
The Story of Lockbit Ransomware
The Story of Lockbit Ransomware After penetrating the network, the attackers take several steps to ensure that the Ransomware attack is successful. They want to infect as many systems as possible, sto...

The Week in Dark Web - 30 July 2021 - LockBit Strikes Again
The Week in Dark Web – 30 July 2021 – LockBit Strikes Again Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. admin access sale, company databa...

How to Monitor Your SSL Certificates Expiration Easily and Why
How to Monitor Your SSL Certificates Expiration Easily and Why SSL is a secure socket layer certificate, a small data file that establishes a secure connection between a web page and a browser. HTTPS ...

The Week in Dark Web - 23 July 2021 - Ransomware to Data Theft
The Week in Dark Web – 23 July 2021 – Ransomware to Data Theft Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. admin access sale, company dat...

The Most Dangerous of Their Kind Remote Code Execution (RCE) Attacks
The Most Dangerous of Their Kind Remote Code Execution (RCE) Attacks Remote Code Execution (RCE) is a class of software vulnerabilities. An RCE vulnerability allows a malicious actor to execute code o...

The Week in Dark Web - 16 July 2021 - Incidents from the MENA Region a...
The Week in Dark Web – 16 July 2021 – Incidents from the MENA Region and Mexico Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. admin access ...

An overview of Verizon’s 2021 Data Breach Investigation Report: An Ove...
An overview of Verizon’s 2021 Data Breach Investigation Report: An Overall Summary for Industries, Incident Classification Patterns and SMBs. For adapting to the changing Cyber Threat World, you need ...

The Week in Dark Web - 9 July 2021 - Access and Database
The Week in Dark Web – 9 July 2021 – Access and Database Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. admin access sale, company database ...

The What, Where & When for Effective Dark Web Threat Hunting
The What, Where & When for Effective Dark Web Threat Hunting Many companies worldwide have implemented dark web monitoring tools to detect emerging cyber risks proactively. However, hunting threa...

How to Detect Your Network is Used by Botnets Without Touching Your Sy...
How to Detect Your Network is Used by Botnets Without Touching Your Systems? Malicious bots called “bad bots” not only evolve continually, but are very specific to certain applications, su...

The Week in Dark Web - 25 June 2021 - Threat Actor Syndicate
The Week in Dark Web – 25 June 2021 – Threat Actor Syndicate Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. admin access sale, company datab...

Best OSINT Resources to Follow
Best OSINT Resources to Follow One of the benefits of the cyber security is its openness to sharing. There is a good sense of community in the industry with people freely creating and sharing tools. I...
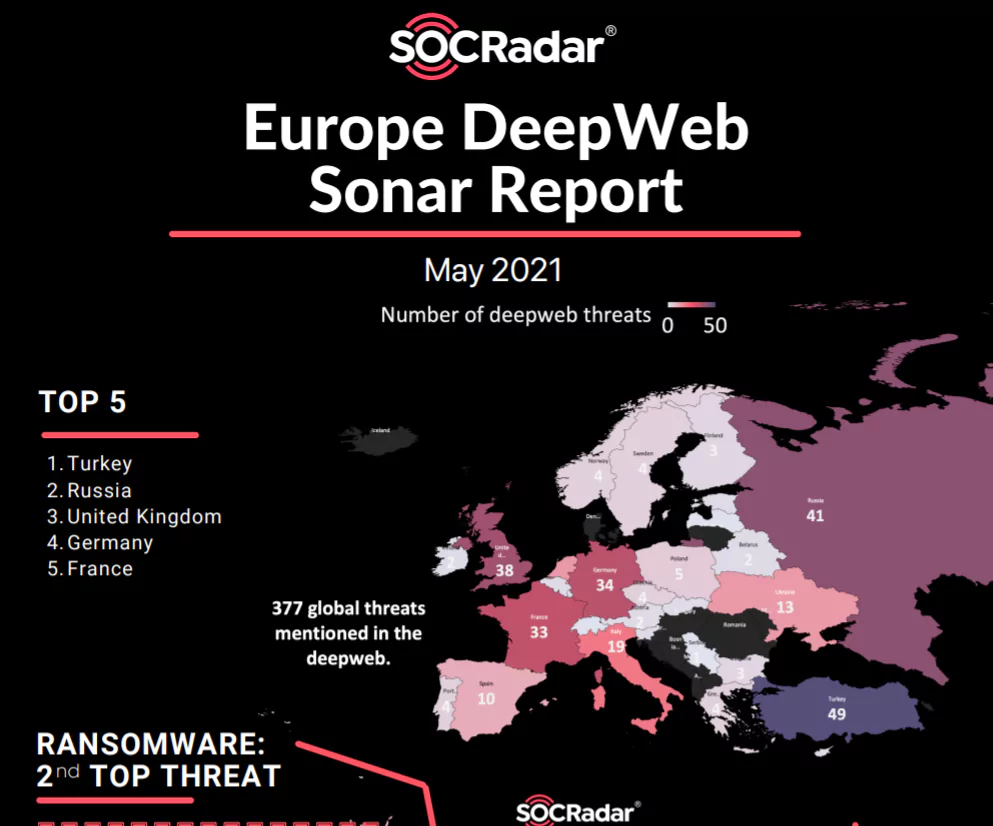
Comparing MEA (Middle East and Africa) and Europe against the Dark Web...
Comparing MEA (Middle East and Africa) and Europe against the Dark Web Threats Companies that wish to safeguard customers and employees typically invest in Dark Web monitoring solutions to warn them i...

The Week in Dark Web - 18 June 2021 - Hackers Gonna Hack
The Week in Dark Web – 18 June 2021 – Hackers Gonna Hack Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. admin access sale, company database ...
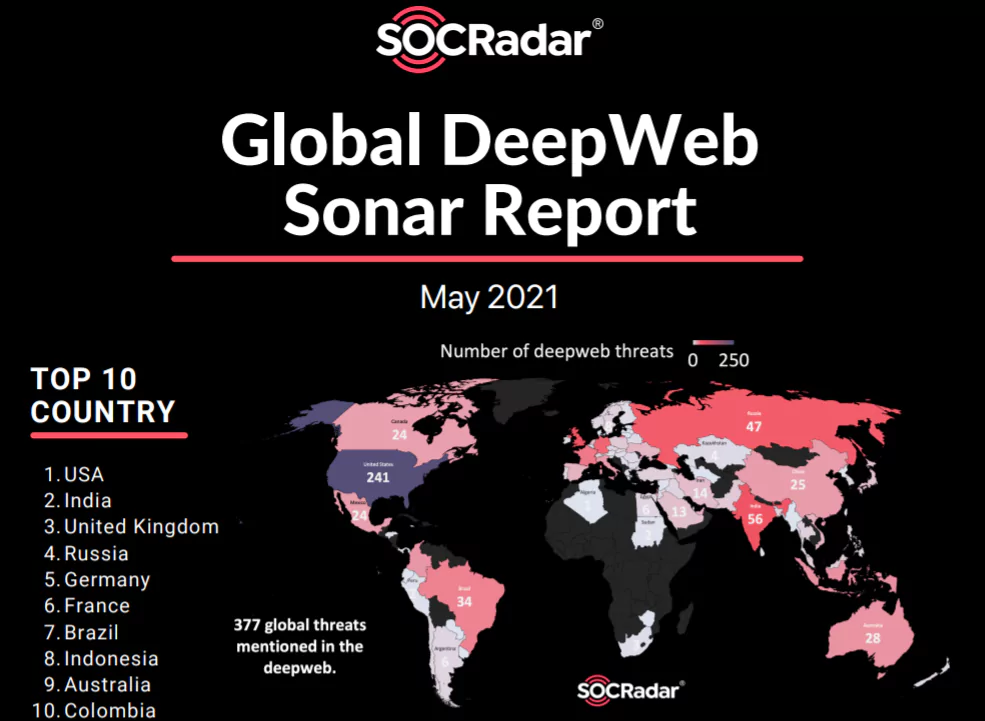
Did You Try SOCRadar Global DeepWeb Sonar Report Yet?
Did You Try SOCRadar Global DeepWeb Sonar Report Yet? Unidentified attackers have apparently unlimited resources, pressuring security authorities to regularly evaluate all aspects of their security st...

The Week in Dark Web - 11 June 2021 - Deep Web Havoc
The Week in Dark Web – 11 June 2021 – Deep Web Havoc Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. admin access sale, company database thef...

Best Practices for External Attack Surface Management (ASM) with Use-C...
Best Practices for External Attack Surface Management (ASM) with Use-Cases Gartner has predicted that by 2021, one-third of successful attacks on the enterprise will be through shadow IT resources and...

The Week in Dark Web - 4 June 2021 - Down the Deep Web
The Week in Dark Web – 4 June 2021 – Down the Deep Web Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. admin access sale, company database th...

Disrupt Attacker Infrastructure to Prevent Future Attacks with Takedow...
Disrupt Attacker Infrastructure to Prevent Future Attacks with Takedown Service Malware and phishing sites harm companies and organizations all over the world. Through removing sites and blocking atta...

The Week in Dark Web - 21 May 2021 - Hacking Worldwide
The Week in Dark Web – 21 May 2021 – Hacking Worldwide Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. admin access sale, company database th...
































