Zero-Day Vulnerabilities in Citrix NetScaler and WinRAR Are Under Active Exploitation (CVE-2023-4966, CVE-2023-38831)
Serious vulnerabilities in Citrix NetScaler and WinRAR are currently being exploited by threat actors targeting various entities, including government organizations.
[Update] December 19, 2023: “Xfinity Reports Customer Data Breach Due to Citrix Server Compromise”
[Update] November 22, 2023: Read under the title: “Joint Cybersecurity Advisory on CISA: LockBit 3.0 Ransomware Exploiting Citrix Bleed.”
[Update] November 16, 2023: “APT29 Exploits the WinRAR Vulnerability (CVE-2023-38831) in Attacks Targeting European Embassies”
[Update] November 8, 2023: “CISA Releases Guidance on Addressing the Citrix Bleed Vulnerability (CVE-2023-4966)”
[Update] October 24, 2023: “Citrix Urges Immediate Action on CVE-2023-4966 Vulnerability Exploitation.”
Researchers recently revealed active exploitation of CVE-2023-4966 in Citrix’s NetScaler ADC and Gateway appliances, while Google’s TAG has identified government-backed hacking groups exploiting CVE-2023-38831 in WinRAR. Attackers have exploited these vulnerabilities as zero-days, targeting users of NetScaler appliances to hijack their sessions, and users of WinRAR to execute arbitrary code and infect systems with malware.
In this blog post, we will explore the details of these vulnerabilities in NetScaler appliances and WinRAR, as well as available mitigation methods. We aim to provide a comprehensive understanding of the NetScaler and WinRAR vulnerabilities, shed light on the threat actors behind their exploitation, and guide readers through the latest developments in the cyber threat landscape.
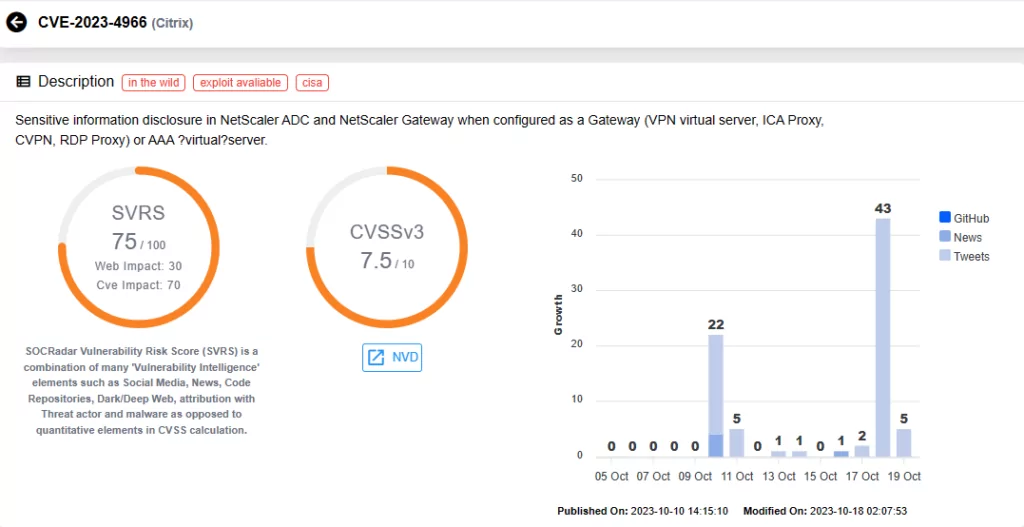
Critical NetScaler ADC and Gateway Vulnerability Exploited Since Mid-2023 to Hijack Sessions (CVE-2023-4966)
Last week, Citrix has released an advisory addressing two vulnerabilities found in NetScaler ADC and Gateway appliances. These vulnerabilities, known as CVE-2023-4966 and CVE-2023-4967, are related to unauthenticated buffers. CVE-2023-4966 can lead to the disclosure of sensitive information, while CVE-2023-4967 may result in a Denial-of-Service (DoS) situation.
Most recently, Mandiant has revealed that CVE-2023-4966 has been actively exploited in the wild since August, as a zero-day issue.
Which Versions of Citrix NetScaler ADC and Gateway Are Vulnerable?
The vulnerability affects the following versions of NetScaler ADC and Gateway appliances:
- NetScaler ADC and NetScaler Gateway 14.1 before 14.1-8.50
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.15
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-92.19
- NetScaler ADC 13.1-FIPS before 13.1-37.164
- NetScaler ADC 12.1-FIPS before 12.1-55.300
- NetScaler ADC 12.1-NDcPP before 12.1-55.300
Citrix has emphasized that NetScaler ADC and NetScaler Gateway version 12.1 have reached their End-of-Life (EoL) status and are also vulnerable to this critical security issue, meanwhile customers using Citrix-managed cloud services or Citrix-managed Adaptive Authentication remain unaffected.
How Critical Are the Vulnerabilities?
The first vulnerability carries a CVSS score of 9.4 (7.5 on NVD) and has been exploited in the wild as a zero-day issue. The second vulnerability is also of high severity, with a CVSS score of 8.2.
To exploit these vulnerabilities, there is a specific requirement: the affected appliances must be configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server.
“Exploits of CVE-2023-4966 on unmitigated appliances have been observed,” Citrix notes in the updated advisory. This underscores the urgency for Citrix customers to promptly apply the necessary patches to mitigate these vulnerabilities.
What Could the Exploitation of CVE-2023-4967 in NetScaler ADC and Gateway Appliances Lead to?
Researchers at Mandiant have detected zero-day exploitation of CVE-2023-4967 in the wild, commencing in late August 2023. Organizations in the professional services and technology sectors, along with government organizations, have been specifically targeted.
Upon exploitation, attackers can hijack authenticated sessions, effectively bypassing Multi-Factor Authentication (MFA) and other robust authentication measures. It is crucial to note that sessions compromised by an attacker might persist even after applying the patch designed to address CVE-2023-4966. Furthermore, Mandiant reports that in some observed instances, session data was pilfered before the patch deployment, and subsequently leveraged by threat actors.
The risk associated with the exploit may further escalate, based on the permissions and access scope granted to the affected identity or session. The greater the level of privileges, the more threat actors possess the ability to collect additional credentials, move laterally within the network, and potentially gain access to further resources within the environment.
You can access all updates related to this vulnerability through SOCRadar’s Vulnerability Intelligence module. Additionally, you can utilize this module to search for other identified vulnerabilities, access detailed information about them, and monitor associated threat activities.
Citrix Urges Immediate Action on CVE-2023-4966 Vulnerability Exploitation
Citrix has issued a critical alert, emphasizing the urgent need to promptly secure all NetScaler ADC and Gateway appliances. The company disclosed ongoing attacks associated with the CVE-2023-4966 vulnerability, with reported incidents involving session hijacking and targeted exploits. Notably, Mandiant previously reported the exploitation of the other zero-day vulnerability, CVE-2023-4967, starting in late August.
CISA has recently listed CVE-2023-4966 in its Known Exploited Vulnerabilities catalog, mandating federal agencies to secure their systems by November 8.
With Citrix and CISA advocating patching efforts against CVE-2023-4966 exploitation, swift action is of the utmost importance.
CISA Releases Guidance on Addressing the CitrixBleed Vulnerability (CVE-2023-4966)
CISA has issued guidance for addressing the Citrix NetScaler ADC and Gateway vulnerability, known as CVE-2023-4966 (Citrix Bleed), in response to active, targeted exploitation.
“CISA and our partners are responding to active, targeted exploitation of a vulnerability, CVE-2023-4966, affecting Citrix NetScaler ADC and NetScaler Gateway.”
The CISA blog post provides details about the vulnerability’s impact and offers links to helpful resources for mitigation and remediation.
CISA has previously incorporated this vulnerability into its KEV catalog, and the deadline for action is today (November 8, 2023). CISA is committed to regularly updating the page with further guidance, emphasizing the ongoing necessity for organizations to address and prevent the exploitation of this vulnerability.
Joint Cybersecurity Advisory on CISA: LockBit 3.0 Ransomware Exploiting Citrix Bleed
CISA, FBI, MS-ISAC, and ASD’s ACSC have issued a joint Cybersecurity Advisory (CSA) to share details and detection methods related to LockBit 3.0 Ransomware‘s exploitation of the Citrix Bleed vulnerability, CVE-2023-4966.
TTPs and IOCs from various sources, including the FBI, ACSC, and voluntarily shared Boeing data, are included in the advisory. Boeing reported LockBit 3.0 affiliates gaining initial access to Boeing Distribution Inc., a segment managing parts and distribution in a separate environment, by exploiting the Citrix Bleed vulnerability. Similar activities have been observed by other trusted third parties, according to the advisory.
The aerospace giant Boeing encountered a LockBit attack on October 27, with the threat actors imposing a negotiation deadline of November 2. LockBit kept changing Boeing’s victim status, removing and then adding the company several times to its victim listing until November 10, when it listed Boeing as “data published,” accompanied by a 40GB data leak and download links.
The advisory includes an extensive list of Indicators of Compromise (IOCs) associated with CVE-2023-4966 exploitation activity, categorized as High, Medium, or Low based on their connection to LockBit 3.0 affiliates’ exploitation.
CISA and the collaborating organizations strongly advise network administrators to implement the mitigations recommended in the advisory; hunting guidance and YARA rules are also provided.
For further details, refer to the advisory.
Xfinity Reports Customer Data Breach Due to Citrix Server Compromise
Comcast Cable Communications, operating as Xfinity, disclosed that following a Citrix server breach in October, attackers compromised customer-sensitive information.
Malicious activity within Xfinity’s network was detected between October 16 and 19, and it was later discovered that attackers had also exfiltrated the data of some customers. Xfinity, after an investigation, confirmed on December 6, 2023, that the exfiltrated customer data included usernames and hashed passwords, with the potential inclusion of names, contact info, last four digits of Social Security numbers (SSNs), birthdates, and security questions.
Xfinity has patched the vulnerability and mitigated its impact, as customers were prompted to reset passwords as a precaution. Xfinity also reported that the breach did not impact its operations, and there was no ransom demand. Furthermore, Xfinity stated that it is not aware of any customer data being leaked anywhere, nor of any attacks on its customers.
How to Protect NetScaler ADC and Gateway Appliances Against CVE-2023-4966?
Customers using NetScaler ADC and Gateway are strongly encouraged to install the relevant updated versions as soon as possible to prevent exploitation:
- NetScaler ADC and NetScaler Gateway 14.1-8.50 and later releases
- NetScaler ADC and NetScaler Gateway 13.1-49.15 and later releases of 13.1
- NetScaler ADC and NetScaler Gateway 13.0-92.19 and later releases of 13.0
- NetScaler ADC 13.1-FIPS 13.1-37.164 and later releases of 13.1-FIPS
- NetScaler ADC 12.1-FIPS 12.1-55.300 and later releases of 12.1-FIPS
- NetScaler ADC 12.1-NDcPP 12.1-55.300 and later releases of 12.1-NDcPP
For further guidance on patching CVE-2023-4966, refer to Citrix’s official advisory.
While patching is the best approach, Mandiant has provided a document outlining alternative measures that can be applied if an immediate update is not possible:
- Enforce ingress IP address restrictions on vulnerable appliances to limit exposure, restrict access to trusted or predefined source IP address ranges to reduce external attack exposure.
- After upgrading, terminate all active and persistent sessions per appliance. Use the Command-Line Interface (CLI), connect to your appliance and run the command: clear lb persistentSessions
- Rotate credentials for identities accessing resources through a vulnerable NetScaler ADC or Gateway appliance. In the presence of suspicious activity or lateral movement, prioritize credential rotation for a broader range of identities.
- If web shells or backdoors are found on NetScaler appliances, rebuild them using a clean-source image with the latest firmware. If restoring from a backup image is necessary, review the backup configuration to ensure there are no backdoors.
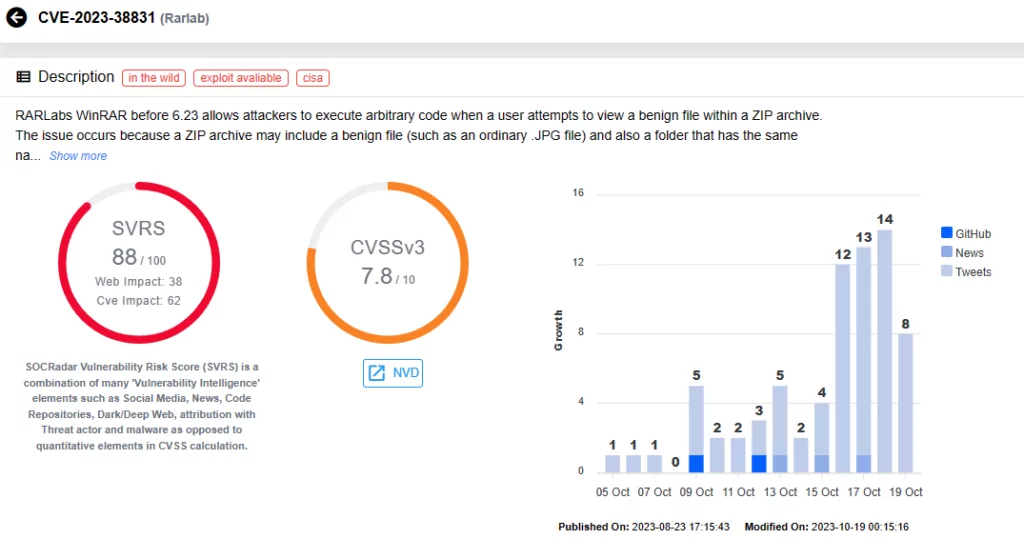
Nation-State Threat Actors Exploit WinRAR Zero-Day Vulnerability in Campaigns Targeting Government Organizations (CVE-2023-38831)
Google’s Threat Analysis Group (TAG) recently detected government-backed hacking groups exploiting a known vulnerability, CVE-2023-38831 (CVSS score: 7.8, High severity), in file archive tool WinRAR.
RARLabs released an updated WinRAR version in August 2023 that fixed several security bugs, including CVE-2023-38831. This vulnerability causes unintended file expansion when handling certain archives, allowing attackers to execute arbitrary code when users open harmless files within ZIP archives.
According to Google, the vulnerability was exploited as a zero-day by threat actors since at least April 2023, targeting financial traders and distributing various commodity malware families. Following its disclosure, Proof-of-Concept (PoC) exploits and exploit generators quickly surfaced on GitHub, with testing activity observed from financially motivated and Advanced Persistent Threat (APT) actors experimenting with CVE-2023-38831.
What is the WinRAR Vulnerability About? (CVE-2023-38831)
When a user double-clicks on a innocuous looking “poc.png_” file in WinRAR prior to version 6.23, it executes “poc.png_.cmd” instead. This happens because WinRAR mistakenly extracts both the selected file and files inside a matching directory to a random temporary folder when determining which files to expand.
WinRAR then normalizes the file path, removing appended spaces, and attempts to execute the user-selected file with a trailing space in the path. This triggers an unexpected behavior in ShellExecute, where it looks for file extensions and ends up executing the first file it finds with an extension like “.pif, .com, .exe, .bat, .lnk, .cmd.”
This quirk in ShellExecute causes “poc.png_.cmd” to be executed, even though the user initially double-clicked on a different file. The issue is not limited to trailing spaces; any space in the file extension can trigger this vulnerability.
Campaigns Exploiting CVE-2023-38831 in WinRAR
Google TAG reports that threat actors have utilized this vulnerability in multiple campaigns targeting various organizations:
- FROZENBARENTS (aka SANDWORM), associated with the Russian GRU, impersonated a Ukrainian drone warfare training school in a recent campaign. They used an email lure to deliver a benign PDF document along with a malicious ZIP file exploiting CVE-2023-38831. The payload was a Rhadamanthys infostealer, a commercially available tool, which Google reports is unusual for this group.
- FROZENLAKE (aka APT28), also attributed to Russian GRU, targeted Ukrainian government organizations in a spear-phishing campaign using CVE-2023-38831. They used a free hosting provider to serve the exploit, redirecting users to a mockbin site to verify their location before delivering the malicious file. The decoy document was an event invitation from Razumkov Centre, a Ukrainian think tank.
- FROZENLAKE introduced a new technique in their toolkit by using an exploit file named “IOC_09_11.rar” to create a reverse SSH shell and execute an IRONJAW script via PowerShell. IRONJAW steals browser login data and local state directories, exfiltrating them to a command and control server.
- ISLANDDREAMS (aka APT40), a group linked to China, exploited CVE-2023-38831 in a campaign targeting Papua New Guinea. Their phishing emails included a Dropbox link to a ZIP archive containing the exploit, a password-protected decoy PDF, and an LNK file.
Google advises organizations and users to keep their software up-to-date. For more information and available Indicators of Compromise (IoCs) on the threat actors known to have exploited the vulnerability, visit Google’s analysis of the WinRAR vulnerability. You can find WinRAR updates here.
APT29 Exploits the WinRAR Vulnerability (CVE-2023-38831) in Attacks Targeting European Embassies
The National Security and Defense Council of Ukraine has reported that APT29 exploited the CVE-2023-38831 vulnerability in WinRAR during attacks on European embassies. The campaign, initiated in September 2023, targeted diplomatic entities in Azerbaijan, Greece, Romania, and Italy.
Visit the APT profile to learn more about the campaign: APT Profile: Cozy Bear / APT29
Proactively Defend Against Exploitation with SOCRadar’s Attack Surface Management
SOCRadar provides continuous monitoring of security vulnerabilities, offering timely intelligence essential for safeguarding organizational assets. With the Attack Surface Management (ASM) module, you can access critical information about vulnerabilities impacting your assets and streamline patch prioritization for effective protection.