
An Overview of Microsoft Digital Defense Report 2024
The Microsoft Digital Defense Report 2024 offers a detailed view of the increasingly intricate global cybersecurity landscape. The tech giant reveals that its customers face over 600 million cyberattacks daily, including ransomware, phishing, and identity breaches. The Microsoft Digital Defense Report 2024 underscores the expanding influence of nation-state affiliated threat actors, whose cyber operations support broader geopolitical conflicts through espionage, disruption, and manipulation.
One notable finding is the growing collaboration between cybercrime gangs and nation-state groups, where tools and techniques are shared to boost attack sophistication. Covering key areas such as the evolving threat landscape, ransomware trends, DDoS attacks, and the critical role of identity security, the Microsoft Digital Defense Report 2024 also highlights the increasing complexity of modern ransomware attacks, with case studies like Octo Tempest (aka Scattered Spider) shedding light on their real-world impact.
Another major focus is the role of AI in cybersecurity—both as a tool for attackers and as a robust defense mechanism. Governments and industries are making strides to establish global AI security standards, ensuring a multi-layered defense against these evolving threats.
In this blog post, we will provide an overview of these key findings, breaking down the insights from the Microsoft Digital Defense Report 2024 to help organizations stay ahead of the ever-changing cybersecurity landscape.
Key Insights from the Microsoft Digital Defense Report 2024
Here’s a brief summary of the key insights from the Microsoft Digital Defense Report 2024, highlighting the most critical statistics mentioned:
- 600 million cyberattacks daily targeting Microsoft customers.
- 2.75x increase in ransomware attacks year-over-year, though fewer reach encryption stages.
- Tech scams surged by 400%, with over 100,000 daily incidents in 2024.
- Phishing attacks up by 58%, increasingly leveraging legitimate web services for malicious campaigns.
- Growing collusion between cybercrime gangs and nation-state actors, sharing tools to escalate attacks.
- DDoS attacks peaked at 4,500 daily in June 2024, with a rise in covert application-layer threats.
- $1 trillion stolen by fraudsters globally in 2023, with e-commerce fraud expected to exceed $90 billion annually by 2028.
While these insights offer a snapshot of the rising threats in the cyber landscape, the following sections provide more context on the key findings from the Microsoft Digital Defense Report 2024 and how they relate to today’s cybersecurity challenges.
Nation-State and Ransomware Trends
The Microsoft Digital Defense Report 2024 highlights a sharp increase in cyber activity from nation-state actors and financially motivated criminals. Nation-state threat actors are increasingly collaborating with cybercriminals, sharing tools and techniques. Microsoft observed this trend throughout 2023 and 2024, with key examples including:
- Russian threat actors outsourcing cyber espionage to criminal groups, particularly targeting Ukraine. In one instance, malware compromised at least 50 military devices.
- Iranian actors using ransomware in a campaign to exploit data stolen from Israeli sites, selling the removal of profiles for profit.
- North Korea leveraging ransomware, with the custom variant FakePenny targeting aerospace and defense organizations.
Geopolitical conflicts play a crucial role in shaping these attacks. Around 75% of Russian cyber activities focused on Ukraine and NATO members, while China and Iran focused on targets like Taiwan, Israel, and Gulf countries involved in normalizing relations with Israel.
Furthermore, nation-state actors, particularly from Russia, Iran, and China, are actively working to influence the U.S. election, using cyber tools to spread disinformation and lower confidence in democratic processes.
On the cybercrime front, financially motivated attacks are also on the rise:
- Ransomware attacks have increased by 2.75 times, though fewer reach the encryption stage.
- Tech scams surged 400%, with malicious infrastructure often disappearing in under two hours, demonstrating the agility of these threats.
Although it is pointed out that fewer ransomware attacks reach the encryption stage in 2024, they are getting more and more sophisticated every day. The Octo Tempest group, for example, illustrates how ransomware tactics are evolving. Also known as Scattered Spider, this group gained prominence for hybrid attacks on both cloud and on-premises assets. Notably, they employ social engineering, SIM swapping, and adversary-in-the-middle (AiTM) techniques to infiltrate networks, eventually deploying ransomware payloads such as Qilin and RansomHub.

Learn more about Scattered Spider on SOCRadar’s Dark Web Profile
SOCRadar’s Dark Web Monitoring keeps a close eye on underground forums and marketplaces, helping you uncover potential threats before they can make an impact. With real-time insights into ransomware actors’ tactics, you can explore their attack methods, tools, and potential targets to stay one step ahead.
Additionally, SOCRadar’s Threat Actor Intelligence provides in-depth analysis of threat actors and malware operations, including their behavior patterns and emerging campaigns, enabling you to strengthen your defenses and combat them effectively.
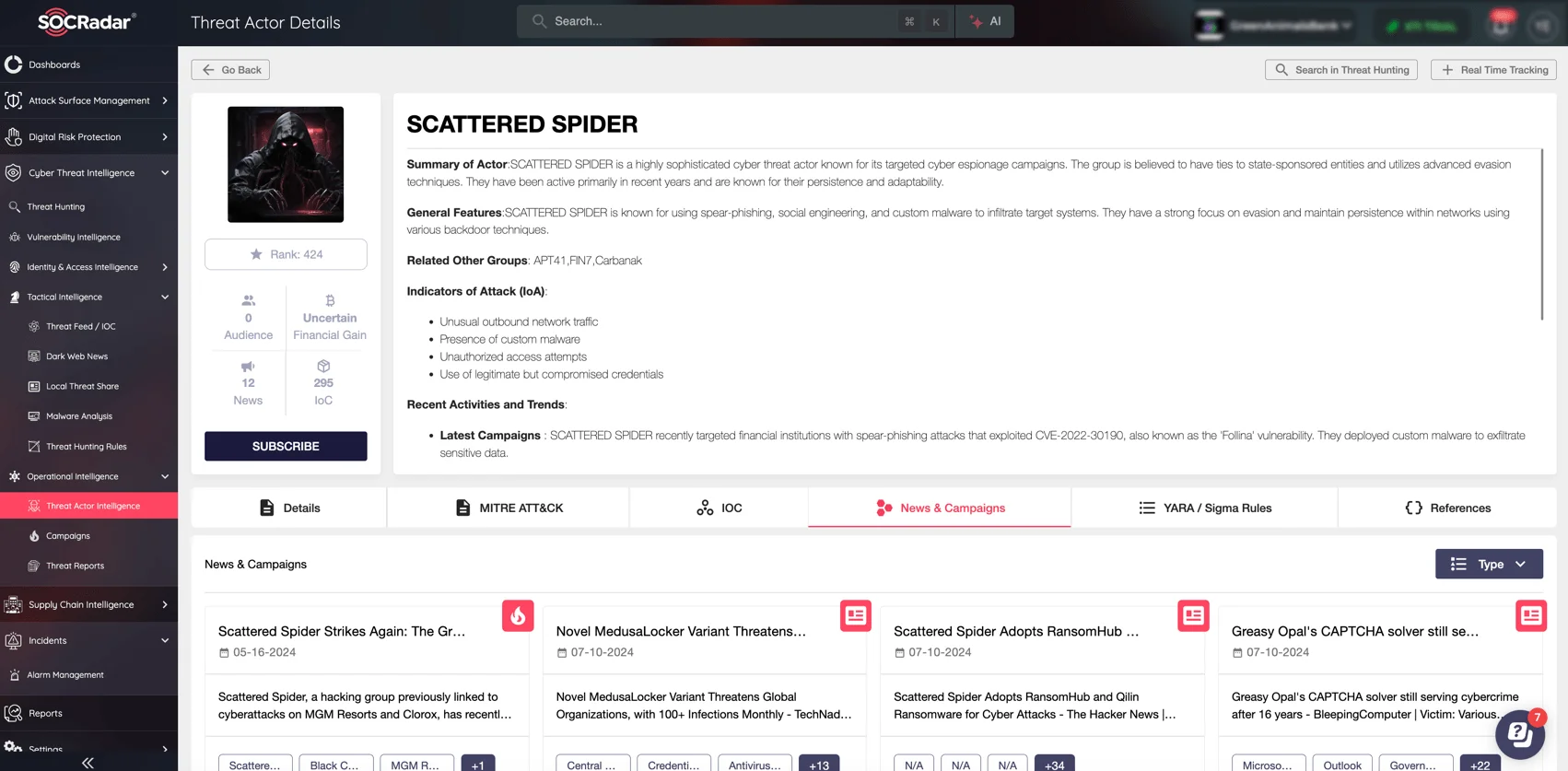
Details of Scattered Spider, also known as Octo Tempest (SOCRadar Threat Actor Intelligence)
Strengthening Cybersecurity with a Secure Future Initiative
The Microsoft Digital Defense Report 2024 emphasizes the importance of strategic approaches to cybersecurity, spotlighting the Secure Future Initiative and the need for threat-informed defense strategies.
Solutions for Data Security and Impact of AI
Microsoft agrees that organizations must proactively manage their digital environments with data security at the forefront. This includes understanding how data flows, identifying risks, and tailoring security policies based on user roles. A strong data security strategy involves continuous visibility, through monitoring data access and usage, as well as dynamic policies that allow low-risk users more freedom while implementing tighter controls for high-risk individuals.
To manage the complexities of modern data ecosystems, organizations should adopt integrated security solutions, reducing alert fatigue and improving response times. Essential components include:
- Data Classification and Labeling: Properly identify and safeguard sensitive data.
- Data Loss Prevention (DLP): Implement DLP policies to prevent unauthorized access, particularly as AI technology advances.
The rise of AI also introduces challenges in data governance, particularly around the identification and protection of sensitive information. Organizations must ensure that critical data is properly labeled and secured to prevent unintended exposure when using AI-driven applications. Additionally, AI can be leveraged to automate the classification process, making it easier to identify and safeguard sensitive information across systems.
In general, Generative AI is becoming a tool for both cybercriminals and nation-states, with China using AI-generated imagery and Russia leveraging AI-generated audio in influence operations. Though these efforts have yet to show significant success, AI’s role in cyberattacks is growing. On the defense side, AI is proving invaluable for cybersecurity professionals by speeding up responses and analyzing threats more efficiently.
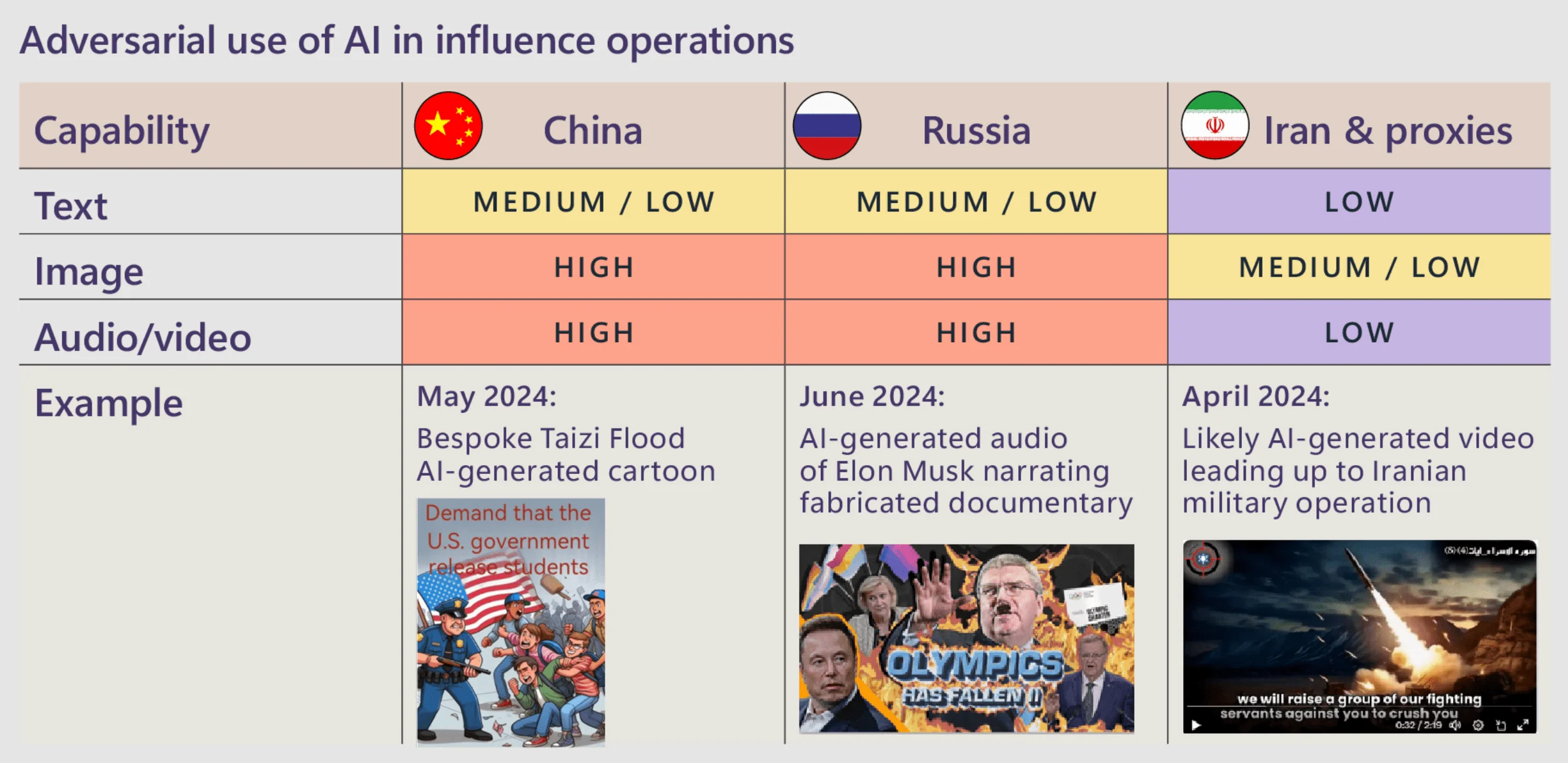
Adversarial use of AI (Microsoft Digital Defense Report 2024)
The Role of Threat-Informed Defense and Accountability
A threat-informed defense allows organizations to adopt an attacker’s perspective, improving their ability to safeguard critical assets. By identifying potential attack paths and vulnerabilities, this strategy helps organizations stay ahead of evolving threats.
Unified threat visibility consolidates insights across all assets—cloud-based, on-premises, and identity-related—into a single view, allowing a focus on protecting the most targeted assets while continuously addressing vulnerabilities.
A strong cybersecurity strategy also depends on accountability across the organization. Leadership must promote a security-first culture with clear, adaptable guidelines. By fostering collaboration and avoiding a blame-focused environment, organizations can more effectively manage risks and build resilience against evolving cyber threats.
Emerging DDoS Threats and Application Loop Attacks
DDoS attacks are an ever-growing threat, with both their frequency and sophistication increasing. These attacks overwhelm websites or services with excessive traffic, leading to disruptions, downtime, financial losses, and damage to reputations.
According to Microsoft Digital Defense Report 2024, since mid-March 2024, DDoS attacks have surged, peaking at approximately 4,500 daily attacks in June. More concerning are the rise of covert application-layer DDoS attacks, which directly target web applications rather than networks. These attacks are harder to detect and mitigate compared to traditional network-level attacks.
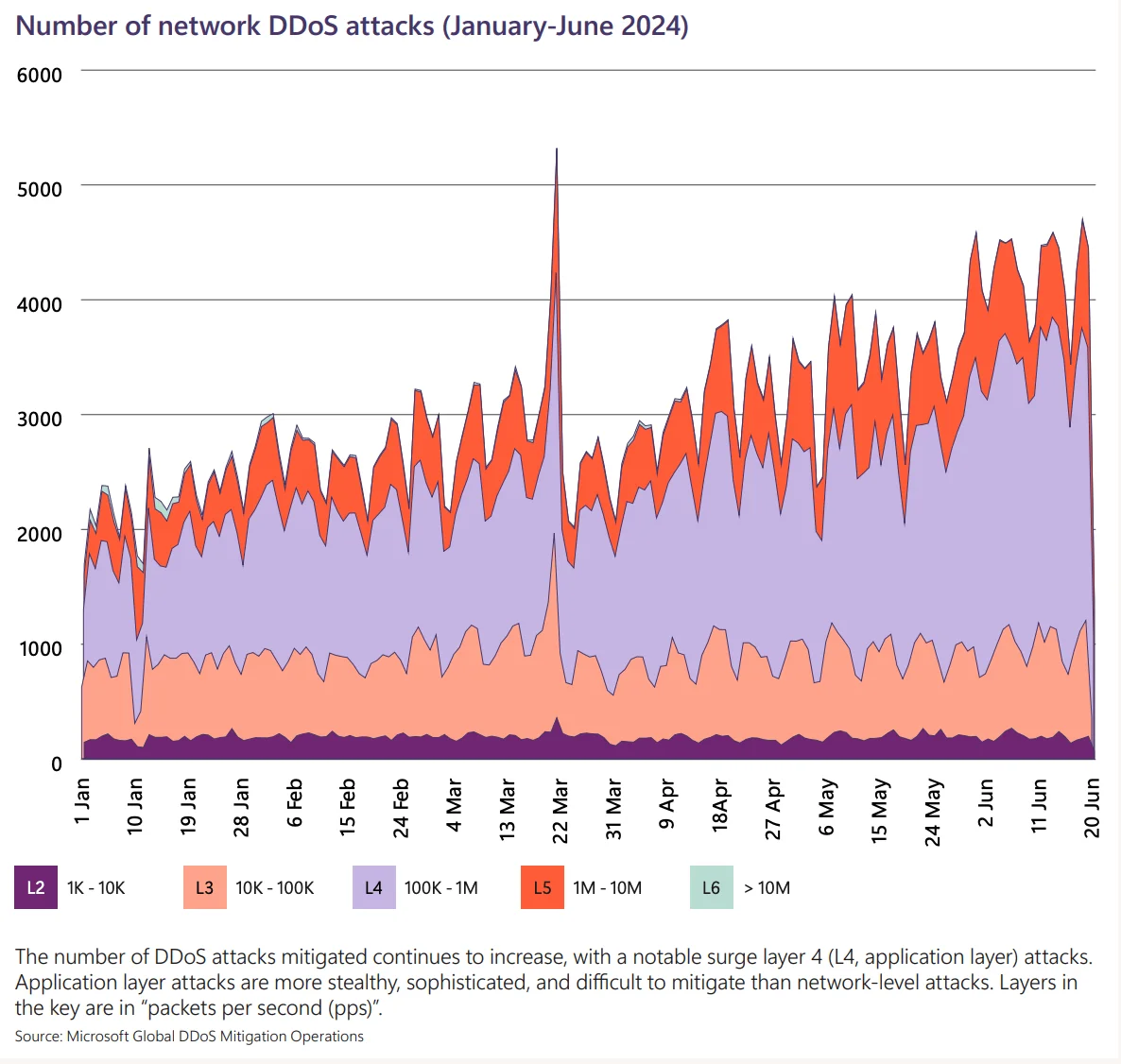
Number of network DDoS attacks through January-June 2024 (Microsoft Digital Defense Report 2024)
Also a new and more complex threat is the application loop attack. This type of DDoS attack exploits vulnerabilities in core internet protocols such as DNS and NTP, causing servers to exchange endless error messages. Unlike typical volumetric attacks, loop attacks can cripple systems with minimal data, severely affecting server and network performance.
India’s gaming sector has emerged as a major target, with a sharp rise in DDoS attacks against sectors like finance and technology around the globe, driven largely by hacktivists.
To counter DDoS attacks, organizations should limit their applications’ exposure to the public internet and implement a defense-in-depth strategy. This includes combining network layer DDoS protection with web application firewalls. Conducting regular DDoS simulations can also help ensure systems are adequately protected.
SOCRadar Labs’ DoS Resilience module can help your organization strengthen its defenses against Denial-of-Service (DoS) threats, allowing you to evaluate your domain’s or subnet’s ability to withstand DoS attacks. Additionally, you can check out our blog on the Global DDoS Attack Landscape for insights from Q1 2024.
Insights on Identity Attacks and Trends
Identity-based attacks remain a dominant force in the threat landscape, with password-based methods leading the charge. Over 99% of these attacks, such as breach replays, password sprays, and phishing, exploit predictable human behaviors like weak passwords and reusing credentials.
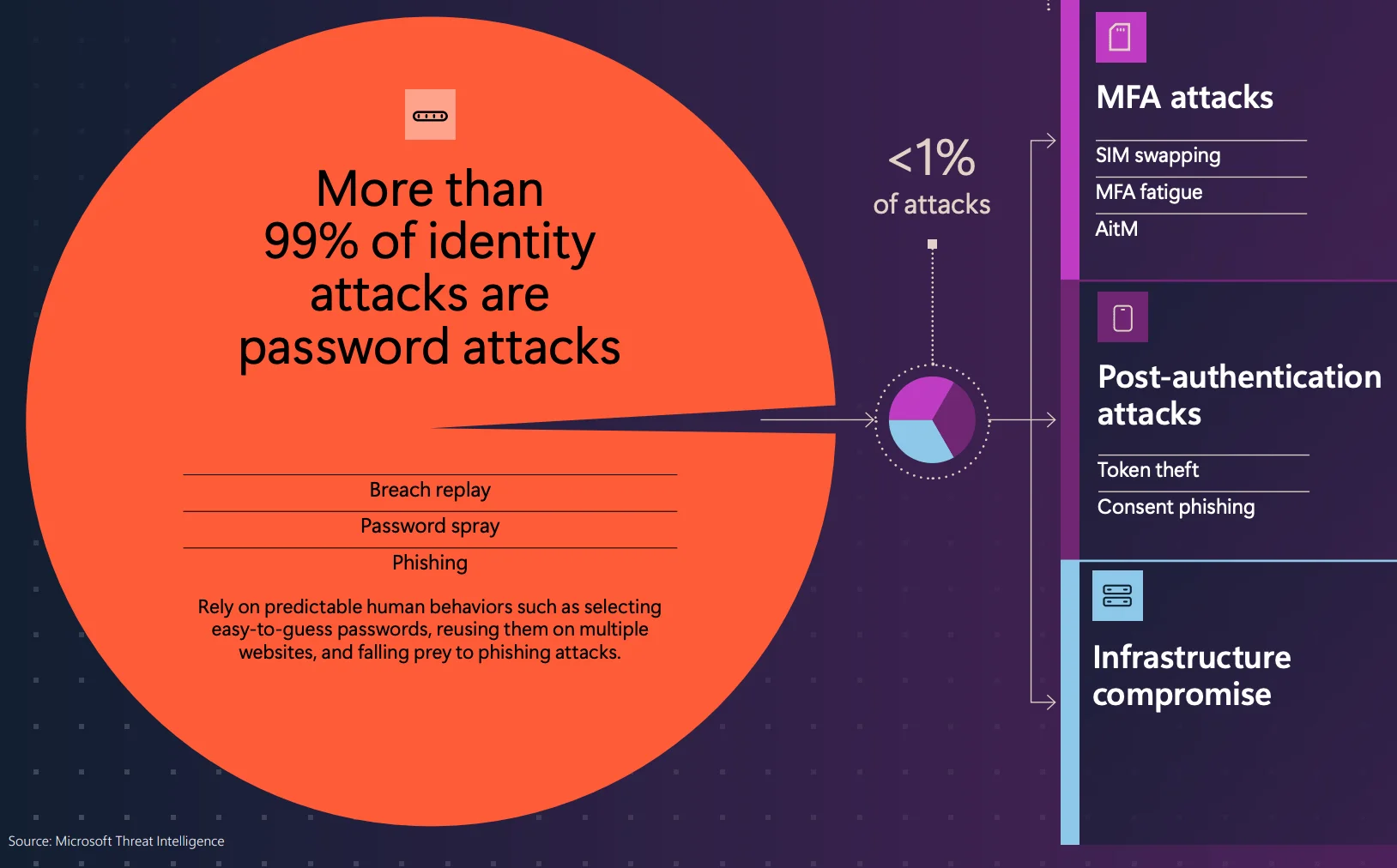
More than 99% of identity attacks are password attacks (Microsoft Digital Defense Report 2024)
Although Multi-Factor Authentication (MFA) can provide strong defense, attackers are evolving tactics like SIM swapping, MFA fatigue, and phishing to bypass these protections. Additionally, post-authentication threats like token theft and consent phishing further jeopardize accounts after legitimate access is gained. Infrastructure compromise, often involving sophisticated, hard-to-detect methods, is another significant threat, especially from nation-state actors.
Phishing campaigns, in particular, remain a prevalent method used by attackers to steal sensitive information, compromising user accounts and gaining unauthorized access to systems. Attackers use sophisticated impersonation techniques, masquerading as legitimate entities to deceive users into disclosing their credentials or clicking on malicious links. These tactics are often successful because they exploit trust within communication channels, especially email and social platforms.
In response to these challenges, organizations must adopt stronger identity protection strategies, ensuring MFA is enforced, implementing zero trust principles, and educating users about the dangers of phishing. By focusing on identity as a critical security boundary, companies can better protect their most vulnerable assets—user credentials—and reduce the likelihood of successful attacks.
Growing Fraud Landscape
Fraud incidents are rising globally, with increasingly sophisticated methods targeting both consumers and businesses.
The Microsoft Digital Defense Report 2024 states that in 2023, over $1 trillion was stolen by scammers, causing businesses to lose an average of 1.5% in profits and consumers to lose $8.8 billion—a 30% increase compared to 2022. Common types of fraud include payment fraud, Business Email Compromise (BEC), investment scams, and the rise of deepfake impersonation.
Cyber-enabled financial fraud is also expanding, with investment scams alone accounting for over $4.5 billion in losses last year. Microsoft has been proactive in combating this rise, suspending more than 64 million abusive accounts and partnering with law enforcement in major takedowns, including successful raids in India.
Phishing remains a critical threat, with a 58% increase in attacks during 2023. QR code phishing, where malicious links are hidden behind QR codes, has become more prevalent, making it harder to detect attacks. Meanwhile, BEC attacks continue to evolve, with new techniques like inbox rule manipulation and lateral phishing increasing success rates.
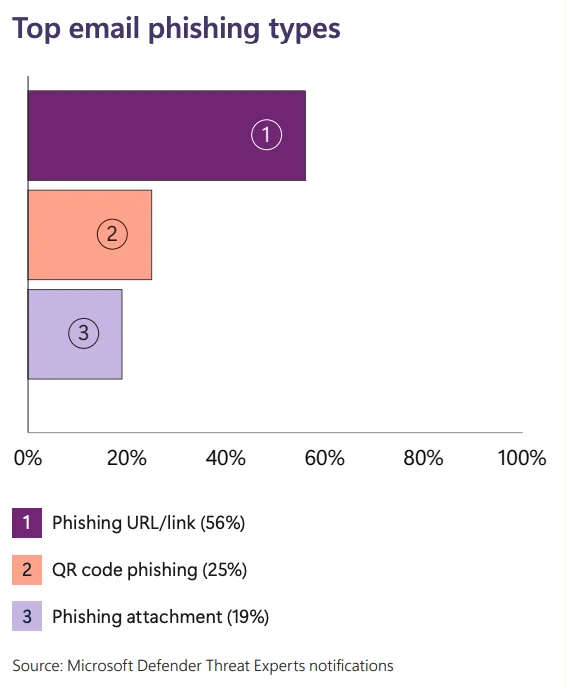
Top email phishing types (Microsoft Digital Defense Report 2024)
To counter these threats, organizations must adopt a multi-layered defense strategy. This involves using AI and machine learning to detect unusual transaction patterns, implementing advanced authentication methods, and fostering industry-wide collaboration to strengthen fraud prevention. The Microsoft Digital Defense Report 2024 emphasizes the importance of a unified effort between public and private sectors to address the growing wave of cyber-enabled fraud.
SOCRadar supports this effort by providing real-time insights into suspicious activities and emerging threats through its advanced Threat Intelligence platform. By monitoring dark web forums, exposed data, and phishing campaigns, SOCRadar alerts organizations to fraud-related risks targeting their assets.
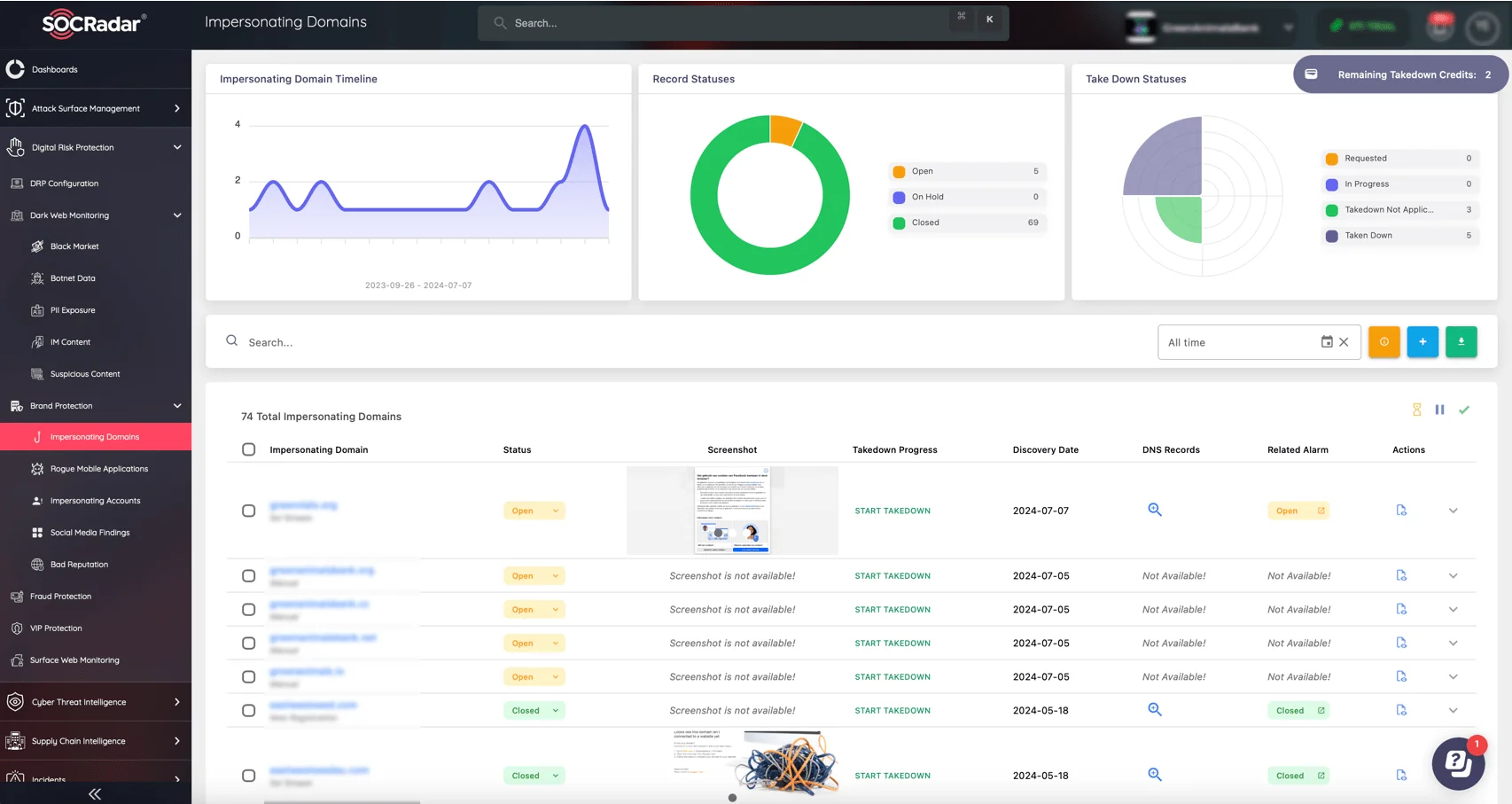
Monitor impersonating domains, accounts, and other fraud attempts via SOCRadar’s Brand Protection
SOCRadar’s Digital Risk Protection (DRP) solution helps your business to proactively identify fraudulent schemes, protect sensitive information, and develop effective takedown strategies, reinforcing your defenses against fraud tactics.
Conclusion
The Microsoft Digital Defense Report 2024 paints a vivid picture of the rapidly evolving cyber threat landscape, highlighting both the sophistication and volume of attacks targeting organizations globally.
With over 600 million cyberattacks each day, including threats from nation-state actors and financially motivated cybercriminals, it is clear that the stakes for cybersecurity are becoming higher.
Additionally, the Microsoft Digital Defense Report 2024 sheds light on the expanding threat of ransomware, DDoS attacks, and fraud, urging organizations to adopt proactive, multi-layered defense strategies. Whether it’s combating identity-based threats or addressing the surge in financial fraud, businesses must strengthen their defenses through advanced security tools, threat intelligence, and collaboration with industry peers.
In this challenging landscape, platforms like SOCRadar Extended Threat Intelligence (XTI) provide vital support to organizations, helping them stay one step ahead by delivering real-time insights, monitoring threat activities, and offering strategies to mitigate the risks of cyber attacks.


































