Threat Actor Profile: BianLian, The Shape-Shifting Ransomware Group
Nowadays, there is a rise in the number of ransomware groups with names that mean something. For example, Yanluowang is a deity in Chinese mythology, the god of death and the underworld judge. Some of the groups name themselves for behaving according to that meaning. One of them is BianLian.
As its name implies, BianLian (变脸), which is a reference to the traditional Chinese art of “face-changing”, is a shape-shifting cyber threat actor known for its agile adaptation and rapid evolution in its tactics, techniques, and procedures. Starting as a banking Trojan, it has swiftly transformed into a full-fledged ransomware group that operates at a global level.
Let’s delve into the BianLian Ransomware Group.
Who Is BianLian?
BianLian is a threat actor that runs a ransomware operation with the same name BianLian ransomware. It first appeared as an Android banking trojan in 2019. However, like its namesake, the traditional Chinese art of “face-changing,” BianLian has demonstrated remarkable adaptability, shifting its operations to focus on ransomware attacks and becoming a ransomware strain first observed in July 2022.

The group has shown a particular proclivity for evolving its tactics rapidly, enhancing its code, and diversifying its attack vectors to evade detection and counteract defensive measures.
How Does BianLian Attack?
BianLian employs a multi-stage attack methodology. Initial access to the target system is often achieved through spearphishing emails containing malicious attachments or links to compromised websites. Upon successful infiltration, the malware will communicate with its command and control (C2) server, downloading additional modules and tools to escalate its privileges and establish a persistent foothold in the compromised system.
- Initial Access: BianLian gains initial access to networks by leveraging compromised Remote Desktop Protocol (RDP) credentials, likely acquired from initial access brokers or via phishing.
- Command and Control(C2): The group implants a custom backdoor specific to each victim written in Go and install remote management and access software, such as TeamViewer, Atera Agent, SplashTop, and AnyDesk for persistence and command and control.
The group also creates and/or activates local administrator accounts and changes those account passwords.
- Defense Evasion: BianLian uses PowerShell and Windows Command Shell to disable antivirus tools, specifically Windows Defender and Anti-Malware Scan Interface (AMSI).
- Discovery: The group uses a combination of compiled tools, which they first download to the victim environment, to learn about the victim’s environment. These tools include Advanced Port Scanner, SoftPerfect Network Scanner (netscan[.]exe), SharpShares, and PingCastle.
BianLian also uses native Windows tools and Windows Command Shell to query currently logged-in users, query the domain controller to identify all groups, accounts in the Domain Admins and Domain Computers groups, all users in the domain, retrieve a list of all domain controllers and domain trusts, and identify accessible devices on the network.
- Credential Access: BianLian uses valid accounts for lateral movement through the network and to pursue other follow-on activity. To obtain the credentials, they use Windows Command Shell to find unsecured credentials on the local machine, harvest credentials from the Local Security Authority Subsystem Service (LSASS) memory, download RDP Recognizer to the victim system, and attempt to access an Active Directory domain database (NTDS.dit).
- Persistence and Lateral Movement: BianLian uses PsExec and RDP with valid accounts for lateral movement. Prior to using RDP, they used Command Shell and native Windows tools to add user accounts to the local Remote Desktop Users group, modified the added account’s password, and modified Windows firewall rules to allow incoming RDP traffic.
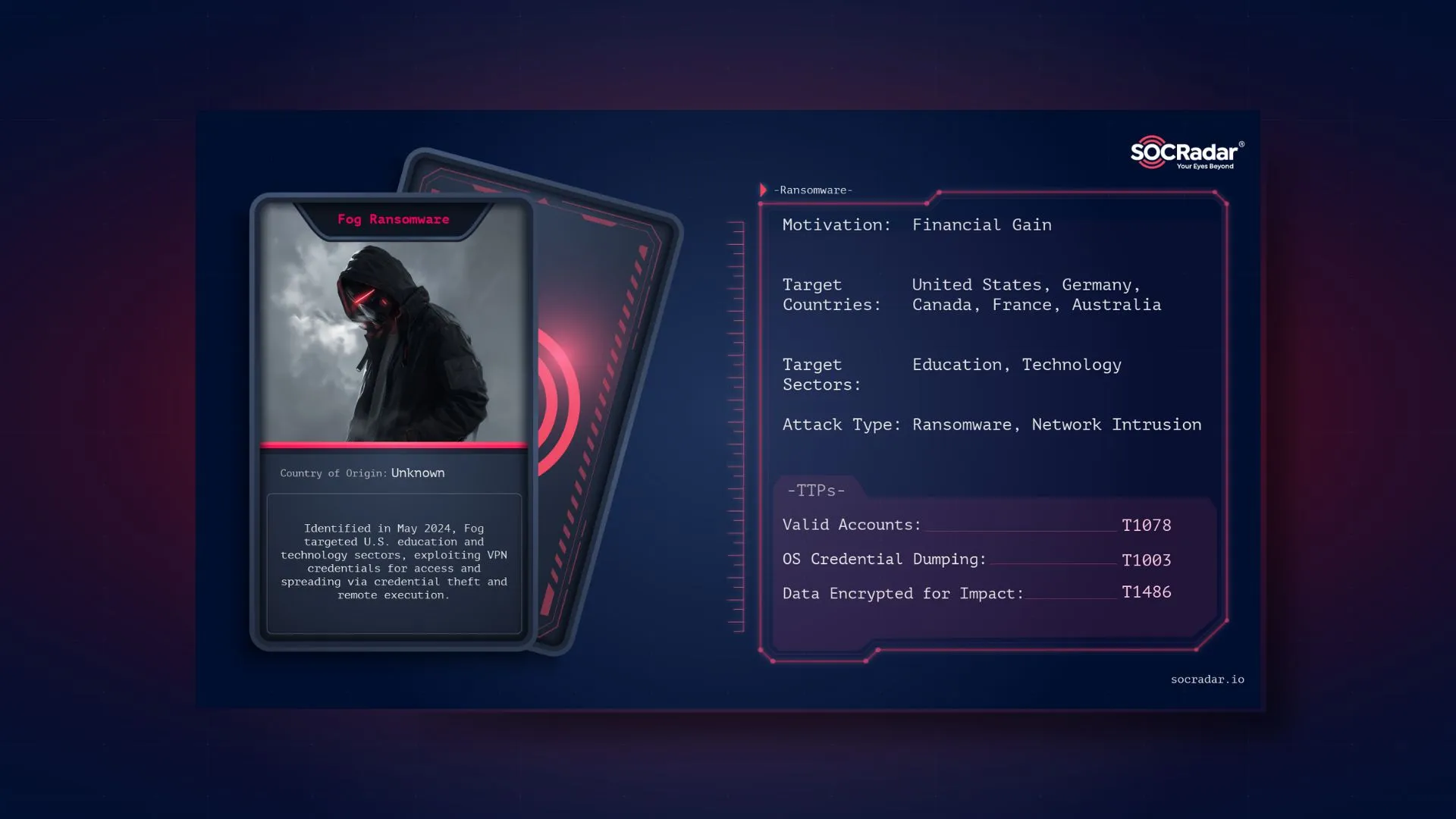
BianLian ransomware encrypts the victim’s data, rendering it inaccessible, and then demands a ransom payment to restore access.
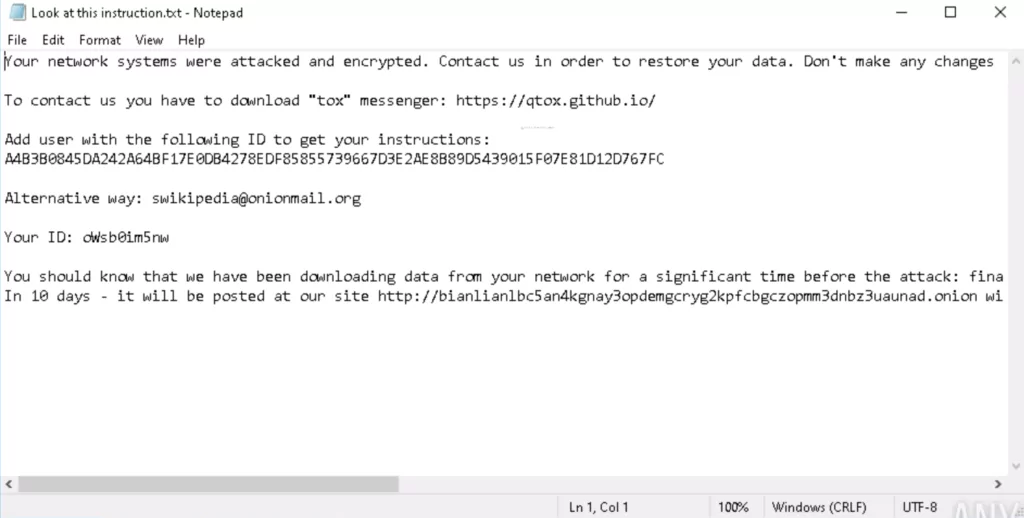
The group operated following a double-extortion model in which they encrypt data after exfiltration; since the decryptor released by Avast is working, the group switched to an exfiltration-based model to guarantee receiving the ransom payment.
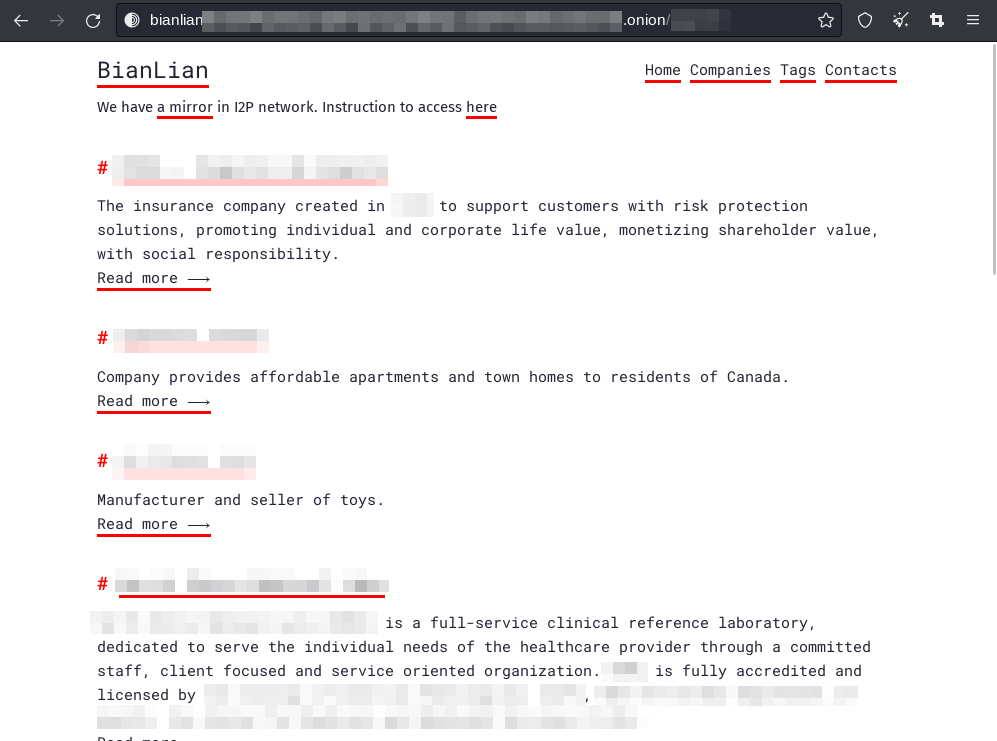
Quick Look at BianLian’s Tor Site
BianLian ransomware group shares their victim announcements on their own TOR website. When the page first opens, we are greeted by certain headings. These headings are, respectively: Home, Companies, Tags and Contacts. Below the headings, the group’s most recent victim announcements are listed.
The contact page contains the Tox messenger address and onionmail extension contact addresses that the group used and told to download in the ransom note.

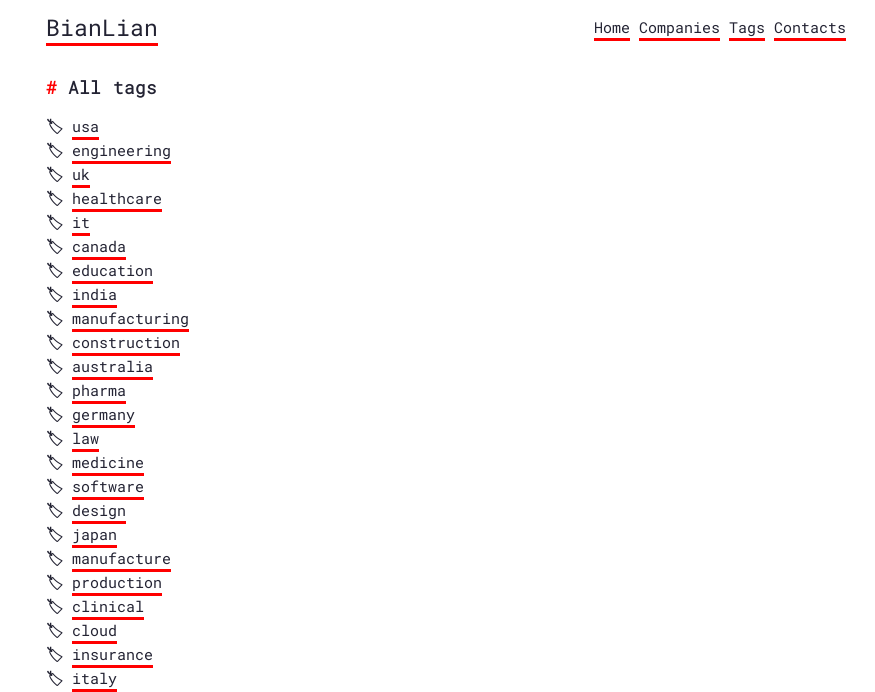
On the Tags page, there is a list of the tags in the victim announcement posts the group has made so far.
If you look at a recent victim announcement page made by the group, the extension of the company that was attacked, explanations about the company and the files that were leaked, if any, are listed respectively.
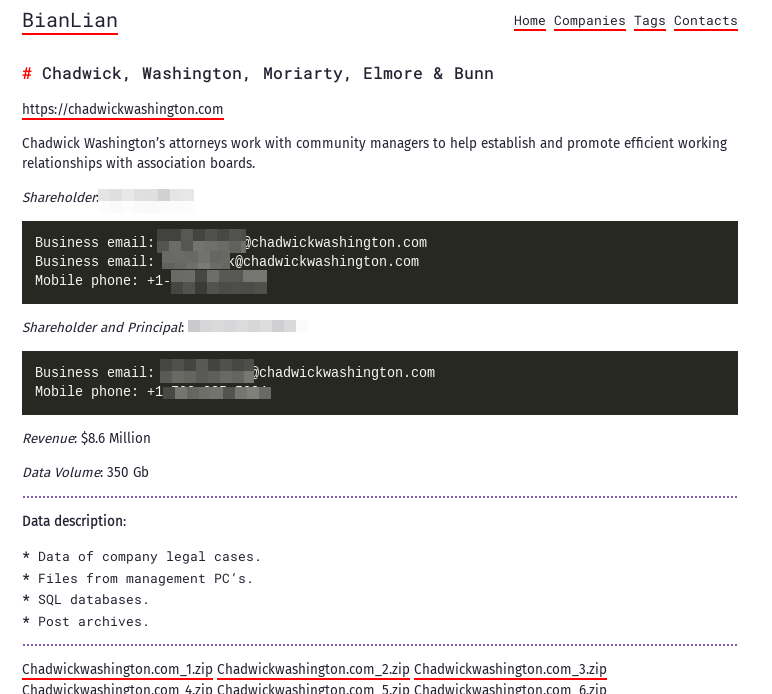
Findings on BianLian Ransomware:
We made our analysis using the SHA256 hash “eaf5e26c5e73f3db82cd07ea45e4d244ccb3ec3397ab5263a1a74add7bbcb6e2” on Anyrun.
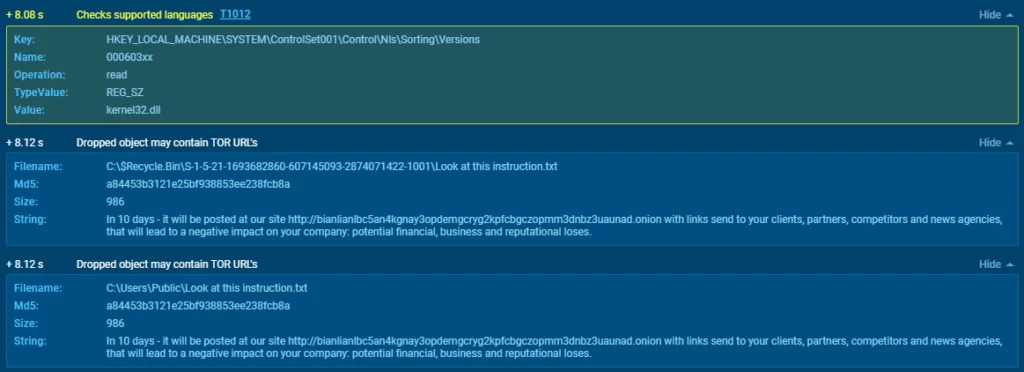
When the program first runs, it checks the languages supported by the environment it runs in (T1012). It starts by dropping the ransom note, which contains the Tox messenger ID, Tox messenger GitHub link, victim ID, and the TOR address of the group, to all directories. Since the software communicates via OfficeClickToRun[.]exe, it also leaves this file in the word startup folder (T1562.006).
We observed malware’s use of OfficeClickToRun[.]exe by analyzing another sample of BianLian with Sha-256 of “597C492A5AF56D935D360FCFD2C1E89928DDE492C86975F2C5CC33EC90B042CE”
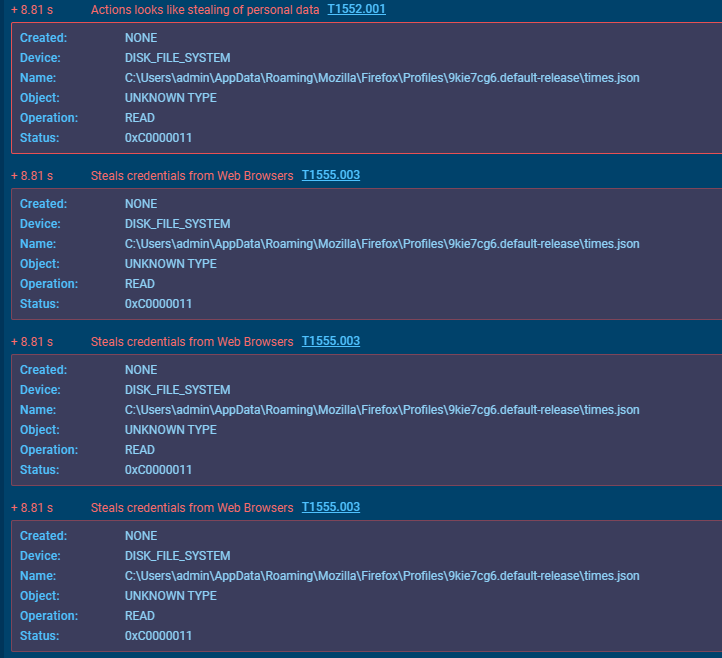
We observed that after a certain period of time, it started stealing activities. First, it steals Web browser information; in our analysis we observed that Mozilla Firefox Profiles folder’s times.json, addons.json, cookies.sqlite, handlers.json, content-prefs.sqlite (T1552.001), container.json(T1555.003) files has been read by the malware. We can suppose that the malware also stole personal data during this process.
After all ransom note dropping and stealing activities are completed, it encrypts the files and changes their extensions to .bianlian (T1486).
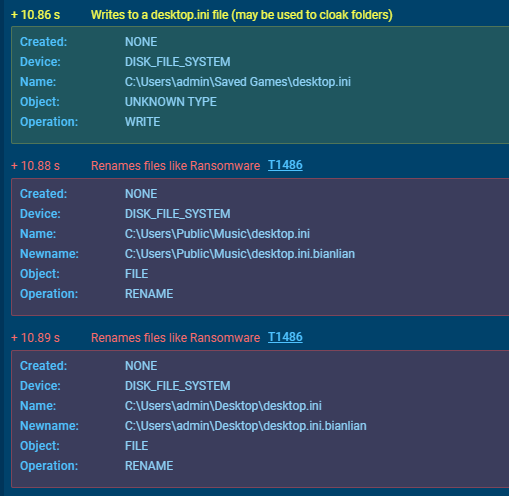
Finally, the program runs CMD[.]exe (T1059.003) and executes the following command in the command line:
“cmd /c del C:UsersadminAppDataLocalTempeaf5e26c5e73f3db82cd07ea45e4d244ccb3ec3397ab5263a1a74add7bbcb6e2[.]exe”
and we see it leaves various files; some of these files are named: “metamodel.jfm.bianlian”, “edb.log.bianlian” and “the-real-index.bianlian”.
According to the information we got from Anyrun’s text report:
Malicious activities of BianLian are:
- Writes file to Word startup folder,
- Renames files like Ransomware,
- Drops executable file immediately after starts,
- Actions look like stealing of personal data,
- Steals credentials from Web Browsers.
Suspicious activities are:
- Checks supported languages,
- Creates files like Ransomware instructions,
- Creates files in the program directory,
- Writes to a desktop.ini file (may be used to cloak folders),
- Starts CMD.EXE for commands execution,
- Drops a file with a compile date too recent,
- Reads the computer name,
- Executed via COM,
- Creates files in the user directory,
PE and DOS header information:
The IP addresses that make the suspicious connections observed in this analysis are:
- 40.127.240[.]158 (Port 443)
- 20.31.108[.]18 (Port 443)
- 20.54.89[.]15 (Port 443)
When we query the first IP address (40.127.240[.]158) on VirusTotal, we see no suspicious warnings at first glance, and the IP address looks clean according to the VirusTotal. After, when we examine the comments tab, we conclude that it is also used by other threat actors, such as Medusa Locker. In addition, this IP address was also mentioned in our Dark Web Profile: Vice Society Ransomware Group blog.
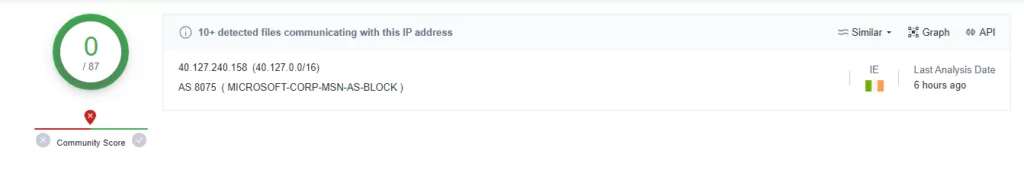
When we query 20.31.108[.]18, we see that it looks clean but is used in various stealer activities. And lastly, when we query 20.54.89[.]15, we see that this IP address is also marked as malicious.
Anyrun’s and some of the other BianLian samples’ IoCs we have gathered on our platform are in the appendix section of the article.

What are the Targets of BianLian?
BianLian has a broad attack range. Initially, individual users were the primary targets when it functioned as a banking trojan. With the evolution into more advanced ransomware, the group expanded its target sectors to include businesses, governmental organizations, healthcare facilities, and educational institutions.
Targeted Sectors
The group appears to be particularly interested in sectors with sensitive data and the financial capacity to pay large ransoms. These sectors include:
- Financial institutions
- Government
- Professional Services
- Manufacturing
- Media & Entertainment
- Healthcare
- Education
- Law
Targeted Countries
Geographically, the group seems to operate globally, but a higher concentration of attacks is reported in North America and Europe. This might suggest that BianLian is focusing on regions with high economic value.
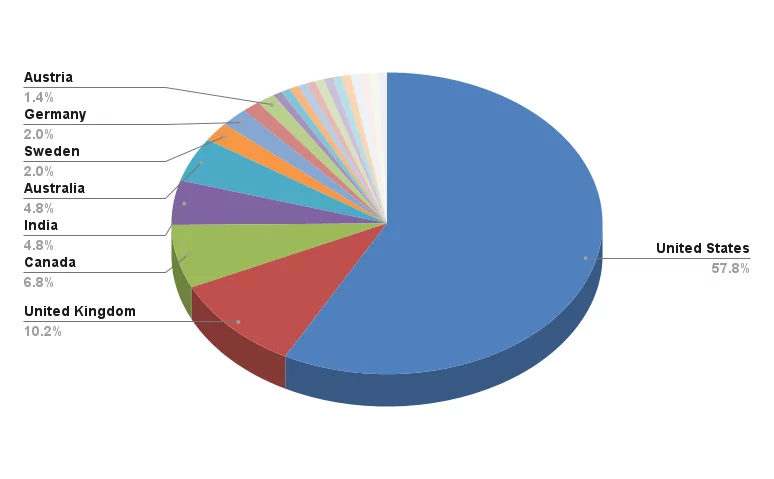
According to SOCRadar’s observations, BianLian mostly targeted organizations based in the United States with about 60% rate. United Kingdom (10.2%) and Canada (6.8%) follows as most targeted victims by BianLian.

What Are The Latest Activities About BianLian?
Recently, BianLian has been responsible for a series of high-profile attacks. For instance, the Cybersecurity and Infrastructure Security Agency (CISA) reported one of the group’s most notable operations in their advisory notice, where they identified BianLian’s shift from simple ransomware to an extortion-based strategy.
DXC Technology also published a report detailing a rapid increase in BianLian’s ransomware activities, emphasizing the group’s effectiveness and growth rate.
Attacks of BianLian Over Time
Looking at the attack frequency of the group, it is seen that it was more active in 2023:
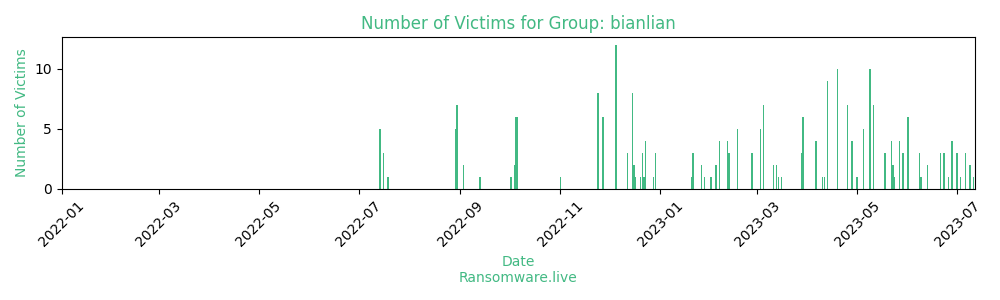
When we divide their attacks into 2022 and 2023 and look at them in detail:
2022
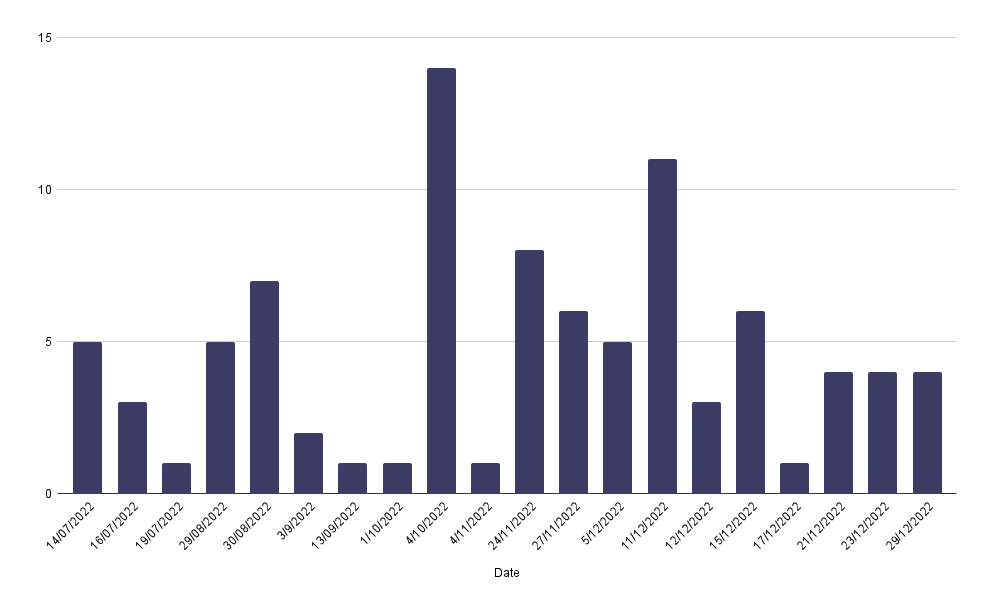
In 2022, the group is more active in early October and throughout December.
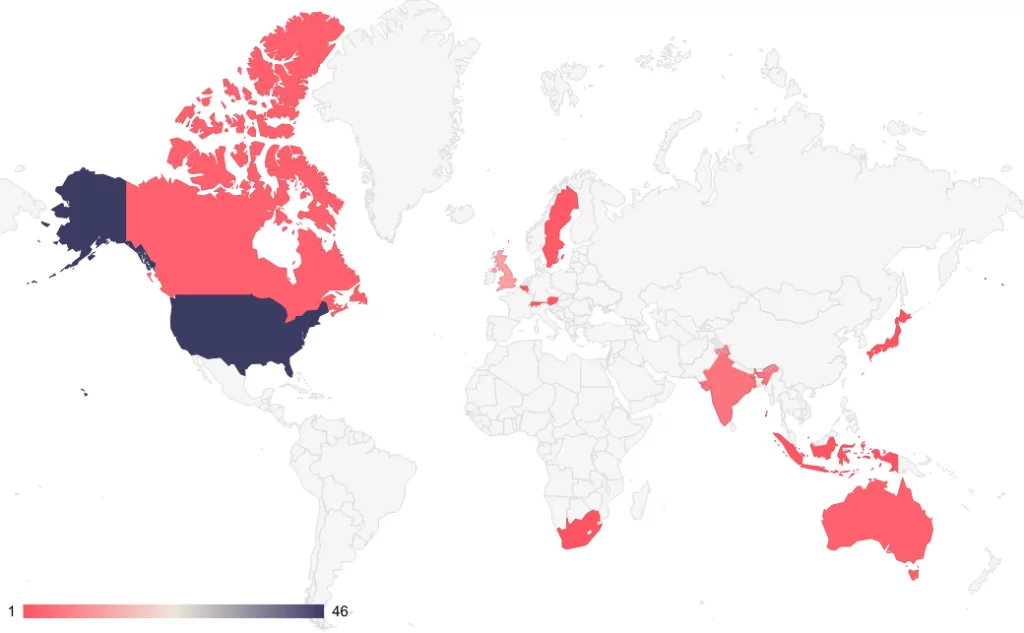
Looking at the details of the attacks, it is seen that the majority of the victims are from the United States.
2023
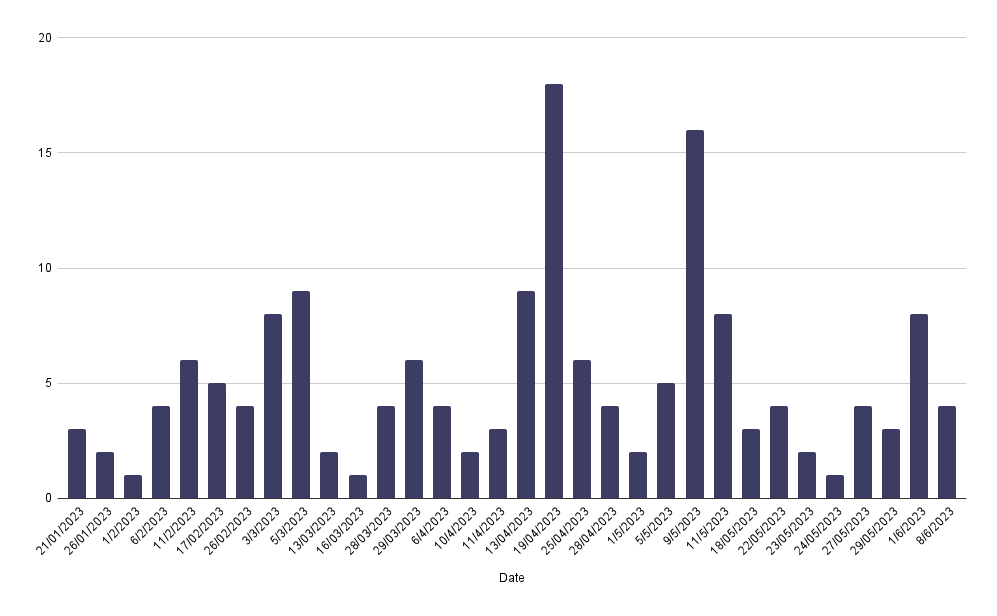
Looking at the details of 2023, it is seen that the group was much more active than in 2022 and the number of attacks increased in April and May.
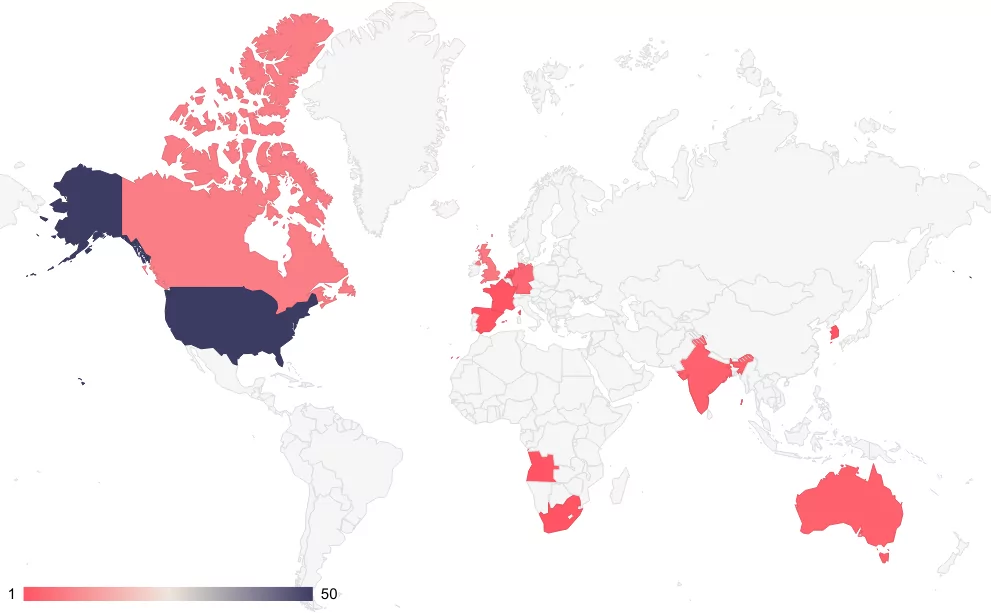
Looking at the details of the attacks, it is seen that the majority of the victims are from the United States, just like in 2022.
What Are the Group’s Latest Attacks?
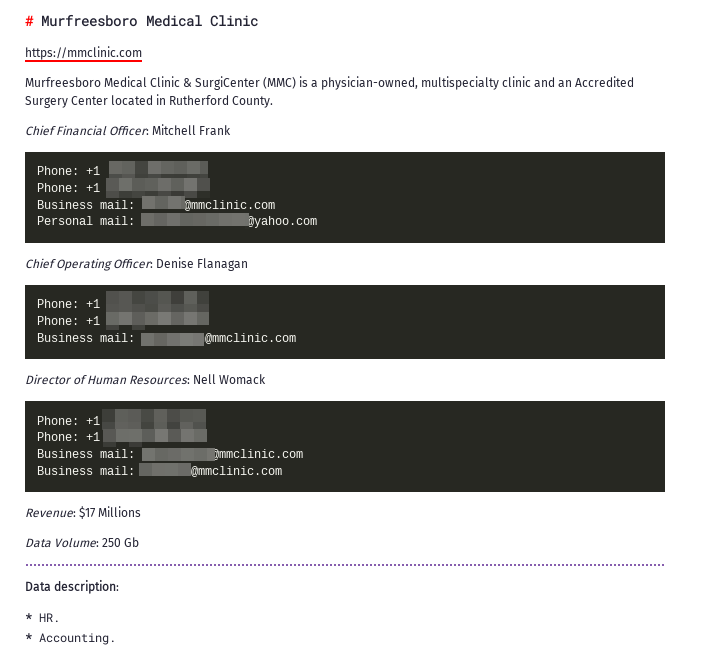
Murfreesboro Medical Clinic:
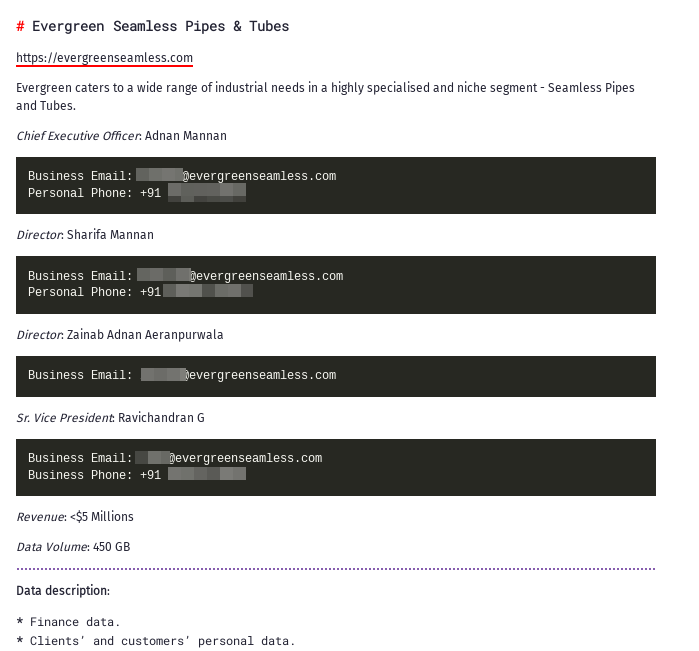
Evergreen Seamless Pipes & Tubes:
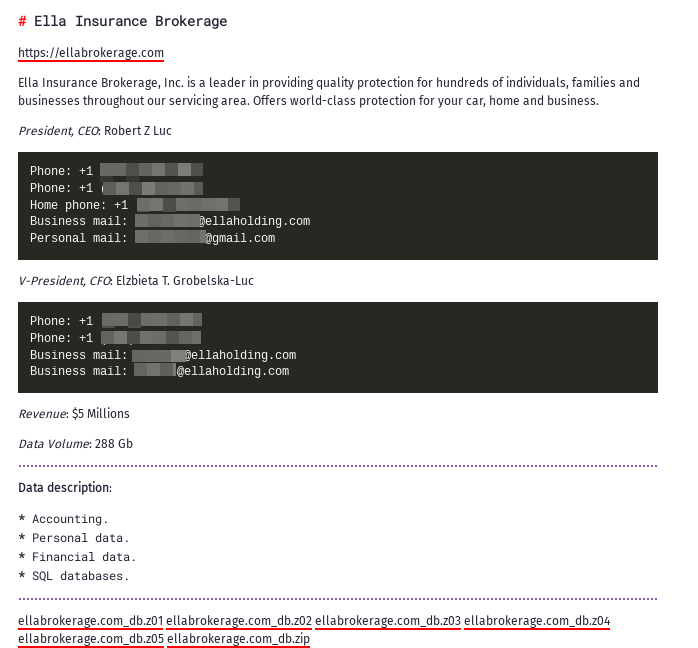
Ella Insurance Brokerage:
Unknown Victims:
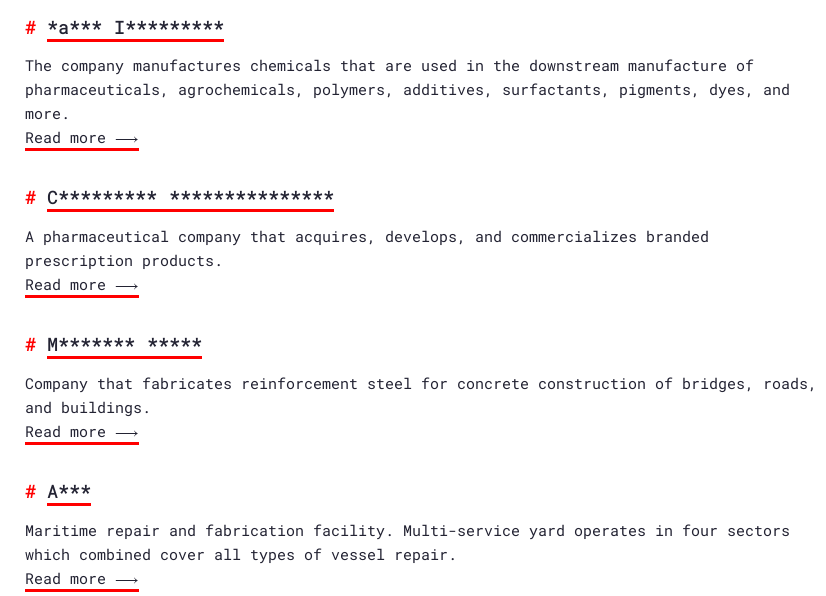
In some of the attacks, the group does not give the names of the victims in full and covers them with asterisks. The reason for this may be that negotiations with the victim are ongoing, but they have developed such a method to cause fear in the victim.

Conclusion
BianLian, borrowing its name from the Chinese art form involving quick changes of masks, represents a significant threat to various sectors around the world. With their evolving tactics, the group has demonstrated its adaptability, resilience, and cunningness. By transitioning from a primary focus on ransomware to an extortion-based approach, BianLian has effectively kept itself at the forefront of cyber threat discussions.
Their operations not only pose an immediate risk of data loss but also the long-term danger of reputational damage from data leaks. The threat they pose is both direct, through their cyberattacks, and indirect, by creating an environment of fear and uncertainty.
Security Recommendations Against BianLian
Defending against BianLian and similar cyber threats is a multi-layered task. Here are some recommendations:
Employee Training: Awareness is the key when it comes to cybersecurity. Adversaries generally exploit human error to gain initial access. As it is observed, BianLian is getting initial access using spearphishing attachments or links. Regularly conducting cybersecurity awareness training for employees and informing them about the latest phishing techniques and how to report suspected phishing attempts could eliminate most of the risk.
Regular Backups: Keep frequent backups of important data, and ensure that backups are not connected to the main network.
Use Strong Passwords: Use complex and unique passwords for each account. Consider using a password manager to store passwords securely. Also, implementing the MFA solution provides enhanced protection by layering multiple defenses against unauthorized access.
Keep Systems Updated: Regularly update all software and operating systems. This can help protect against vulnerabilities that threat actors like BianLian often exploit.
Monitor Network Traffic: BianLian shifted its business model to double-extortion lately. Monitoring network traffic closely for unusual data flows that could suggest a data breach can play a significant role in the prevention of any data loss.
Use Antimalware Solutions: Using antimalware software could detect and quarantine threats.
Incident Response Plan: Have a clear incident response plan in place. This can help minimize damage in the event of a breach.
It should be remembered that cybersecurity is not a one-time fix but an ongoing process. Constant vigilance and a proactive security approach are essential in fighting against groups like BianLian. When it comes to proactivity, Cyber Threat Intelligence comes to mind. Implementing CTI into business could help detect or prevent an incident before the risk has increased.
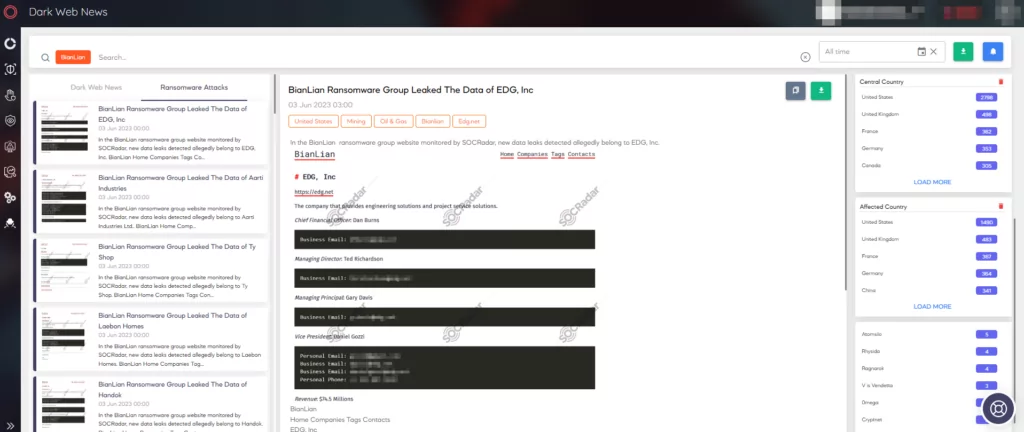
By using Ransomware News in the Dark Web News panel in the CTI module of SOCRadar, the latest announcements of BianLian can be followed.
Organizations can also use SOCRadar’s Attack Surface Management (ASM) panel to be aware of the current risks in their IT infrastructure.
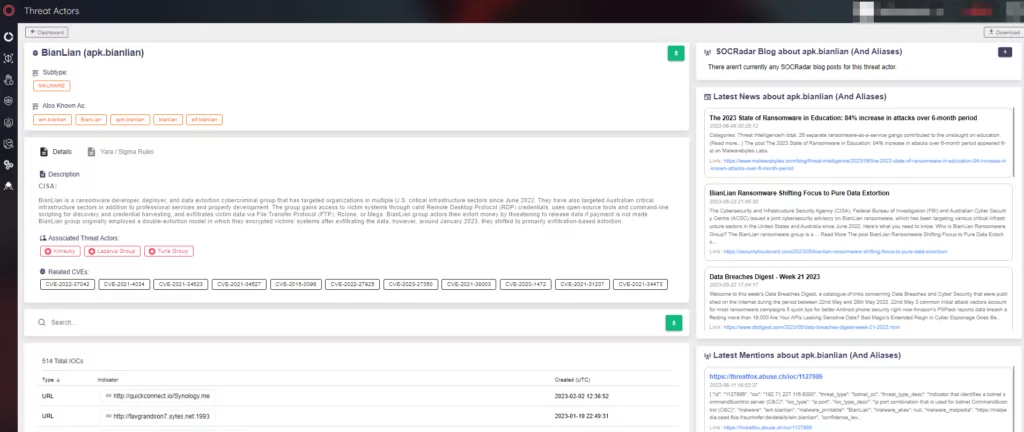
From the Threat Actor/Malware page, organizations can benefit from IoCs,YARA rules written for this threat actor, and learn about news/forum posts where this actor is mentioned.
MITRE ATT&CK TTPs Used by BianLian
| Techniques | ID |
| Resource Development | |
| Develop Capabilities: Malware | T1587.001 |
| Initial Access | |
| External Remote Services | T1133 |
| Phishing | T1566 |
| Privilege Escalation | |
| Valid Accounts | T1078 |
| Execution | |
| Command and Scripting Interpreter: PowerShell | T1059.001 |
| Command and Scripting Interpreter: Windows Command Shell | T1059.003 |
| Scheduled Task/Job | T1053 |
| Persistence | |
| Account Manipulation | T1098 |
| Create Account: Local Account | T1136.001 |
| Defense Evasion | |
| Modify Registry | T1112 |
| Impair Defenses: Disable or Modify Tools | T1562.001 |
| Impair Defenses: Disable or Modify System Firewall | T1562.004 |
| Credential Access | |
| Unsecured Credentials: Credentials In Files | T1552.001 |
| OS Credential Dumping: LSASS Memory | T1003.001 |
| OS Credential Dumping: NTDS | T1003.003 |
| Discovery | |
| Account Discovery: Domain Account | T1087.002 |
| Domain Trust Discovery | T1482 |
| File and Directory Discovery | T1083 |
| Network Service Discovery | T1046 |
| Network Share Discovery | T1135 |
| Permission Groups Discovery: Domain Groups | T1069.002 |
| Query Registry | T1012 |
| Remote System Discovery | T1018 |
| System Owner/User Discovery | T1033 |
| Lateral Movement | |
| Remote Services: Remote Desktop Protocol | T1021.001 |
| Collection | |
| Clipboard Data | T1115 |
| Command And Control | |
| Ingress Tool Transfer | T1105 |
| Remote Access Software | T1219 |
| Exfiltration | |
| Transfer Data to Cloud Account | T1537 |
| Exfiltration Over Alternative Protocol | T1048 |
| Exfiltration Over Web Service: Exfiltration to Cloud Storage | T1567.002 |
| Impact | |
| Data Encrypted for Impact | T1486 |
Appendix
IoCs of BianLian:
| IOC Type | IOC |
| URL | hxxp[:]//quickconnect[.]io/Synology[.]me |
| URL | hxxp[:]//favgrandson7[.]sytes[.]net:1993 |
| URL | hxxps[:]//fv9-2[.]failiem[.]lv/down.php?i=nvge8wkk3 |
| URL | hxxp[:]//cmnb9[.]cc |
| URL | hxxp[:]//45.15.156[.]210[:]8081 |
| IP | 45.92.156[.]105 |
| IP | 5.188.6[.]118 |
| IP | 40.127.240[.]158 |
| IP | 20.31.108[.]18 |
| IP | 20.54.89[.]15 |
| xxx@mail2tor[.]com | |
| swikipedia@onionmail[.]org | |
| CVE | CVE-2023-27350 |
| CVE | CVE-2022-37042 |
| CVE | CVE-2022-27925 |
| CVE | CVE-2021-4034 |
| CVE | CVE-2021-34523 |
| Hash | eaf5e26c5e73f3db82cd07ea45e4d244ccb3ec3397ab5263a1a74add7bbcb6e2 |
| Hash | f7a3a8734c004682201b8873691d684985329be3fcdba965f268103a086ebaad |
| Hash | de31a4125eb74d0b7cbf2451b40fdb2d66d279a8b8fd42191660b196a9ac468f |
| Hash | dda89e9e6c70ff814c65e1748a27b42517690acb12c65c3bbd60ae3ab41e7aca |
| Hash | da7a959ae7ea237bb6cd913119a35baa43a68e375f892857f6d77eaa62aabbaf |
For more IOCs, you can visit the Threat Actor/Malware page under the CTI module of SOCRadar XTI Platform.