
Major Cyber Attacks Targeting the Finance Industry
The finance industry is an attractive target for cybercriminals due to the large amounts of sensitive data and financial assets at stake. Over the past decade, we have witnessed a series of high-profile cybersecurity incidents that have not only compromised the security of financial institutions but also shaken the confidence of consumers and investors alike. While Adam Smith’s concept of the invisible hand and laissez-faire economics suggest that markets will naturally find equilibrium, the reality is far more complex in the world of cybersecurity.
According to IBM’s Cost of a Data Breach Report 2024, the global average cost of a data breach has reached $4.88 million, a 10% increase from the previous year. For organizations in the financial sector, this growing financial burden highlights the importance of cybersecurity investments. In addition, the largest fine under the European Union’s General Data Protection Regulation (GDPR) in 2023 was €1.3 billion, imposed on Meta, underscoring the significant legal and financial risks of a breach.
However, in the realm of cybersecurity, the “invisible hand” is more of a vigilant overseer—constantly monitoring and intervening to ensure that systems remain secure. In this context, SOCRadar XTI acts as this invisible hand, continuously tracking hacker forums, Telegram channels, and ransomware group sites to detect and mitigate emerging threats. This blog post will explore some of the most significant cybersecurity events affecting the financial sector, with a focus on incidents from 2023 through early 2025.
What Are the Most Common Types of Cyber Attacks Targeting the Finance Industry
The financial sector continues to be one of the most targeted industries in the cyber threat landscape, with cybercriminals deploying a range of sophisticated attacks. These include data breaches, phishing, ransomware, and DDoS attacks, all of which pose significant risks to financial institutions, investors, and consumers.
Data leaks and financial fraud dominate the threat spectrum, while the rise of Dark Web activity has made these threats even more prevalent, with cybercriminals increasingly using hacker forums and other platforms to buy and sell access to financial networks, tools, and stolen data.
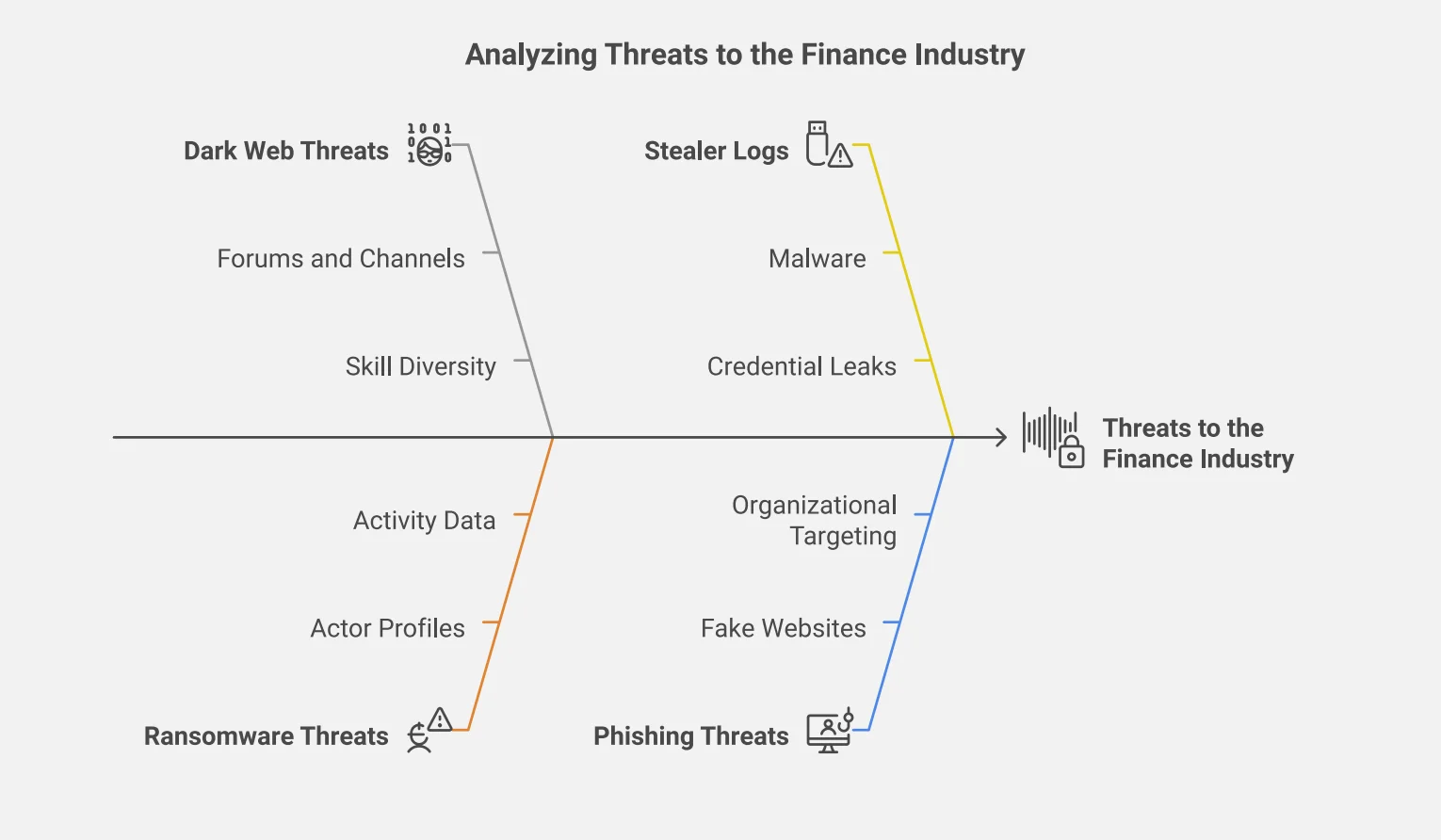
Common cyber threats to the finance industry
Content of Dark Web Posts Targeting the Financial Sector
SOCRadar has identified numerous cyber attack allegations on Dark Web platforms, including hacker forums and Telegram channels. From January 2023 to February 2025, SOCRadar observed 2,893 database sales and leakage claims, along with a wide range of other malicious activity involving service sales, vulnerability/exploit sales, phishing, and even DDoS/website defacement.
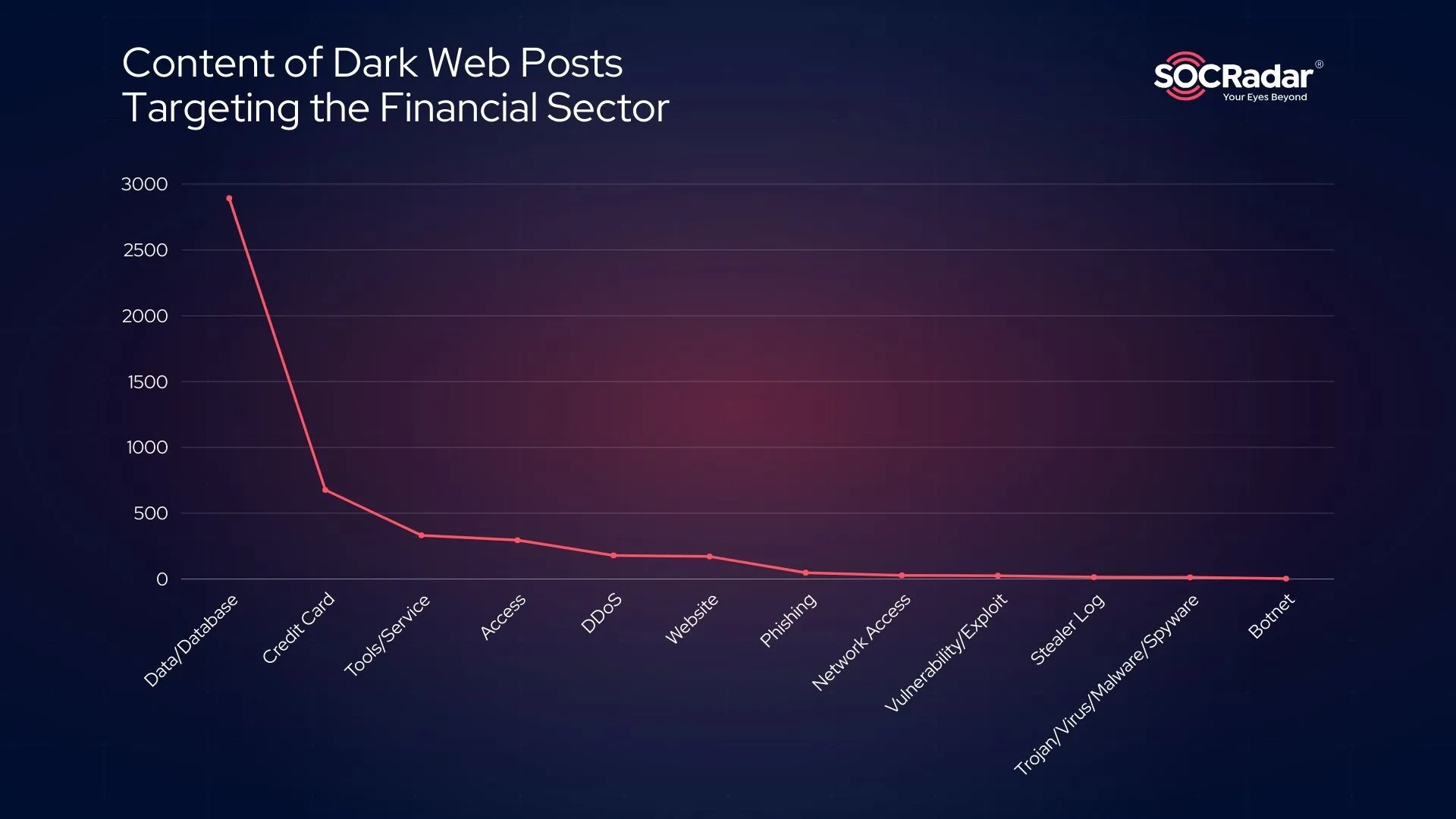
Content of Dark Web Posts Targeting the Financial Sector
The overwhelming majority of posts targeting the financial sector on the Dark Web are related to database sales and leaks, accounting for 55.5% of observed activity. The second most common category involves credit card sales and carding methods, comprising 13% of the total activity, while third-place entries include posts related to the sale of various tools and services. This reflects the dominance of data breaches and financial fraud in the ongoing cyber threat landscape.
Most Targeted Countries in the Finance Industry
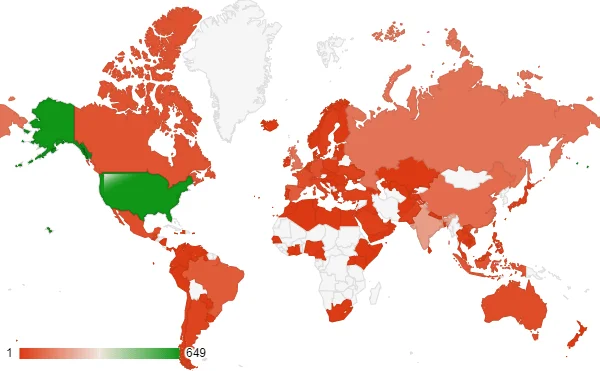
Targeted Countries for the Finance Industry
The global nature of cyber threats against financial institutions is evident from the wide geographical spread of targeted organizations. The countries most frequently targeted by these cyber attacks include the United States, India, the United Kingdom, Russia, China, Spain, Brazil, Indonesia, Canada, and Germany.
Threat Actors That Are Most Targeting the Financial Sector (2023 – Early 2025)
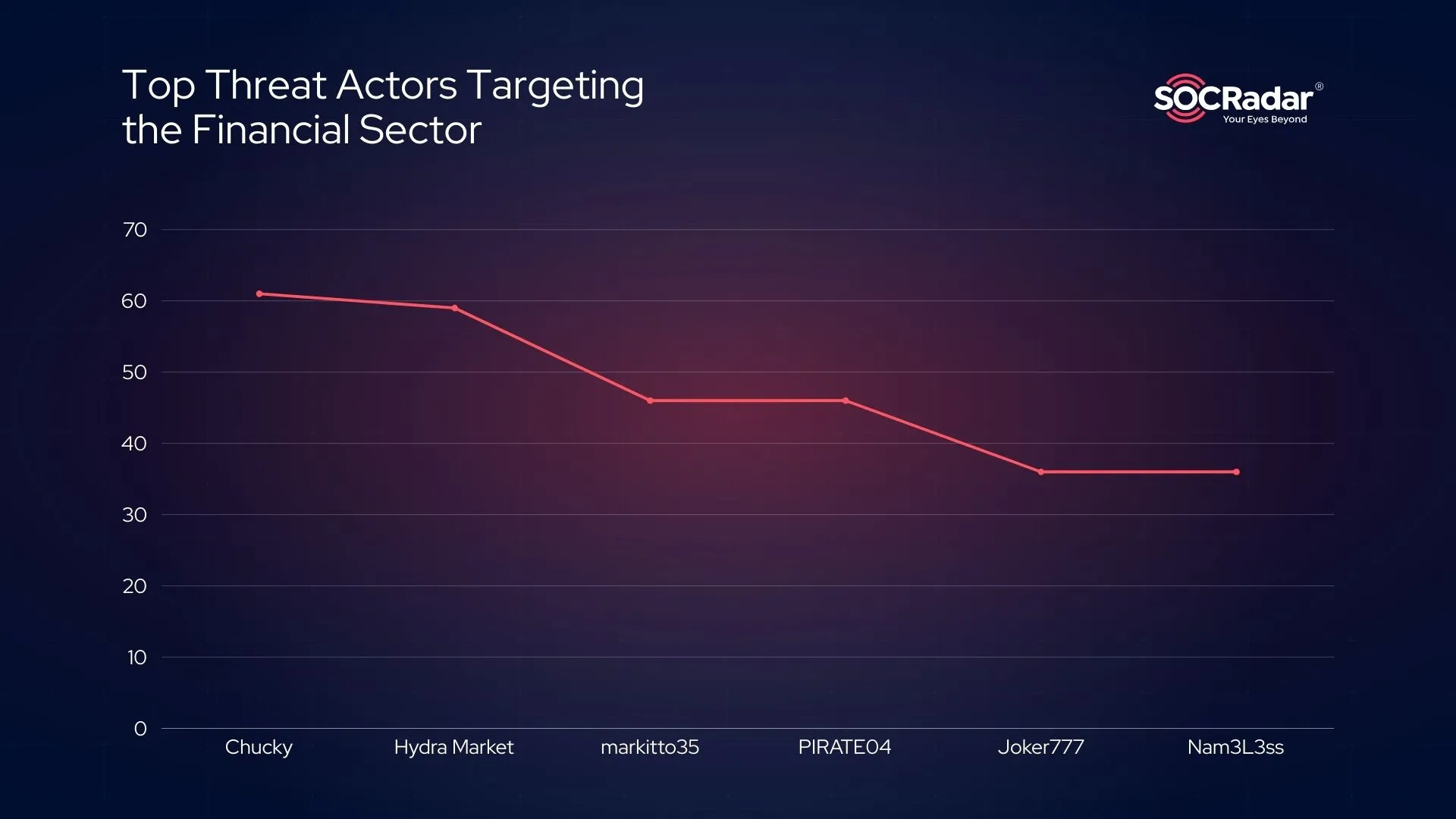
Top Threat Actors Targeting the Financial Sector in 2023 – 2025 Q1
Since 2023, several notorious threat actors have been particularly active in targeting the financial industry. Leading the pack is Chucky, an administrator of the LeakBase hacker forum, who has been responsible for reposting and publishing new data breaches. Chucky was the most active threat actor in 2023, contributing significantly to the rise in data leaks targeting the financial sector.
Another key player is IntelBroker, infamous for their involvement in high-profile breaches, including those affecting Europol, Apple, and AMD. IntelBroker’s attacks against the financial sector account for 11% of their total cyber intrusions across industries.
Other notable actors include Hydra Market, once the largest darknet market hosting 80% of Dark Web activity before its 2022 shutdown, and Nam3L3ss, known for leaking sensitive data from organizations like Amazon and HSBC through claimed past exploitations of the MOVEit Transfer software.
Top 10 Ransomware Gangs Targeting the Financial Sector
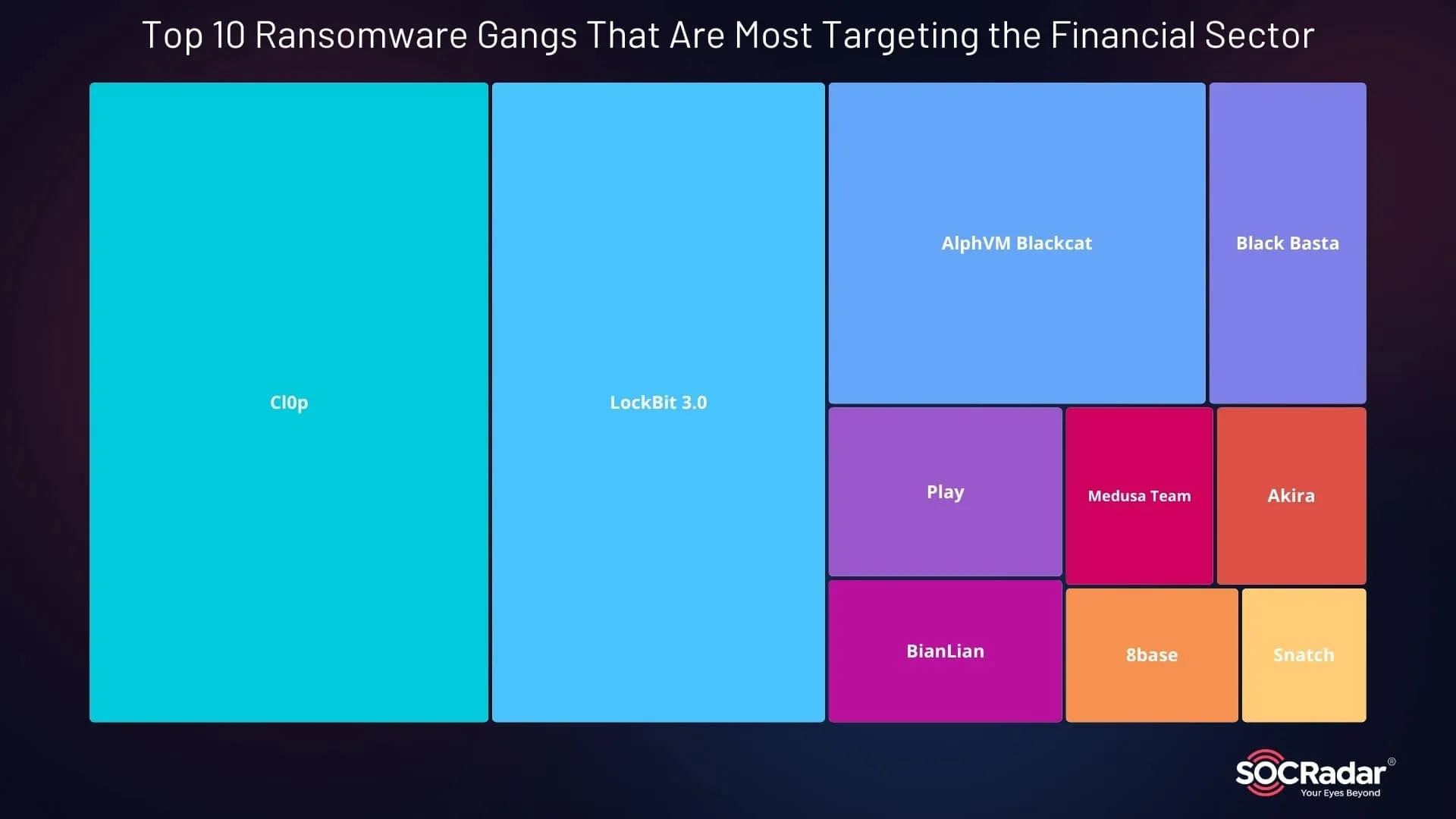
Top 10 Ransomware Gangs That Are Most Targeting the Financial Sector
Ransomware attacks have been a major threat to the financial industry, with several gangs leading the charge. Cl0p ransomware tops the list, accounting for 24.9% of ransomware incidents. LockBit 3.0 follows closely with 20.9%, and BlackCat (ALPHV) claims 12% of the attacks. Other significant groups include Black Basta (5%), Play (4%), BianLian (3.3%), and Medusa Team (2.6%). These statistics illustrate the pervasive threat ransomware poses to financial institutions, with each group employing increasingly sophisticated methods to breach security defenses.
Check out SOCRadar’s most recent Finance Industry Threat Landscape Report for more detailed information on the current threats affecting the financial industry. Data breaches, new cyber threats, and the most recent strategies used by threat actors to target financial institutions are all covered in this thorough analysis.
Our report includes detailed findings and actionable intelligence, with separate briefs available for CISOs and CEOs to help guide strategic decision-making.

Stay ahead of evolving threats and gain the insights you need to protect your organization by exploring the full report now.
Major Cybersecurity Incidents Affecting the Financial Sector: 2023 and Beyond
In this section, we will review some of the most significant cybersecurity breaches and threats targeting the financial sector from 2023 to the present. By examining key incidents, we aim to highlight the tactics used by attackers and the consequences for financial institutions.
FBCS Data Breach Exposes Personal Information of Over 4 Million
In February 2024, Financial Business and Consumer Solutions (FBCS), a U.S.-based debt collection agency, experienced a data breach that affected over 4 million individuals. Between February 14 and February 26, cybercriminals accessed sensitive data, impacting clients like Comcast and Truist Bank.

FBCS is a collection agency, operating within the U.S.
Initially reported to affect 1.9 million individuals, the breach’s scope grew to 4.2 million by July. Exposed data included names, addresses, Social Security numbers (SSNs), and medical information, heightening the risk of identity theft. Comcast confirmed ransomware involvement, offering affected customers a year of free credit monitoring. Truist Bank notified impacted customers in September and provided additional guidance and monitoring solutions.
For more information, read SOCRadar’s detailed coverage: FBCS Breach Exposes Millions, Including Comcast and Truist Bank.
American Express Account Details Exposed

American Express Card
In March 2024, American Express Co. informed Massachusetts regulators that a breach at an external company might have compromised the account details of its cardholders. Although AmEx did not disclose the name of the hacked company or the potential number of affected individuals, it urged customers in a letter to monitor their accounts for any suspicious activity.
Utilize SOCRadar’s Dark & Deep Web Monitoring capabilities to mitigate the impact of such attacks. With SOCRadar’s Dark Web News feature, you can track the latest data exposures and other incidents on threat actor channels. This feature ensures you stay informed about the latest developments and potential threats, allowing for proactive security measures.
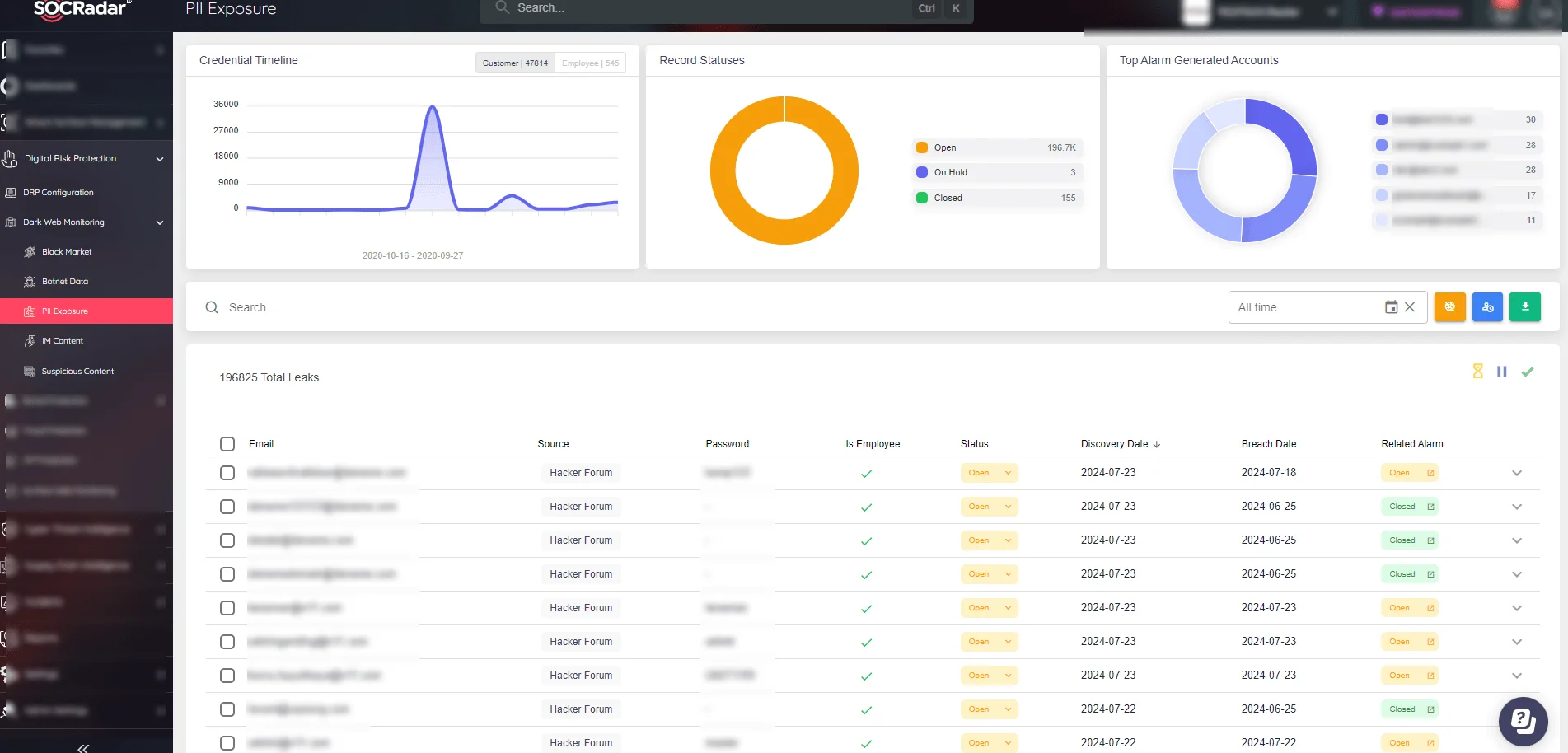
SOCRadar Dark Web Monitoring
Furthermore, SOCRadar consistently monitors cybercriminal forums for fraudulent activity. This helps identify if your private, corporate, or credit card information has been stolen and exposed in Dark Web channels. Through SOCRadar’s Dark Web Monitoring feature, you can check whether your sensitive data is shared in hacker forums, providing an essential layer of protection.
By leveraging SOCRadar’s Dark Web Monitoring and News services, financial institutions can strengthen their cybersecurity posture, proactively countering cyber adversaries and safeguarding sensitive data. Stay ahead of the curve and protect your organization with SOCRadar’s cutting-edge solutions.
LoanDepot Announces Ransomware Attack Compromising Personal Data of 16.6 Million Customers

The cover of LoanDepot’s announcement post regarding their cyber incident.
In January 2024, the US-based mortgage and loan giant LoanDepot announced that it had experienced a ransomware attack. The company revealed that they had taken some of their systems offline in response to the attack. LoanDepot disclosed that sensitive information belonging to 16.6 million customers had been compromised. The stolen data included names, birth dates, email and postal addresses, financial account numbers, and phone numbers. Additionally, LoanDepot confirmed that Social Security Numbers were also stolen during the ransomware attack.
Cross Switch Breach Compromises Personal Data of 3.6 Million Users
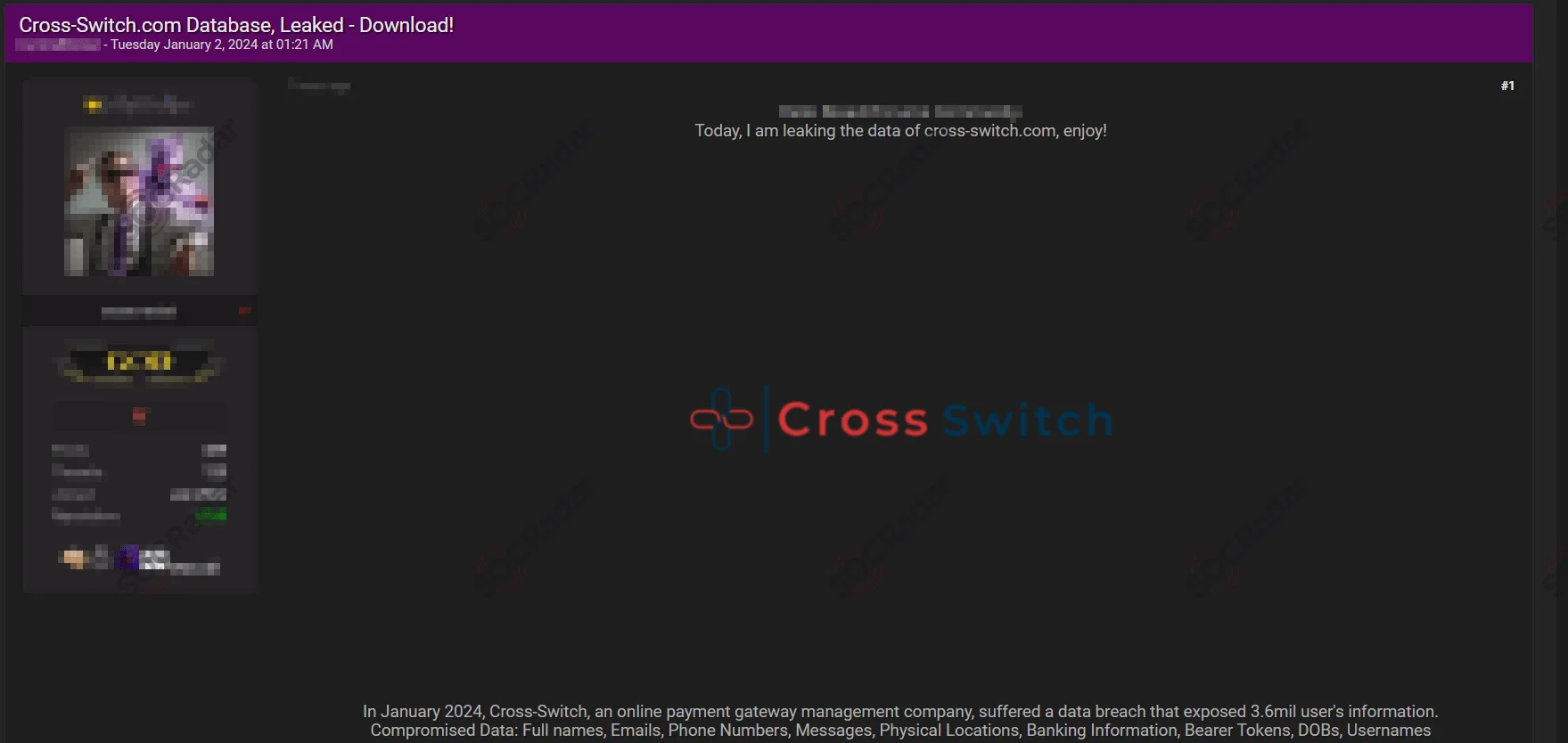
Cross-Switch database leak post (SOCRadar Dark Web News)
In January 2024, Cross Switch, an online payment gateway platform, suffered a major data breach allegedly caused by the threat actor IntelBroker. The breach exposed the personal details of 3.6 million users. IntelBroker revealed the breach on forums, raising concerns over cybersecurity and privacy. The exposed data included names, usernames, phone numbers, banking details, emails, locations, and dates of birth.
Cyber Attack on Mr. Cooper Exposes Data of Nearly 15 Million

Mr. Cooper logo
In October 2023, Mr. Cooper, the largest nonbank mortgage servicer in the U.S., suffered a cyber attack that exposed the personal information of 14.7 million individuals. The breach, occurring between October 30 and November 1, included names, addresses, phone numbers, Social Security numbers, dates of birth, and bank account numbers. The incident also caused a November technical outage, impacting customer payments.
Latitude Financial Breach 14 Million Records Stolen

Latitude logo
In March 2023, Latitude Financial, an Australian financial services company, experienced a data breach in which hackers stole 14 million customer records. These records contained sensitive personal and financial information, including names, addresses, dates of birth, credit card details, driver’s license numbers, passport numbers, and financial statements.
TMX Data Breach Impacts 4.8 Million Customers

TMX Finance logo
TMX Finance and its subsidiaries TitleMax, TitleBucks, and InstaLoan suffered a data breach affecting 4,822,580 customers. The breach, however, was only discovered on February 13, 2023. An investigation revealed that between February 3 and 14, 2023, hackers had stolen sensitive customer data, including full names, dates of birth, passport numbers, driver’s license numbers, federal and state identification card numbers, tax identification numbers, Social Security numbers, financial account details, phone numbers, physical addresses, and email addresses.
Discover the Powerful Features of SOCRadar’s Supply Chain Intelligence
SOCRadar’s Supply Chain Intelligence module enhances cybersecurity with robust features, providing organizations with unparalleled visibility into their supply chain security. Covering over 50 million companies across 373 sectors in 249 countries, this tool automates the mapping process and generates actionable recommendations.
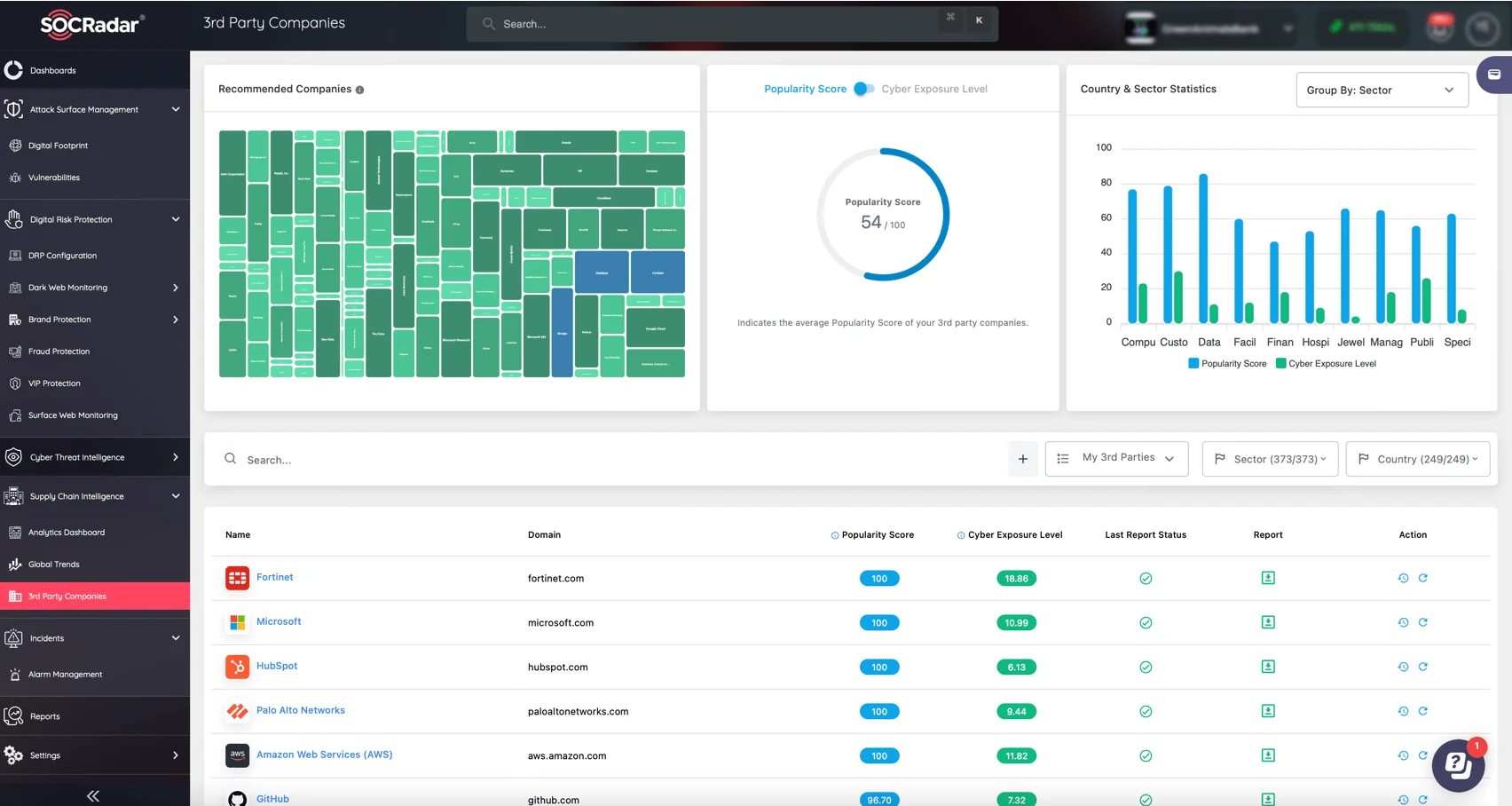
SOCRadar Supply Chain Intelligence – 3rd Party Companies
Key features include:
- Real-time updates on the latest cybersecurity developments and trends.
- Analytics Board for monitoring third-party firms and analyzing global trends.
- Advanced alarming system for critical events and potential risks.
- Comprehensive security reports on third-party vendors.
Additionally, the module offers advanced scoring mechanisms, such as the Cyber Exposure Level and Popularity Score, aiding in prioritizing crucial suppliers. This strategic approach ensures resilience against global cybersecurity threats.
Ransomware Attacks in the Financial Sector
The financial sector continues to be a prime target for ransomware groups, with numerous high-profile breaches occurring in recent years. Ransomware attacks have not only compromised the data of major financial institutions but also threatened the privacy and security of millions of customers.
Prudential Financial Data Breach Affects 2.5 Million People
In February 2024, Prudential Financial reported a data breach compromising the personal information of over 2.5 million individuals. Detected on February 5, the breach was attributed to a cybercrime group accessing administrative and employee accounts. The BlackCat (ALPHV) ransomware group claimed responsibility on February 13.

Discover how BlackCat Ransomware (ALPHV) works and its TTPs by visiting SOCRadar’s Dark Web Profile.
Initially, Prudential reported that 36,000 individuals were affected, but a later update revealed the true scope of the breach, affecting 2,556,210 people. Personal data stolen included names and driver’s license numbers.
Evolve Bank & Trust Data Breach Exposes Personal Info of 7.6 Million
In July 2024, Evolve Bank & Trust disclosed a data breach impacting 7.6 million individuals. The breach was tied to a LockBit ransomware attack, which exposed sensitive customer data after the ransom was left unpaid. The stolen data includes names, Social Security numbers, bank account numbers, and contact details.
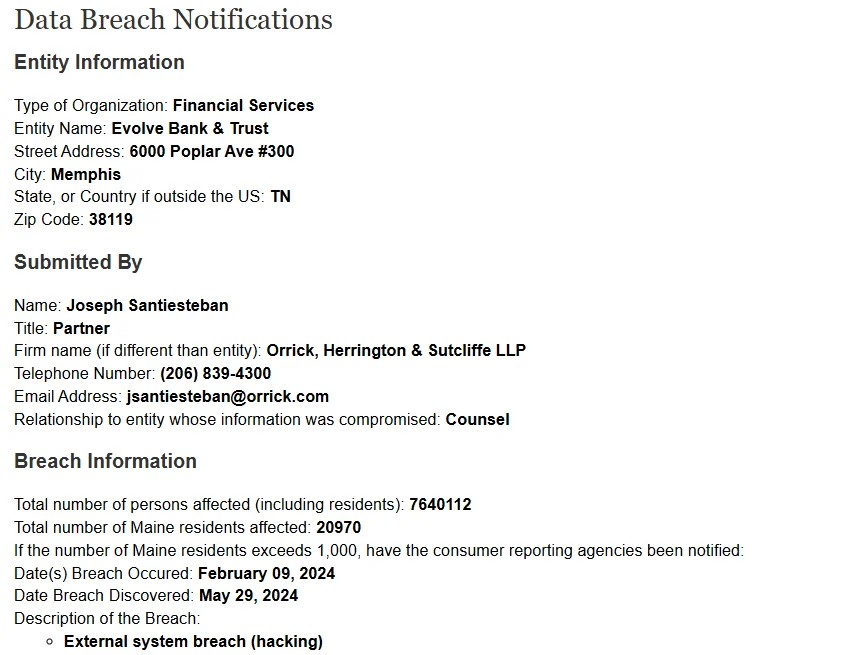
Evolve Bank & Trust breach filing (Maine.gov)
While no funds were accessed, Evolve Bank offered affected individuals 24 months of free credit monitoring and identity protection services. The breach was detected on May 29, with attackers gaining access as early as February.
ALPHV/BlackCat Ransomware Attack on Tipalti Threatened Major Clients

ALPHV’s statement on their dark web platform
In December 2023, the ALPHV/BlackCat ransomware group, known for sophisticated cyber attacks, targeted Tipalti, a leading FinTech company. This alleged breach compromised Tipalti and threatened its high-profile clients, including Roblox, Twitch, and X.
ALPHV/BlackCat claimed to have accessed Tipalti’s systems on September 8, 2023, stealing over 265GB of sensitive data. The attack posed significant risks, particularly to Roblox and Twitch, whose confidential information could be leaked or used for extortion.
LockBit Ransomware Leaks 1.5TB of Data from Bank Syariah Indonesia and Implements Triple Extortion on Fullerton India
In May 2023, LockBit ransomware revealed that it targeted two financial institutions with devastating effects.
Bank Syariah Indonesia (BSI) faced the leak of 1.5 terabytes of personal and financial data affecting 15 million customers and employees after ransom negotiations fell through. The compromised data included information on approximately 15 million customers and employees of Indonesia’s largest Islamic bank. Although BSI initially attributed the service disruptions to IT maintenance, LockBit claimed responsibility for the cyber attack. Negotiation screenshots revealed that LockBit initially demanded $20 million before halting communications, despite the bank’s offer of $10 million.
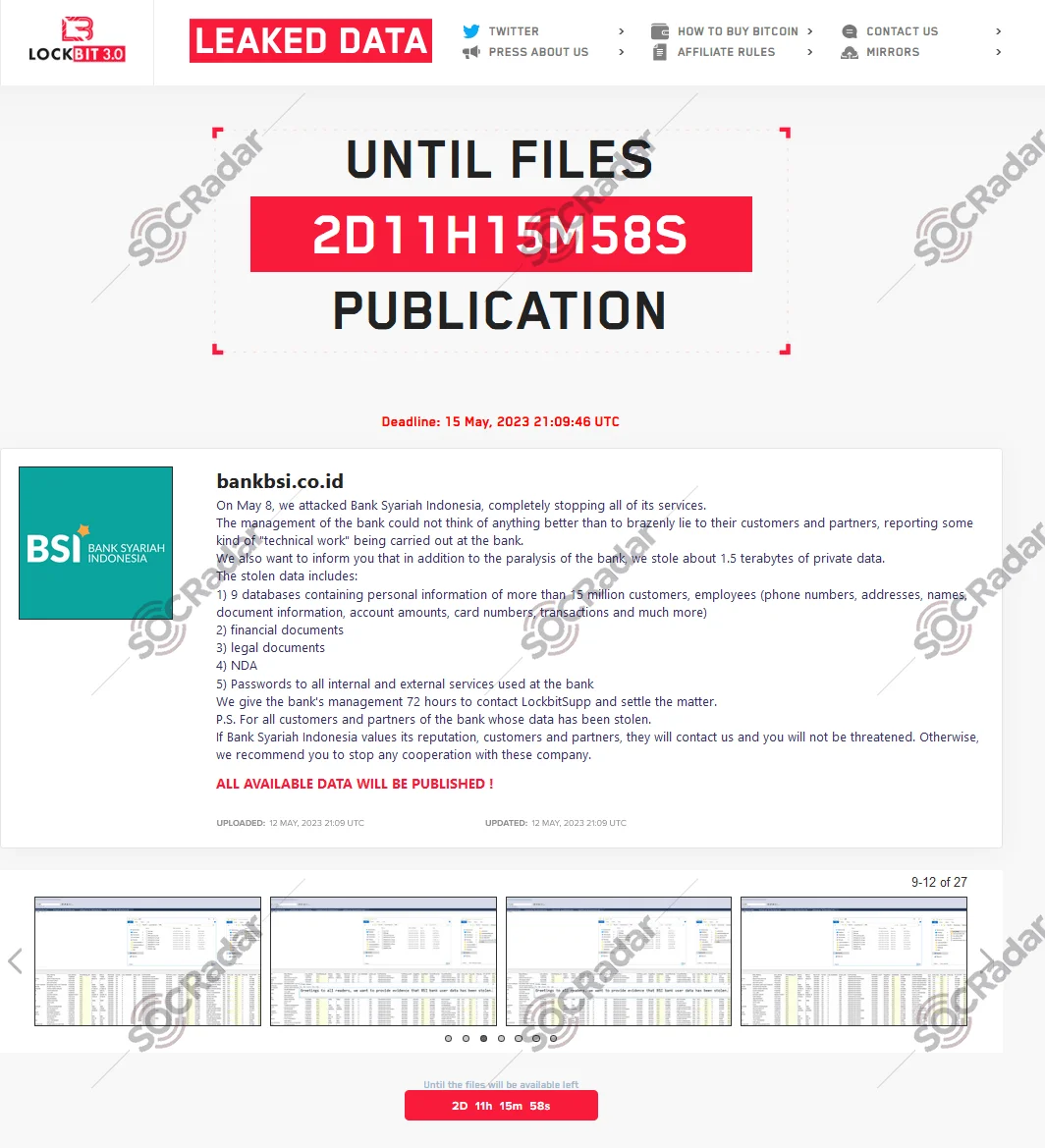
LockBit’s statement on their dark web platform
In parallel, the ransomware actors claimed to have leaked 600GB of data from Fullerton India, after demanding a $3 million ransom. Following a malware attack, Fullerton India briefly suspended operations, but enhanced cybersecurity measures allowed them to resume services. The ransomware group listed the bank on their data leak site, claiming to have stolen loan agreements. Fullerton India’s refusal to pay led to triple extortion tactics.
In a triple extortion attack, cybercriminals demand payment not only from the initial target but also from anyone affected by the potential disclosure of the target’s data.
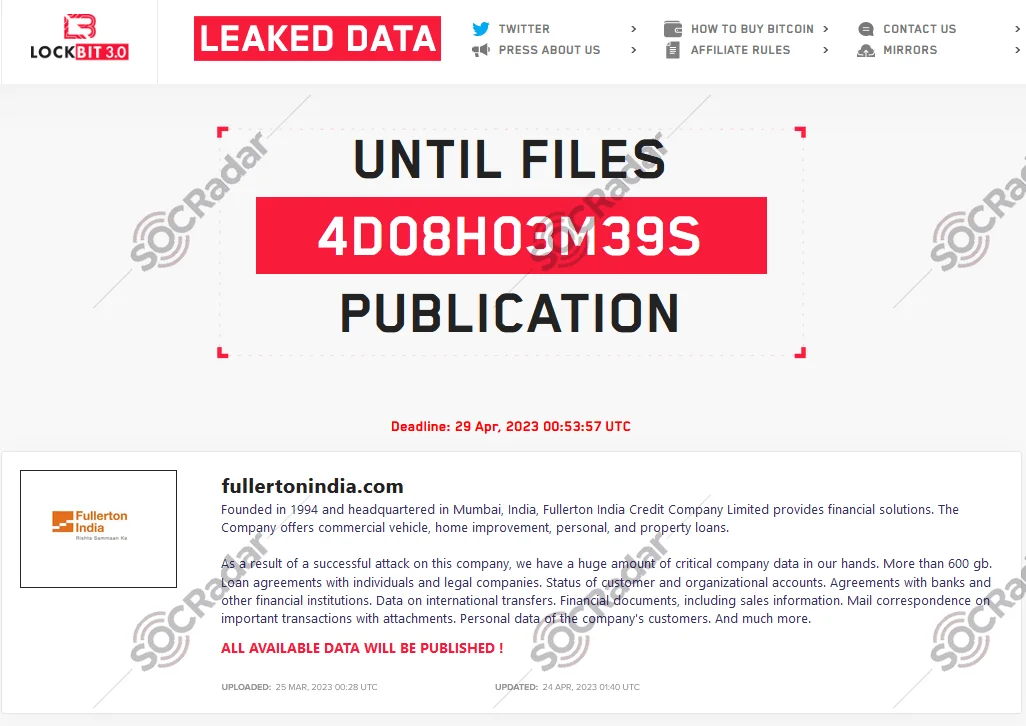
LockBit’s statement on their dark web platform
Second Cyber Attack Claim in a Year
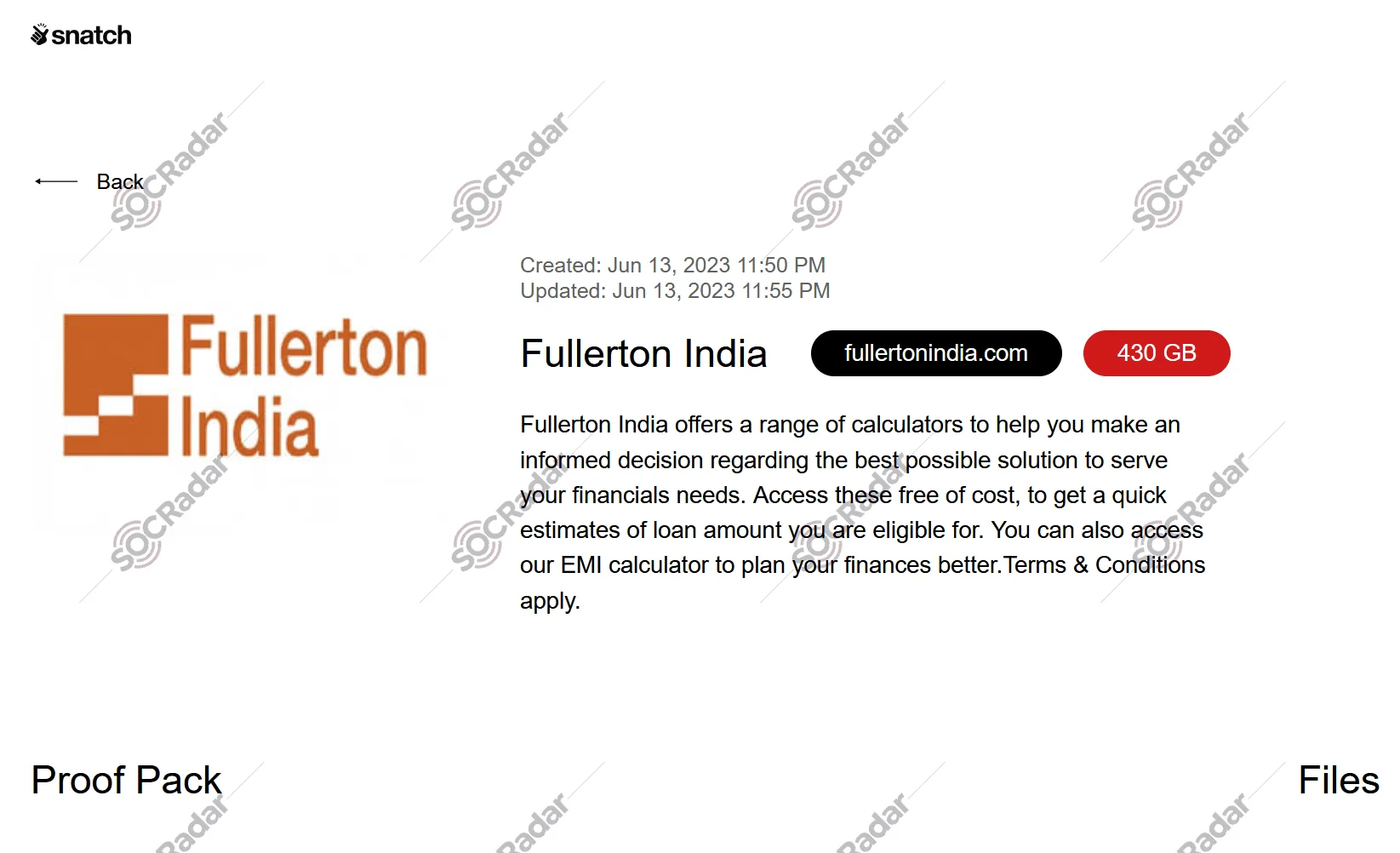
Snatch ransomware gang’s statement on their dark web platform
In June 2023, Fullerton India was also added to the list of victims of the Snatch ransomware gang, which claimed to have compromised an additional 430GB of data.
How SOCRadar Can Help Organizations in the Finance Industry Stay Ahead of Ransomware Threats?
Organizations must keep pace with the evolving threat landscape by adapting their security strategies. SOCRadar’s Extended Threat Intelligence solution provides real-time insights into emerging threats, enabling proactive countermeasures against cyber adversaries. Implementing multi-layered security measures is essential, and SOCRadar supports this with its Threat Intelligence, monitoring services, and advanced Ransomware Intelligence tool.
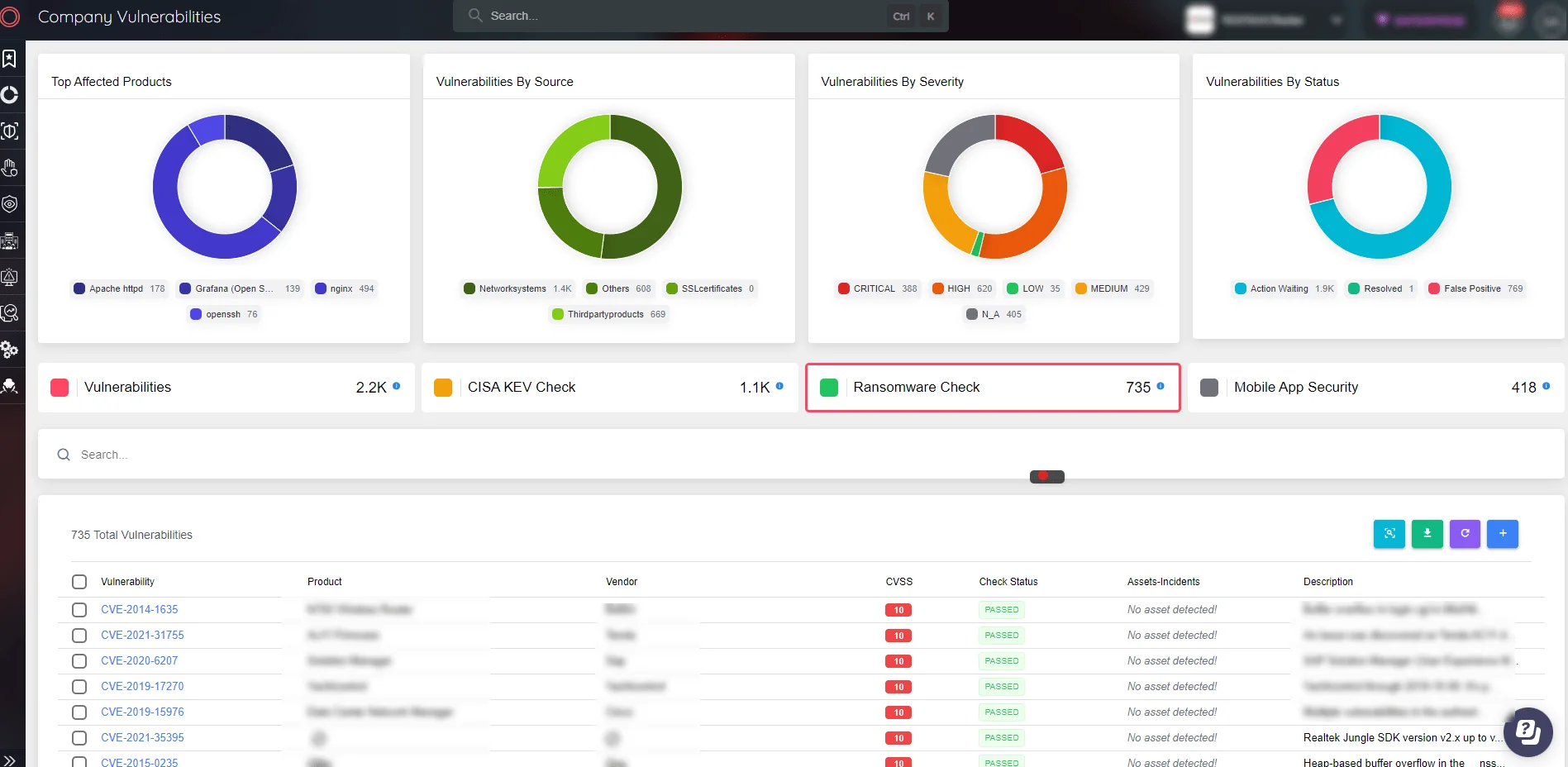
SOCRadar Attack Surface Management
Consistent vigilance against ransomware is necessary, and SOCRadar’s Attack Surface Management helps identify and counter potential threats. Additionally, continuous employee education and training are crucial, supported by SOCRadar’s Digital Risk Protection suite, which includes VIP and Brand Protection services.
Why is SOCRadar the Invisible Hand of Cybersecurity?
Dark Web monitoring is crucial for the financial industry, not only for initial threat detection but also for tracking the evolution of incidents and understanding their broader implications. The continuous activity on Dark Web forums serves as a stark reminder of the persistent threats facing financial institutions. Below, we examine three incidents involving renowned hacker forums, underscoring the importance of vigilant monitoring.
Alleged Data Breach of HSBC and Barclays by IntelBroker
In April 2024, the notorious threat actor IntelBroker announced on BreachForums that they had breached databases allegedly belonging to HSBC and Barclays. The threat actor claimed the data included sensitive information such as notary requests, security certificates, PIX keys, JKS files, security signing keys, compiled .jar files, source code stolen from GitLab, and other unsorted documents.
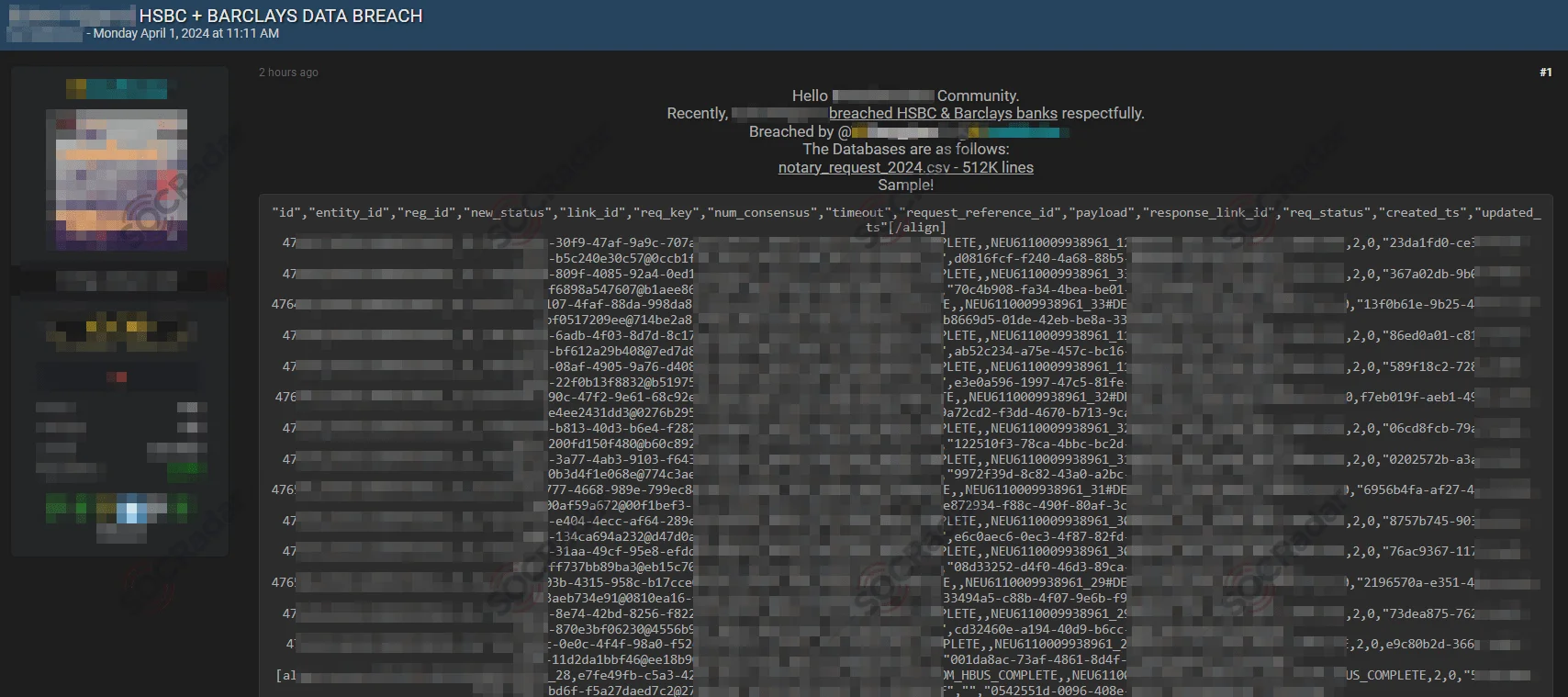
IntelBroker sells data it claims belongs to HSBC and Barclays
According to IntelBroker, the breached data included a file named “notary_request_2024[.]csv” with 512,000 lines containing detailed records. Other files allegedly contained security certificates and keys, compiled code, and various documents.
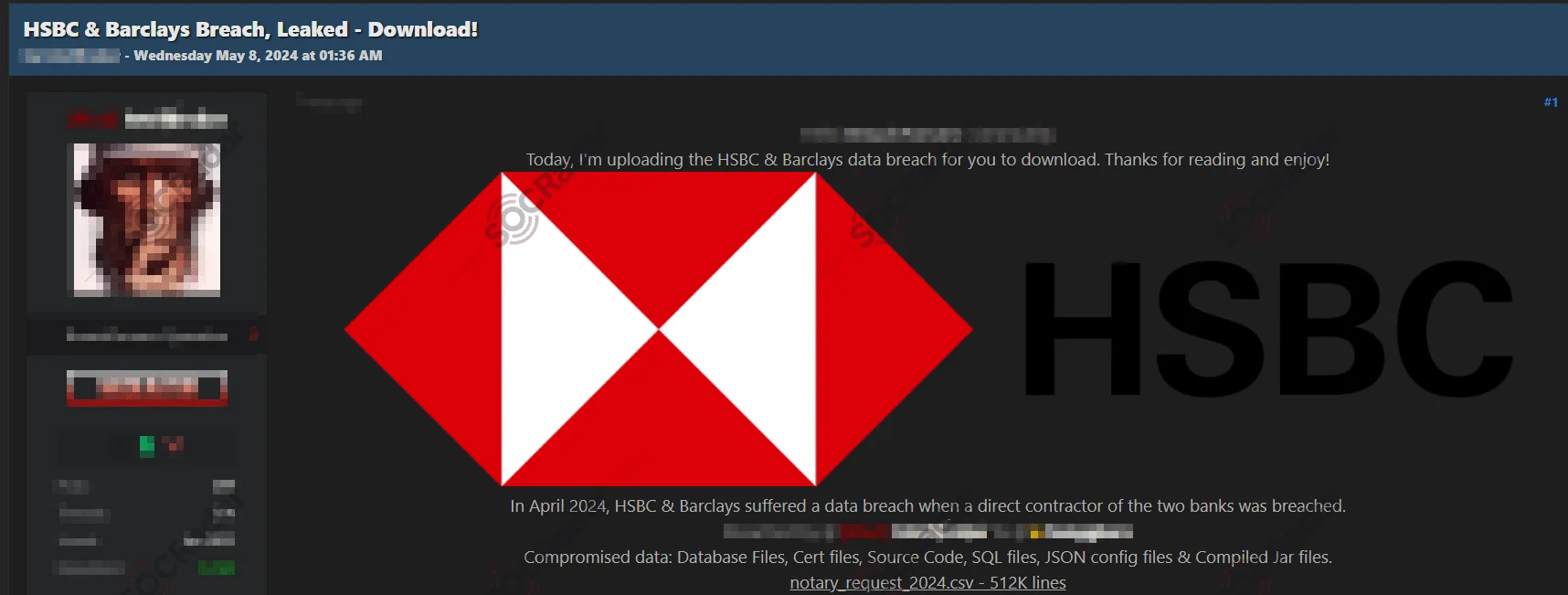
IntelBroker claims to have leaked HSBC and Barclays data
In May 2024, a month after the initial claim, IntelBroker released the data for free on the same forum, stating that a direct contractor of HSBC and Barclays was breached, compromising database files, certificate files, source code, SQL files, JSON config files, and compiled .jar files.
Alleged Data Leak of Truist Bank by ShinyHunters
In June 2024, multiple threat actors, including Sp1d3r, IC3, and ShinyHunters, claimed responsibility for leaking sensitive data allegedly belonging to Truist Bank.
Here’s the timeline of events:
June 11, 2024: Sp1d3r, a known threat actor, announced a breach involving Truist Bank, offering the stolen data for $1 million.
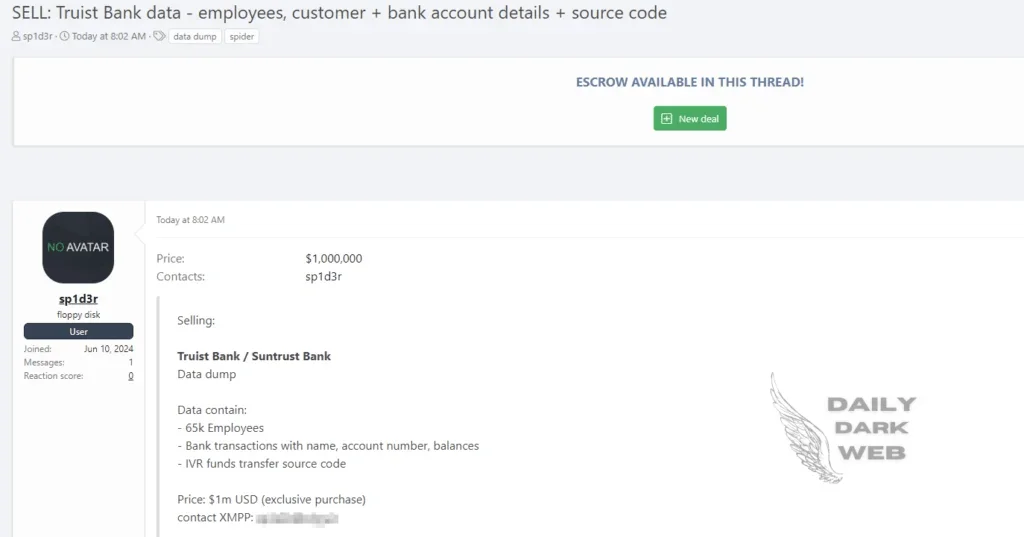
Sp1der’s statement
June 13, 2024: Truist Bank acknowledged a breach dating back to October 2023, but clarified it was unrelated to the Snowflake platform, despite initial rumors.
June 24, 2024: Another hacker forum post from IC3 claimed that all databases from the Truist breach would be sold for $75,000, with the group separate from both ShinyHunters and Sp1d3r.
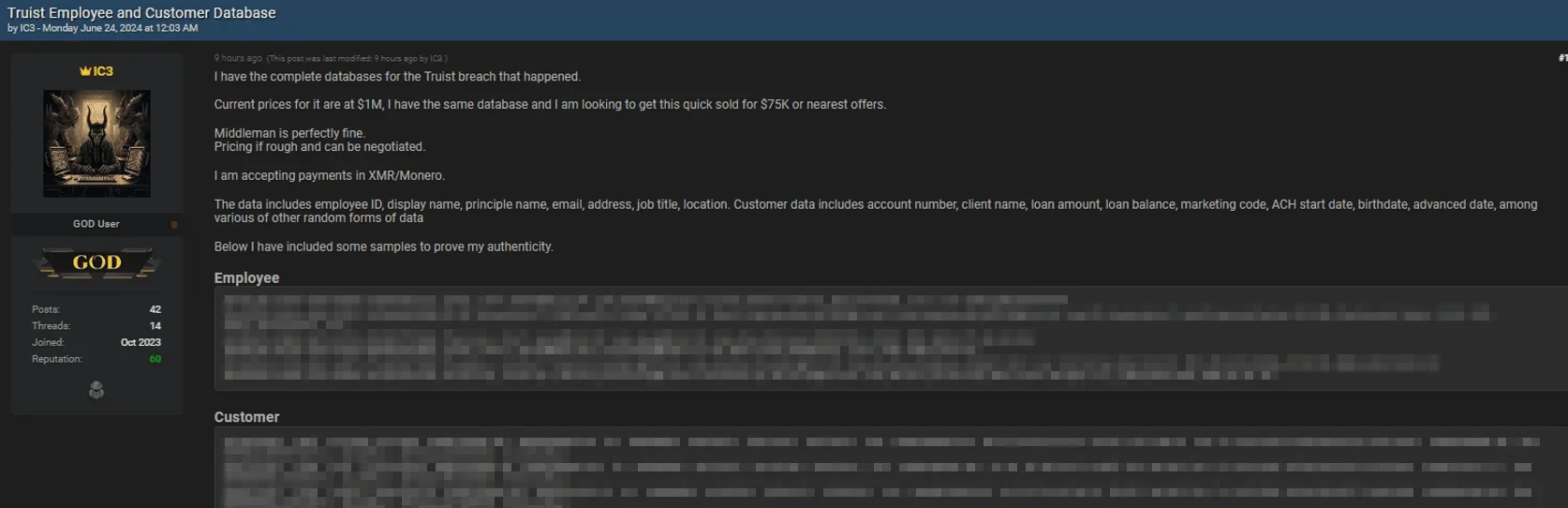
IC3 threat actor’s announcement
June 27, 2024: SOCRadar researchers discovered that ShinyHunters had leaked data related to Truist Bank on BreachForums. The exposed data included over 79,000 unique work email addresses, account balances, dates of birth, job titles, names, partial credit card data, and phone numbers of Truist Bank employees. Additionally, the leak included 65,000 employee records from IBM TRIRIGA, 22,900 records from Azure Active Directory (AAD), and bank transactions containing names, account numbers, balances, and IVR funds transfer source code.
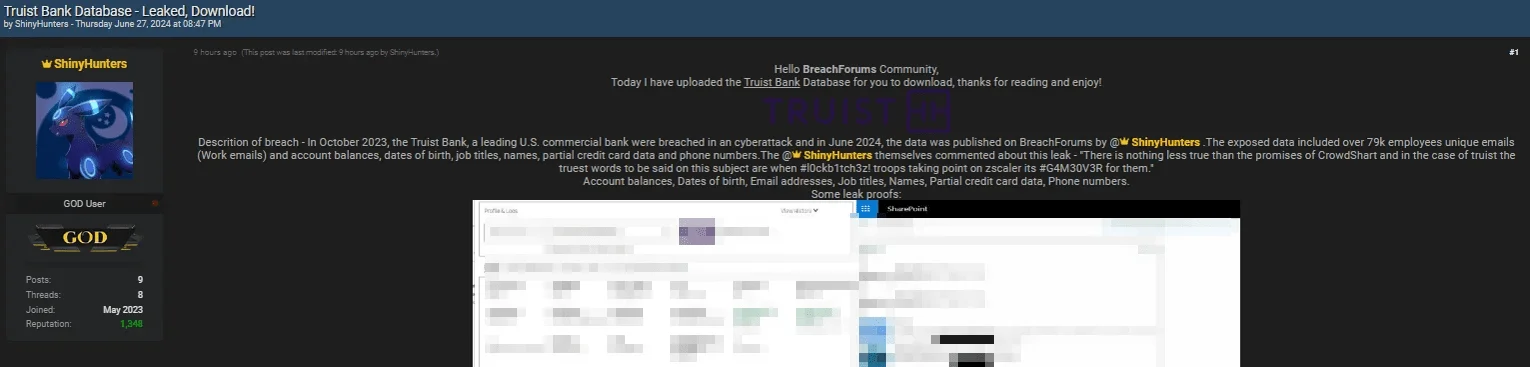
ShinyHunt3r’s statement
BidenCash Exposes 1.9 Million Credit Card Records
In December 2023 The SOCRadar Dark Web Team detected a significant breach involving BidenCash, a notorious carding market active since June 2022. This breach has resulted in the exposure of 1.9 million credit card details on a hacker forum.

BidenCash’s post on a popular Russian hacker forum
BidenCash has aggressively marketed its services across various hacking platforms, frequently releasing stolen credit card data to lure in more cybercriminals. These card details are typically harvested through malicious methods like website skimmers and infostealer malware.
To gain initial traction in 2022, BidenCash leaked 8 million lines of data, which included email addresses and about 6,700 credit cards. Later, in October 2022, they expanded their leaks to cover 1,221,551 credit card details.
By February 2023, BidenCash had further escalated its activities, leaking around 2.1 million credit card records on a Russian hacker forum. This pattern of increasing data breaches highlights the growing threat posed by the BidenCash marketplace.
In an era where cyber threats are constantly evolving, particularly targeting the finance industry, the importance of robust Dark Web monitoring cannot be overstated. The incidents involving IntelBroker, ShinyHunters, and BidenCash demonstrate the persistent risks and the need for continuous vigilance. Financial institutions must proactively monitor the Dark Web to detect, track, and mitigate these threats effectively.
SOCRadar Dark Web News






































