercriminals Seek to Turn Humanitarian Crisis Into Opportunity On Monday, February 6, 2023, Turkey and Syria woke up to the morning of a major natural disaster. Two devastating earthquakes, 7.7...

Malware Analysis: LummaC2 Stealer
Malware Analysis: LummaC2 Stealer By SOCRadar Research [Update] November 22, 2023: Read under title: “LummaC2 v4.0 Features Anti-Sandbox Technique Employing Trigonometry and Google Cookie Revival.” [U...

Why Ransomware Groups Switch to Rust Programming Language?
Why Ransomware Groups Switch to Rust Programming Language? By SOCRadar Research The Rust programming language, which was released in 2015, became popular in a short time. Continuing to increase in pop...

Decryptors Available for the ESXiArgs Incidents and Cl0p Ransomware Va...
Decryptors Available for the ESXiArgs Incidents and Cl0p Ransomware Variants Researchers have developed decryptors for some recent ransomware operations. The specific ransomware operations u...

Major Cyberattacks in Review: January 2023
Major Cyberattacks in Review: January 2023 Cybersecurity is a constantly changing concern because threats always evolve and adapt to new technology and trends. The first month of 2023 has seen numerou...

Microsoft Exchange Server Vulnerability Trend in 2022
Microsoft Exchange Server Vulnerability Trend in 2022 By SOCRadar Research Microsoft Exchange Server, a widely used email and calendar server for businesses, holds critical information vital to an org...

The Week in Dark Web – February 5, 2023 – Access Sales and Data Leaks...
The Week in Dark Web – February 5, 2023 – Access Sales and Data Leaks Powered by DarkMirror™ Threat actors can weaponize even the smallest scraps of information in large-scale attacks. This is why dar...

ESXiArgs Ransomware Attack Targets VMware Servers Worldwide
ESXiArgs Ransomware Attack Targets VMware Servers Worldwide [February 9, 2023] Update: Ransomware is updated to prevent recovery solutions. Added the subheading “New Version of ESXiArgs Ransomware Pre...

Lessons Learned from Education Industry Attacks in 2022
Lessons Learned from Education Industry Attacks in 2022 By SOCRadar Research The education industry covers a diverse range of organizations, including K-12 education, higher education, private and pub...

1,200 Redis Servers Infected by New HeadCrab Malware for Cryptomining ...
1,200 Redis Servers Infected by New HeadCrab Malware for Cryptomining Operations A new malware has appeared on the frontlines, targeting online Redis servers. The malware, named HeadCrab by researcher...

How Can Extended Threat Intelligence Help CISO's First 100 Days?
How Can Extended Threat Intelligence Help CISO’s First 100 Days? When the expression “first 100 days” is mentioned, we all immediately think of what a leading politician has done fro...
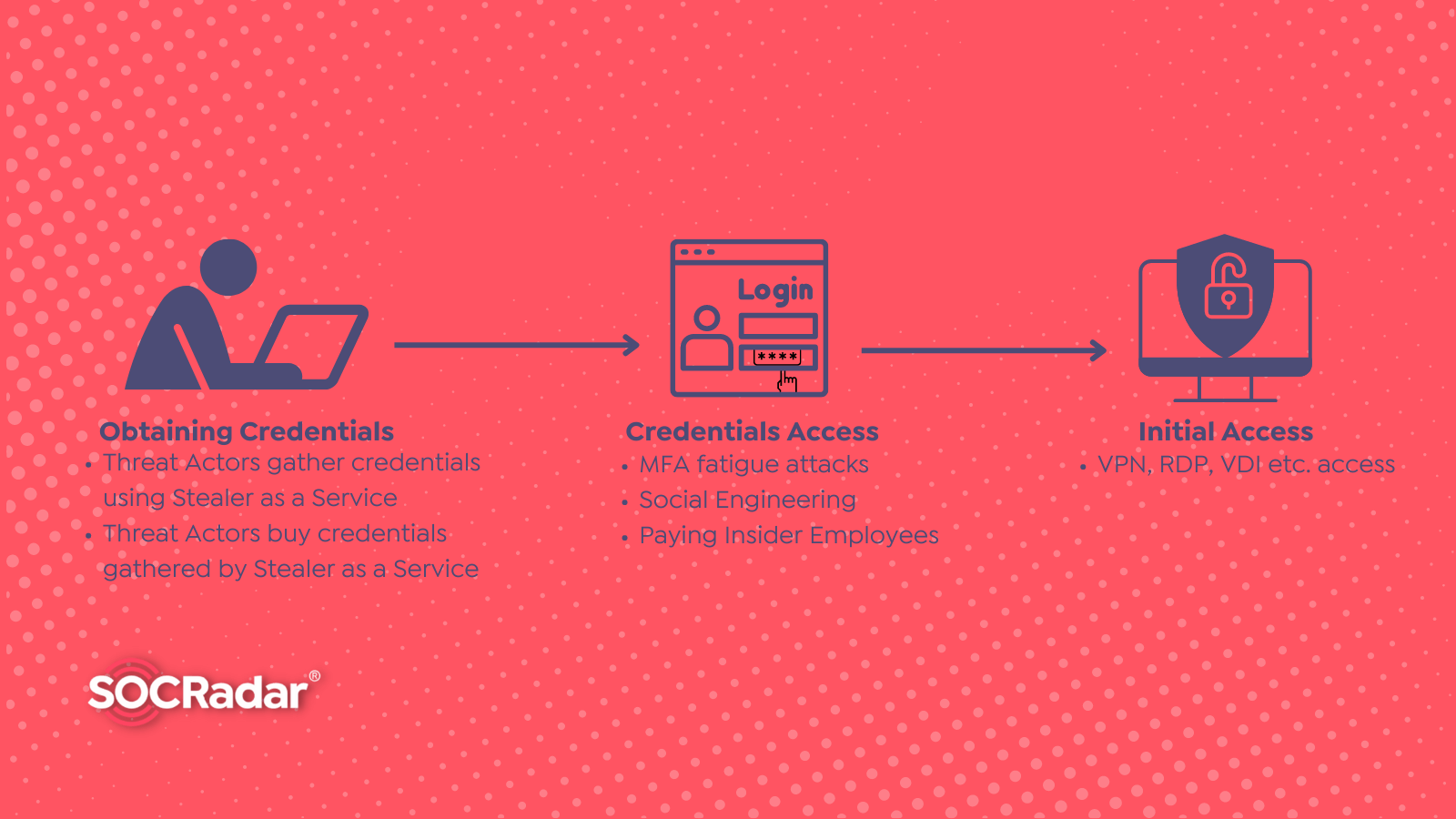
What is Stealer as a Service?
What is Stealer as a Service? By SOCRadar Research Stealer as a service is a marketing approach in which threat actors offer to sell or lease access to information-stealer tools designed to steal...

134M Exploit Attempts: Realtek RCE Vulnerability Targeted in Large-Sca...
134M Exploit Attempts: Realtek RCE Vulnerability Targeted in Large-Scale Attacks Threat actors stepped up their efforts to exploit a remote code execution vulnerability in the Realtek Jungle SDK&...

SOCRadar's End of Year Report: Phishing Threats in 2022
SOCRadar’s End of Year Report: Phishing Threats in 2022 The year 2022 was challenging for global cybersecurity, with waves of cyberattacks during Russia’s invasion of Ukraine setting the t...

The Week in Dark Web – 30 January 2023 – KillNet Targets Germany!
The Week in Dark Web – 30 January 2023 – KillNet Targets Germany! Powered by DarkMirror™ Former DDoS provider, nowadays a pro-Russian threat actor KillNet continues targeting western organizations. Si...

Yandex Code Repositories Leaked Allegedly by Former Employee
Yandex Code Repositories Leaked Allegedly by Former Employee Yandex, a Russian technology company and popular search engine, has had its source code repositories leaked on a hacker forum. Ac...

Malicious Actors in Dark Web: December 2022 Ransomware Landscape
Malicious Actors in Dark Web: December 2022 Ransomware Landscape Ransomware is one of the more common cyberattack types in the news. Behind the scenes of ransomware, there are numerous threat actors, ...

CTI4SOC: Ultimate Solution to SOC Analyst's Biggest Challenges
CTI4SOC: Ultimate Solution to SOC Analyst’s Biggest Challenges Today’s SOC analyst has a lot to deal with. All kinds of challenges await these cybersecurity professionals, who undertake t...

Dark Web Profile: Hive Ransomware Group
Dark Web Profile: Hive Ransomware Group by SOCRadar Research [Update] November 14, 2023: See the subheading: “New Era of Hive Ransomware Under Hunters International.” On November 8, 2021 electronics r...



































