Trick or Threat: Diving into Spooky Techniques of Ransomware Groups
October, a month of chilling winds, pumpkin spice, and haunting tales, also marks Cybersecurity Awareness Month. An annual campaign, Cybersecurity Awareness Month, is designed to raise awareness about the importance of cybersecurity and promote good cybersecurity practices among individuals, businesses, and organizations. As we traverse through the foggy landscapes of the digital realm, we’ll uncover the spooky Tricks, Threats, and Pumpkins (TTPs) employed by ransomware ghouls. So, hold on tight as we navigate the twists and turns of this ghost train, shedding light on the dark corners of the cyber world.


Phishing Shadows (T1566 Initial Access: Phishing)
Phishing, often considered the oldest trick in the cybercriminal’s book, remains a potent weapon in the arsenal of ransomware ghouls. This tactic involves sending deceptive emails that appear to come from a trusted source. These emails often contain malicious links or attachments designed to trick the recipient into revealing sensitive information, downloading malware, or granting access to secure systems.

The effectiveness of phishing lies in its ability to exploit human psychology. By leveraging emotions such as fear, curiosity, or urgency, cyber attackers can manipulate individuals into taking actions that compromise security. This may be the reason why it is also known as human overflow amongst geeks. For instance, a phishing email might warn recipients of a security breach and urge them to click a link to reset their password. Unsuspecting users, driven by concern, may follow the instructions only to find themselves ensnared in the attacker’s trap.
In the context of ransomware, phishing serves as a primary delivery mechanism. Once a user interacts with a malicious link or downloads an infected attachment, ransomware can be silently installed on their system. From there, it’s only a matter of time before the ransomware activates, encrypting valuable data and demanding a ransom for its release.
Cobalt Strike’s Dark Magic (T1059 Command and Scripting Interpreter)
Cobalt Strike, originally designed as a legitimate penetration testing tool, has been co-opted by cyber adversaries and now casts a dark shadow over the cybersecurity landscape. Its versatility and robust features make it a favorite among ransomware ghouls, allowing them to conduct advanced attacks with relative ease.

Ransomware groups leverage Cobalt Strike for its post-exploitation capabilities. Once they gain initial access, often through tactics like phishing, they deploy the Beacon payload to explore the victim’s environment, identify valuable assets and lay the groundwork for the ransomware attack.
The dark magic of Cobalt Strike lies in its ability to blend in. By mimicking legitimate network traffic and using common tools, it evades traditional security solutions. This ability to hide in plain sight, combined with its powerful features, makes Cobalt Strike a formidable weapon in the ransomware ghoul’s toolkit.
RaaS: The Ransomware Cauldron (T1587.001 Develop Capabilities: Malware)
In the dark depths of the cyber underworld, a sinister potion is being mixed – Ransomware-as-a-Service (RaaS). This model has transformed the ransomware landscape, making it accessible to a broader range of cybercriminals, from seasoned hackers to novice threat actors.

RaaS operates much like any other ‘as-a-service’ offering in the legitimate business world. It provides ransomware tools and infrastructure on a rental or commission basis. This means that individuals or groups don’t need to develop their ransomware strains or set up the infrastructure required for a successful attack. Instead, they can simply “rent” these resources from a RaaS provider.
The RaaS model has several chilling implications:
Lowered Barriers to Entry: With RaaS, even those with limited technical skills can launch sophisticated ransomware attacks. This has expanded the pool of potential attackers, increasing the overall threat.
Constant Evolution: RaaS providers continuously update and refine their offerings to evade detection and improve success rates. This means that defense mechanisms need to evolve just as rapidly to stay effective.
Diversified Threats: Since RaaS allows multiple threat actors to use the same infrastructure, victims may face a wide variety of attack vectors and techniques, even if the underlying ransomware strain remains consistent.
Profit Sharing: Typically, RaaS providers take a cut of the ransom paid by victims. This profit-sharing model incentivizes both the RaaS provider and the attacker to maximize the impact of each attack, leading to higher ransom demands and more aggressive tactics.
Ransomware Double-Extortion Elixir (T1074 Exfiltration: Data Staged)
In the spectral realm of ransomware, data exfiltration has emerged as a chilling technique, adding another layer of horror to an already nightmarish scenario. While traditional ransomware attacks focused on encrypting data and holding it hostage, modern ransomware ghouls have evolved, now stealing sensitive data before encrypting it.

This evolution has given birth to what is known as the double-extortion attack. In this sinister strategy, cybercriminals not only encrypt the victim’s data but also exfiltrate it. The victim is then faced with a dual threat: pay the ransom to decrypt the data and resume business operations, and pay an additional ransom to prevent the stolen data from being sold or released to third parties.
The motivations behind data exfiltration are multifaceted:
Increased Leverage: By stealing sensitive data, ransomware actors gain additional leverage over their victims. Organizations are more likely to pay the ransom when faced with the prospect of their confidential information being exposed or sold on the dark web.
Monetization Opportunities: Even if the victim refuses to pay the ransom, cybercriminals can monetize the stolen data by selling it to other threat actors or using it for identity theft and fraud.
Reputation Damage: The public exposure of sensitive data can cause significant reputational damage to organizations, leading to loss of customer trust and potential legal repercussions.
Pressure Tactic: The threat of public exposure serves as a pressure tactic, compelling victims to pay the ransom quickly to avoid public shaming and the associated consequences.
TOR’s Labyrinth (T1090.003 Command and Control: Multi-hop Proxy)
The Onion Router, commonly known as TOR, is a beacon for those seeking anonymity in the vast expanse of the internet. Originally designed to protect users’ privacy and security by routing traffic through multiple servers, TOR has become a double-edged sword, offering a haven for cybercriminal activities, including ransomware operations.

Ransomware ghouls are drawn to the labyrinthine depths of TOR for several reasons:
Anonymity: TOR’s primary allure is its promise of anonymity. By bouncing internet traffic through a series of relays, TOR masks users’ locations and usage, making it nearly impossible to trace back to the source. This ensures that ransomware operators can conduct their nefarious activities without revealing their identities.
Secure Communication: Ransomware groups often use TOR for command and control (C2) communications. This ensures that their instructions to infected machines and data transfers remain hidden, evading detection by traditional security tools.
Payment Portals: TOR is frequently used to host ransom payment portals. Victims are directed to these hidden sites to receive payment instructions, often in cryptocurrencies like Bitcoin. The use of TOR adds an additional layer of security, ensuring that these transactions remain concealed.
Data Leak Sites: Modern ransomware groups, employing the double-extortion tactic, often threaten to release stolen data on dedicated leak sites. Many of these sites are hosted on the TOR network, ensuring they remain accessible while evading law enforcement’s attempts to shut them down.
Targeted Ransomware Hauntings (T1046 Discovery: Network Service Discovery)
Nowadays, ransomware attacks have evolved into planned operations. Attackers often spend time discovering their victim’s network configurations, identifying high-value targets, and understanding the network’s topology. This reconnaissance allows them to maximize the impact of their attack, ensuring they hit where it hurts the most. As defenders, recognizing the signs of such targeted discoveries and implementing robust network segmentation and monitoring becomes vital in preventing these tailored nightmares.

As we journey through Cybersecurity Awareness Month, it’s essential to recognize the growing threat of targeted ransomware attacks. Awareness, vigilance, and a proactive cybersecurity posture are our best defenses against these haunting threats.
Lightning-Fast Curses of Ransomware(T1486 Impact: Data Encrypted for Impact)
In the realm of ransomware, time is of the essence. The faster the encryption, the quicker the attacker can demand a ransom, catching victims off guard and increasing the likelihood of payment.

The paralyzing effect of ransomware is felt most acutely when encryption is swift. LockBit 3.0 and Royal Ransomware are known for their rapid encryption techniques, leaving victims in a state of shock and disbelief as they scramble to respond.
Deceptive Disguises (T1027 Defense Evasion: Obfuscated Files or Information)
In the world of ransomware, deception is the name of the game. Attackers employ many obfuscation techniques to cloak their malicious activities, ensuring their nefarious deeds go unnoticed until it’s too late. These deceptive disguises are designed to evade detection, bypass security measures, and confound analysts.

Here’s a closer look at some of the haunting obfuscation techniques:
Compression: By compressing malicious files, attackers can reduce their size and change their appearance, making them harder to detect by traditional security tools.
Encryption: Encrypting the code or payload of malware ensures that its true nature remains hidden. Only after the malware is executed does it reveal its true intent, often too late for any defensive measures to take effect.
Encoding: Encoding changes the format or representation of the malware, making it appear benign or unrelated to its actual function.
Packing: Packed malware is wrapped within another file, hiding its true nature. When executed, the packed malware unpacks itself and launches its attack. For instance, threat actors have been known to exploit WinRAR self-extracting (SFX) archives, manipulating them to stealthily install backdoors in target systems. These archives, typically containing decoy files, can be weaponized to execute malware, turning what appears to be a benign archive into a potent threat. Similarly, the BlackCat/ALPHV ransomware operation has introduced a tool named “Munchkin” that utilizes .ISO files, commonly used as disk image formats. Once a device is compromised, attackers craft a new virtual machine using this .ISO, which contains scripts designed for malicious activities, from password dumping to deploying the BlackCat encryptor.
Polymorphism and Metamorphism: These techniques allow malware to change its appearance with each iteration, making it incredibly challenging for signature-based detection tools to identify.
Code Injection: By injecting malicious code into legitimate processes, ransomware can operate under the guise of genuine applications, evading detection and gaining trusted status within the system.
Creeping Through the Network (T1534 Lateral Movement: Internal Spearphishing)
Once inside a network, ransomware ghouls don’t remain stationary. They creep, crawl, and slither through the victim’s network, seeking valuable data and systems to ensnare in their evil grasp.

Here’s a closer look at the haunting techniques of lateral movement:
Credential Harvesting: After gaining initial access, attackers often seek out user credentials. These stolen credentials, especially those of administrators or privileged users, allow them to move freely within the network, accessing sensitive systems and data.
Exploiting Vulnerabilities: Ransomware ghouls often exploit known vulnerabilities in software and systems to spread their infection to other parts of the network.
Remote Execution Tools: Tools like PsExec or Windows Management Instrumentation (WMI) can be co-opted by attackers to execute commands or deploy malware on remote systems.
Pass-the-Hash and Pass-the-Ticket: These techniques allow attackers to authenticate to other systems without knowing the actual password, leveraging stolen hash values or Kerberos tickets.
Internal Spearphishing: In some cases, attackers may send phishing emails to other users within the same organization, leveraging trust and internal communication channels to spread the ransomware.
Living off the Land: Attackers often use built-in system tools and legitimate software to move laterally, avoiding detection by not introducing new, unfamiliar tools into the environment.
Breaching the Gates (T1190 Exploit Public-Facing Application)
Public-facing applications, the digital gateways to organizations, are often the first line of defense against cyber threats. However, they can also become the entry points for ransomware ghouls if not hardened enough. Attackers are always on the prowl, seeking vulnerabilities in these applications to exploit and gain a foothold within the network. From outdated software to misconfigurations, any weakness can be a potential breach point. Once inside, the attackers can unleash their ransomware payloads, causing havoc and disruption. As we stand guard during Cybersecurity Awareness Month, it’s crucial to regularly audit, patch, and secure our public-facing applications, ensuring that the gates remain impervious to the lurking threats outside.

Like creatures lurking in the dark waiting for the right moment to strike, ransomware groups exploit known software vulnerabilities. Clop and Medusa, for instance, have been observed leveraging unpatched software to gain unauthorized access, emphasizing the importance of regular software updates and patch management.
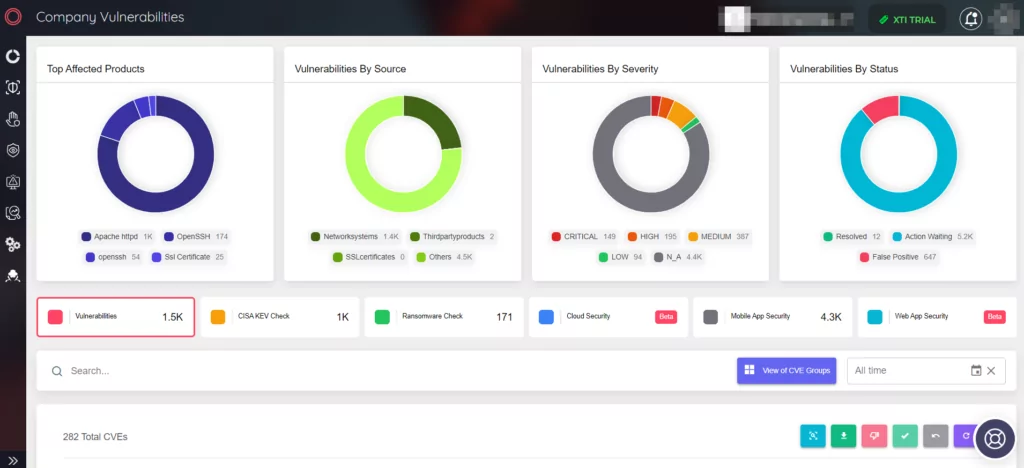
By using the Vulnerability Management panel in SOCRadar’s Attack Surface Management module, companies can be aware of the vulnerabilities in their assets and act on them early.
Conclusion
As we disembark from our ghost train ride through the chilling world of ransomware, it’s essential to remember that knowledge is our most potent weapon. October, being Cyber Security Awareness Month, serves as a stark reminder of the ever-present digital threats lurking in the shadows, waiting for an opportune moment to strike. But with awareness, we can illuminate these shadows and protect our digital realms.

Cybersecurity awareness training plays a pivotal role in proactively securing networks against threats such as ransomware. By educating employees, stakeholders, and the broader community, we can foster a culture of vigilance and resilience. Here’s why this awareness is crucial:
Proactive Defense: Knowledge empowers individuals to recognize and thwart potential threats, from phishing emails to suspicious downloads, before they can take root.
Unified Front: Cybersecurity is a collective responsibility. When everyone is informed and vigilant, the organization presents a unified front against cyber threats, making it harder for attackers to find a weak link.
Rapid Response: Awareness training ensures that in the event of a breach, individuals know the steps to take, from isolating affected systems to notifying the relevant authorities, ensuring a swift and effective response.
Continuous Learning: The cyber threat landscape is ever-evolving. Regular training sessions ensure that everyone is updated on the latest threats and best practices, ensuring that defenses remain robust.
Building Trust: For businesses, showcasing a commitment to cybersecurity can build trust with customers and partners, assuring them that their data is in safe hands.
In the face of growing ransomware threats, let’s take the lessons from Cyber Security Awareness Month to heart. By staying informed, adopting best practices, and fostering a culture of cybersecurity awareness, we can ensure that our digital journeys remain safe, secure, and free from the clutches of ransomware ghouls.
SOCRadar continuously monitors the Dark Web and shares the current updates under the Dark Web News panel in the Cyber Threat Intelligence module. In the Ransomware News tab inside the Dark Web News panel, you can follow the latest Ransomware news: