
Top 10 Data Leaks in 2022
Threat actors need sensitive information to carry out most of their malicious activity. They typically obtain the information by conducting various cyberattacks or simply gathering it from unprotected platforms, accounts, or databases.
When an attacker exploits a piece of information, they usually sell or leak it later for other threat actors to freely use, causing further damage and hiding their tracks. It is also important to remember that exposure of personal information increases the risk of identity theft.
Data leaks typically have a long-lasting effect because the information is always reusable in different attack techniques.
In this blog, we present you the data leak incidents that received the most attention in 2022.
Download SOCRadar’s 2022 End-of-Year Report and get more insights into major data leaks.
10. Medibank | 9.7 Million Customer Data
Medibank’s customer data was compromised due to the company’s refusal to pay its attackers following a ransomware incident. The data was stolen but not encrypted because Medibank stopped the attack following reports from Australian authorities.

How Did It Happen?
Medibank is one of Australia’s largest private health insurance providers. Earlier than November, the company was targeted by a group possibly related to the REvil (Sodinokibi) ransomware gang and reported unusual activity within their system in October.
During the breach, attackers gained access to 9.7 million customers’ data. They published sample data and demanded a $10 million ransom from Medibank, threatening to leak the stolen data on the dark web if they refused.
Medibank refused to pay the ransom, so the attackers leaked the documents on the dark web on November 9. In late November, the hackers released additional data to close the case against Medibank, with the message: “Happy Cyber Security Day!!! Added folder full. Case closed.”
What Type of Information Has Been Exposed?
Threat actors leaked customers’ names, birthdates, addresses, phone numbers, email addresses, and the information of some of the customers’ authorized representatives.
9. WhatsApp | 487 Million Phone Numbers
In November, a threat actor advertised the phone numbers of 487 million WhatsApp users for sale on a breach forum. According to reports, the database was recent.

How Did It Happen?
Although it was most likely scraped, it is unclear how the threat actor got access to these records. The threat actor divided the records into datasets and priced them differently.
Later, the post was taken down, but new dark web posts started to spread similar information. Using the exposed phone numbers, attackers could trick users via SMS or phone calls.
What Type of Information Has Been Exposed?
The leaked data included phone numbers from users in 84 countries, most of whom were from Egypt, Italy, and the US.
8. Twitter | 7 Million Accounts
Another popular application, Twitter, had a significant data leak incident in July. The leak resulted in a much larger leak afterward.

How Did It Happen?
A threat actor acquired over 5.4 million Twitter user records with private information and leaked it on a hacker forum. Attackers obtained the information in December 2021 by using an API vulnerability that had been made public in a HackerOne bounty program and was fixed in January 2022. In July 2022, the threat actor sold personal information for $30,000.
In November, security researchers found nearly 7 million Twitter profiles with private information on the dark web. In addition to the 1.4 million suspended user profiles collected using a different API, the database also contained the 5.4 million user profiles from the earlier leak.
What Type of Information Has Been Exposed?
Leaks included public information like verified status, account names, Twitter IDs, bios, screen names, and personal phone numbers.
7. Optus | 9.8 Million Customer Information
A threat actor gained unauthorized access to Optus’ network and stole 9.8 customer information records. It is unclear when the actual breach happened, but it was detected on September 22.

How Did It Happen?
According to reports, the telecom company had an API allowing customer data access without authorization or authentication. The vulnerable API could be the entry point of the attack.
The hacker “optusdata” uploaded a sample of 10,200 customers’ stolen data and demanded a $1 million ransom. Still, after facing law enforcement, they apologized to Optus and its customers and declared to have destroyed the data.
The victims of the breach have reportedly been receiving phone calls, emails, and SMS messages from phishing actors. A new phishing campaign was reported on November 11, in which attackers impersonated Equifax and offered free Equifax subscriptions via SMS to trick Optus customers into clicking a malicious link.
What Type of Information Has Been Exposed?
Optus reported on September 28 that the 9.8 million records included 14,900 valid Medicare IDs and 22,000 expired Medicare card numbers.
6. BidenCash | 1.22 Million Credit Cards
BidenCash carding marketplace leaked an advertisement dump that contained information of 1,221,551 credit cards. The data was made publicly available.

How Did It Happen?
The stolen credit card information was made available on new domains of BidenCash, presumably in an effort to advertise them, as well as on other hacker forums. The marketplace obtains the information in leaks via stealer malware and skimmers.
BidenCash had leaked a promotional dump before the carding website was first launched on June 16. The initial database dumped then contained about 8 million lines of data, including email addresses, with about 6,700 credit cards.
What Type of Information Has Been Exposed?
Along with credit card numbers, the data leak included expiration dates, names, CVV numbers, bank names, social security numbers, phone numbers, email addresses, and addresses.
5. MyDeal | 2.2 Million Customer Information
An Australian retail marketplace operated by Woolworths, called MyDeal, reported a data breach that affected 2.2 million customers.

How Did It Happen?
According to the company, a hacker gained access to the CRM system using stolen credentials and obtained the sensitive customer information. The hacker then offered the stolen information for sale on a dark web forum.
What Type of Information Has Been Exposed?
Personal information, including names, email addresses, phone numbers, delivery addresses, and some birthdates, was exposed.
4. Rockstar Games | Source Code, Assets, Test Clips
Slack and Confluence servers owned by Rockstar Games were compromised due to a network breach. Data from video games called “GTA 5” and the upcoming “GTA 6” were stolen.

How Did It Happen?
“Teapotuberhacker,” also responsible for Uber’s intrusion, leaked the data on GTAForums. The threat actor sold some of the data for more than $10,000.
On Twitter, word of the incident spread quickly, and the incident is now called one of the biggest leaks in the video game industry.
Additionally, more threat actors were trying to profit from the situation by offering fake leak data for sale.
What Type of Information Has Been Exposed?
GTA 5 and GTA 6 source code and assets, as well as GTA 6 testing videos, were allegedly stolen. The size of the stolen data is unknown, but 90 clips from game tests were leaked by the threat actor, revealing some of the storyline and theme.
3. Neopets | 69 Million Accounts
The virtual pet platform Neopets, which introduced its own NFTs, had its source code and database publicized.

How Did It Happen?
A data breach of the Neopets platform led to over 69 million users’ personal information theft.
A threat actor under the alias “TarTarX” sold the data on a breach forum. Researchers found that the attackers had access to Neopets’ systems since January 3, 2021.
What Type of Information Has Been Exposed?
The stolen database contains 460MB of source code and usernames, names, email addresses, passwords, zip codes, dates of birth, genders, activation codes, and other additional information.
2. ChatVPN, GeckoVPN, and SuperVPN | 21 Million Accounts
A threat actor exposed 10GB of data on a Telegram channel. The data contained 21 million records from users of various VPN services.

How Did It Happen?
In 2021, threat actors listed 21 million data records belonging to ChatVPN, GeckoVPN, and SuperVPN users for sale on the dark web.
Later, in May 2022, the data dump was leaked for public use via a Telegram hacker channel.
The data also contained hashed credentials, but because there were no duplicate password hashes in the records, decrypting them would be more difficult for threat actors.
What Type of Information Has Been Exposed?
Exposed data included users’ full name, country, payment information, account status, expiration date, email address, and hashed password string.
1. NVIDIA | 71,000 Employee Credentials
In February, Nvidia experienced a breach that led to the theft of 71,335 employees’ credentials. The threat actors later leaked the information of compromised accounts.

How Did It Happen?
Some of Nvidia’s systems were disrupted as a result of the cyberattack. The Lapsus$ gang later claimed responsibility for the hack and disclosed that they had stolen 1TB of data from Nvidia’s network. After a futile ransom demand, 20GB of the data was leaked on threat actors’ Telegram channel.
Lapsus$ threatened that they would leak hardware information if the company did not remove the LHR restrictions on GeForce RTX 30 series firmware. The group also demanded that Nvidia commit to open-sourcing their GPU drivers.
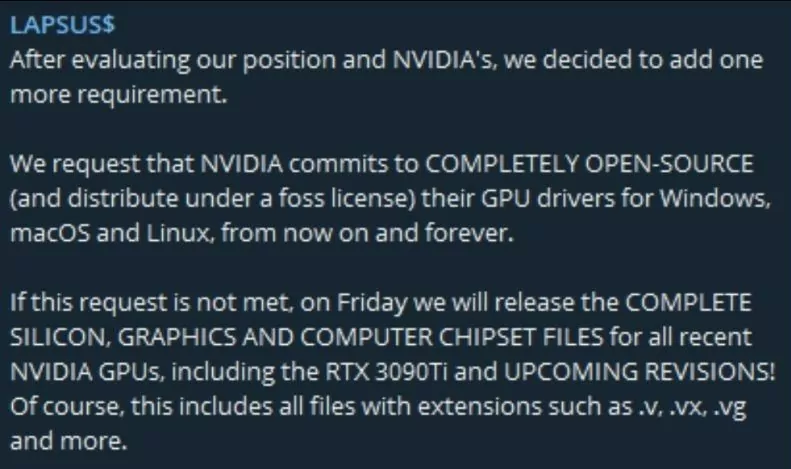
What Type of Information Has Been Exposed?
The data contained email addresses and NTLM password hashes that threat actors could decipher. Threat actors also claim that they accessed firmware information, documentation, private tools, drivers, SDKs, and additional information about Nvidia’s falcon.
Take Action Against Data Leaks: 5 Best Practices
- Train employees about security and raise awareness.
- Use strong passwords, and avoid reusing/recycling across multiple services.
- Create a zero-trust environment in your organization.
- Beware of past leaks on services you use.
- Stay updated about new dark web threats. Check the DarkMirror tool to see the most recent data leaks found on dark web forums that SOCRadar monitors.
How Can SOCRadar Help?
SOCRadar can help monitor the dark web for leaked sensitive information related to your organization, whether it is corporate, customer, or employee data, and notify you about critical data leak incidents.
Our platform also provides Source Code Leakage Monitoring, which regularly checks public code repositories such as GitHub and GitLab for cases of exposed data, source code, API, and keys.



































