
FIFA World Cup 2022 Qatar: Dark Web & Phishing Landscape Analysis
FIFA World Cup 2022 will be organized in Qatar from November 20 to December 18, 2022. Predictions show that 1.5 million people will travel to Qatar to watch the tournament, which national teams from 32 countries will attend. Such large international organizations are becoming more attractive to cyber attackers. People’s and the media’s interest in these organizations, the use of high-tech in such events, the digital activities of all the players, audience, visitors, fans, stakeholders, and people’s lack of awareness of cyber security all pave the way for cyber threat actors.
Past experiences show that large-scale sports organizations attract threat actors. Russian authorities announced during FIFA World Cup 2018 that they blocked 25 million cyber-attacks. At the 2018 PyeongChang Winter Olympics, the organization was targeted by 12 million cyber-attacks per day, totaling 600 million. Across the 2020 Tokyo Olympics and Paralympics, authorities prevented 450 million cyber-attacks on the official website and organizing committee systems. The number of attacks on Tokyo was particularly remarkable because the Olympics were played without an audience within the scope of the Covid-19 measures, so attacks like ticket sales fraud and stealing personal information were on the lowest level.
In addition to the large attacks that drew public attention, numerous fraud and scam attacks like phishing emails containing promotional or lottery offers, threat actors used fake FIFA ticket sales websites, fake live streaming or score/match schedule tracking links, and malware-embedded mobile applications in the previous FIFA events. Although these attacks, carried out specifically to collect personal data and have financial gain appear small-scale, they have a significant impact as they are both large and aimed at all fans worldwide.
As the FIFA World Cup 2022 Qatar is getting ready to kick off, the attackers have already started their operations. SOCRadar Extended Threat Intelligence platform has detected various intelligence from different sources, and SOCRadar researchers focused on profiling threat actors targeting this prestigious organization.
Dark Web Analysis on FIFA World Cup 2022 Qatar
SOCRadar Dark Web researchers have detected no threat directly targeting FIFA World Cup Qatar 2022 so far. Meanwhile, they found a post that could be a potential threat, as seen below;
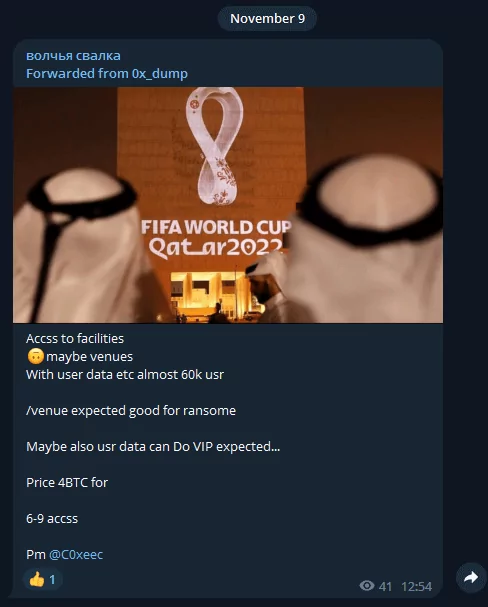
Threat actor claims to have data of 60 thousand users, which may give access to World Cup facilities. Such a sale valued at 4BTC for almost 60k users’ data on sale may indicate a critical threat.
SOCRadar Dark Web researchers discovered the following topics are mostly shared on underground forums and Telegram channels:
– FIFA World Cup 2022 ticket sales shares:
– FIFA World Cup 2022 referenced token, coin, and bet postings:
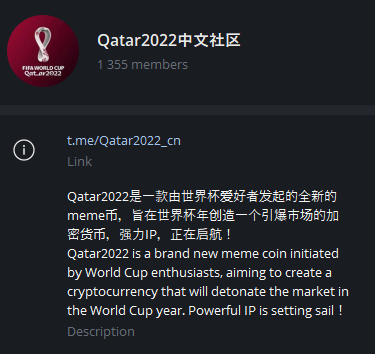

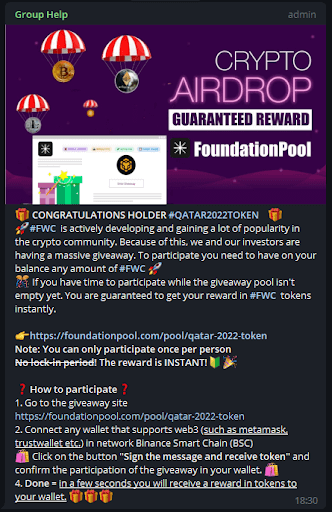
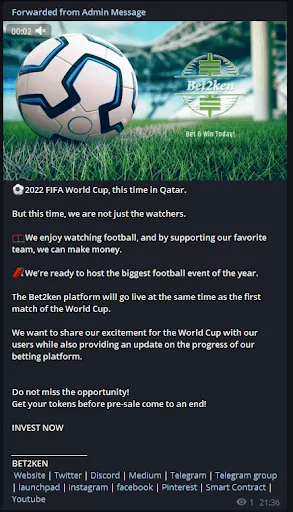
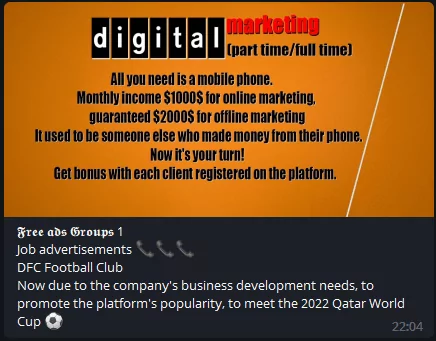
– FIFA World Cup 2022 referenced digital marketing job listings:
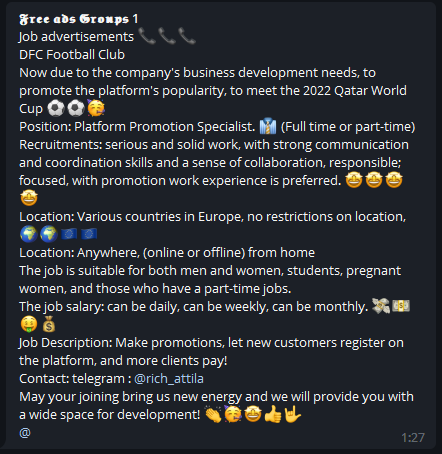
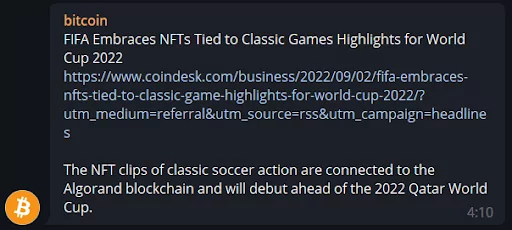
– FIFA World Cup 2022 referenced news citations:

Black Market Sales
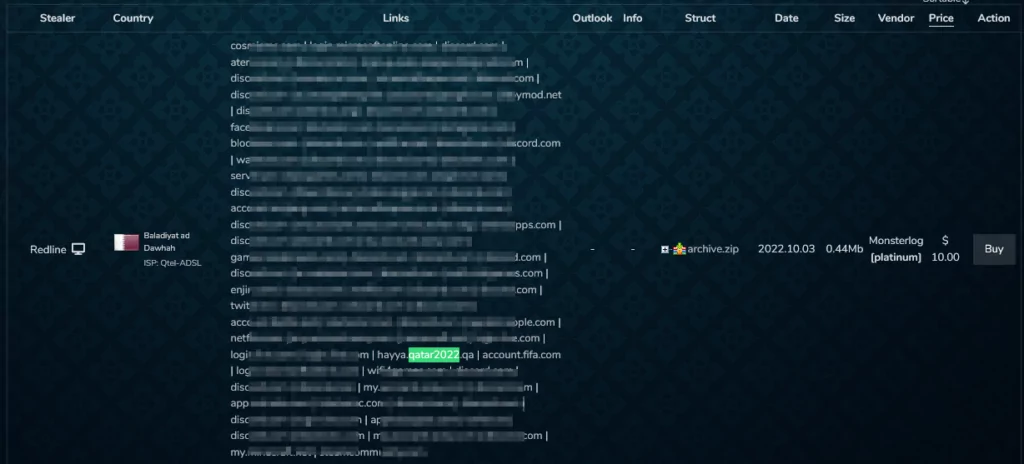
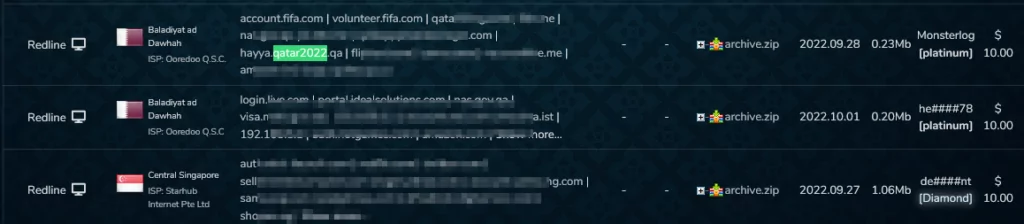
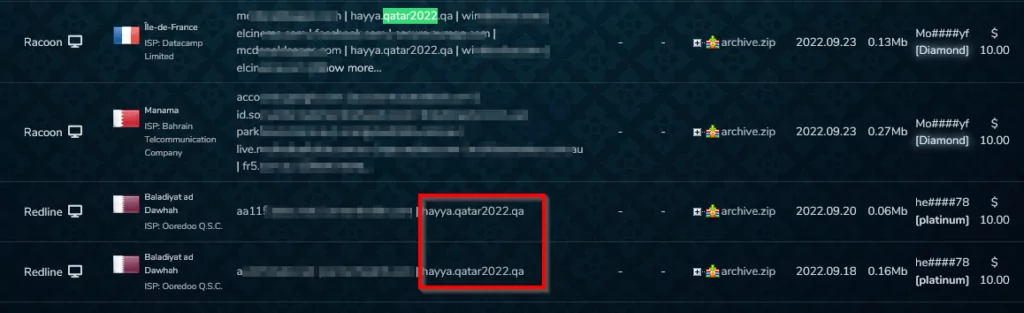
SOCRadar Dark Web researchers investigated sales announcements of the account details of the sub-domains related to the organization’s main domain, “qatar2022.qa,” in the Dark Web markets.
Dark web markets offer for sale stolen logs gathered from victims infected by info stealers. The victim data is sold in ” bots ” packages containing session cookies, IP addresses, browser fingerprinting, and victim account passwords. By acquiring these credentials, threat actors can access accounts and carry out harmful operations, including business email compromise (BEC), privilege escalation, and compromising the victim’s public online identity. Threat actors frequently utilize obtained account credentials to go beyond targeted organizations’ security and fraud protection tools. Each bot has different pricing depending on the number of account credentials, the type of account, and the victim’s location.
Researchers from the SOCRadar dark web team discovered 179 bots in the “Russian Market” and two bots in the “2easy shop” subdomains of the main domain “qatar2022.qa”.
Most of these bots are associated with the subdomain hayya.qatar2022.qa, which is used to sign up for the ‘Hayya Card’ system. The ‘Hayya Card’ is a mandatory Fan ID issued by organizers that serve as an entry permit to the state of Qatar, access to the stadium, and free subway and bus transportation. Hayya’s requirement for digital ID for all events increases the number of victims and broadens the attack surface.
Phishing Analysis
Phishing attacks are among the most common social engineering attacks, and threat actors widely use them in international sports organizations. In general, phishing attacks are quite damaging because society’s level of cyber security awareness is low. This damage increases exponentially in organizations with many enthusiastic fans, such as the FIFA World Cup. Social engineering attacks aim to gain personal or private information, access, and credentials using manipulation techniques by exploiting human error. There are plenty of types of social engineering attacks, but phishing and baiting techniques are used by threat actors more frequently.
Phishing attacks are designed to steal victims’ passwords, Personally Identifiable Information (PII), or other sensitive data by sending them fake messages offering free tickets, gifts, giveaways, discounts, or other attractive items. Phishing attacks could occur via SMS, social media posts, emails, etc.
Threat actors commonly use two strategies when creating phishing domains:
Typosquatting:
Typosquatting is one of the social engineering techniques and can usually be seen in phishing scenarios. Its main goal is to trick the victim into visiting malicious websites with minor changes in the websites’ original names. During FIFA events, there can be seen created domains using typosquatting.
Possible typosquatting forms are “fifawordcup,” “fiifa,” “fifa2O22” (using the letter O instead of zero “0”), “fifawor1dcup” (using one “1” instead of letter L), etc.
![An example of typosquatting web site: fifawordcup2022[.]com](https://socradar.io/wp-content/uploads/2022/11/fifa-world-cup-2022-typosquatting-1024x626.jpg)
Generic Top-Level Domains (TLDs):
Another phishing tactic is using different generic Top-Level Domains (TLD) -.com, .org, .gov, etc.- with the same keyword the organization uses. These could be like fifa2022[.]pro, fifa2022[.]world, fifa2022[.]space while FIFA is officially using fifa2022.com. You can find some examples below:
- fifaworldcup.com
fifaworldcup.com is registered by FIFA and redirects to https://www.fifa.com/fifaplus/en/tournaments/mens/worldcup/qatar2022 and below are listed the same domain names with different TLDs registered just before Qatar2022.
|
Domain Name |
Date of Detection by SOCRadar |
|
fifaworldcup[.]app |
October 1, 2022 |
|
fifaworldcup[.]world |
October 1, 2022 |
|
fifaworldcup[.]pro |
October 1, 2022 |
|
fifaworldcup[.]online |
October 6, 2022 |
|
fifaworldcup[.]tours |
October 6, 2022 |
![Another website designed to live stream FIFA (fifaworldcup[.]world)](https://socradar.io/wp-content/uploads/2022/11/fifa-world-cup-2022-generic-tlds-1024x854.jpg)
- fifa2022.com
The “fifa2022.com” domain address is registered by Federation Internationale De Football Association (FIFA) itself, and this domain’s registrar is “CSC CORPORATE DOMAINS, INC.” when a whois query is made. In addition, this domain was registered on September 5, 2003.
|
Domain Name |
Registrar |
Date of Detection by SOCRadar |
|
fifa2022[.]ir |
Parvasystem |
October 9, 2022 |
|
fifa2022[.]live |
NameCheap |
October 1, 2022 |
![Iranian website that sells FIFA World Cup 2022 domains (fifa2022[.]ir)](https://socradar.io/wp-content/uploads/2022/11/iranian-website-selling-fifa-world-cup-2022-domains-1024x523.png)
Potential Phishing Domains
Phishing attacks on previous FIFA World Cup organizations showed parameters like “FIFA, WorldCup, year of the organization, name of the host country, name of host cities, name of the organization’s mascot, and the name of notable personages” are used for phishing domains. Threat actors prefer to create malicious domains with these keywords or combinations to design a phishing campaign. In this regard, SOCRadar analysts scanned domain names based on including specific keywords with their combinations –such as fifa2022, fifaworldcup, Qatar, Qatar22, tickets, Lusail, Al Khor, Al Rayyan, Doha, Al Wakrah, La’eebLa’eeb, etc. Till this blog’s publication date, they observed more than 200 potential phishing domains related to FIFA World Cup 2022. Some examples of the domains are listed below:
|
Domain Name |
Registrar |
Date of Detection by SOCRadar |
|
2022worldcupiclub88[.]com |
GoDaddy |
October 6, 2022 |
|
26lionspourqatar2022[.]com |
Domain.com |
October 6, 2022 |
|
accessqatarworldcup[.]com |
Atak Domain |
October 13, 2022 |
|
cupqatar[.]net |
Dynadot |
October 6, 2022 |
|
fifa[.]onl |
Dynadot |
October 13, 2022 |
|
fifa2022[.]bet |
GoDaddy |
October 12, 2022 |
|
fifa2022[.]space |
GoDaddy |
October 12, 2022 |
|
fifa2022[.]website |
Namecheap |
October 9, 2022 |
|
fifa2022live[.]com |
GoDaddy |
October 12, 2022 |
|
fifa2022live[.]net |
GoDaddy |
October 20, 2022 |
|
fifa4[.]cc |
Alibaba Cloud |
October 9, 2022 |
|
fifa5[.]cc |
Alibaba Cloud |
October 9, 2022 |
|
fifaqatar[.]art |
Namecheap |
October 20, 2022 |
|
fifaqatar[.]shop |
GoDaddy |
October 6, 2022 |
|
fifaqatarcup[.]com |
GoDaddy |
October 13, 2022 |
|
fifaquiniela[.]com |
PDR |
October 20, 2022 |
|
qatar2022[.]io |
Namecheap |
October 12, 2022 |
|
qatarworldcup[.]tv |
Tucows |
October 13, 2022 |
|
tickets-qatar2022[.]com |
Ascio Technologies |
October 12, 2022 |
|
tornel-qatar2022[.]com |
Akky Online Solutions |
October 12, 2022 |
|
qatar2022[.]palmsbet[.]top |
eNom, LLC |
October 12, 2022 |
|
qatar2022[.]pro |
GoDaddy |
October 12, 2022 |
![An example of a betting site opened for Qatar2022 (qatar2022[.]palmsbet[.]top)](https://socradar.io/wp-content/uploads/2022/11/fifa-world-cup-2022-potential-phishing-domains.jpg)
The detected potential phishing URLs are monitored 24/7 by SOCRadar analysts and reported to the relevant authorities as soon as they are transformed into a phishing page.
Sponsors/Partners and their impersonators:
Sponsor organizations can become targets using their names in phishing domains. Partners, sponsors, and supporters for FIFA World Cup Qatar 2022 are below:
FIFA Partners
- QatarEnergy
- Qatar Airways
- HYUNDAI • KIA
- Coca-Cola
- Wanda Group
- Adidas
- Visa
FIFA World Cup Sponsors
- BYJU’s
- Crypto.com
- Mengniu Dairy
- Budweiser
- Hisense
- McDonald’s
- Vivo
Regional Supporters:
- GWC Logistics
- QNB
- Ooredoo Telecommunications
SOCRadar Analysts detected some phishing domains related to FIFA World Cup 2022 partners during their research (e.g., cocacolaqatar2022.zendesk.com, adidas-worldcupqatar2022.com, using qnbqatar.cnumm.com)
- Adidas:
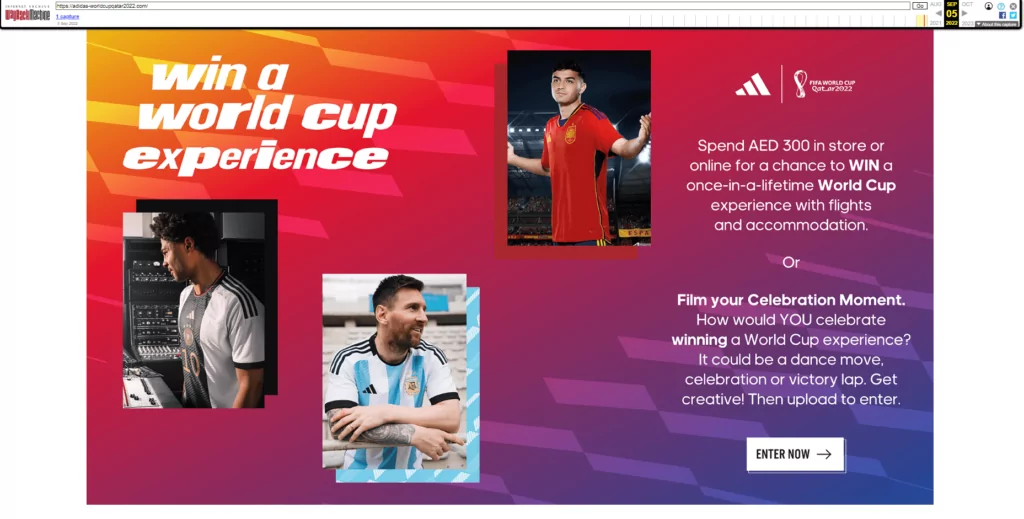
Note: In this example, the whois query shows that this domain is owned by an Iranian IP address.
- QNB:
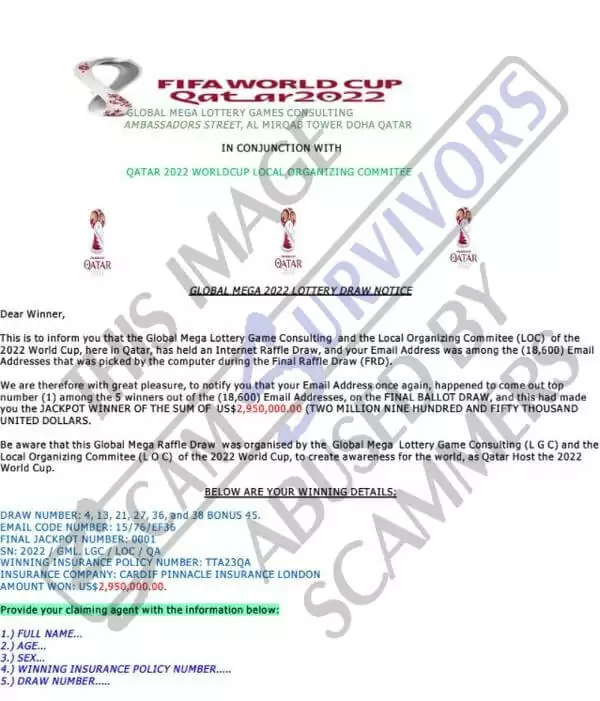
Phishing Mails
Threat actors use big event themes like FIFA World Cup to create phishing emails. They use the “fake lottery” context commonly to trick their victims. Here are some examples of phishing emails reported on various websites or forums that use the FIFA World Cup Qatar 2022 theme.

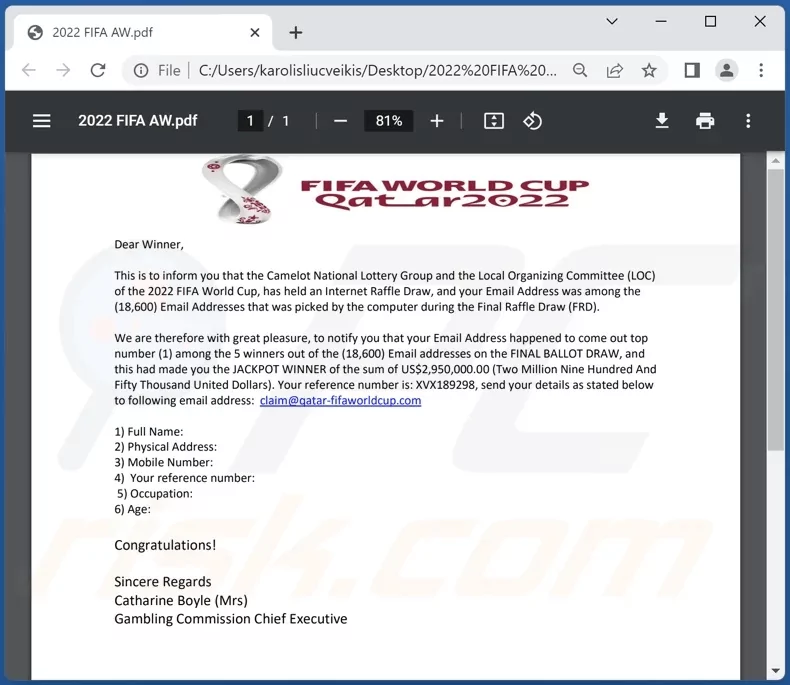
Besides fake websites and phishing emails, threat actors could use social media to operate their phishing campaigns using giveaways, and they can reach more people using advertisements.
Conclusion
Probably, FIFA World Cup 2022 in Qatar will be targeted by cybercriminals at a high level, like many others before. In this regard, all spectators and organizations participating in the event must take precautions to protect themselves from cyber risks.
The host country, Qatar, established its National Cyber Security Committee in 2013. In 2014, they published a National Cyber Security Strategy document, addressing action plans, implementations, and identifying possible threats in Qatar’s cyber landscape. Qatar has positioned itself to have robust cyber security controls in place over the years to ensure the cyber security of the event.
As another target for potential cyber threats, all FIFA spectators should be aware of the following points:
- Maintaining general cyber security hygiene (Using up-to-date software, anti-virus, etc.)
- To be aware of the numerous social engineering strategies that cybercriminals employ.
- To be aware of digital communication and website links related to the World Cup, especially not clicking on suspicious emails and web links with World Cup themes;
- Not to use credentials, passwords, or credit card information on sites or platforms where they are unsure of the security.
While FIFA World Cup 2022 event approaches, it is predicted that cyber threat activities will increase even more, and especially tournament-themed phishing campaigns and fake domain names will rise. Threat intelligence gathered before, during, and after the organization helps to determine the security environment and potential threats. For this challenge, a CTI (Cyber Threat Intelligence) solution fed by all channels, including social media, OSINT, and the dark web, will be helpful.
As an extended threat intelligence solution, SOCRadar will closely monitor cyber-attacks during the FIFA World Cup 2022 in Qatar and keep users updated.



































