
How Are MSPs (Managed Service Providers) at Risk of Data Breaches?
Have you ever wondered how your Managed Service Provider (MSP) is protecting both your data and its own? It is prudent to regularly assess your MSP along with other stakeholders in your supply chain to ensure robust security. Over recent years, hackers, especially ransomware groups, have caused data breaches at increasingly larger companies. A relatively new malicious tactic is emerging: when a cyberattack group gains access to an MSP, it attains the ability to simultaneously damage a multitude of companies serviced by the MSP.
Typically, Managed Service Providers possess elevated access rights across many of their customer networks. In numerous instances, multiple customers are managed through a centralized portal or data repository. If an MSP does not implement adequate cybersecurity controls on its systems, all client systems and data are consequently placed under cyber threat. We have already witnessed the devastating effects of this type of supply chain attack, with incidents like SolarWinds (2020) and Kaseya (2021) and MOVEit (2023) putting thousands of customers at risk in recent years. Let’s take a broader and more comprehensive look at the threat landscape facing MSPs from a cyber risk and threat intelligence perspective.
What is a Managed Service Provider (MSP)?
According to Gartner, a Managed Service Provider (MSP) is capable of delivering services such as network, application, infrastructure, and security management through continuous and regular support either on the customers’ premises, in the MSP’s data center (hosting), or in a third-party data center.
Traditionally, the term MSP has been applied to infrastructure or device-centric types of services, but it has expanded to include ongoing management, maintenance, and support.
MSPs have become a popular choice for companies that lack the internal resources to support their business technology needs. Functioning like on-demand IT teams, MSPs provide third-party technical support tailored to specific needs and budgets. There is a growing trend in utilizing such services, which can also be hosted in the cloud. According to Research and Markets, the Managed Service Provider (MSP) industry was valued at $161.37 billion in 2021 and is projected to reach $311.31 billion by 2027.
A Brief History of High-profile Attacks on Managed Service Providers (MSPs)
Two notable examples of high-profile attacks targeting Managed Service Providers are those related to SolarWinds (2020) and Kaseya (2021). These attacks impacted hundreds of companies and government agencies worldwide.
1) Solarwinds Orion
In December 2020, news emerged of a supply chain attack on SolarWinds’ network monitoring platform, Orion, affecting more than 18,000 public and private organizations.
Victims had their critical data and information accessed through a trojanized SolarWinds Orion software update, which carried the SUNBURST backdoor. While SUNBURST is attributed to Russian Intelligence threat actors, the names Nobelium and APT29 were also highlighted as associated threat actors.
This incident was noted as a severe cyber attack, negatively impacting 28% of MSPs along with numerous other sectors, including IT, consulting, government, and telecom.
2) Kaseya VSA
In July 2021, attackers targeted Kaseya VSA (Virtual System Administrator) servers used by Managed Service Providers to distribute REvil ransomware to thousands of corporate endpoints in a situation that became one of the largest mass-scale ransomware incidents to date. The attackers exploited a zero-day vulnerability in a VSA component, which was then used in an exploit chain that bypassed Windows Defender and other native operating system security measures. The attackers claimed to have infected “more than one million systems.”
Unfortunately, this attack had serious consequences for MSPs and their customers. More than 1,500 organizations and 40 MSPs worldwide suffered significant repercussions, many due to their connections with their Managed Service Providers.
Which APTs Have Recently Targeted Managed Service Providers?
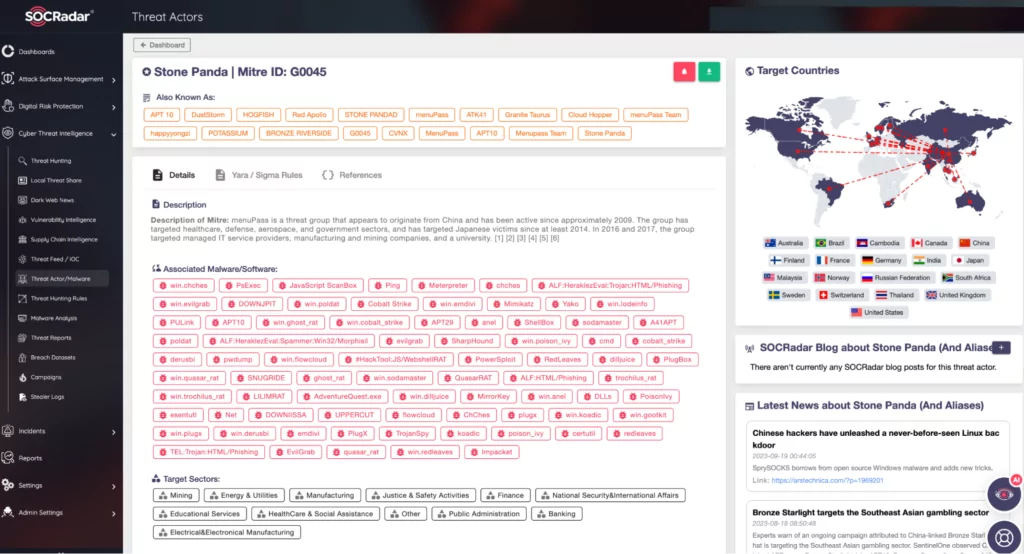
Some attacks on MSPs involve Advanced Persistent Threats (APTs) – often state-sponsored groups with objectives beyond financial gain, such as espionage. APT10, a Chinese-backed espionage group, is known to have targeted numerous MSPs in past attack campaigns focused on Australian, Japanese, US, and Norwegian organizations. Notably, IBM and HPE were among these targets. In May 2022, authoritative organizations such as the FBI, NSA, and CISA issued a cybersecurity advisory in anticipation of APTs increasingly targeting MSPs.
Why Do Threat Actors Target MSPs?
To understand why cybercriminals find MSPs incredibly attractive, let’s examine 3 main reasons.
- Attacking an MSP allows threat actors to potentially access multiple organizations with a single assault, given that an MSP serves a large number of customers. Hence, by compromising just one MSP, threat actors can gain access to a plethora of potential victims.
- Since MSPs are utilized by organizations of various sizes and verticals, they present a broader and richer environment for cyberattacks.
- Sometimes, MSPs can be the weakest link in the security chain of an important target for threat actors. For instance, although the target being pursued may have a robust and mature security posture, the MSP’s privileged access to the company’s digital environment may simplify the task for threat actors to pre-target the MSP and achieve their objective.
What Happens When MSPs are Compromised? Can They Trigger Massive Supply Chain Attacks?
Sometimes, it might be challenging to determine the full extent of the impact following a breach of Managed Service Providers. For instance, a data breach could escalate into a “cascade of supply chain attacks” a term brought to the forefront by the attack on the Windows desktop application “3CX VoIP client” that emerged in the second quarter of 2023. This indicates that when third-party companies providing services to numerous organizations are attacked, the involvement of other third-party service providers among the service recipients can amplify the impact of the cascade of supply chain attacks.
Consequently, third-party service providers that MSPs serve also confront this exponentially growing breach risk. These factors should be considered during risk assessment to ensure service providers do not become a weak and insecure link in the digital supply chain.
Recent Dark Web Incidents Related to IT & Security Companies
SOCRadar’s dark web team monitors underground forums and hacker channels 24/7, providing dark web intelligence by analyzing the data they obtain. Some of this current data will be discussed in regard to data breaches of companies offering IT and cybersecurity services relevant to MSPs.
Dark web intelligence refers to the stream of compiled and analyzed data collected from the dark web, which has proven to be one of the most effective solutions for proactively combating cybercriminals and reducing data loss. It can also protect you against potential future cyber-attacks by providing actionable and reliable intelligence on compromised accounts of your customers/employees before your organization and third-party companies such as MSPs are targeted.
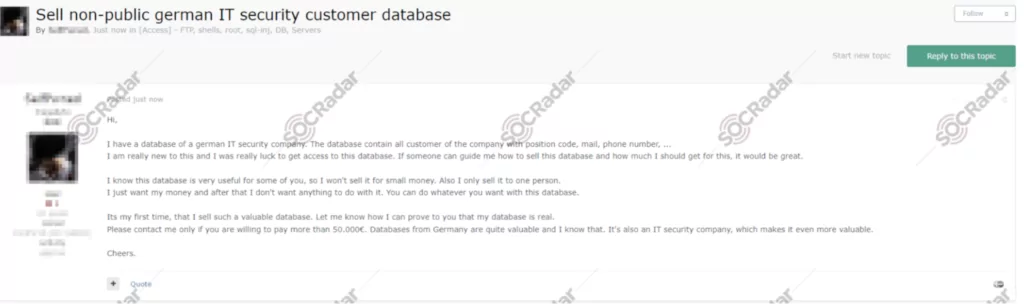
On February 25, 2023, in a hacker forum monitored by SOCRadar, a new alleged database sale was detected for an IT company operating in Germany.
On May 23, 2023, the Play ransomware group’s website, also monitored by SOCRadar, allegedly announced a new ransomware victim: Black Cat Networks. The company has been providing managed support for on-premises computer network infrastructure since 2007. The threat actor announced possession of confidential data, including customer and employee documents, financial records, and tax information, and threatened to disclose them within three days if the ransom is not paid.

On June 20, 2023, on the Black Basta ransomware group website monitored by SOCRadar, a new ransomware victim was allegedly announced as Materna Group. Founded in 1980 in Germany, Materna Group today comprises private companies, several subsidiaries, and a holding company. With a group turnover of EUR 554 million (2022), it, along with its subsidiaries, provides IT and digitalization project services.

How Can Customers of Managed Service Providers Prevent Being Affected by a Breach
Managed Service Providers and their customers often operate under a shared security responsibility model. In practice, the boundaries of this model can often become blurred, especially when determining who is responsible for what, particularly in terms of the security of infrastructure, applications, platforms, and data.
MSP customers should not assume that MSPs are secure by default. Instead, they should maintain ongoing communication and interaction with their MSP to review the security solutions implemented. Even the largest service providers can suffer data breaches and be negligent in protecting their customers’ data. The recent accidental exposure of 38 TB of data in Microsoft cloud services was preceded in 2022 by the leak of 65,000 customer data from 111 countries as a result of the misconfiguration of a bucket called BlueBleed.
Specification and contract processes should assertively require an MSP to demonstrate its ability to protect the client’s digital environment. Contractual provisions should include testing, auditing, documentation, and even financial contingencies for cyber impact.
What Are the Trends for MSP Cybersecurity Best Practices and Service Offerings?
According to ConnectWise’s MSP Threat Report 2023, below are the trends predicted for 2023 and beyond that will impact MSPs’ cybersecurity best practices and service offerings.
- MSPs continue to be a major target of sophisticated cyber attacks, particularly from state-sponsored groups, in supply chain and critical infrastructure attacks.
- Implementing a zero-trust network architecture is crucial for MSPs and should be a priority.
- Benefiting from threat intelligence information and fostering inter-organizational collaboration and information sharing for proactive security is critical for MSPs. A threat intelligence program has proven to be an essential component in reducing and managing supply chain risks.
- MSPs will continue to bridge the IT capability gap with technology stacks within the realm of consolidation and outsourcing; hence, prioritizing state-of-the-art security approaches is essential.
- The demand for a skilled and specialized workforce for MSPs to manage their security operations will increase, and filling this gap will require time.
How Can MSPs and Customers Be Protected Against Cyber Threats? How to Prevent an MSP Security Breach?
To ensure the security of sensitive information and data shared between Managed Service Providers and their clients, several crucial security-related recommendations are outlined below. By adopting these measures, security processes and contractual commitments can be re-evaluated to align with clients’ risk tolerance and mitigate risks associated with MSPs.
- Prevent initial compromise by enhancing the security of vulnerable devices, protecting internet-facing services, defending against brute force attacks and password spraying, and warding off phishing attempts.
- MSPs should enable logging and monitoring of both internal and client network activity, as contractually agreed upon, and augment these measures for better security visibility.
- While MSPs recommend the adoption of Multi-Factor Authentication (MFA) across all customer services and products, clients should ensure that their contractual arrangements mandate the use of MFA in the services and products they receive.
- MSPs should have a comprehensive understanding of their environment and segregate their networks accordingly. It is essential to identify, group, and isolate critical business systems, applying appropriate network security controls to them to reduce the potential scale of a security breach.
- MSPs should enforce the principle of least privilege within their network environment and update privileges promptly as there are changes and updates to management roles.
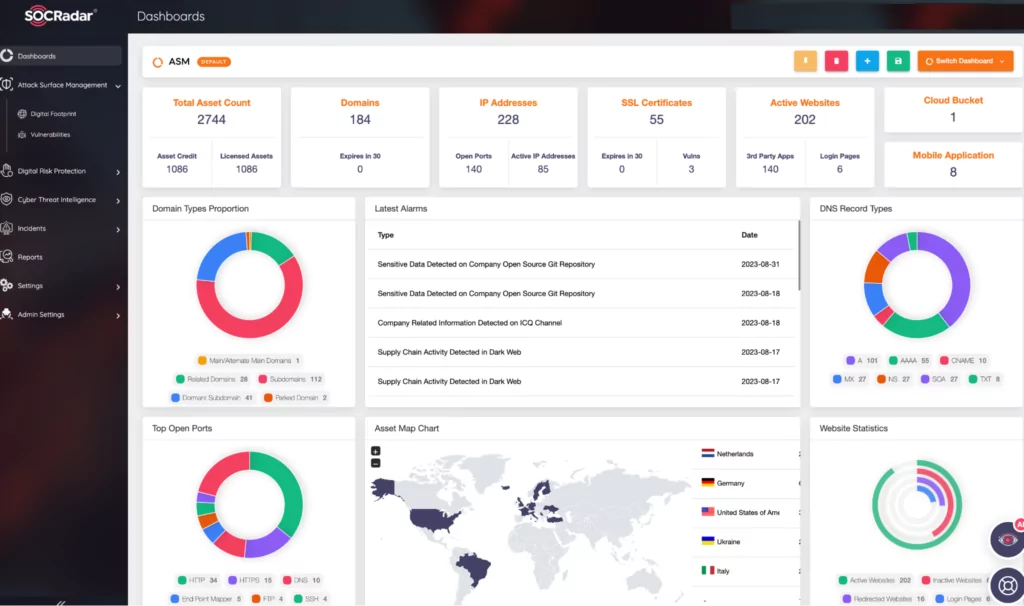
- Both MSPs and customers should periodically review their internet attack surface and consider engaging professional Attack Surface Management (ASM) services such as SOCRadar EASM when needed. These services are vital as they provide a unified view of your cyber assets for complete visibility of your expanding attack surface.
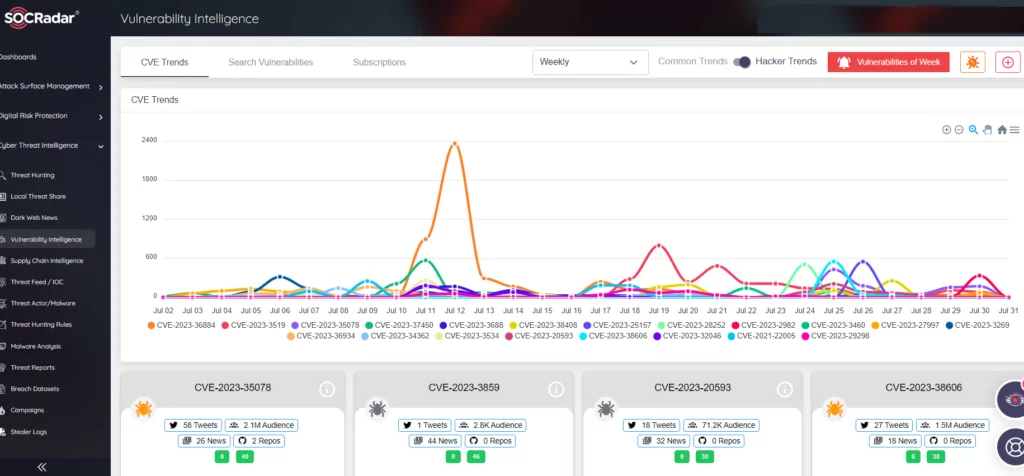
MSPs should ensure that their software is up-to-date, including operating systems, applications, and firmware. It is crucial to prioritize patching vulnerabilities listed in CISA’s catalog of Known Exploited Vulnerabilities (KEV). The SOCRadar Vulnerability Intelligence service can be considered to facilitate vulnerability tracking and provide more accessible insights.
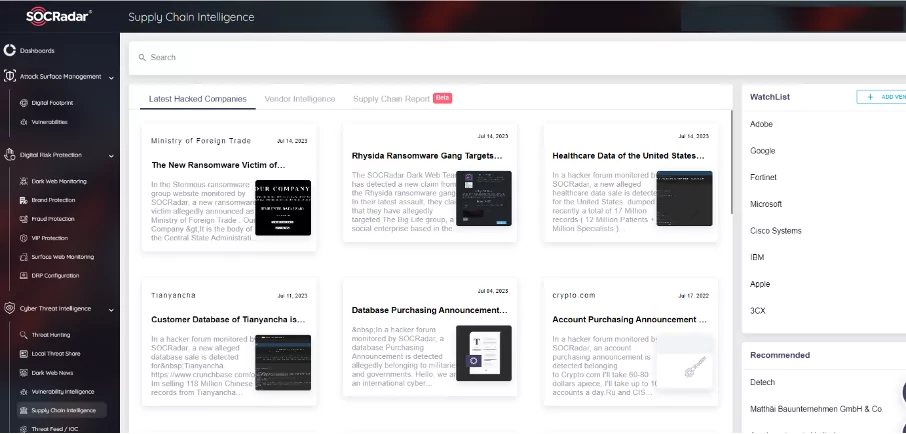
- Proactive management of information supply chain risk across all units is crucial for MSPs, utilizing risk assessments to determine and prioritize resource allocation. The SOCRadar Supply Chain Intelligence module can alert you to companies currently exposed to cyber-attacks, extract actionable intelligence from historical cyber incidents and data breaches reported by manufacturers, and provide a report enriched with threat intelligence.
- Both MSPs and their customers should collaborate on issues such as cybersecurity, where shared responsibility is pivotal. It’s essential to draft contracts that clearly define their roles and responsibilities.
Conclusion
In this article, we’ve observed that Managed Service Providers are not only susceptible to large, headline-grabbing attacks but are now targets of widespread malware and ransomware attacks akin to other organizations.
We explored why MSPs need to exhibit higher security standards and why they should be at the forefront of adopting the security strategies they recommend to their clients. While MSPs are expected to ease and enhance their customers’ operations, becoming an entry point for malicious activity could trigger severe consequences no one wishes to bear. The rising number of attacks and evolving trends signify growing security risks.
We continually urge organizations to adopt measures to shield themselves from cyber threats and to maintain vigilant monitoring for signs of malicious activity. It is imperative to note that a fundamental step in guarding your organization against data breaches involves your security team actively exploring cyber threat intelligence products and services. SOCRadar assists security teams in addressing each of these security considerations across the entire intelligence ecosystem.




































