
Microsoft Exchange Server Vulnerability Trend in 2022
Microsoft Exchange Server Vulnerability Trend in 2022 By SOCRadar Research Microsoft Exchange Server, a widely used email and calendar server for businesses, holds critical information vital to an org...

ESXiArgs Ransomware Attack Targets VMware Servers Worldwide
ESXiArgs Ransomware Attack Targets VMware Servers Worldwide [February 9, 2023] Update: Ransomware is updated to prevent recovery solutions. Added the subheading “New Version of ESXiArgs Ransomware Pre...

Lessons Learned from Education Industry Attacks in 2022
Lessons Learned from Education Industry Attacks in 2022 By SOCRadar Research The education industry covers a diverse range of organizations, including K-12 education, higher education, private and pub...

How Can Extended Threat Intelligence Help CISO's First 100 Days?
How Can Extended Threat Intelligence Help CISO’s First 100 Days? When the expression “first 100 days” is mentioned, we all immediately think of what a leading politician has done fro...
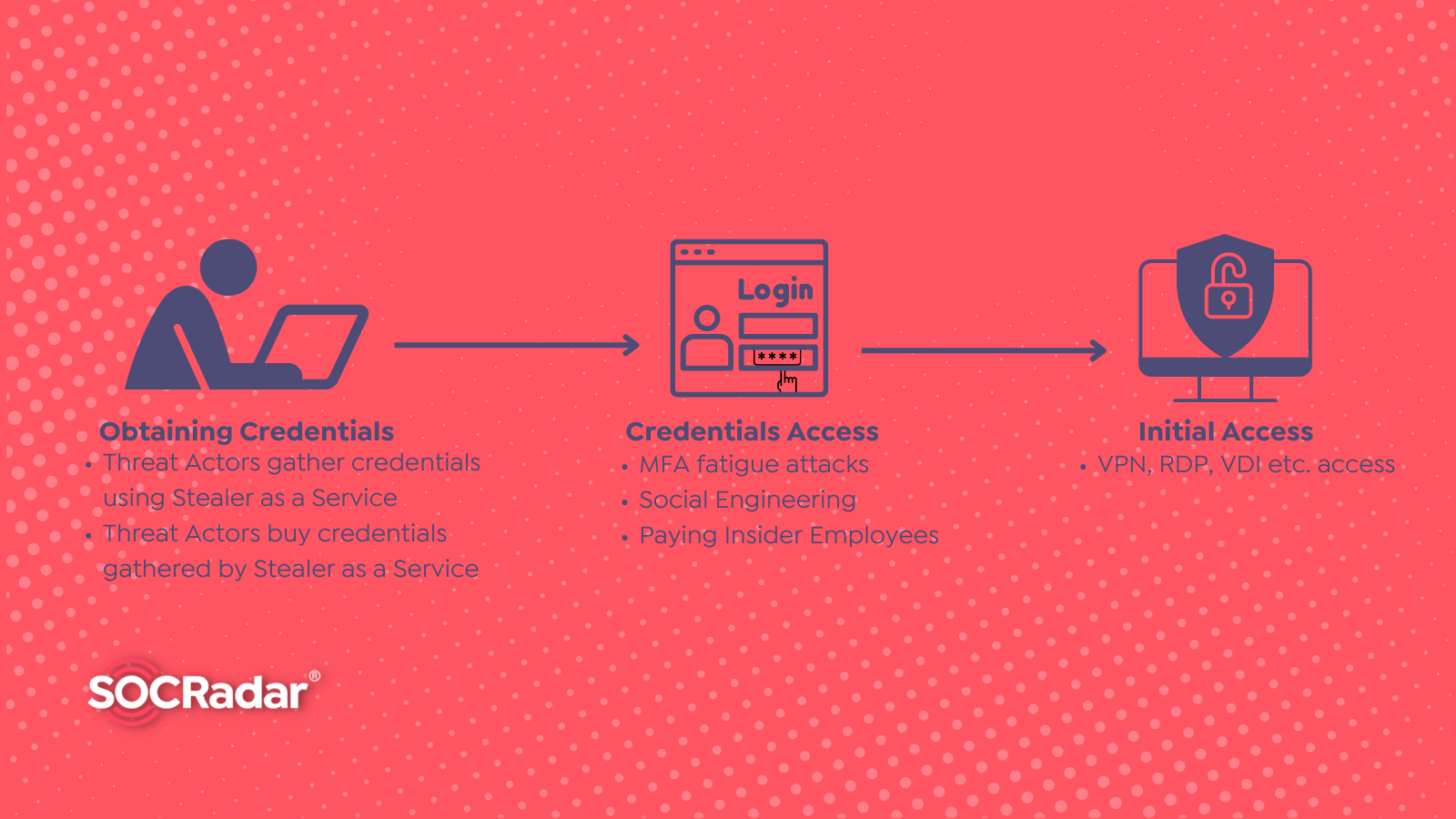
What is Stealer as a Service?
What is Stealer as a Service? By SOCRadar Research Stealer as a service is a marketing approach in which threat actors offer to sell or lease access to information-stealer tools designed to steal...

Malicious Actors in Dark Web: December 2022 Ransomware Landscape
Malicious Actors in Dark Web: December 2022 Ransomware Landscape Ransomware is one of the more common cyberattack types in the news. Behind the scenes of ransomware, there are numerous threat actors, ...

CTI4SOC: Ultimate Solution to SOC Analyst's Biggest Challenges
CTI4SOC: Ultimate Solution to SOC Analyst’s Biggest Challenges Today’s SOC analyst has a lot to deal with. All kinds of challenges await these cybersecurity professionals, who undertake t...

Introducing Radar Pages: Major Cyber Attacks
Introducing Radar Pages: Major Cyber Attacks Cybersecurity has grown in importance as a geopolitical factor. Cyberattacks target public and private systems each day, and the variety of attac...

From Zero to Adversary: APTs
From Zero to Adversary: APTs By SOCRadar Research From time to time, news hit the front pages regarding cyberattacks on significant infrastructures, such as nuclear facilities, or major companies, suc...

Hydra Aftermath and the Future of Dark Web Marketplaces
Hydra Aftermath and the Future of Dark Web Marketplaces By SOCRadar Research Russian-speaking Hydra Market was the biggest among darknet markets, with a $1B turnover in 2020. It was also the largest n...

SOCRadar Launches New CTI Solution for SOC Analysts
SOCRadar Launches New CTI Solution for SOC Analysts Introducing CTI4SOC, SOCRadar’s stand-alone threat intelligence to meet the needs of SOC analysts. With its comprehensive ...

4 Lessons Learned from Log4Shell
4 Lessons Learned from Log4Shell By SOCRadar Research Log4Shell vulnerability shook the cyber world to its core when it first became public in December 2021. It is a zero-day vulnerability d...

5 Lessons Learned from Ransomware Attacks in 2022
5 Lessons Learned from Ransomware Attacks in 2022 By SOCRadar Research In 2022, SOCRadar researchers detected over 1700 alleged ransomware victims. The total number was approximately 29% higher than i...

SOCRadar Free Dark Web Training: Learn How to Navigate in the Shadows
SOCRadar Free Dark Web Training: Learn How to Navigate in the Shadows The concept of the dark web plays a key role in today’s increasingly complex cybercrime ecosystem. Threat actors share the dataset...

5 Lessons Learned from Data Breaches in 2022
5 Lessons Learned from Data Breaches in 2022 By SOCRadar Research Online products and services are growing daily. Consumers are entrusting more personal information to online databases, and businesses...

Major Cyber Attacks in Review: December 2022
Major Cyber Attacks in Review: December 2022 In the last month, we have seen many cyber incidents, ranging from data breaches at retailers to various cyberattacks on cryptocurrency exchange platforms....

10 Questions to ChatGPT: How It Can Change Cybersecurity
10 Questions to ChatGPT: How It Can Change Cybersecurity This blog is written with the help of OpenAI’s ChatGPT. In November 2022, OpenAI -an Artificial Intelligence research and deployment company- ...

4 Lessons Learned from Supply Chain Attacks in 2022
4 Lessons Learned from Supply Chain Attacks in 2022 At the BlackBerry Security Summit in 2022, four-fifths of IT decision-makers said they had been notified of an attack or vulnerability in ...

Increasing Cyberattacks Targeting the Gaming Industry in 2022
Increasing Cyberattacks Targeting the Gaming Industry in 2022 By SOCRadar Research The gaming industry has recently emerged as a preferred target for cyberattacks. The industry is constantly growing, ...
An Analysis of Central Banks Hackings: Who is Next?
An Analysis of Central Banks Hackings: Who is Next? By SOCRadar Research Critical infrastructures are the basis for the functioning of the countries’ system, and they are essential to continue the cou...
































