
In the Crosshairs: Top 10 Threat Actors Targeting the USA
As the digital landscape continues to evolve, the United States finds itself at the forefront of emerging cybersecurity challenges. With its critical infrastructure, extensive government networks, and vibrant economy, the nation remains a prime target for a myriad of cyber threats. From state-sponsored actors seeking to undermine national security to sophisticated cybercriminal organizations aiming to exploit vulnerabilities for financial gain, the USA’s threat landscape is diverse and complex.
Since the beginning of 2023, SOCRadar has identified 3956 distinct posts on the dark web. Furthermore, a total of 2710 ransomware attacks have been detected, with 2436 of these attacks targeting the United States as their primary objective. All of these data have been carefully examined to identify the top 10 threat actors targeting the United States.
SOCRadar Dark Web News module
As SOCRadar, we delve into the top 10 threat actors that pose significant risks to the USA in this report; exploring their tactics, targets, and potential impact on the nation’s cybersecurity posture. Through detailed analysis and insights, we aim to provide a comprehensive understanding of the evolving cyber threats facing the USA and the urgent need for robust cybersecurity measures to mitigate these risks.
Most Targeted Industries in USA
The threat landscape in the United States is shaped by a myriad of factors, including the industries that are most frequently targeted by top threat actors. Recent data reveals a concerning trend, with the Information Industry emerging as the primary focus of malicious activities, accounting for 23.79% of all cyber attacks. Following closely behind are the Finance and Insurance industry, targeted at a rate of 15.67%, and the Retail Trade Industry, which comprises 13.41% of the attacks.
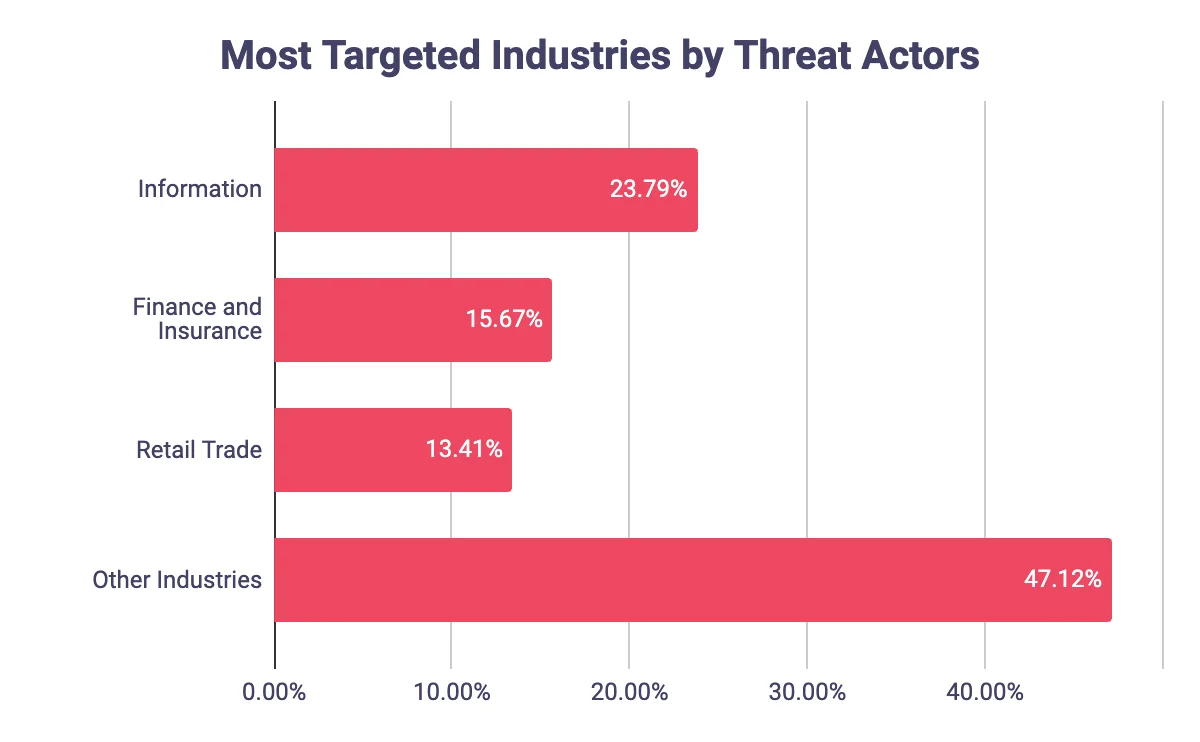
Graph of the industries most targeted by threat actors
The remaining industries collectively constitute 47.12% of the threat landscape, encompassing a diverse range of industries such as Public Administration, Manufacturing, Electronic Shopping and Mail-Order Houses, Professional, Scientific, and Technical Services, and Healthcare and Social Assistance. This comprehensive analysis sheds light on the industries most vulnerable to cyber threats, highlighting the urgent need for enhanced cybersecurity measures to protect critical infrastructure and sensitive data.
Most Common Dark Web Threat Categories
The Dark Web serves as a thriving hub for various cyber threats, with threat actors leveraging its anonymity to engage in illicit activities. Recent data analysis sheds light on the most common threat categories observed on the Dark Web, revealing Public Data Sharing as the predominant category, constituting 49.10% of all observed activities. Following closely behind is the Selling Compromised Data category, accounting for 47.19% of the threat landscape. Hack Announcements trail behind at 3.48%, while the remaining 0.23% comprises other miscellaneous categories. This comprehensive overview underscores the pervasive nature of cyber threats on the Dark Web and the critical importance of proactive cybersecurity measures to combat them.
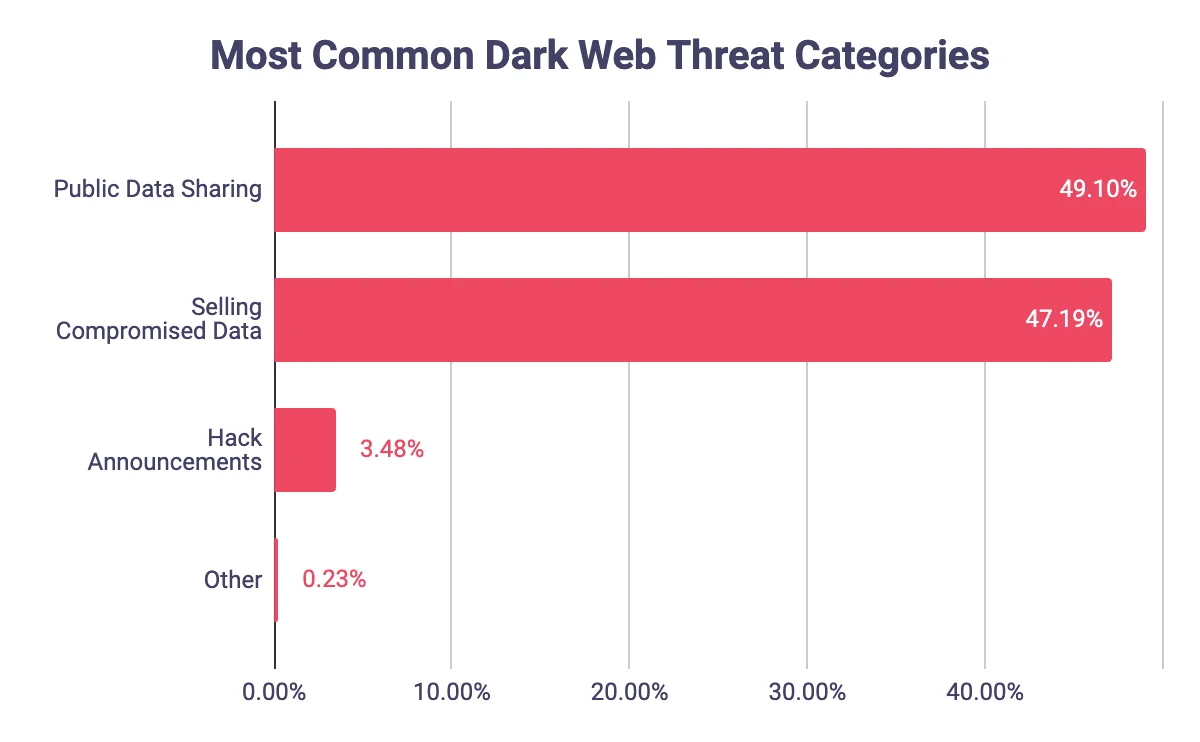
Graph of the most common dark web threat categories
The Aftermath of Ransomware Attacks
Recent analysis reveals that the majority of ransomware attacks result in Victim Announcements, comprising 78.61% of the total share types. Meanwhile, Data Exposure accounts for the remaining 21.39%, indicating a significant threat to sensitive data. These findings underscore the urgent need for robust cybersecurity measures to mitigate the risks posed by ransomware attacks.
Based on this data, we can infer that in the majority of ransomware attacks, the demanded fee is paid by the victim to the attacker. This highlights the critical need for enhanced cybersecurity measures to combat the prevalent threat posed by ransomware attacks and safeguard sensitive data from exploitation.
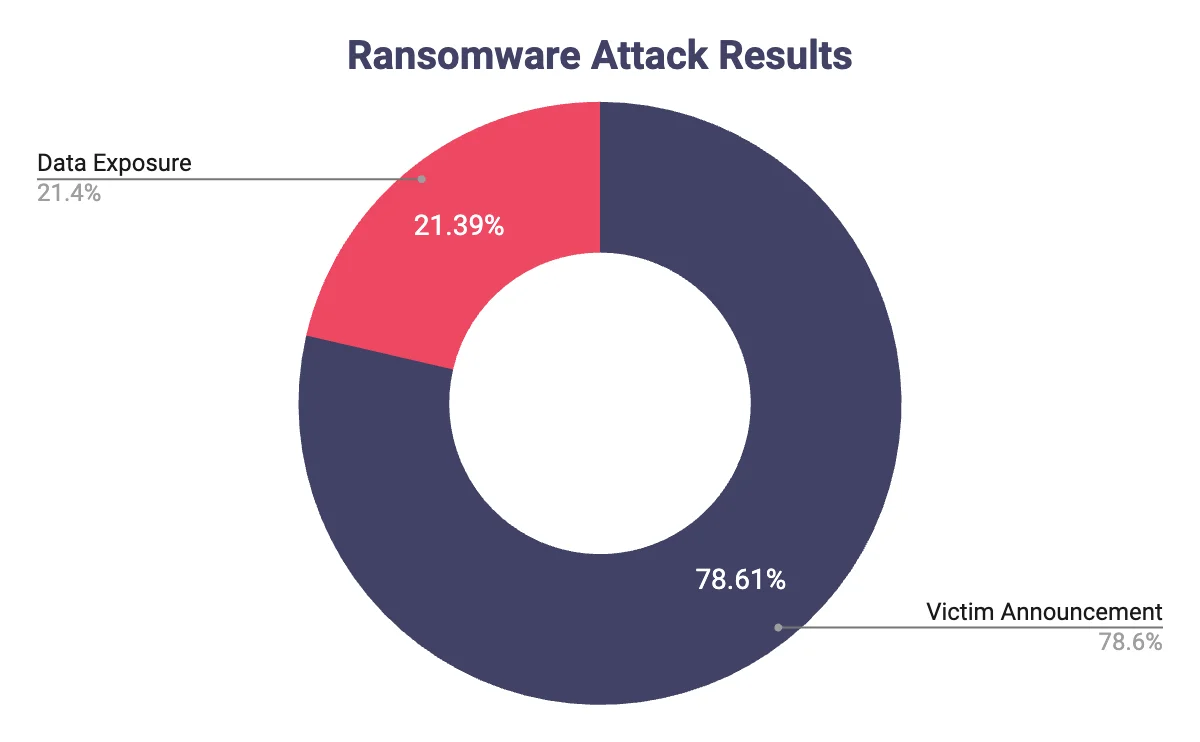
Ransomeware attack results analysis
After analyzing the statistical insights and graphical representations, we now delve into the profiles of the Top 10 Threat Actors Targeting the United States of America. In this section, we provide concise summaries of each threat actor’s tactics, objectives, and notable activities.
Top 10 Threat Actors Targeting United States of America
Lockbit 3.0:
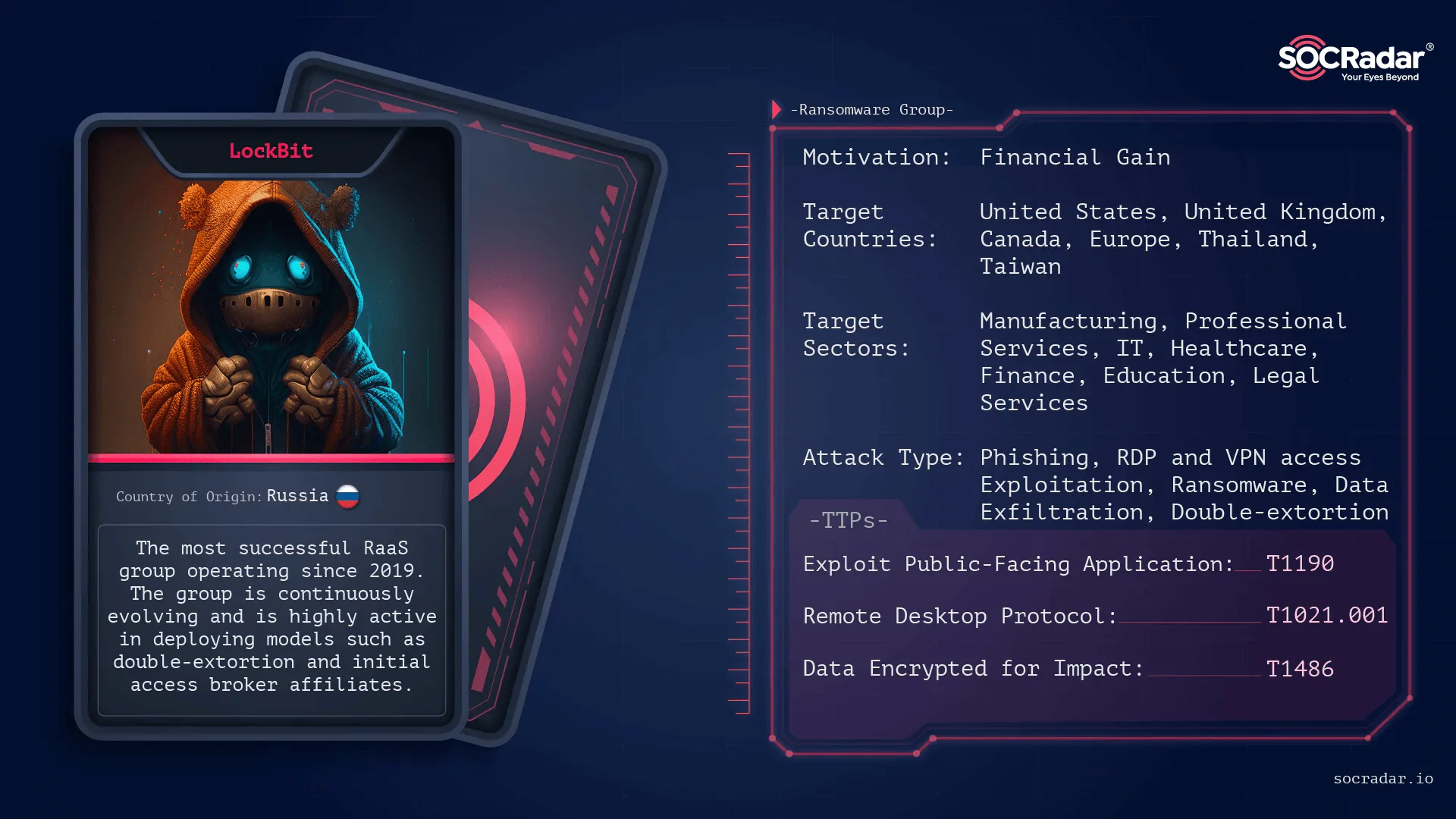
Threat Actor Card of Lockbit 3.0 Ransomware Group
LockBit 3.0, a successor to LockBit and LockBit 2.0, operates as a Ransomware-as-a-Service (RaaS) group. Since January 2020, LockBit has shifted to an affiliate-based model, employing various tactics to target businesses and critical infrastructure organizations. They are known for employing strategies like double extortion and initial access broker affiliates, as well as recruiting insiders and hosting hacker recruitment contests. With over 1,500 victim announcements on the SOCRadar platform, LockBit emerged as the most active ransomware group in 2022 following Conti’s shutdown. As of the first quarter of 2023, they remain the most prolific group, boasting over 300 announced victims.
For more detailed information about the Lockbit 3.0 Ransomware Group, you can visit our blog post.
ALPHV Blackcat:

Threat Actor Card of ALPHV BlackCat Ransomware Group
BlackCat, also referred to as ALPHV, has gained prominence as a ransomware entity pioneering the adoption of Rust, a cross-platform programming language facilitating seamless customization of malware across diverse operating systems, including Windows and Linux. Leveraging Rust’s capabilities, the group has effectively eluded detection measures while proficiently encrypting victims’ files. This strategic employment of Rust enables the group to target multiple operating systems and circumvent security protocols unequipped to scrutinize Rust-based malware.
For more detailed information about the ALPHV BlackCat Ransomware Group, you can visit our blog post.
Cl0p:

Threat Actor Card of Cl0p Ransomware Group
Clop, also referred to as “Cl0p,” stands as a cybercriminal entity recognized for its sophisticated extortion tactics and widespread dissemination of malware across the globe. The word clop comes from the Russian word “klop,” which means “bed bug,” a Cimex-like insect that feeds on human blood at night (mosquito). A distinguishing feature of Cl0p is the string “Don’t Worry C|0P” found in the ransom notes.
With a track record of extorting over $500 million in ransom payments, the group focuses on major organizations on a global scale. Gaining infamy in 2019, Clop has executed notable attacks, employing extensive phishing initiatives and advanced malware to breach networks and coerce ransom payments, leveraging the threat of data exposure if demands remain unmet.
For more detailed information about the Cl0p Ransomware Group, you can visit our blog post.
Play:
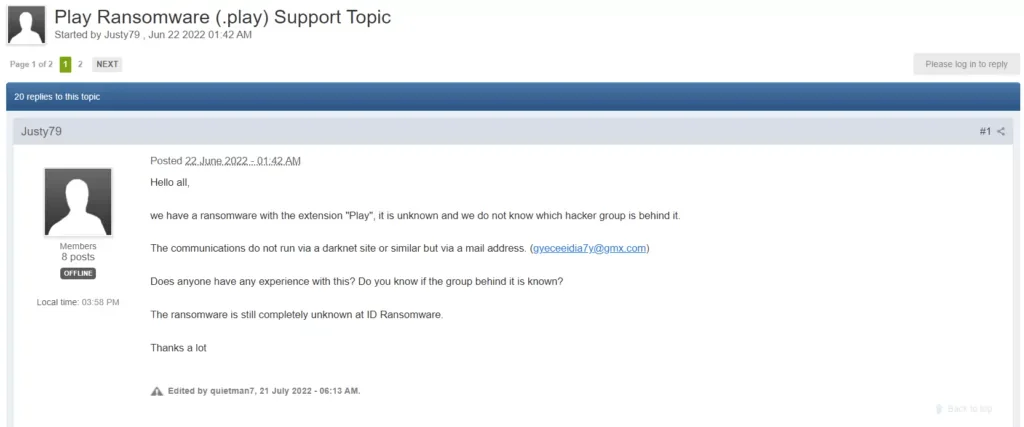
Play Ransomware First Seen
On June 22, 2022, a user in the BleepingComputer forum reported encrypted files with the extension “Play,” which subsequently led Trend Micro to publish an analysis article on the new ransomware variant, Play Ransomware. While primarily targeting the Latin American region, Brazil is notably at the top of the list. Despite appearing to be a new ransomware group, their identified Tactics, Techniques, and Procedures (TTPs) bear resemblance to those of the Hive and Nokayawa ransomware families. One of the shared behaviors is the use of AdFind, a command-line query tool capable of collecting information from Active Directory.
The Play Ransomware group employs various methods to gain initial access to an organization’s network, including the use of known valid accounts, exposed RDP servers, and exploiting FortiOS vulnerabilities CVE-2018-13379 and CVE-2020-12812. Once access is gained, they utilize “lolbins” binaries, commonly used by ransomware groups, as part of their attack arsenal.
Distribution of executables within the internal network occurs through Group Policy Objects, followed by the execution of scheduled tasks, PsExec, or wmic. Upon achieving full access, they proceed to encrypt files with the “.play” extension.
Researchers have identified the Play Ransomware group as the first threat actor to employ intermittent encryption, a technique aimed at better evading detection by employing partial encryption on systems that rely on static analysis to detect ransomware infections. Intermittent encryption involves encrypting chunks of 0x100000 bytes based on the file size.
For example,
- files less than or equal to 0x3fffffff bytes are encrypted in two chunks,
- files less than or equal to 0x27fffffff bytes are encrypted in three chunks.
Observations revealed that a sample encrypted every other 0x100000 byte chunk until the end of the file, with the non-encrypted chunks consisting solely of null characters, making them visually distinguishable from encrypted chunks.

Partial content of a file encrypted by PLAY (Source: SentinelOne)
For more detailed information about the Cl0p Ransomware Group, you can visit our blog post.
Black Basta:
Black Basta, a prominent Ransomware-as-a-Service (RaaS) operation, emerged in early 2022, swiftly establishing itself as one of the most active threat actors globally. Within its initial months, Black Basta targeted 19 significant enterprise victims and over 100 confirmed victims, focusing on organizations in the US, Japan, Canada, the UK, Australia, and New Zealand. Unlike indiscriminate attacks, Black Basta employs highly targeted strategies, leveraging double extortion tactics to encrypt critical data and servers while threatening to expose sensitive information on its public leak site.
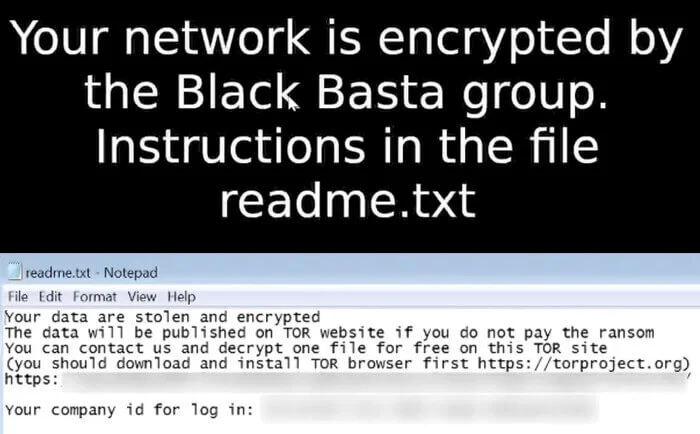
Black Basta Ransom Note (Source: TripWire)
Initial access for Black Basta attacks typically begins with sophisticated spear-phishing campaigns. By April 2022, the group expanded its operations by openly seeking to purchase access to corporate networks, sharing profits with affiliated Initial Access Brokers (IABs). Once inside a target’s network, Black Basta utilizes various methods to escalate privileges and move laterally, including leveraging tools like QakBot stealer, MimiKatz, and exploiting vulnerabilities such as ZeroLogon and PrintNightmare.
For command and control over infected systems, Black Basta employs a combination of Cobalt Strike Beacons, SystemBC for C2 proxy, and the Rclone tool for data exfiltration. The encryption phase involves disabling antivirus software, remotely executing encryption payloads via PowerShell, and eliminating system shadow copies. With an evolved encryption module, Black Basta employs advanced obfuscation techniques and the XChaCha20 algorithm for symmetric encryption, enhancing its ability to evade detection by endpoint security products.
For more detailed information about the Black Basta Group, you can visit our blog post.
BianLian:

Threat Actor Card of BianLian Ransomware Group
Named after the traditional Chinese art of “face-changing,” BianLian (变脸) embodies the essence of agility and transformation in the cyber threat landscape. Originally emerging as an Android banking trojan in 2019, BianLian swiftly transitioned into a formidable ransomware group, showcasing its ability to adapt and evolve rapidly.
BianLian’s evolution culminated in the creation of the BianLian ransomware, marking its foray into the realm of ransomware operations on a global scale since July 2022. Employing sophisticated tactics akin to its namesake, BianLian demonstrates a knack for shape-shifting its strategies to stay ahead of defenses and maximize its impact.
Using a multi-faceted approach, BianLian gains initial access to target systems through spearphishing emails containing malicious attachments or links to compromised websites. Once inside, the ransomware communicates with its command and control (C2) server, facilitating the deployment of additional modules and tools to elevate privileges and establish a persistent presence within the compromised environment.
For more detailed information about the BianLian Ransomware Group, you can visit our blog post.
Akira:
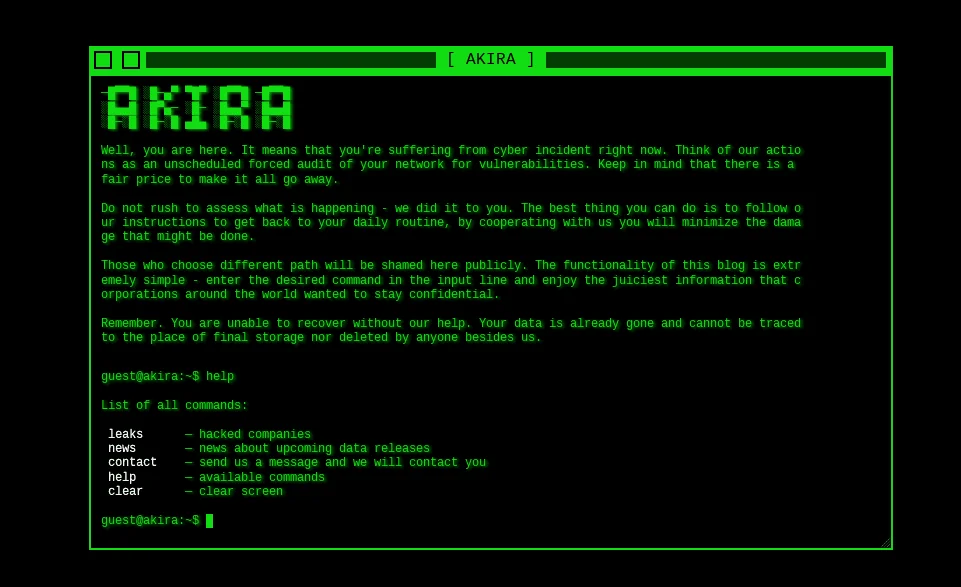
Akira Ransomware Note (Source: Truesec)
The Akira ransomware made its debut in March 2023, focusing its attacks primarily on businesses located in the United States and Canada. Featuring a distinct retro aesthetic, their Tor Leak site evokes the nostalgic charm of “green screen” consoles reminiscent of the 1980s, offering a unique interface controlled by specific commands. While the Akira ransomware of today showcases a significant departure in its code from the version active in 2017, both iterations share a common trait: the encryption of files bearing the .akira extension.
At the heart of Akira’s operations lies a clear financial incentive. Employing double extortion tactics, the group pilfers crucial data from victims before encrypting their devices and files. Interestingly, the perpetrators provide victims with a choice between paying for file decryption or opting for complete data deletion.
Infiltrating victims’ environments typically involves the acquisition of valid credentials. These credentials may be sourced from partners or obtained through prior attacks. Leveraging an arsenal of third-party tools such as PCHunter, AdFind, PowerTool, Terminator, Advanced IP Scanner, as well as remote desktop access tools like Windows Remote Desktop Protocol (RDP), AnyDesk, and Radmin, the actors navigate their way through target networks with precision. Additionally, tools like WinRAR and Cloudflare’s tunneling tool are employed to further facilitate their malicious activities.
Hydra:

Hydra Malware – Source: hispasec
Hydra, has recently emerged as a threat targeting users of banking applications in Spain and Latin America, disguising itself as Google Chrome and the Google Play Store. According to Bridewell’s analysis, a total of 28 Hydra Command-and-Control (C2) servers have been identified, some of which are currently operational, while others have been deployed but remain unused in any known attacks.
Characterized by its tendency to request numerous dangerous permissions, often exceeding 20 by default, Hydra gains extensive control over various device functionalities, enabling it to execute a variety of malicious actions.
These actions include stealing login credentials for financial institutions through the overlaying of a malicious login page over legitimate ones, intercepting SMS-based One-Time Passwords (OTPs) for Multi-Factor Authentication (MFA), pilfering lock screen PINs to authorize specific actions, and remotely accessing and manipulating infected mobile devices through Remote Access Trojan (RAT) functionality. Additionally, Hydra can flood contacts with bulk SMS messages from infected devices, facilitating various purposes such as spamming or disseminating phishing messages. Moreover, the trojan can manipulate device settings, potentially disabling security features like Play Protect or re-enabling Wi-Fi and mobile networks if previously deactivated by the user.
For more detailed information about the Hydra Group, you can visit our blog post.
Chucky:
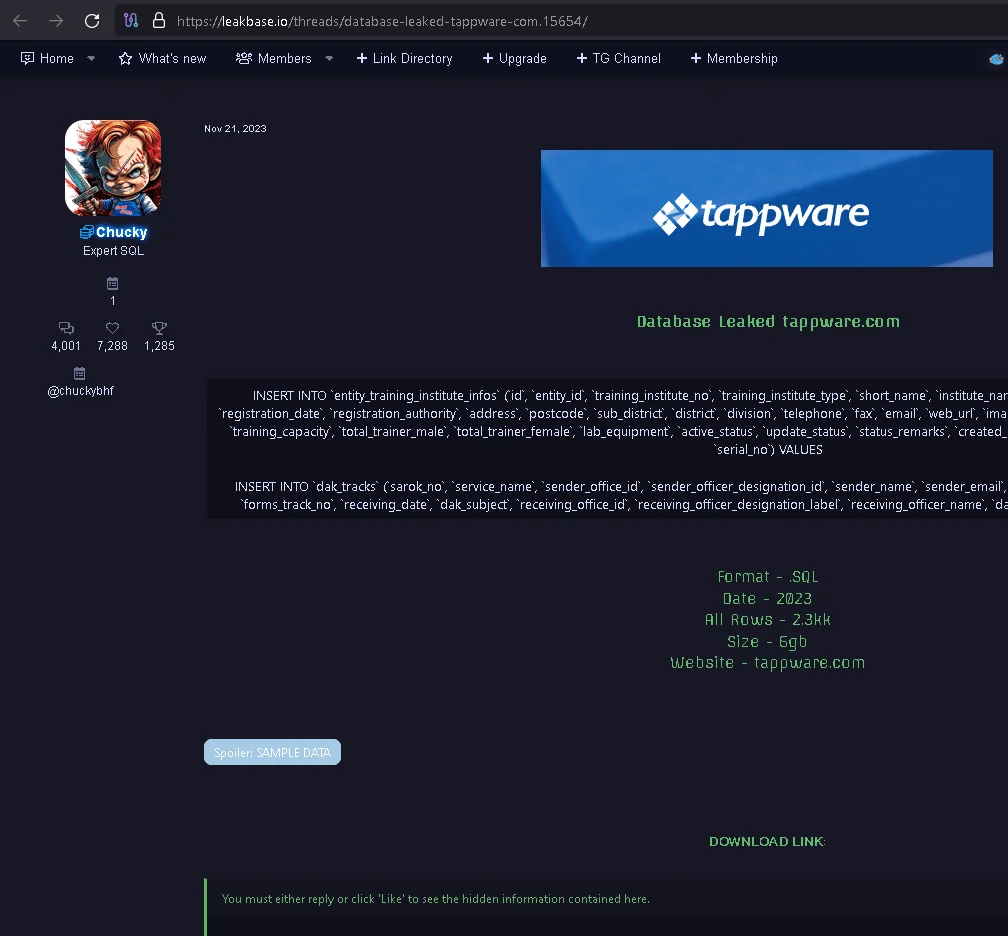
Threat Actor Chucky – Source: leakbase
Chucky, also known by aliases such as LeakBase, Sqlrip, and Chuckies, is a significant threat actor active across various underground forums. Operating under multiple monikers, especially LeakBase, Chucky shares vast collections of databases, often containing sensitive information from global entities.
LeakBase, one of Chucky’s identities, was previously known for providing data breaches and had reportedly faced shutdown in 2017. However, recent activities indicate a resurgence, with the actor regularly sharing new collections of databases, including those obtained via unauthorized means.
One of the most notable attacks attributed to this threat actor is the breach of the Swachh Bharat Mission’s swachh.city platform, which is run by the Ministry of Housing and Urban Affairs, threatening exposure of critical information of 16 million Indian users. Then, LeakBase posted a 6GB data dump on BreachForums in September 2022. This incident underscores the significant impact of Chucky’s activities on both individuals and organizations alike.
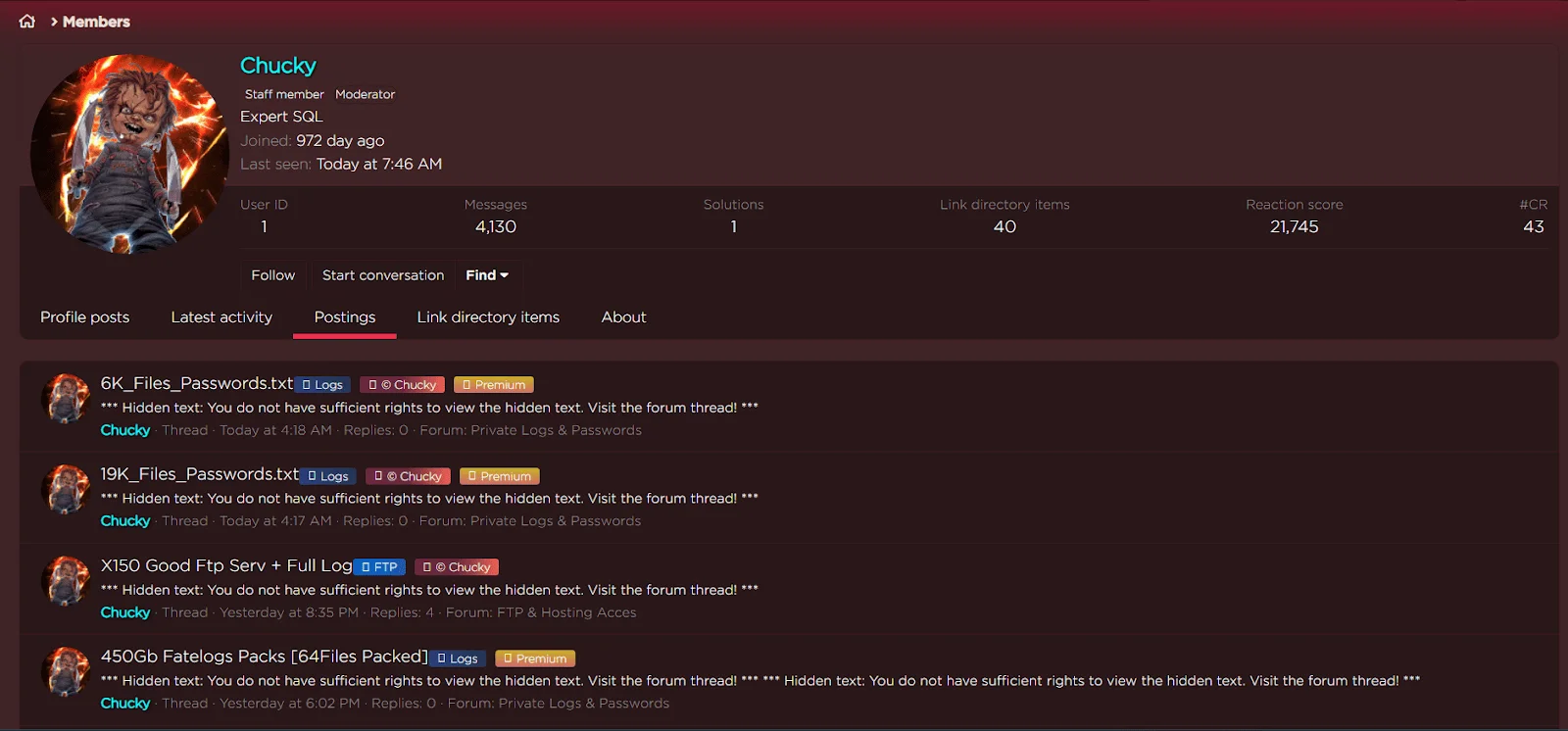
Posts made by Chucky on leakbase.io
The screenshot showcases the activities of the threat actor known as Chucky (also referred to as Leakbase) on Leakbase.io, where there are numerous significant posts in the platform.
Markitto35:
The identity of “Markitto35,” whether an individual or group, remains elusive, lacking definitive information. This moniker may serve as an alias adopted by a hacktivist or cybercriminal, yet official records or documentation pertaining to their activities are non-existent.
Certain hacktivists or cybercriminals navigate online realms under pseudonyms, masking their true identities, thereby complicating efforts to ascertain their real personas.
It is imperative to differentiate between entities engaging in discussions and potentially disseminating information about cyber activities and the actual perpetrators or threat actors. The individuals scrutinized in this report emerge as prominent voices across platforms monitored by SOCRadar, particularly concerning discussions on threats aimed at the United States of America.
While their precise ties to threat actors remain unclear, an evident trend links many of these post owners to hacktivist groups or individuals. This trend underscores the influence of ideological and political motivations in cyber threat activities directed at the United States of America.
Conclusion
In conclusion, this report sheds light on the dynamic landscape of cyber threats targeting the United States of America. Through comprehensive analysis of various metrics, including the most targeted industries, prevalent threats on the dark web, aftermath of ransomware attacks, and the top threat actors, it becomes evident that the cybersecurity challenges facing the USA are multifaceted and ever-evolving. As cyber threats continue to evolve in sophistication and scale, it is imperative for organizations and cybersecurity professionals to remain vigilant and proactive in their defense strategies. By staying informed about emerging threats and implementing robust security measures, we can better safeguard our digital assets and mitigate the risks posed by cyber adversaries.
As SOCRadar, we are committed to empowering our customers with preemptive strike capabilities through our comprehensive threat intelligence modules. By providing actionable insights and early warning indicators, we enable organizations to proactively identify and neutralize emerging threats before they manifest into full-scale attacks. Our innovative solutions equip businesses with the agility and resilience needed to stay ahead of adversaries in today’s dynamic cyber landscape, ensuring the security and integrity of their digital assets.
SOCRadar Threat Actor/Malware module




































