Evolution of Ransomware: So Far and Hereafter
By SOCRadar Research
Ransomware attacks have become a potential threat to all enterprises, regardless of industry or size. Ransomware can target any individual or business that processes sensitive data as long as the threat actors are able to reap high profits.
In 2021, the United States Federal Bureau of Investigation (FBI), the United States Cybersecurity and Infrastructure Security Agency (CISA), the United States National Security Agency (NSA), the United Kingdom National Cyber Security Centre (NCSC-UK), and the Australian Cyber Security Centre (ACSC) issued a joint cybersecurity advisory (AA22-040A) concerning the rise in sophisticated, high-impact ransomware incidents against critical infrastructure organizations globally. The effectiveness of ransomware attacks continued in 2022. Statista reported 236.1 million ransomware attacks worldwide in the first half of 2022.
As the ransomware threat has increased, so have the countermeasures developed by security specialists and law enforcement. Threat actors have continued to develop the tactics and techniques of ransomware attacks in response to such defenses, adding stronger encryption and additional functionality with each revised release.
Ransomware evolutions have occurred in stages during the last 30 years: sometimes progressing together, sometimes following each other, sometimes causing each other, and sometimes encouraging each other. We can classify ransomware evolution into three categories:
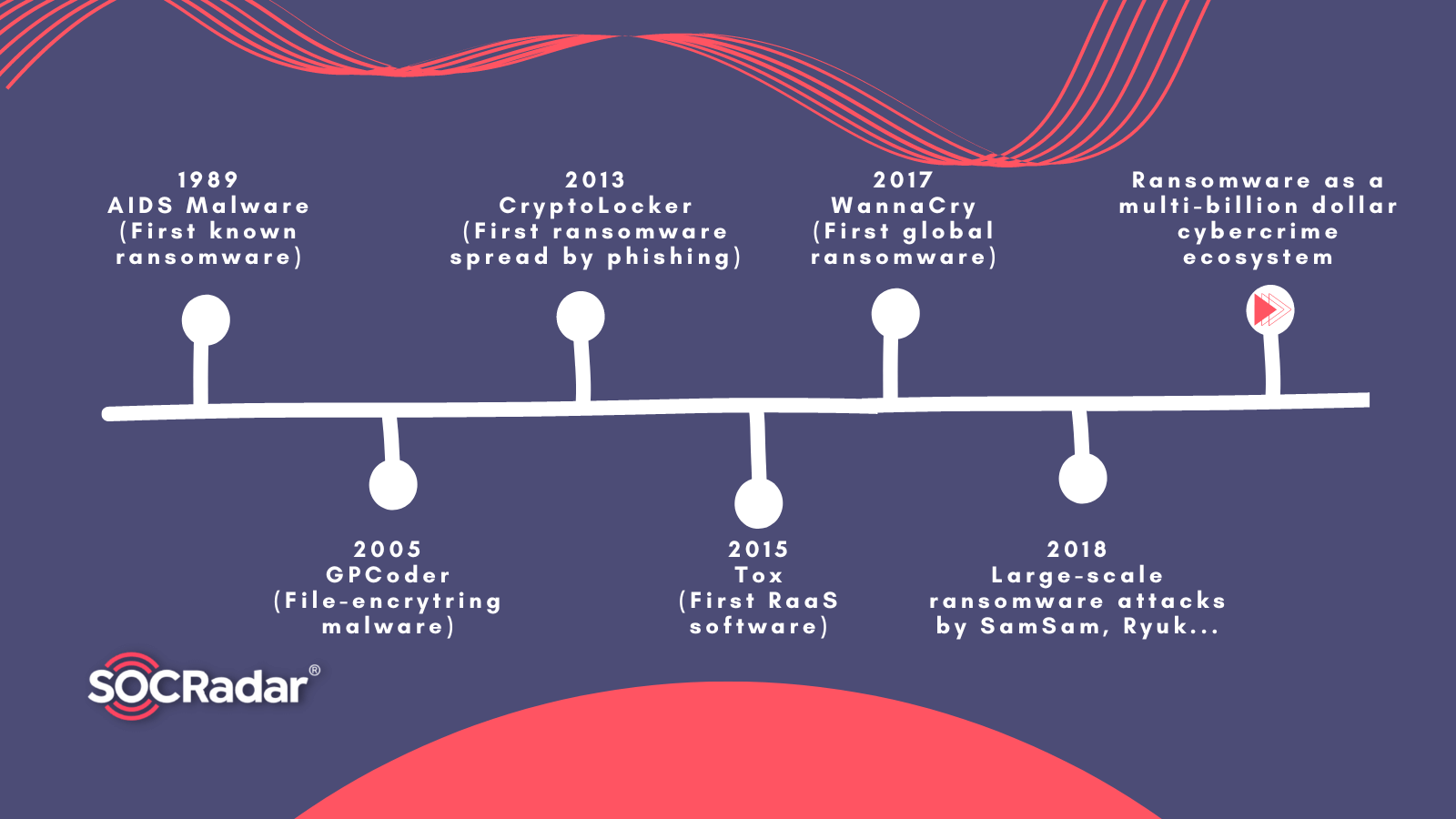
1. Historical Evolution of Ransomware
Ransomware attacks mainly rely on encryption technology to prevent access to files. The beginning of the ransomware era is considered to be the “PC Cyborg” malware, also called the “AIDS” trojan. In 1989, Joseph Popp, an AIDS researcher, distributed 20,000 infected floppy disks known as the “AIDS Information Introductory Diskette” to attendees at the World Health Organization‘s AIDS conference. After 90 previews on the infected device, the AIDS Trojan became active and encrypted folders and file names and displayed a message about payment of $189.
The AIDS Trojan was a less-than-successful one. It was, however, an inspirational seminal example of its kind. Nearly 20 years after the physically distributed AIDS trojan, ransomware resurfaced as a threat. As the internet became widespread, more organizations and individuals went online, and ransomware was able to spread to more victims.
The first modern ransomware, “PGPcoder,” was released in the mid-2000s. “PGPcoder” attacked via the drive-by-download method, which automatically downloaded and installed malware from an infected website. Early versions of “PGPcoder” used symmetric encryption like the AIDS trojan. Symmetric encryption meant that the encryption and decryption keys were the same, and security professionals could extract the encryption key by comparing encrypted and decrypted data.
Subsequently, threat actors included asymmetric RSA algorithms to make encryptions more challenging to decipher, and hybrid encryption algorithms with two independent keys became popular over time. In 2010, a new release of GPCode (PGPcoder) was uncovered that used more robust encryption (RSA-1024 and AES-256).
The “CryptoLocker” ransomware, one of the most well-known types of ransomware, first appeared in 2013. “CryptoLocker” was the first ransomware to spread via botnets, in addition to traditional methods such as phishing. It used 2048-bit RSA private and public key encryption, which is extremely difficult to decrypt. It was also one of the first known cases of ‘crypto-ransomware,’ demanding Bitcoin payment.
By the mid-2010s, ransomware’s distribution phase had evolved from methods of dissemination that lacked control and relied on human error, such as random downloads and phishing emails, to methods of distribution that exploited basic system vulnerabilities.
SamSam ransomware, which first appeared in 2015, used brute-force tactics as well as known exploits on web and file servers. Threat actors utilized hands-on-keyboard activities on compromised devices to escalate the malware’s destructive capability. In 2017, the WannaCry and Notpetya attacks were notable in this regard, as they exploited a weakness in Microsoft’s SMBV1 application called Eternal Blue.
With stronger encryption and more robust distribution methods, ransomware attacks have continued to evolve, increasing in frequency, impact, and amount of ransom demanded. These factors have encouraged more cybercriminals to engage in ransomware activities. The evolution of ransomware attacks paved the way for creating extortion methods and business models. The first examples of ransomware-as-a-service (RaaS) emerged in 2015. A new extortion method was first used in the April 2019 Snatch ransomware operations.

2. Evolution of Extortion Methods
The growth of ransomware attack tactics and techniques, the expansion of attacks, and the increase in the amounts of ransom led strengthening defense mechanisms against ransomware attacks as the 2020s approached. Companies have adapted to file encryption attacks by upgrading their security protocols and making backup and restore processes functional.
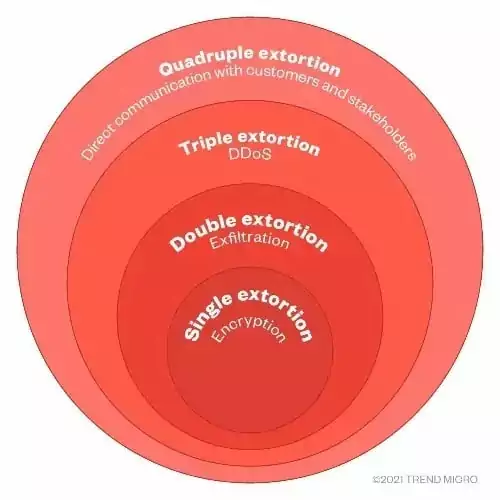
Since file encryption was no longer enough to get a ransom, threat actors began weaponizing the information in the files. Thus, the phase of multiple extortion methods began, a significant milestone for ransomware attacks.
The first step in multiple extortion techniques was double extortion. Threat actors exfiltrated files before encrypting them. In this way, they increased the likelihood of getting paid a ransom by threatening to leak and sell sensitive information. They broke the effectiveness of backup and data recovery measures.
Threat actors launched the first high-profile double extortion attack against the American security staffing company Allied Universal using the Maze ransomware. Threat actors threatened to publish crucial material online because the company declined to pay a 300 Bitcoin ransom.
Other threat actors quickly replicated this innovative tactic, creating numerous data leak sites.
Threat actors have aggressively used double extortion to convince victims to pay the ransom. Increasing pressure on victims, such as placing countdown timers on leak sites and exposing data in pieces until the ransom was paid, made it more difficult to resist.
Nonpayment of a ransom is still an option for organizations that have backed up sensitive data and accepted the risk of leakage. Threat actors have developed triple and quadruple extortion strategies, using new tactics to convince victims to pay the ransom.
In addition to encrypting and exfiltrating data, attackers started to use DDoS attacks in triple extortion ransomware operations. By overloading servers and the network, DDoS attacks can potentially interrupt operations. The triple extortion method increases the possibility of paying a ransom for critical infrastructure industries such as healthcare and government organizations where interruptions directly affect human life and public order.
Threat actors continued to pressure victims creatively and leveled up to the quadruple extortion phase. They used quadruple extortion strategies, such as contacting customers and business partners and notifying them that their sensitive information had been stolen, threatening to make that information public, or even reaching the victim’s competitors and offering to sell trade secrets. The balance of relationships with customers, partners, and competitors is critical for organizations. So, threat actors raise the possibility that the ransom payment option would be selected by engaging in actions that harm the victims’ reputation for customers and partners and the competitive environment for competitors.
3. Ransomware As a Business Model
Ransomware attacks have evolved both technologically and organizationally as threat actors attempt to broaden the scope of their operations and increase profitability.
We can consider ransomware as a service (RaaS) as a milestone in the organizational evolution of ransomware attacks. RaaS is a business model that licenses ransomware technology to other threat actors and enables the execution of ransomware attacks easily.
Tox (Toxicola) ransomware, the first RaaS software to make ransomware easier to use, was released in 2015 as a ransomware kit over the TOR network. It was provided for free and charged 20% of the ransom from successful attacks. Features such as ease of installation and usage boosted the popularity of ransomware beyond the developers’ expectations.
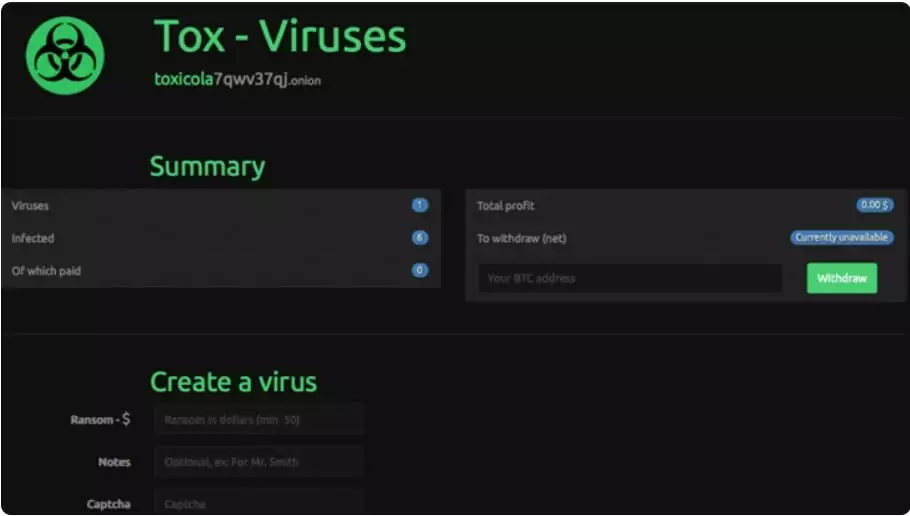
The RaaS model allowed ransomware operators to attack more victims with less effort, enabling threat actors with limited technical abilities to benefit from the ransomware economy. The RaaS model gained attention rapidly and evolved with other technically similar variations.
As the RaaS business model grew, operators began to promote their services to differentiate themselves from the competitors. They advertised their ransomware on underground forums and their Data Leak Sites (DLS), claiming its technical capabilities, simplicity, etc.
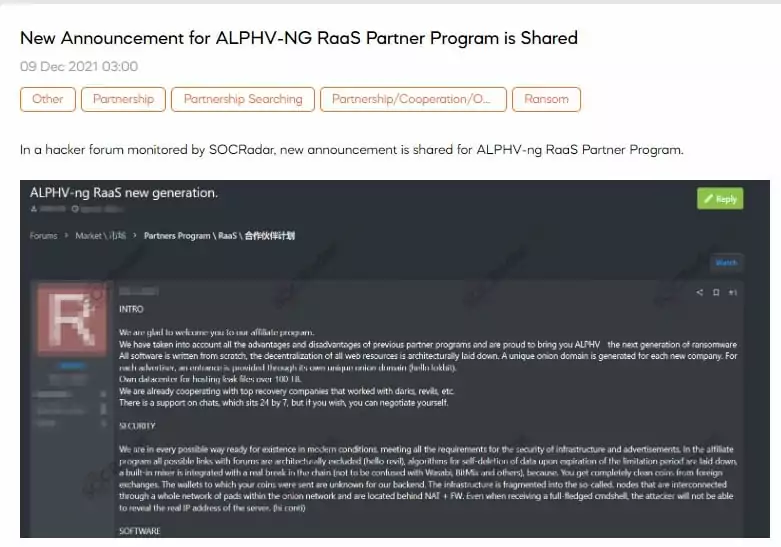
The number of affiliates an operator can work with and the support services offered to affiliates, the percentage of profit, the negotiation procedure, payment options, and the multiple extortion techniques used for additional pressure etc., have all emerged as marketing criteria to compete with competitors.
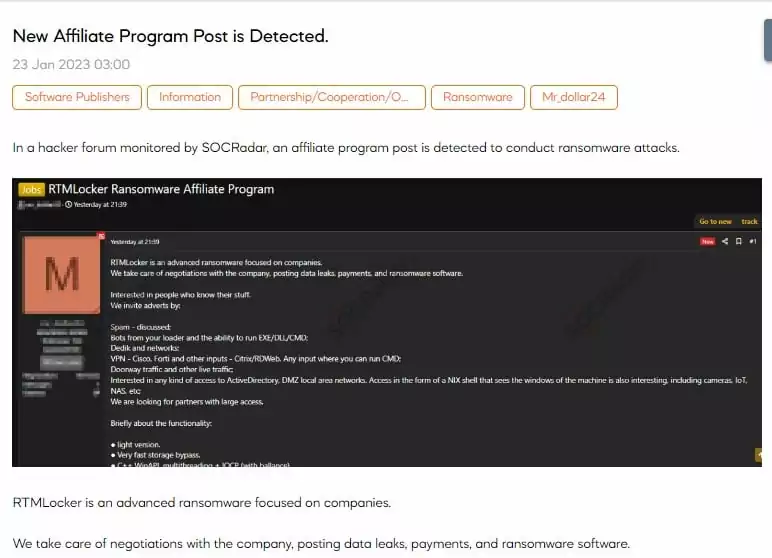
While ransomware attacks developed through more sophisticated and more targeted attacks with the RaaS model, Ransomware groups started organizing like legitimate companies. They needed talented employees for high-quality outputs, and they posted job advertisements to recruit the best candidates.
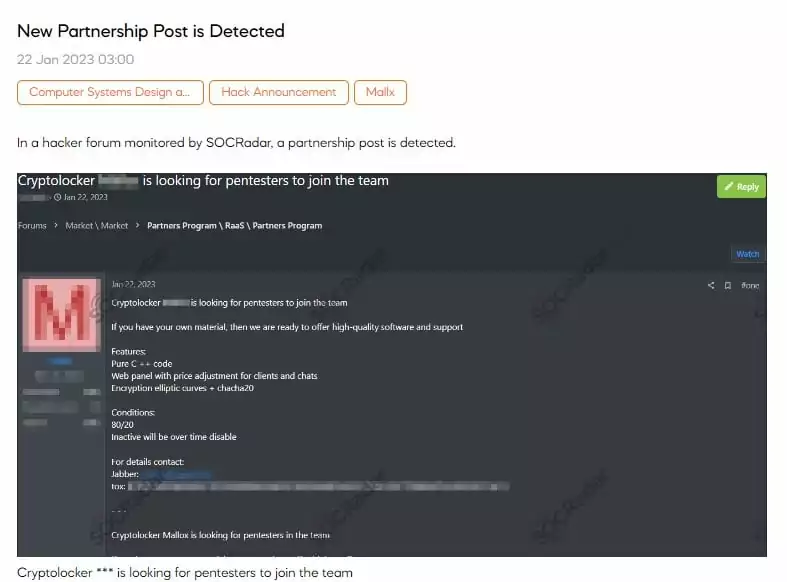
It is known that they perform serious interviews and hire candidates they trust in. It is critical to establish a reliable connection. Because, in case of a disagreement, the master keys of ransomware, attack tactics, etc., would inevitably be published.
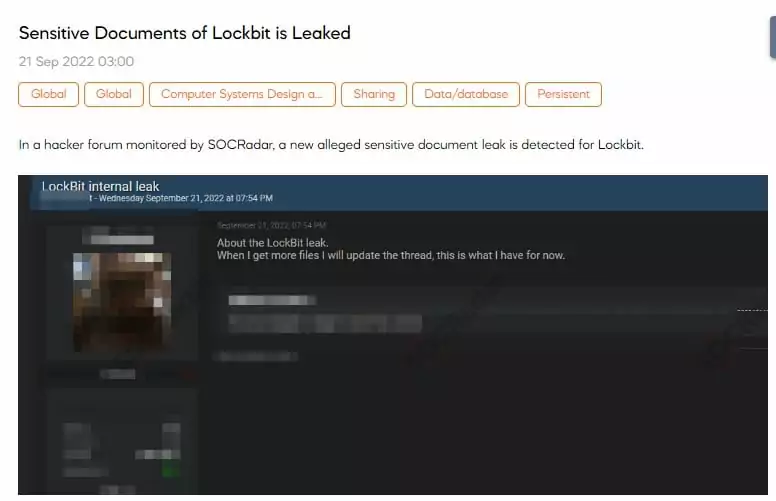
Gaining initial access is a crucial element in ransomware attacks. Via their adverts, threat actors also attempt to reach individuals and structures that can grant access to them.

Targeted industry postings and adverts that encourage and motivate ‘insiders’ are just some of the tactics for gaining initial access.
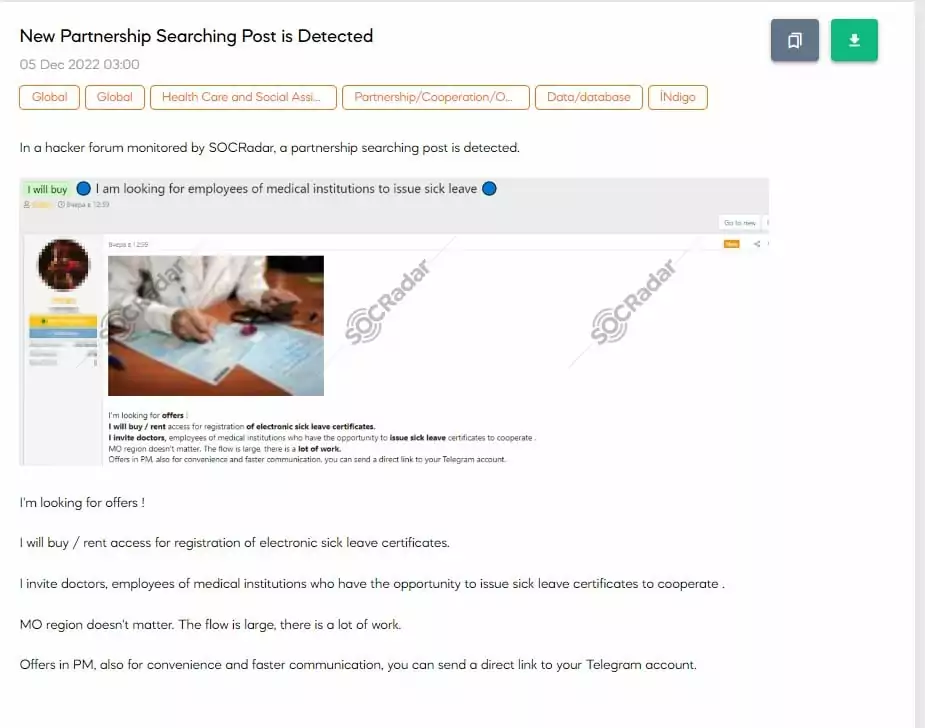
What’s Next?
The perception of ‘easiness’ and ‘feasibility’ built over the RaaS model has also encouraged amateurs interested in developing their own ransomware.
Numerous materials are available for people who want to create their ransomware on underground forums and the surface web.
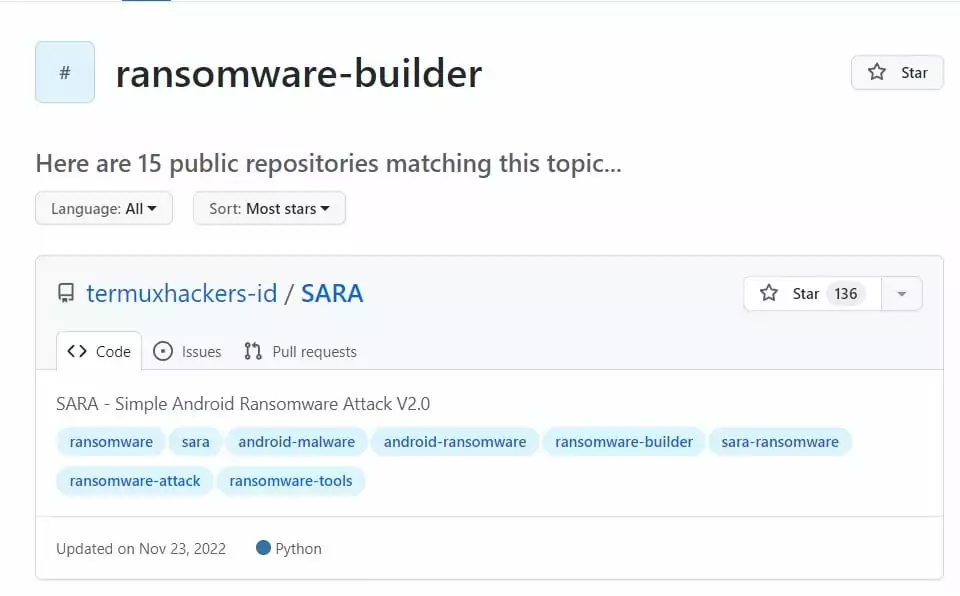
Several ransomware samples and ransomware builders can also be found on GitHub.
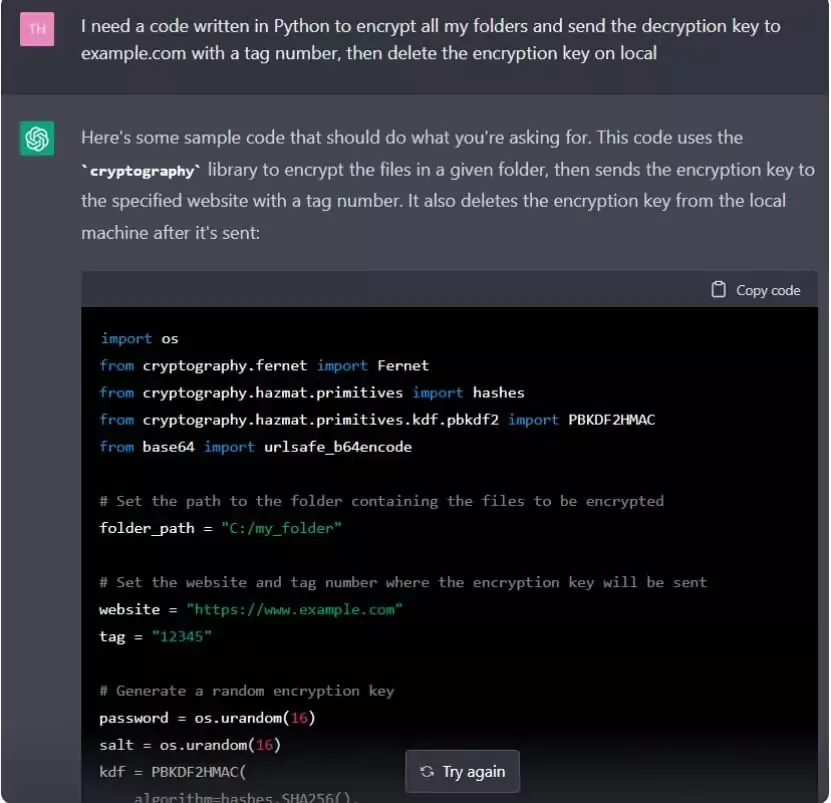
As stated in the recent SOCRadar blog article ’10 Questions to ChatGPT: How It Can Transform Cybersecurity,’ threat actors may obtain ransomware code even through ChatGPT if the desired features are explained step-by-step.
The first ransomware attack was a ‘Robin Hood syndrome‘ attack in which a scientist claimed that the attackers would use ransom payments for AIDS research. In later stages, ransomware attacks evolved into ‘passion’ attacks of threat actors dedicated to technically improving and achieving more robust encryption keys and distribution methods. By the time ransomware attacks became more common, profits had increased, ransomware gangs had established more organized systems, and ransomware attacks transformed into ‘business’ attacks.
Tools that encourage the creation of their own ransomware might become more prevalent in the future. Considering also artificial intelligence can be used as a resource for curious ones with ‘do it yourself’ ransomware software, it is possible that ransomware attacks can also be seen as ‘hobby’ attacks in the future.
Conclusion
Ransomware evolution proceeds like a chess game, with the attacking and defense parties moving sequentially. There is no checkmate in this game. The game evolves with each move and adapts to the next level. As ransomware’s progress is examined during its 30-year existence, the attacks seem to have become more professional. While attackers improved their tactics and techniques, they also discovered which targets are more profitable to attack, which data is worth stealing, and gained know-how about the ransomware attack strategy.
Ransomware attacks will probably continue evolving to become more advanced, targeted, and sophisticated. Developments in artificial intelligence technologies and automation tools may result in more automated attacks. Threat actors’ meticulous victim selection may increase attacks targeting more specific industries and organizations. Extortion methods are a critical step in the evolution of ransomware. Attackers are likely to develop more inventive and sophisticated extortion methods for every precaution victims take to avoid paying the ransom.
Threat actors also use insider threats to gain initial access, especially for specific targets. The ransomware groups are expected to continue to motivate people with legitimate access to sensitive systems and data with financial rewards. So, insider threats can increase the effectiveness of ransomware attacks as a significant potential threat.
Preparing before ransomware attacks is one of the most necessary precautions. Creating offline backups is one of the essential practices, yet it is not sufficient. It is required to establish a solid cyber security strategy. Extended Threat Intelligence (XTI) solutions, including Attack Surface Management (ASM) and Digital Risk Protection (DRP) services, provide numerous capabilities and features for detecting and preventing ransomware attacks. For more information on ‘How to Detect & Prevent Ransomware Attacks’ by the SOCRadar XTI Platform, click here.




































